iOS 12 device management
One of the significant updates with respect to iOS 12 is Apple distrusting certain certificates . It impacts iOS 12 management as it affects the communication between iOS 12 devices and the server, due to security advancements. However, you can manage using the workaround given. This is also applicable Mac machines running macOS Mojave.
Have I been affected?
You would have been affected:
- If you do not have any third-party certificate configured on your server and purchased Endpoint Central on or before January 2017/Mobile Device Manager Plus on or before July 2017. If purchased later, you can still check if you've been affected as explained below.
- If you are managing or plan to manage iOS 12 devices and Windows XP/Windows Server 2003 using Endpoint Central.
How to check if I have been affected?
Open Google Chrome and login to your server on the HTTPS channel(port 9383/8383) and click on icon present to the left of the Not Secure option. Click on Certificates option from the dropdown. If the parameters Issued by and Issued to are the same, then you need follow the steps below to manage iOS 12 devices. This process may vary on other browsers.
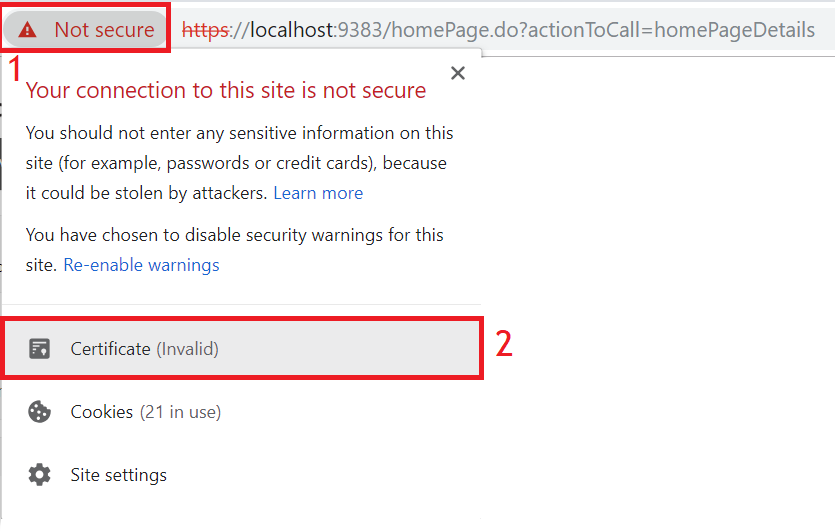
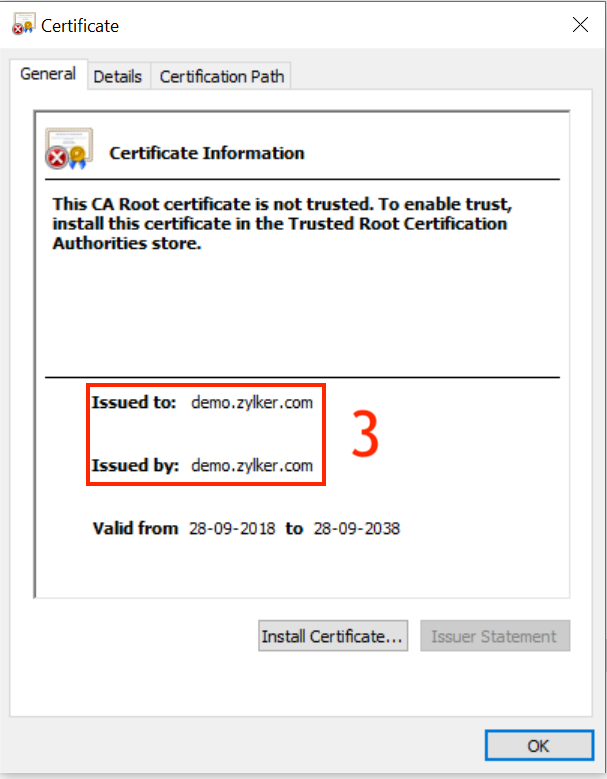
You can also verify by following the steps given below.
