How to Enable HTTPS Configuration in Network Configuration Manager?
Until now, SSL was enabled in Network Configuration Manager manually. The steps can be found here
This step had to be repeated on every setup in case of failover being used and in central-probe setup. When central-probe has failover setup then it becomes very hectic.
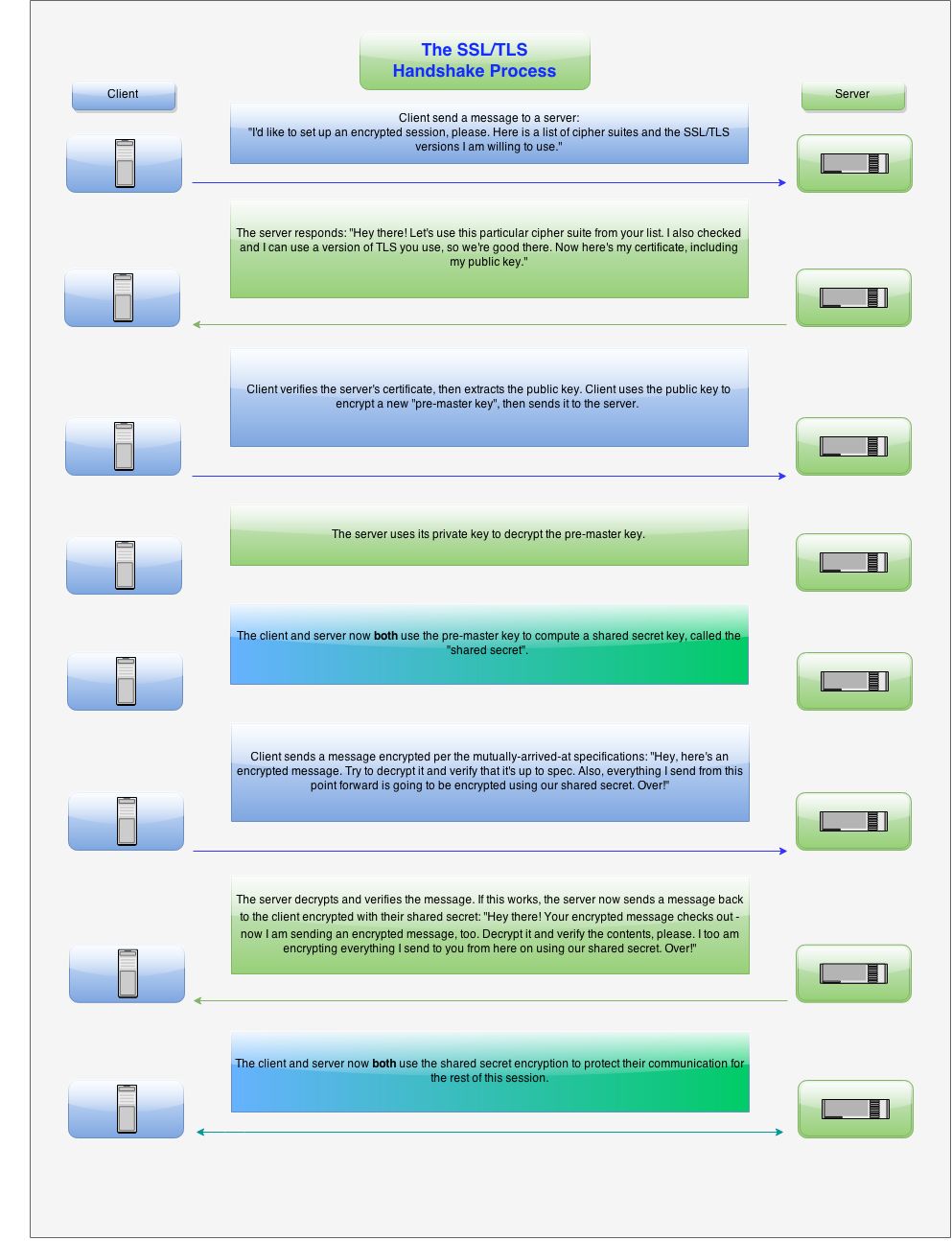
Understanding SSL
Secure Sockets Layer (SSL) is a standard security technology for establishing an encrypted link between a server and a client. It is implemented in client-server communication with a secure handshake process made possible using PKI (Public key Infrastructure). The