
Problem
Your administrators have very little control or supervision over the privileged activity of third-party vendors.

Risk
Credentials shared with third-party remote users are more likely to be exposed due to a lack of direct administrative supervision, which leads to privilege abuse.

Solution
In order to enforce least privilege access on a remote workforce, you will need to expand your Zero-Trust-infused privileged access management (PAM) strategy to include third-party remote users.
The PAM360 touch
ManageEngine PAM360 not only enables your administrator to gate access to third-party, temporary, remote users such as vendors, auditors, or developers, it also lets you exercise complete access governance at every step of a user's privileged access journey.
The privileged access journey
Simplified, secure vendor onboarding Get them up to speed, but safely
What enterprises need today is an automated, yet streamlined, onboarding process for its vendor and third-party remote users that reduces all kinds of manual administrative upheaval.
Privileged access management does exactly that, by weaving security threads into all your onboarding fronts and bringing together multi-process workflows such as privileged access, human resource management, IT service management, etc.
Secure vendor onboarding with PAM360's business workflow automation
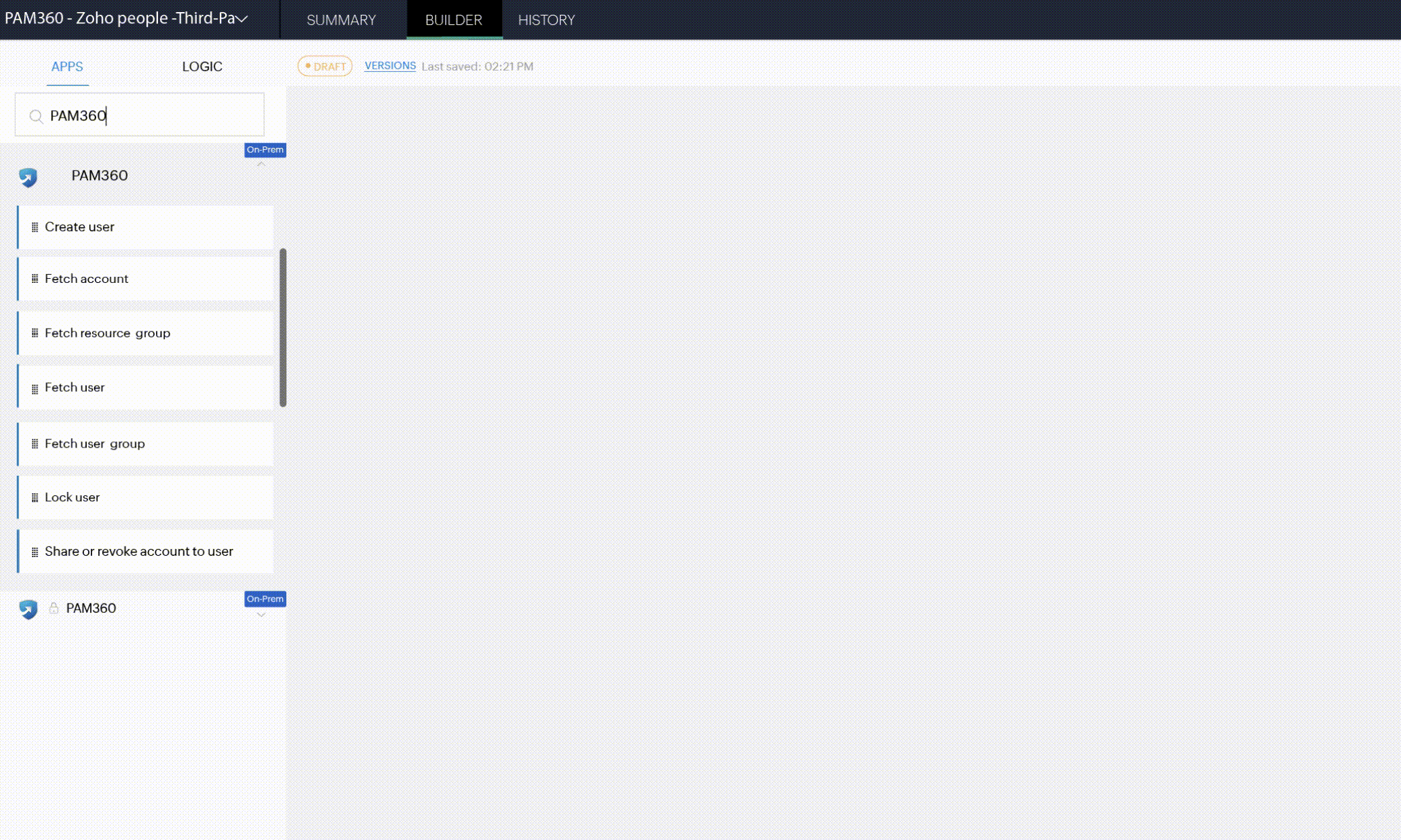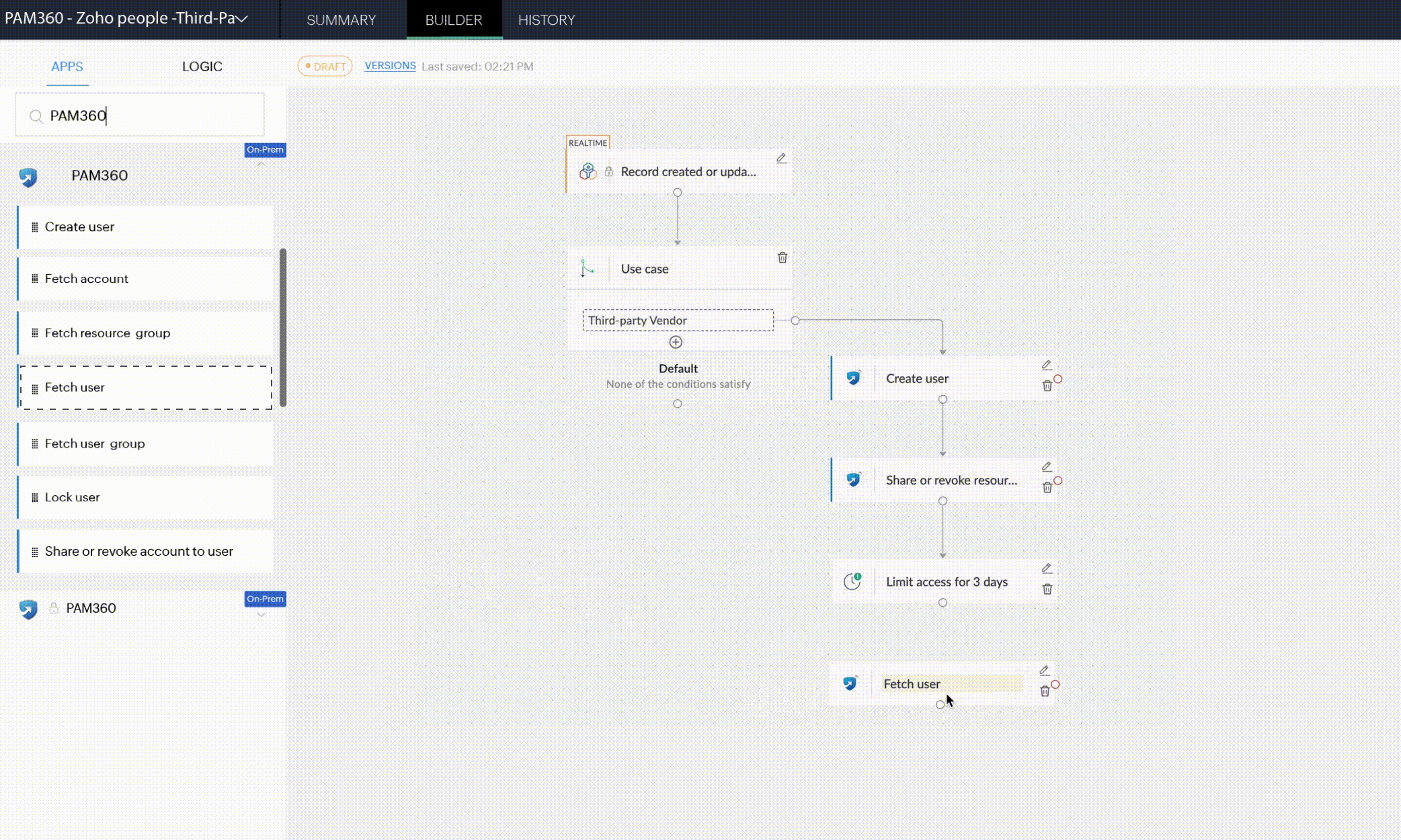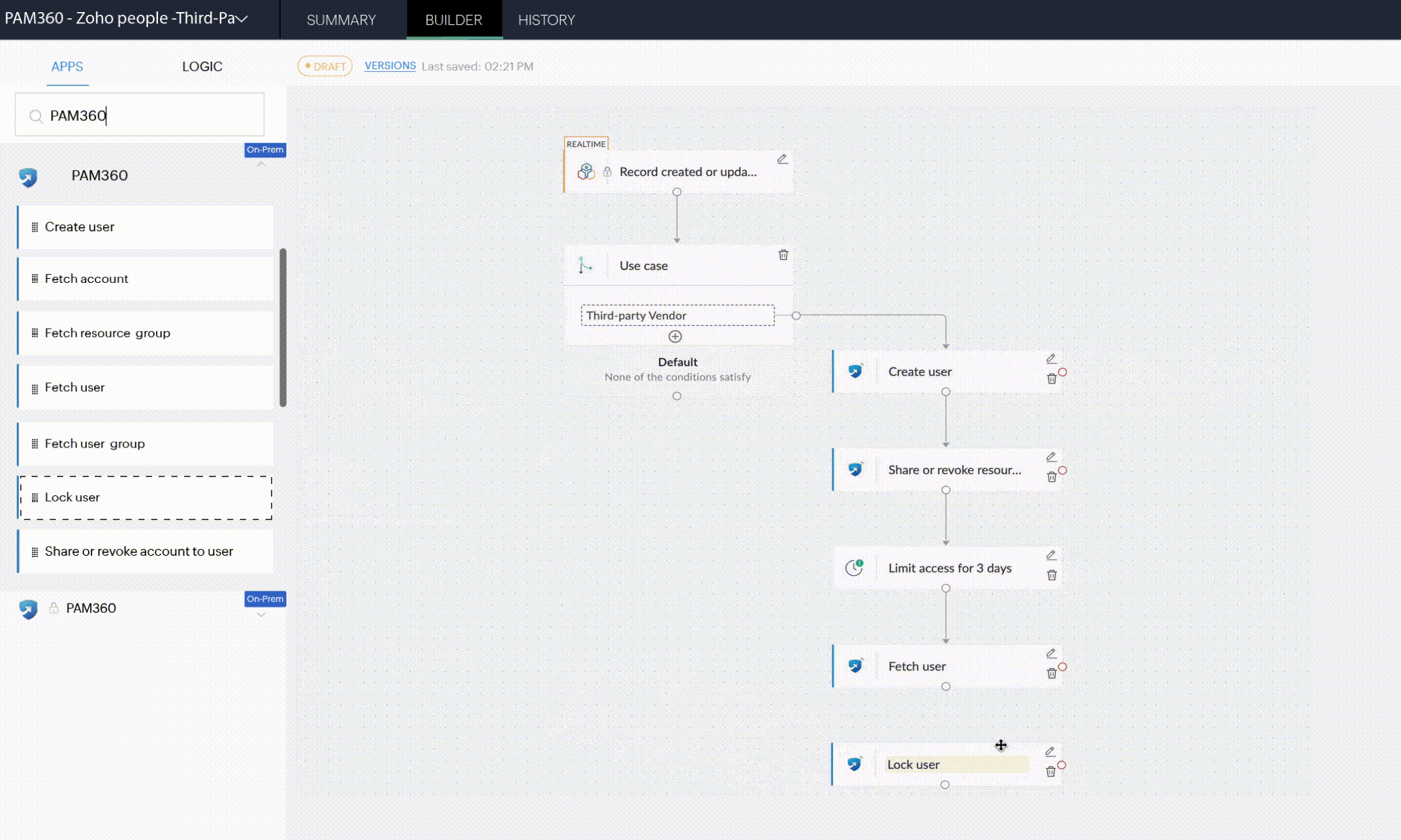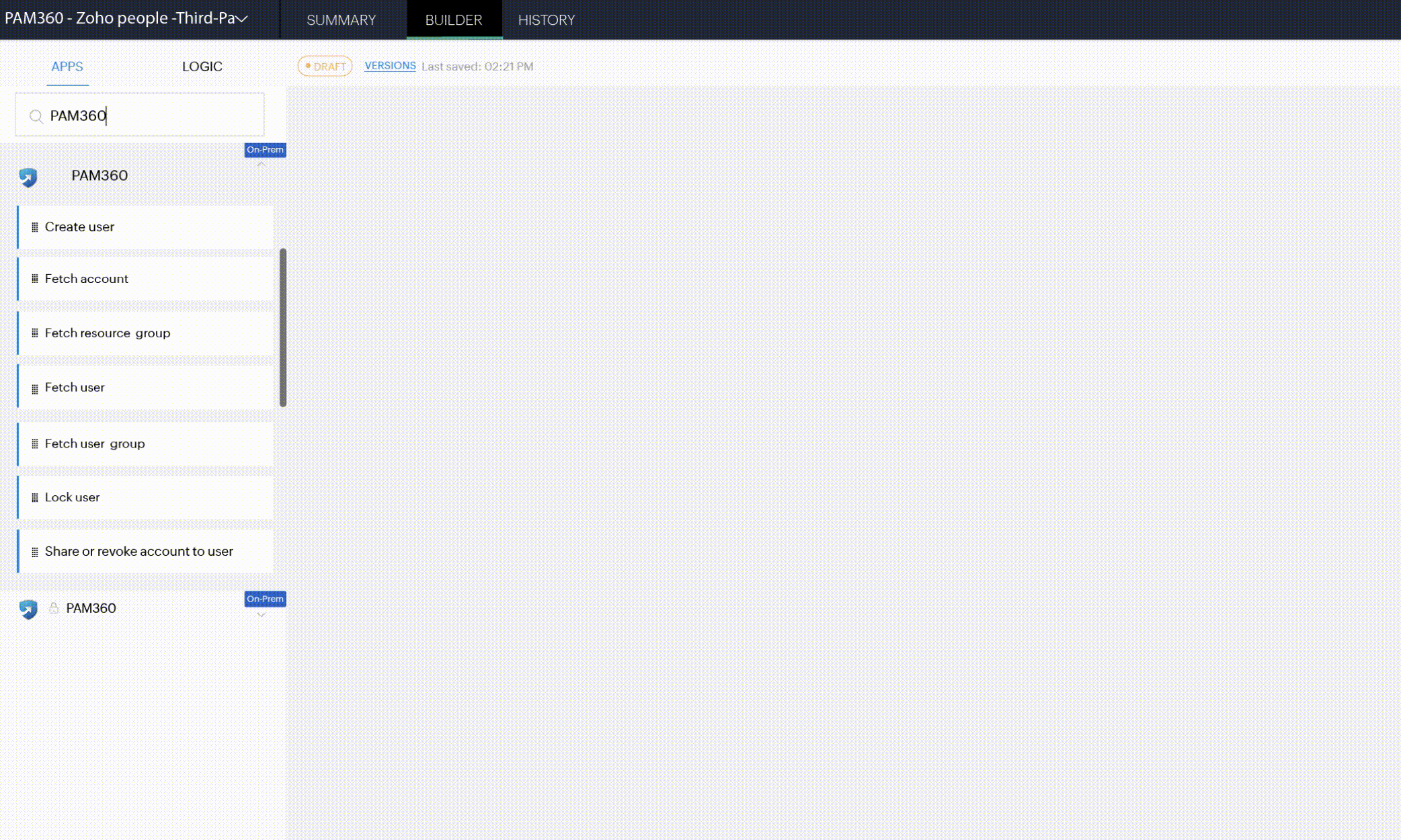

