-
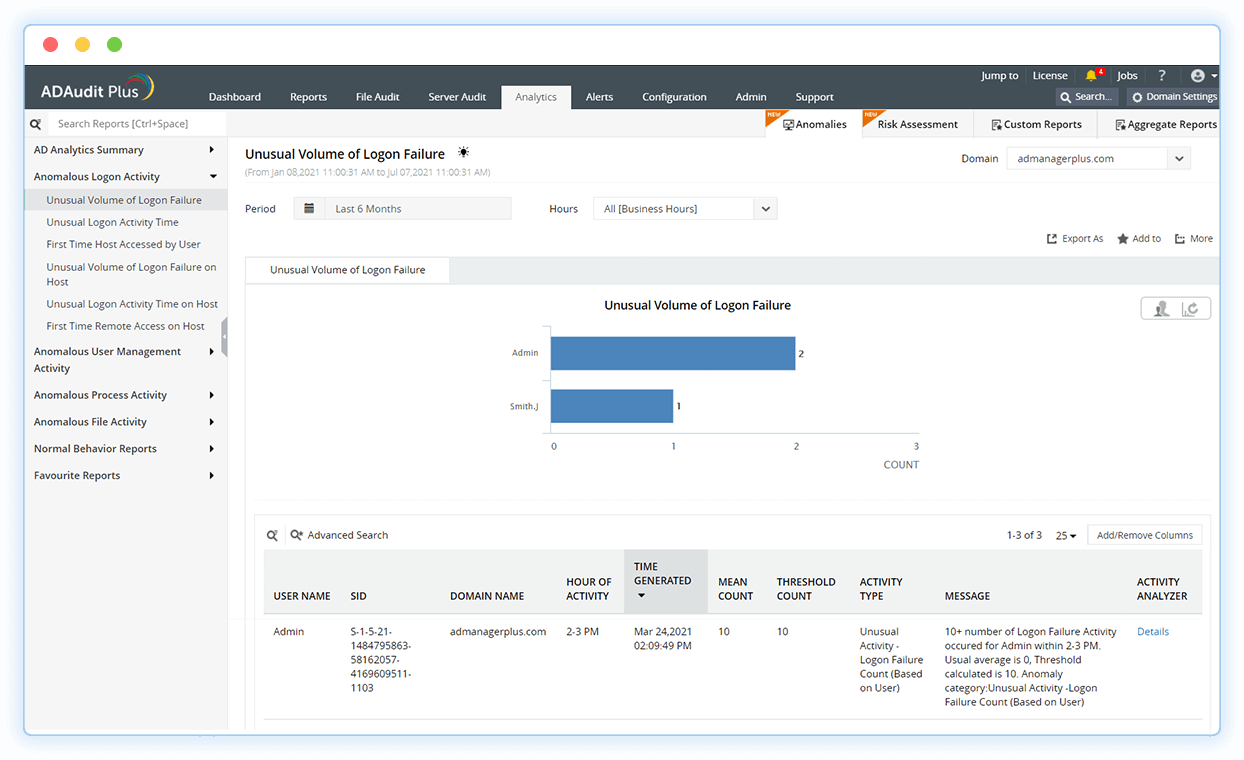
Monitor logons
Detect unusual remote desktop activities, concurrent logons, repeated logon failures, and other suspicious logon activities.
-
Track file activity
Trigger alerts for deletion of critical files, sudden spikes in file accesses, or file activities at unusual times.
-
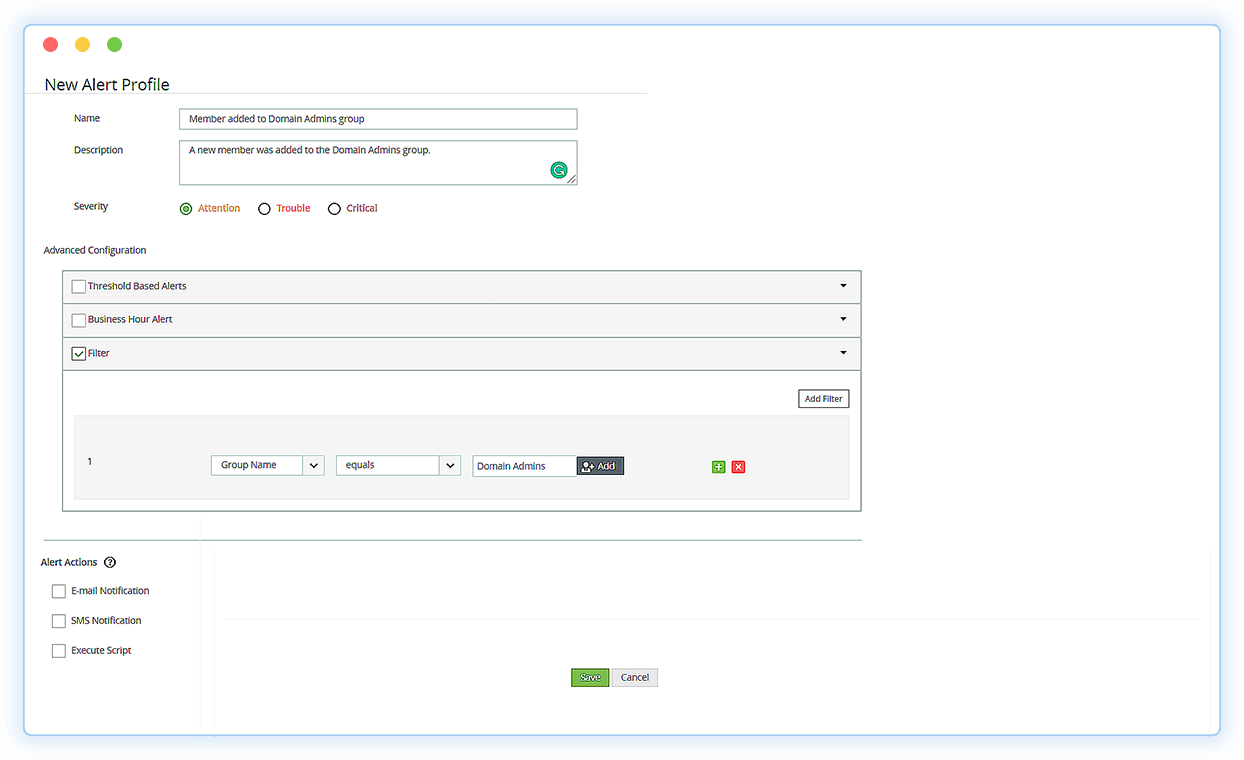
Detect changes
Spot changes to security group membership, Group Policy settings, and other critical change activities.
-
Mitigate threats
Leverage UBA to establish activity patterns and detect subtle anomalies. Execute scripts to automate response actions like shutting down a device.
Streamline auditing, demonstrate compliance, and detect threats in just a few clicks using our UBA-driven auditor.