client and server perform a process called handshake in which they agree upon what encryption they can use and their shared Key before starting to communicate. This information will be encrypted using the public key(contained in certificate) and can only be decrypted using private key(server has it). So no one can intercept the communication further, even if the packets are captured.
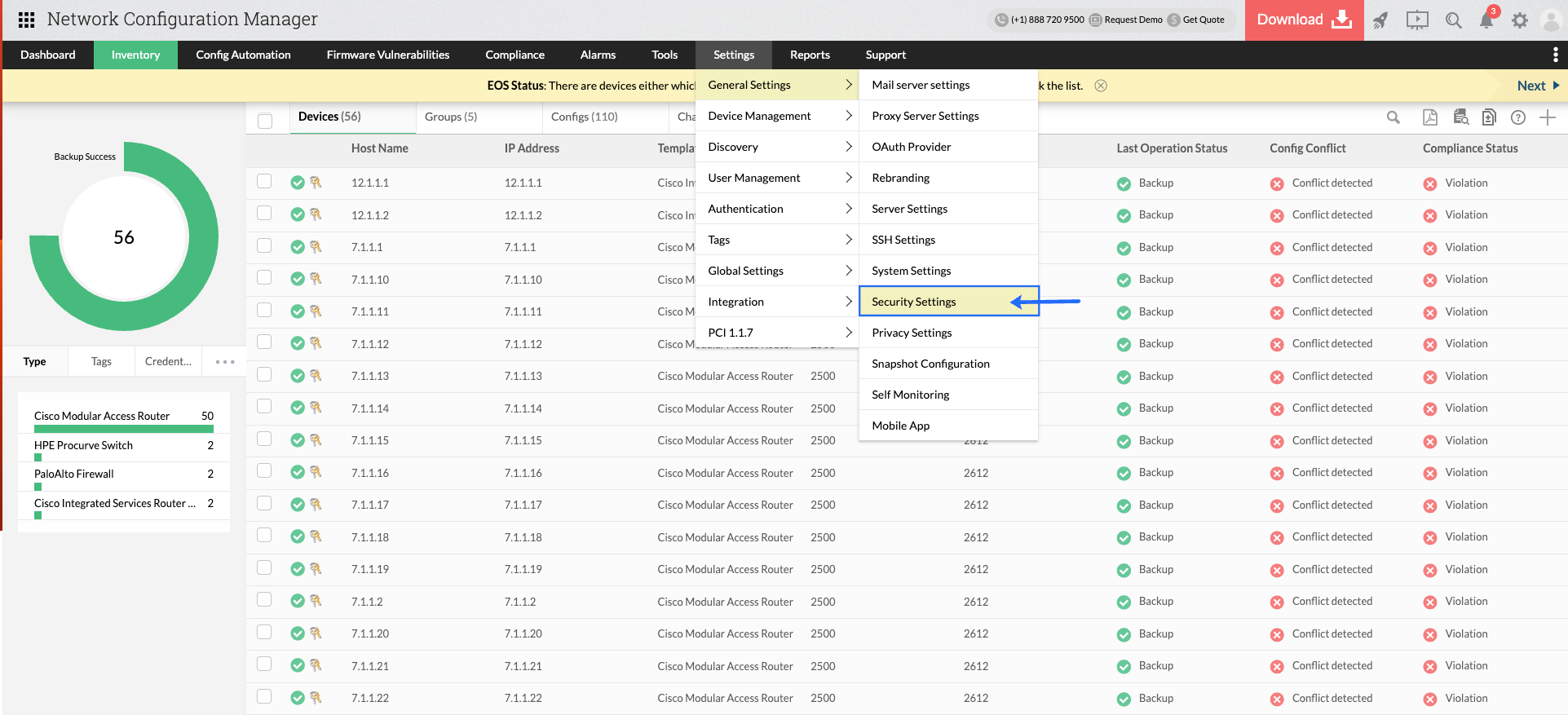
Steps to enable HTTPS in Network Configuration Manager:
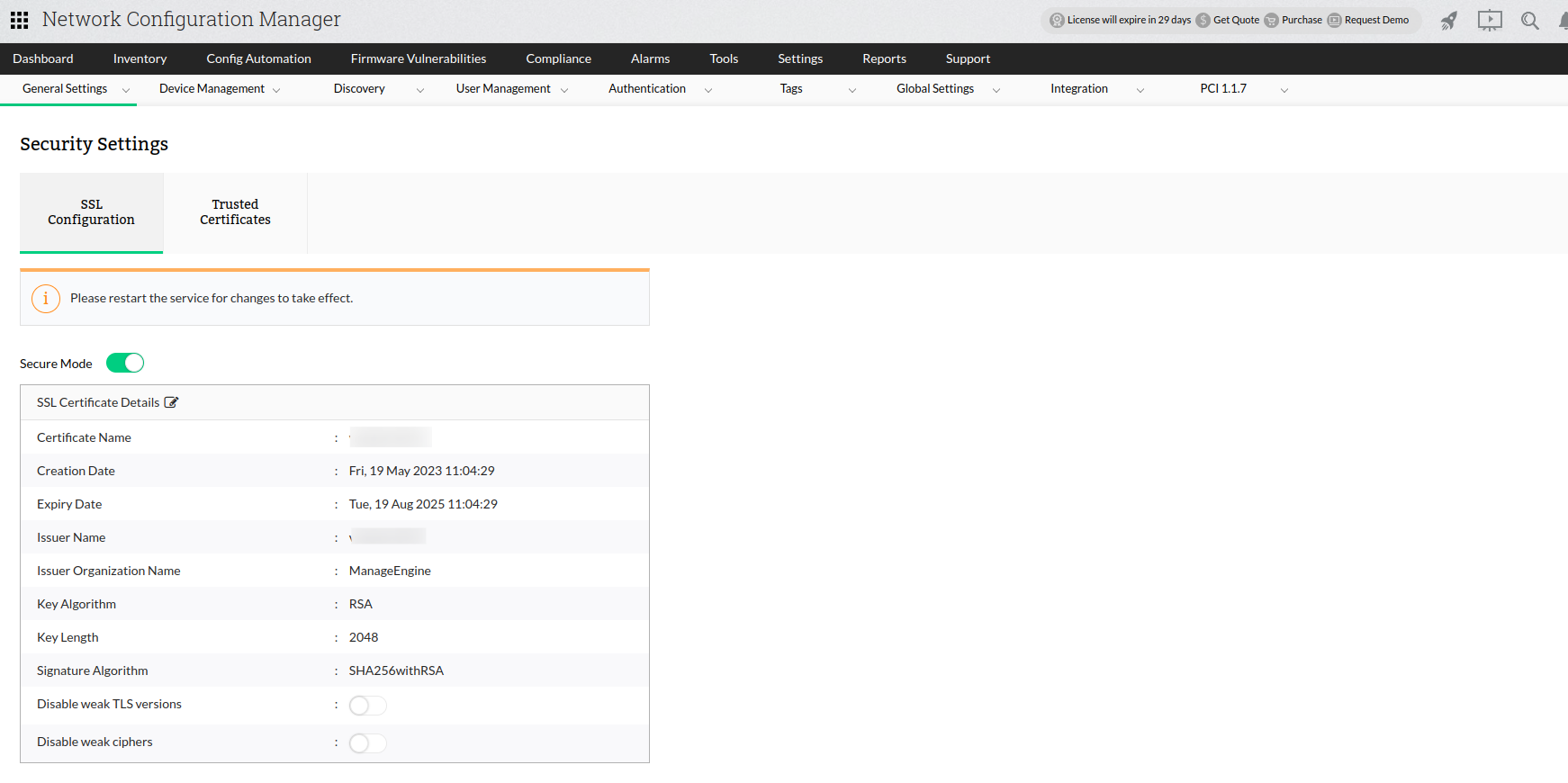
1) Go to Settings -> General Settings -> Security Settings
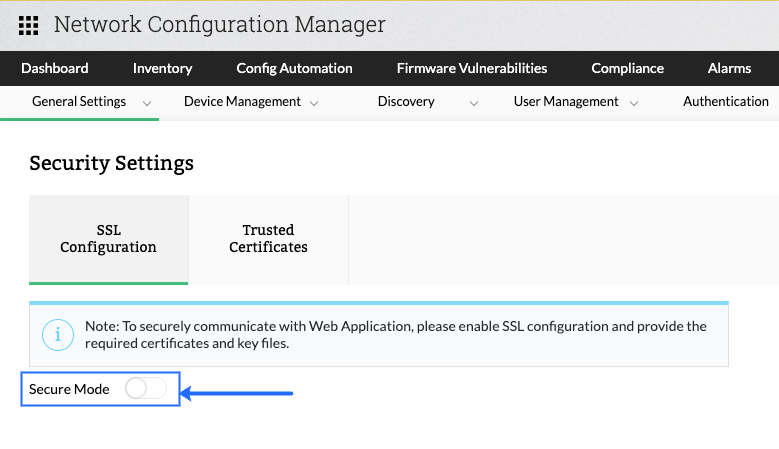
2) Enable the "Secure Mode" button.
