Setting up Two-Factor Authentication - Duo Security
Two-Factor Authentication (TFA) or Multi-Factor Authentication (MFA) is an extra layer of security provided to secure your accounts. This authentication process significantly reduces the risk of unauthorized access, even if your password is compromised. Duo Security, a leading cloud-based Multi-Factor Authentication provider, offers a seamless way to secure your accounts with TFA. By integrating Duo Security with PAM360, you can enhance the security of your privileged access management system, ensuring that only authorized users can access critical resources.
This document will walk you through the following topics:
- Integrating PAM360 and Duo Security
- Connecting to the PAM360 Web Interface with Duo Security as TFA
- Enrolling while Logging In
1. Integrating PAM360 and Duo Security
If you have the Duo application in your environment, you can integrate it with PAM360 and leverage the Duo security authentication as the second level of authentication. This section explains the configurations involved:
- Sign up for a Duo account.
- Log in to the Duo Admin Panel and add a new application.
- Click the Protect an application button. The Protect an application page lists the applications you can protect with Duo.
- Search for Web SDK and click Protect This Application and fill the required field and save it.
- While saving, take a note of the Client ID, Client secret, and API hostname which must be provided in PAM360 GUI (in step 2 below).
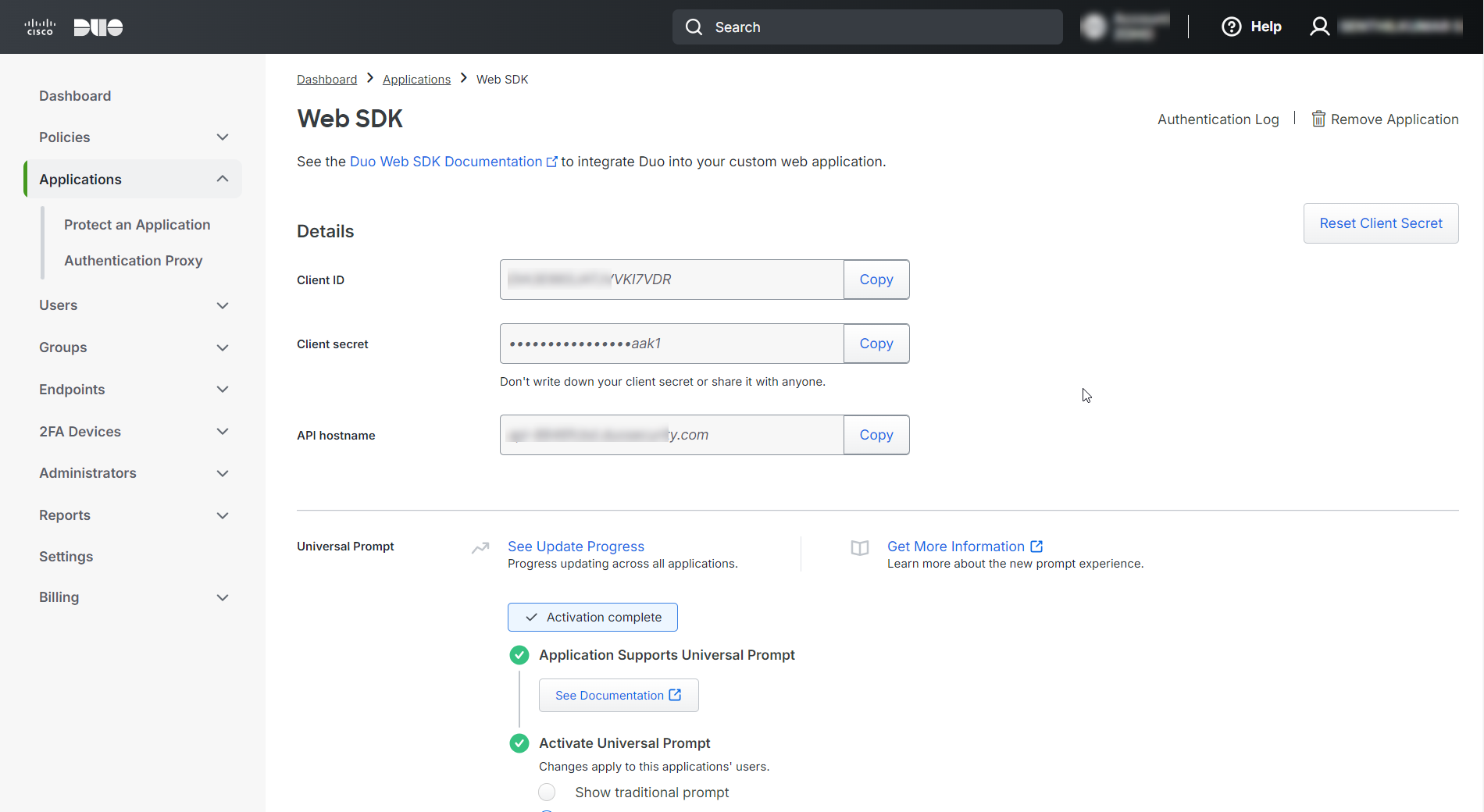
- Enroll your users with Duo and start authenticating.