Steps for the workaround
Option #1: Using third-party certificates
This is the recommended solution as it will be applicable long term and will comply even if Apple has newer security advancements in the future. Further, if most of your managed devices have already been updated to iOS 12, this is the ideal option.
Add third-party certificates to your server as explained here. Once added, you can start managing iOS 12 devices. Also, in case you're using ManageEngine Endpoint Central and managing Windows XP/Windows Server 2003 machines, this is the only available option for managing iOS 12 devices.
In case some devices have already been updated to iOS 12, adding third-party certificates ensures iOS 12 devices automatically contact the server and communication gets re-established automatically.
Option #2: Without using third-party certificates
This is a temporary short-term fix and is applicable only for this particular scenario and not for any newer security advancements made by Apple. Further, this fix is most suited only if no managed devices(or very few devices) have been updated to iOS 12 in your enterprise.
Step #1: Prevent devices from updating to iOS 12
- On your MDM server, click on Device Mgmt from the top menu(in case of Endpoint Central, click on Mobile Device Mgmt from the top menu and select Management from the left pane). Select Automate OS Updates from the menu on the left.
- Click on Create Policy and select Apple from the dropdown. Provide a policy and for the option Deploy OS on devices, choose Delay for and provide 90 days as the delay period. This provides sufficient time for the workaround to be fully implemented. For more details about automating OS updates, you can refer to this.
Step #2: Push new certificates to the enrolled devices
- On the machine running the server, open services.msc and stop the server. Once stopped, navigate to <Directory>\ManageEngine\<Server>\apache\conf and copy the certificate files(server.key and server.cer).
- Create a new folder and paste these certifiicate files. Now, download this zip file and copy it. Paste it in <Directory>\ManageEngine\<Server> and extract its contents.
- Once extracted, go to bin folder and run the batch file, mdm-generate-new-ssl-certificate.bat. Once done, click on the apache folder and select the conf folder.
- Verify if the files, server-new.crt and server-new.key have been added to <Directory>\ManageEngine\
apache\conf . If the files have been added, then you can proceed with the fix. If not, you have not been affected and you can proceed with enrolling iOS 12 devices. - In case of MDM Server, click on Device Mgmt from the top menu(in case of Endpoint Central, click on Mobile Device Mgmt from the top menu and select Management from the left pane). Click on Profiles from the menu on the left.
- Click on Create Profile and select Apple from the dropdown. Select Certificate from the list of policies.
- Configure the policy as explained here and upload the certificate file server-new.crt which is present in <Directory>\ManageEngine\<Server>\apache\conf. Save and Publish this profile.
- Click on Groups & Devices from the menu on the left and select the groups containing iOS devices. If do not have such groups, select all iOS devices. Distribute the created Certificate profile to the selected groups/devices. In case some devices have already been updated to iOS 12, you need to share the certificate to the users and they need to add it manually and fully trust the certificate. An alternate option is to re-enroll the device.
- Verify if the Certificate policy has been associated to all the devices.
Step #3: Add certificate to the server
- Once verified, stop the server as explained previously. Navigate to <Directory>\ManageEngine\<Server>\apache\conf and rename server-new.crt as server.crt and server-new.key as server.key.
- After renaming, start the server and verify if you can enroll iOS 12 devices. If devices can be enrolled, the fix has been applied.
- To apply this fix permanently, select Enrollment from the top menu(in case of Endpoint Central, select Mobile Device Mgmt and select Enroll from the left pane).
- Now select APNs certificate(present under iOS) from the menu on the left. Click on Update Details present on the top right and modify the organization name(it can be reverted later). Once modified, click on Update.
- Click on Inventory and initiate a manual scan on all iOS devices. Once done, you can revert the organization name on the APNs certificate, if need be.
NOTE: Once you are sure the process has been completed, you can disassociate the previously distributed OS update policy(in Step #1) and initiate OS update by creating a corresponding new policy.