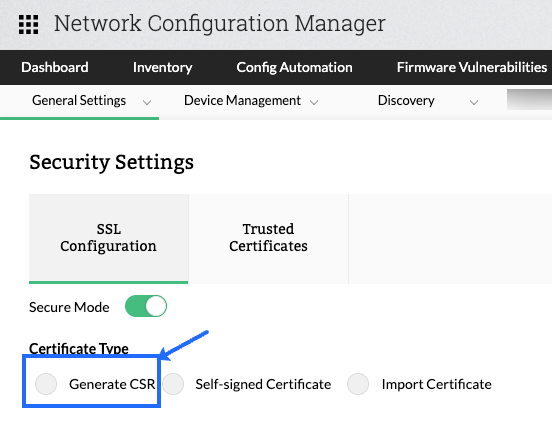
3) Once the button is enabled, you will be prompted to choose from three options, namely:
- Generate a CSR
- Self-signed Certificate
- Import Certificate
4) Generate CSR
This option helps you generate a Certificate Signing Request (CSR). A CSR or Certificate Signing request is a block of encoded text that is given to a Certificate Authority when applying for an SSL Certificate. It is usually generated on the server where the certificate will be installed and contains information that will be included in the certificate such as the organization name, common name (domain name), locality, and country. It also contains the public key that will be included in the certificate. A private key is usually created at the same time that you create the CSR, making a key pair. A CSR is generally encoded using ASN.1 according to the PKCS #10 specification.
A certificate authority will use a CSR to create your SSL certificate, but it does not need your private key. You need to keep your private key secret. The certificate created with a particular CSR will only work with the private key that was generated with it. So if you lose the private key, the certificate will no longer work.
Once you click on the Generate CSR, you will have to fill out a few information for the certificate you want to create for use in Network Configuration Manager Server.
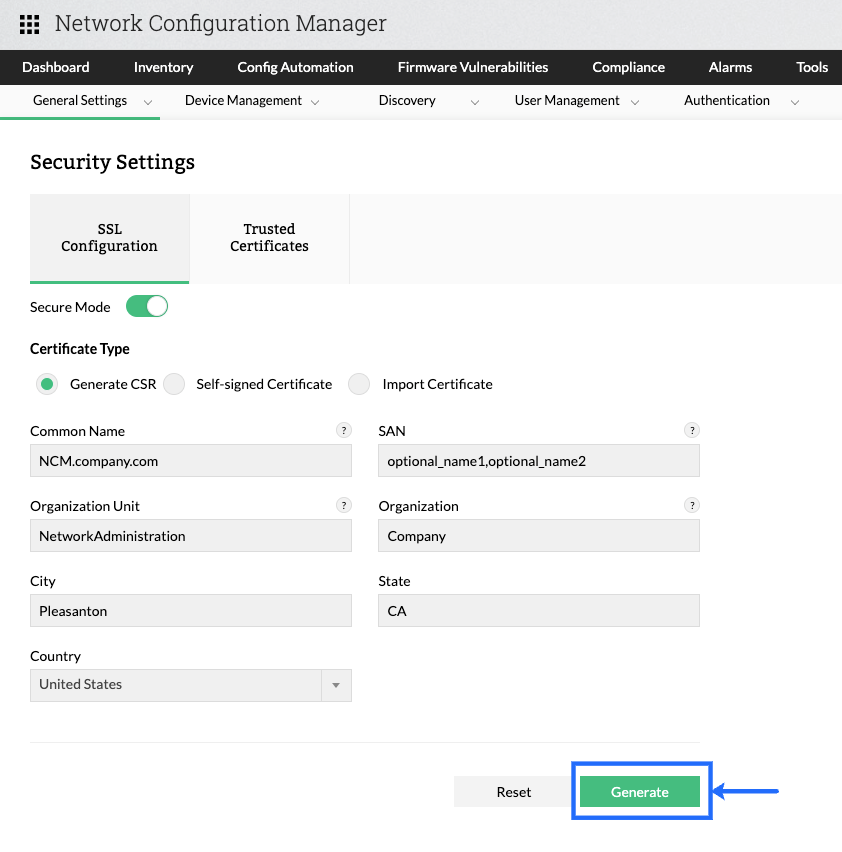
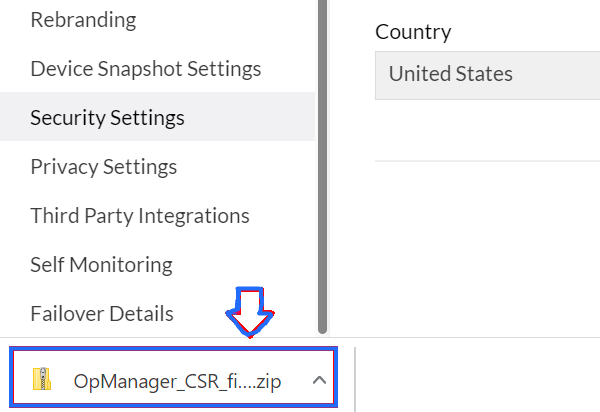
On clicking the Generate button your CSR and Server Key files will be downloaded as a ZIP.
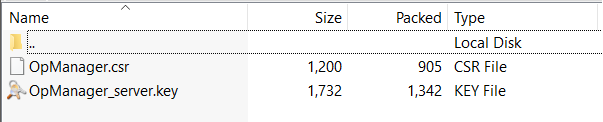
Extract the file and use the "OpManager.csr" file to get a signed certificate from a CA of your choice.
Self-Signed Certificate:
This option lets you enable SSL in Network Configuration Manager with a self generated and self-signed certificate. This certificate is safe to use and is equally secure. But browsers may display them as untrusted, since it is not signed by a Valid CA (Certificate Authority).