Limited visibility, restricted access, privileged account governance Secure onboarding is simply the beginning
With your vendor onboarding automated, it is essential to bring about a dynamic third-party access workflow that checks for extra and standing privileges at each step of a user's access journey.
PAM helps you determine Zero-Trust-focused access control strategies that verify if your third-party users are limited to the necessary privileges required to perform their tasks.
Real-time remote access vigilance Keep track of everything that a user does
Even after your remote users are securely onboarded and are subjected to access controls, their behavior while in session needs to be monitored.
PAM includes covering all bases of a user's privileged access journey. With such an establishment in place, your administrators have real-time supervision on all remote sessions, and they can also one-click terminate such privileges if they notice suspicious clicks or behavior. These sessions are also recorded and can be used for further investigative purposes.

Zero standing privileges in the cloud The skies are on your side with PAM
Privileged access management demands that your entire IT stack be scrutinized for standing privileges associated with your vendors, and this includes the access portfolios in your distributed cloud services.
For an otherwise siloed environment, PAM's cloud infrastructure entitlements management (CIEM) umbrella, throws a spotlight on hidden privileges. This lets you enforce least privilege access across your cloud user base. In doing so, a CIEM function enables you with periodic analysis of permissions and shadow admin accounts, letting you remediate such over privileged policies on the go.
Comprehensive, real-time auditing and reporting Keep notes handy in case you are tested
While it is important to set boundaries with privileged access and be meticulous with access sharing, it only makes sense if you have a system in place that ensures that all these actions are recorded.
A privileged access management solution helps you do that by constantly auditing every single action your third party remote user performs. This information can later be generated into comprehensive reports that come in handy when there's a compliance audit around the corner.