Additional Detail
PAM360 uses the latest Web SDK version and it offers support for both the traditional prompt and the universal prompt methods of authentication.
Upon above Duo configuration, enable Duo Security as the TFA in PAM360 and enforce it to the PAM360 users. Refer here for detailed instructions. When enabling Duo Security as TFA in the PAM360 web interface, enter the Client ID, Client secret, and API hostname that are copied from the Duo application.
2. Connecting to the PAM360 Web Interface with Duo Security as TFA
As explained here, the first level of authentication will be through the usual authentication i.e. users have to authenticate through PAM360's local authentication or Active Directory/LDAP authentication. The users for whom TFA is enabled, will have to authenticate twice successively.
Upon launching the PAM360 web interface with Duo Security as TFA,
- Proceed with the first level of authentication and click Login.
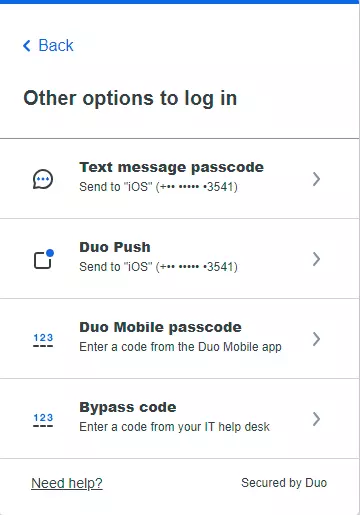
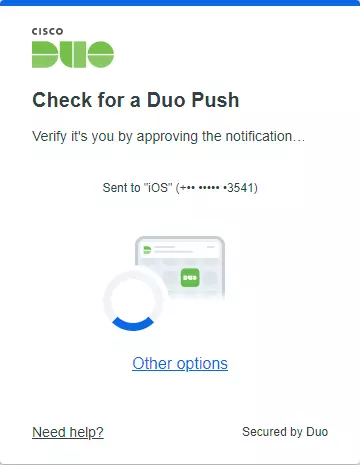
- PAM360 will prompt you to choose an authentication method out of the three options offered by Duo. Choose Duo Push as an authentication method and follow the below steps:
- Tap Send me a Push on the Duo Push request sent to your phone.
- You can also request a One Time Passcode via SMS on your phone, allowing users to avail TFA even when there is no internet connectivity.
3. Enrolling with Duo Application while Logging In
- Click Start Setup on the login page.
- Select the type of device you are adding and enter your phone number.
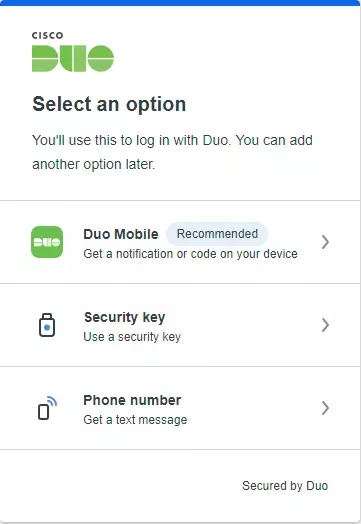
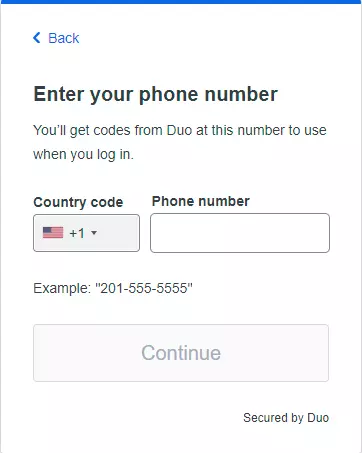
- Verify your phone number by scanning the QR code sent to your phone.
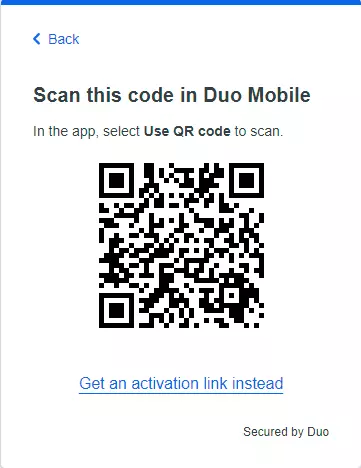
- After successful verification, click Continue.
Caution
If you have configured High Availability, whenever you enable TFA or when you change the TFA service type, you need to restart the PAM360 secondary server once for it to take effect.