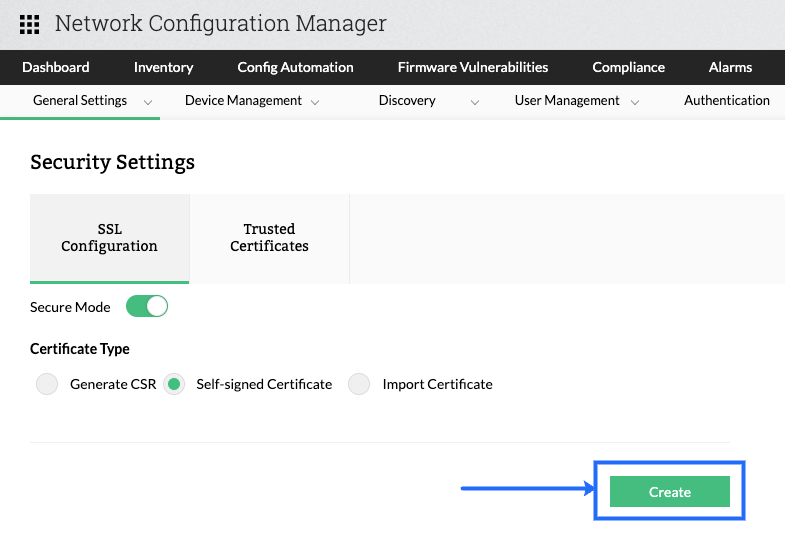
You will be prompted to restart Network Configuration Manager for the changes to take effect.
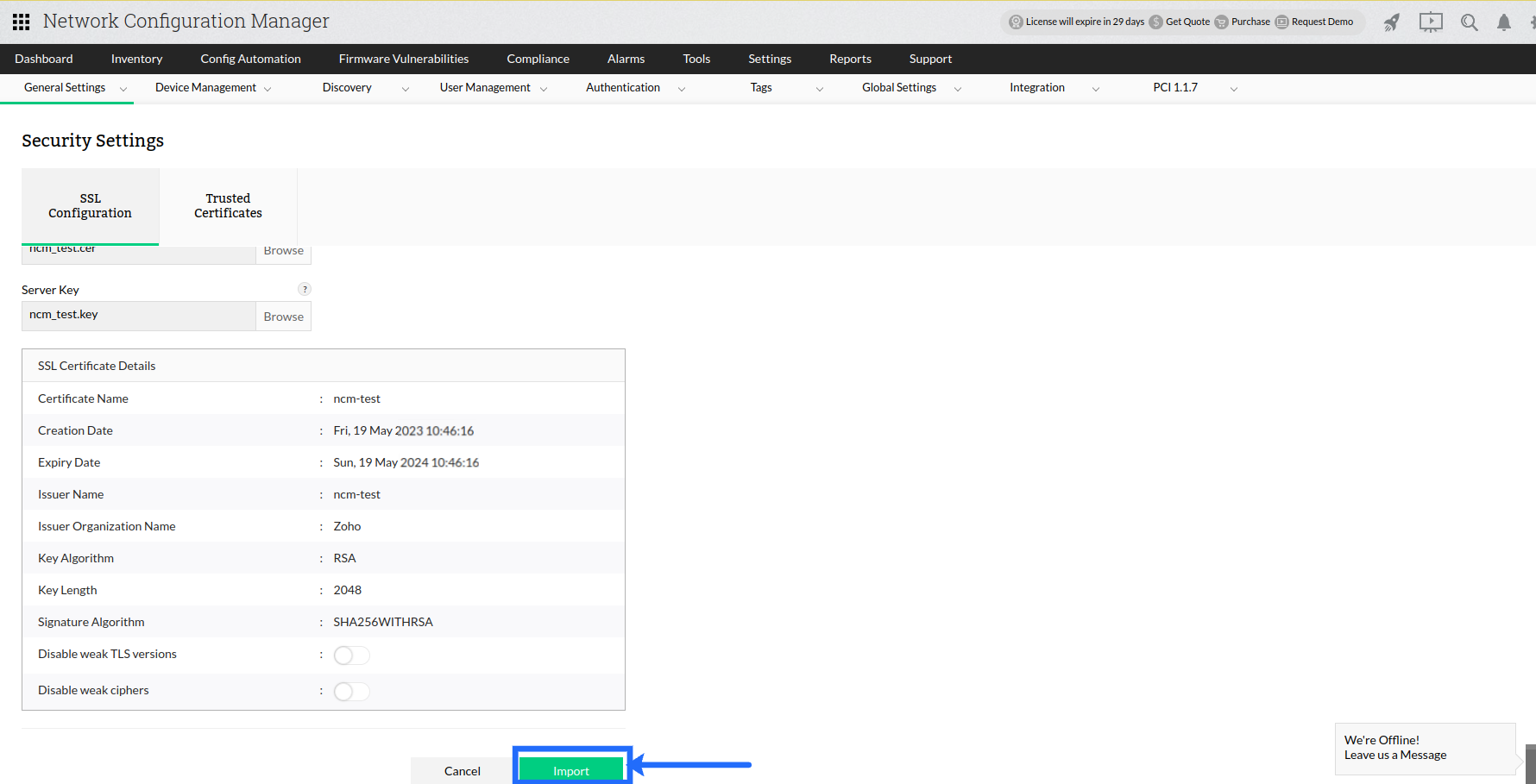
Import Certificate:
Use this option if you already have a valid certificate and key files (or) a keystore or a PFX file with the certificate.
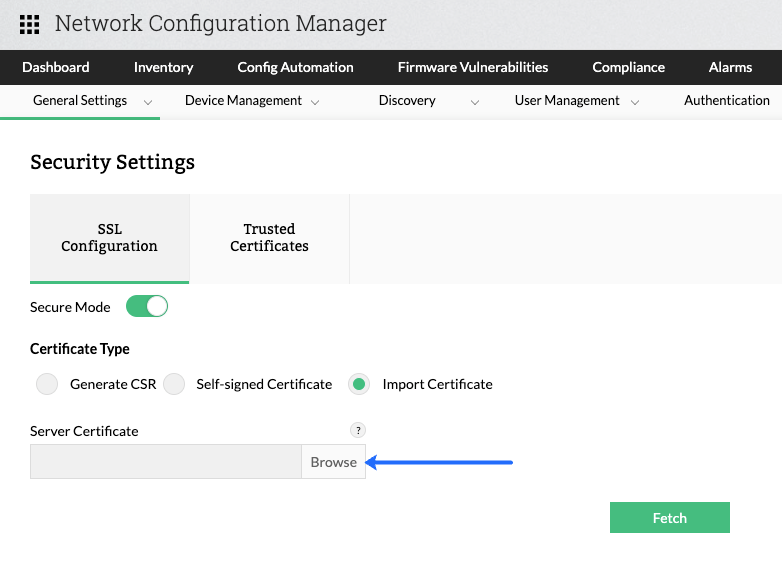
Select a certificate file.