Automatic access revocation and user offboarding Revoke privileges when the time comes
Did you know 75% of insider threat cases involved a former employee?
A remote user with standing privileges is low hanging fruit for potential privilege abuse.
With a functional PAM routine in place, you may incorporate a third party user's exit strategy with the crux of your organization's workflow orchestration, IT service management tools. With an ITSM workflow, and a PAM routine working in tandem, you can domino the complete access revocation and consequent offboarding measures with a single click.

From an ROI standpoint, we’ve gained a lot. It saves time, boosts our security posture, and ensures better compliance. Honestly, not having a PAM solution in 2025 would be surprising. — Mario, security leader at 5BView case study

The overall experience was great. PAM360 is a single point console to access all servers, applications and network devices.

Assistant Manager IT Operations - Software
Great and efficient management panel for high end security, remote access, and zero trust security.

CISO - Manufacturing
What I liked the most about PAM360 is user-friendliness and its ability to efficiently handle network and security aspects.

Administrator - IT Services
PAM360 has proven to be exceptional in managing access within our organisation, offering us an efficient solution for controlling private access.

VP, Data and Analytics - Education
Want to explore PAM360?
Sign up for a personalised demo, today!
FAQs
What is vendor privileged access management?
Vendor privileged access management (VPAM) is a security solution that controls and monitors third-party vendors' privileged access to critical systems, ensuring secure and compliant interactions.
What is the difference between VPAM & PAM?
VPAM secures and audits privileged access for external vendors, while PAM focuses on managing and protecting internal privileged accounts within an organization.
Why do organizations need PAM for vendors?
Organizations need PAM for vendors to protect sensitive data from external threats, enforce access policies, and maintain compliance with cybersecurity regulations.
Benefits of using a vendor privileged access management solution
VPAM ensures controlled vendor access, reduces the risk of data breaches, provides audit trails, and enhances overall security posture for external collaborations.
How does ManageEngine PAM360 address VPAM needs?
ManageEngine PAM360 delivers advanced features like automated secure access workflows, remote session recording, and seamless integrations, making it ideal for managing vendor privileges securely.