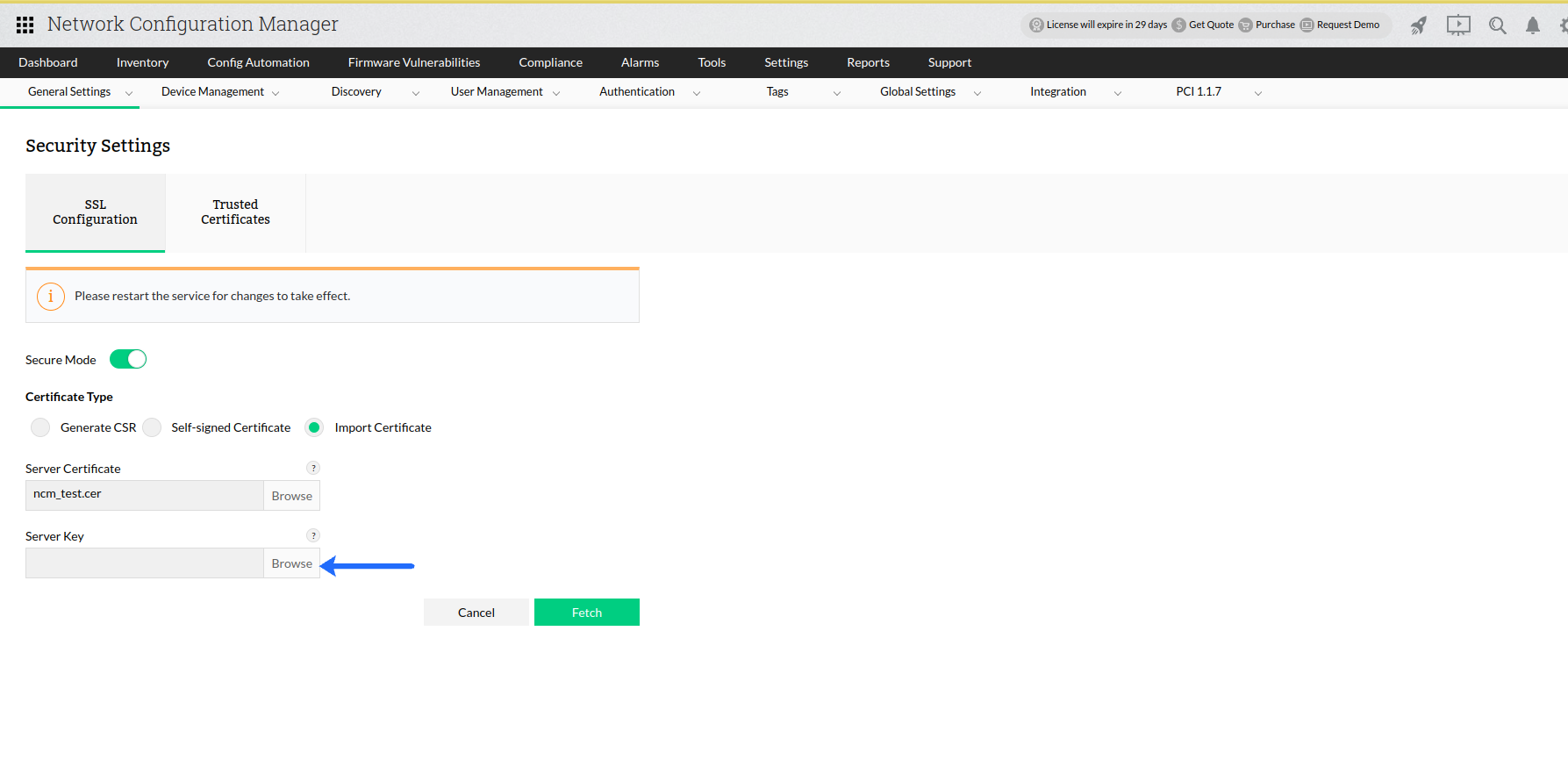
Select the appropriate "key" file.
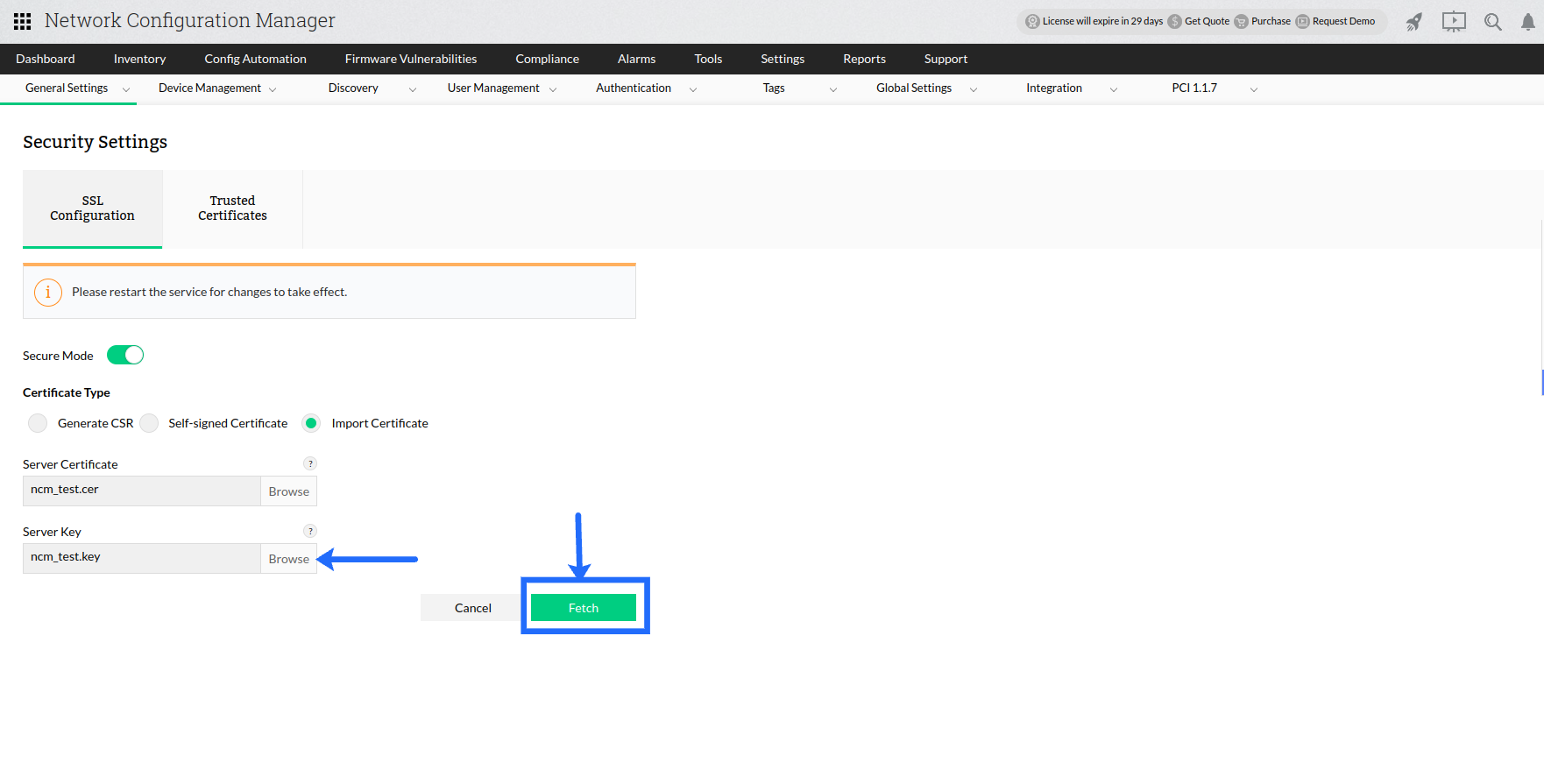
Verify and choose Import.
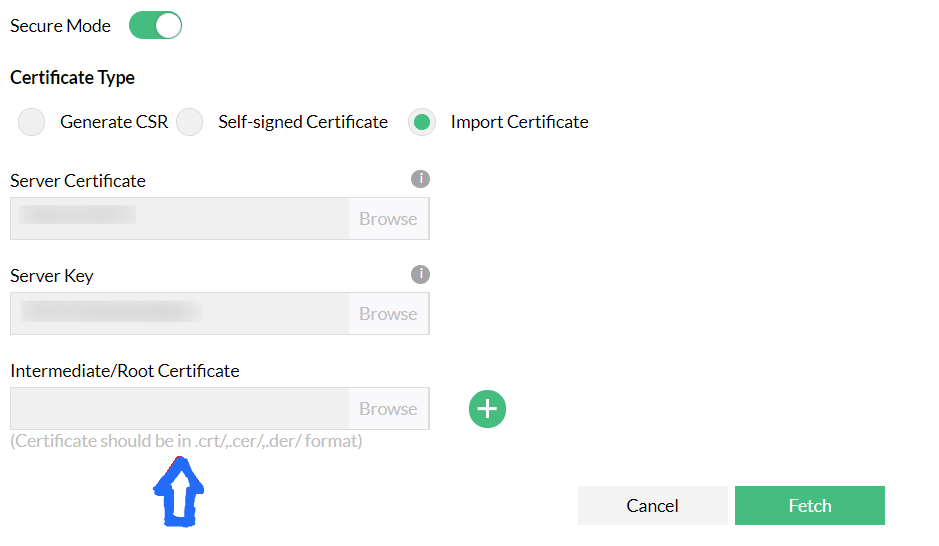
!!! If the certificate cannot be validated with trusted sources, you will be asked to provide the intermediate certificates and root certificate files.
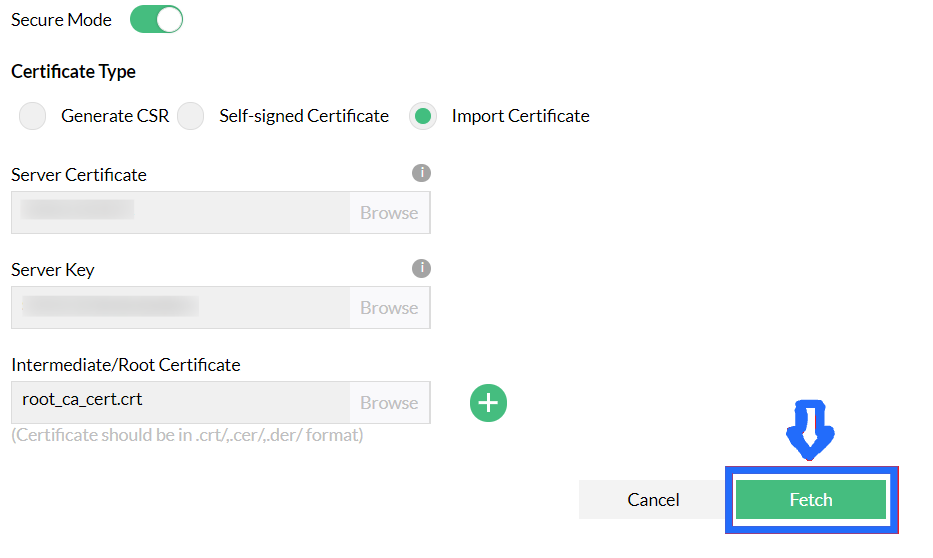
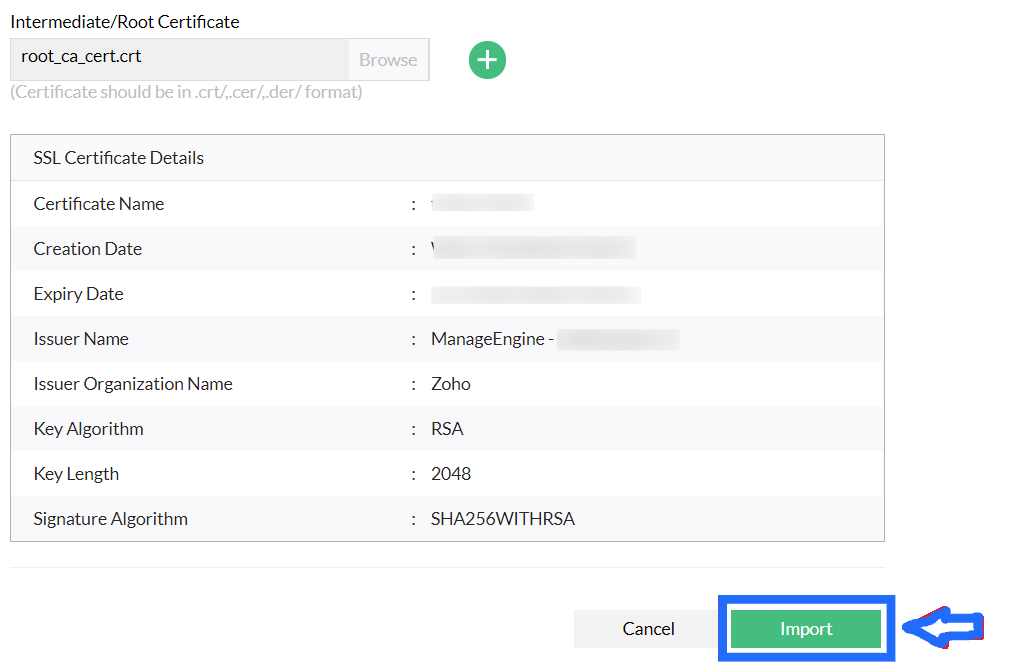
Once uploaded, Verify the certificate and click import. On successful import, you will be prompted to restart Network Configuration Manager.
Importing from PFX or Keystore:
If you are using a Keystore or a PFX file, you will be prompted to input the password for opening the file.
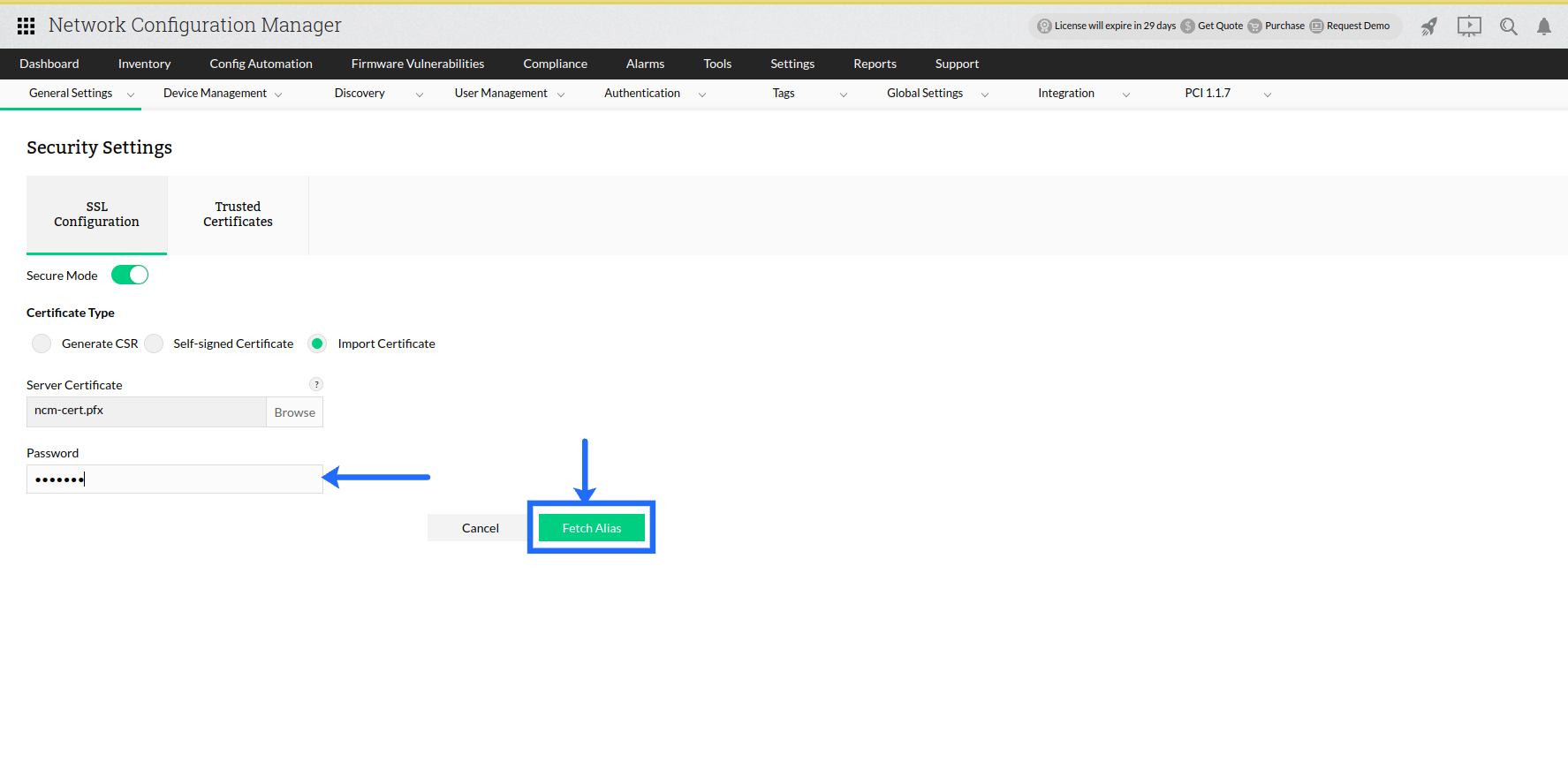
On clicking Fetch, you will be provided with a list of Key-entries present in the keystore. Choose a specific alias which is to be used to enable SSL in Network Configuration Manager.
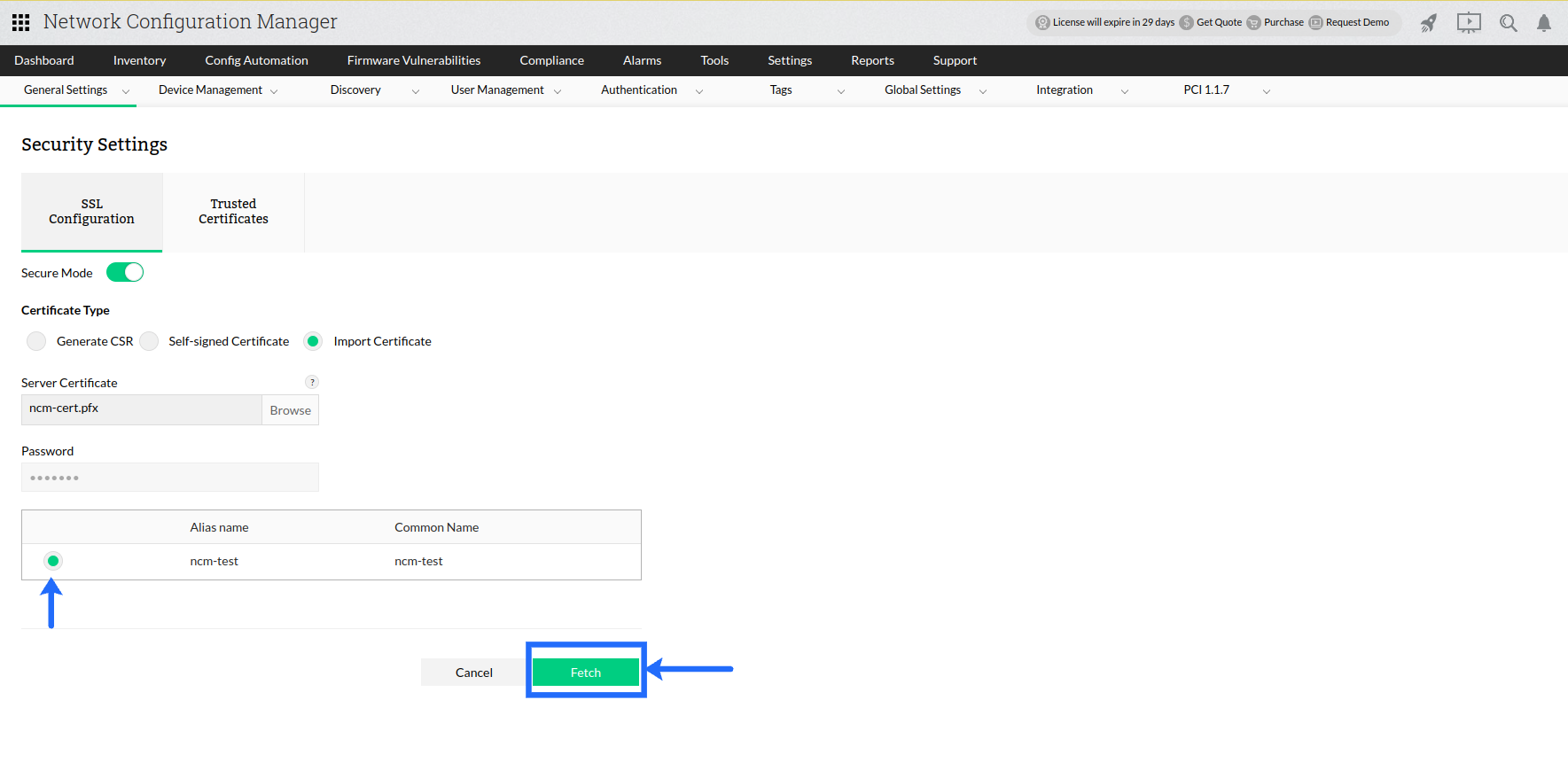
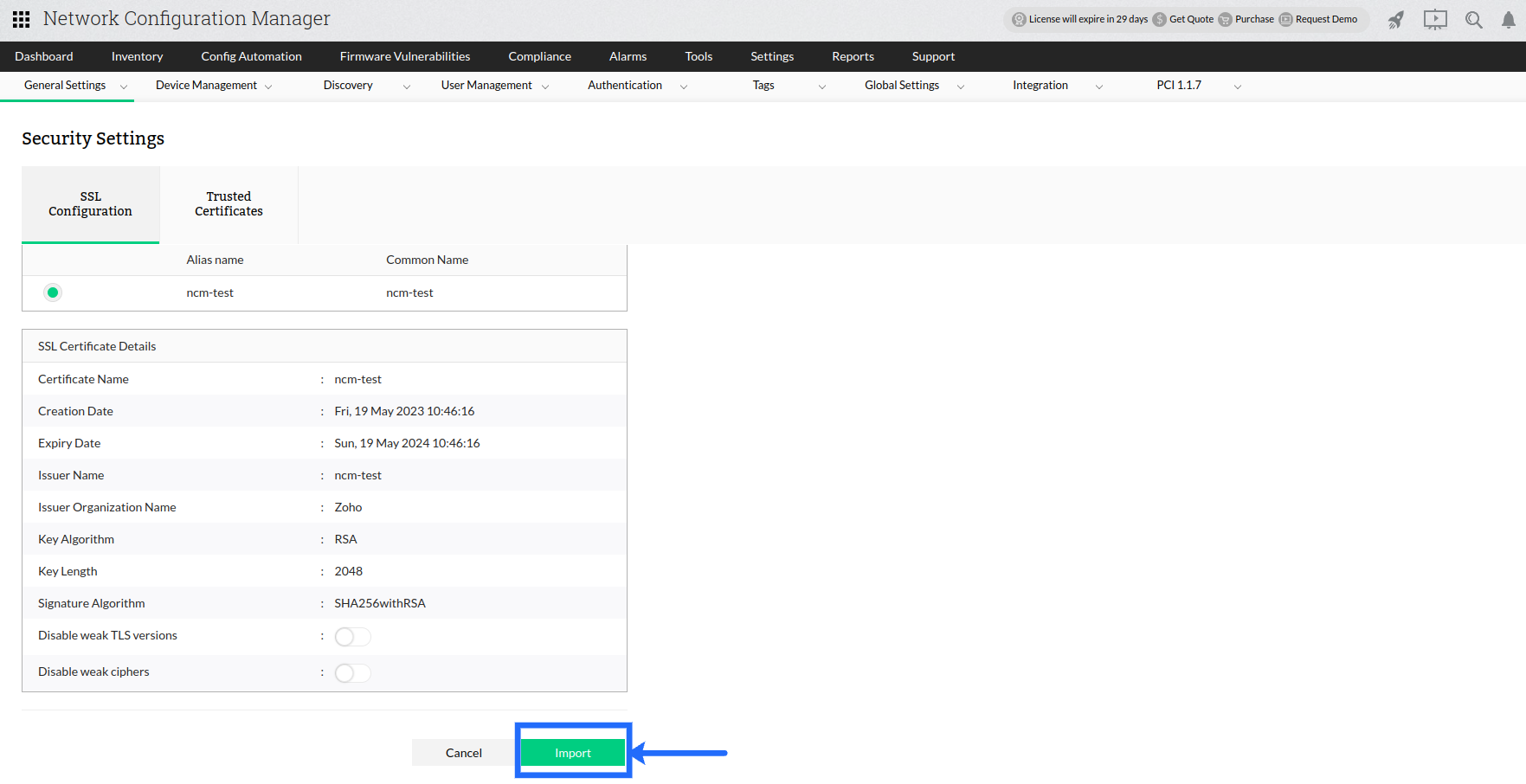
You will be shown a preview of the certificate information, verify and click Import for using the certificate. Again you will be prompted to restart Network Configuration Manager for the changes to take effect.
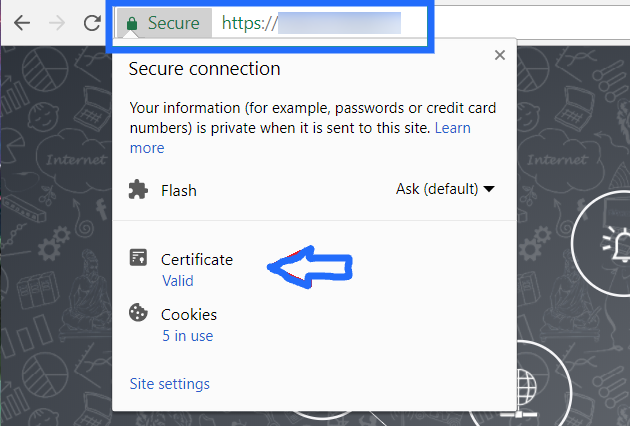
Finally, after enabling SSL through one of the above ways, you will be able to connect to Network Configuration Manager in secure mode:
Thank you for your feedback!