View Top Hosts Reports
To view the top 'N' hosts reports use the following menu option:
- Reports tab > Top N Reports
The Top N Reports section in the Reports tab, lists the top hosts, users, and processes generating important events. You can click the View All link to view all the reports in this section in a single page.
Top Hosts by User Access
This report shows the top 'N' number of hosts with maximum number of successful logins and the top 'N' number of hosts with maximum number of failed login attempts.
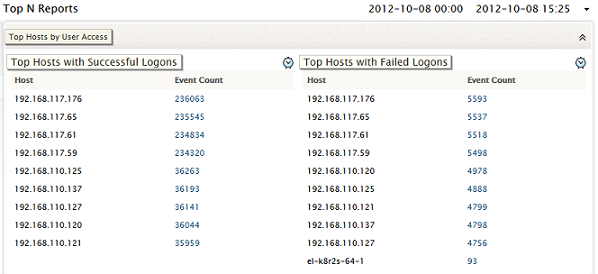
While the former is useful in tracking usage trends of hosts, the latter is important in analyzing which hosts are subject to the most number of security breaches.
You can use this report to decide if security policies need to be changed with respect to certain hosts, or tighten security measures across the network.
Top Users by Login
This report shows the top 'N' number of users with maximum number of successful logins, and the top 'N' number of users with maximum number of failed login attempts.
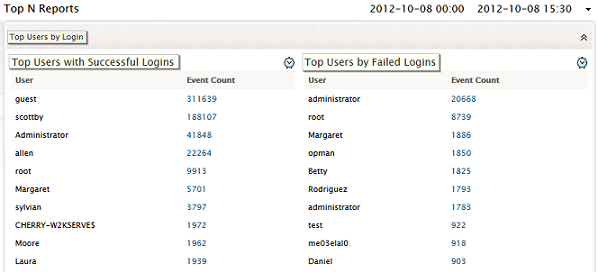
This report tells you which user logged into which host, using the password, and whether the user was successful or not. If a user has been accessing several hosts with the user name and password, this report will show you which hosts were used, and when. If the user has tried to log on, but was unsuccessful, this report will show you how many times the user was unsuccessful, on which hosts did the user try, and when.
You can use this report to identify errant users on the network, and set up security policies to track such users.
Top Interactive Login
In this report, only the logins done interactively through the UI. This report shows the users with maximum number of successful logins, and the users with maximum number of failed login attempts. This report tells you which user logged into which host, using the password, and whether the user was successful or not.
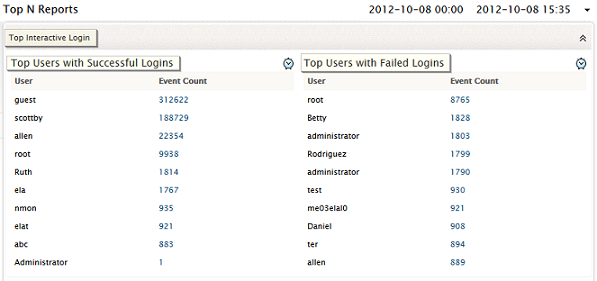
If a user has been accessing several hosts with the user name and password, this report will show you which hosts were used, and when. If the user has tried to log in, but was unsuccessful, this report will show you how many times the user was unsuccessful, on which hosts did the user try, and when.
You can use this report to identify errant users on the network, and set up security policies to track such users.
Top Hosts by Event Severity
This report sorts event logs received from all hosts by severity, and shows the top values for each event severity. At one glance, you can see which hosts have been generating more number of critical events, warning events, and so on. By default, the overall top hosts generating events of any severity, is shown, with the View Severity value set to All. You can view top 'N' number of hosts severity wise more number of events generated.
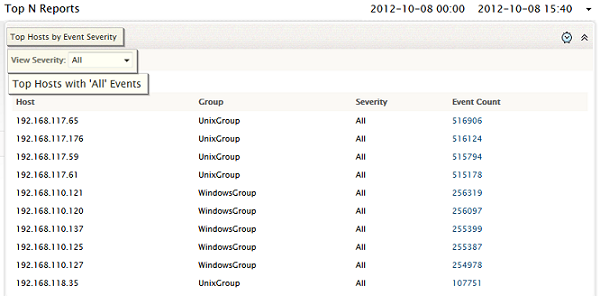
You can use this report to quickly identify the hosts that may be experiencing problems, thereby accelerating the troubleshooting process.
|
Note: Some event severity are applicable only to Unix hosts |
Top Processes by Event Severity
This report sorts event logs generated by processes running across all hosts, and shows the top values for each event severity. At one glance, you can see which processes have been generating more number of critical events, warning events, and so on. By default, the overall top processes generating events of any severity, is shown, with the View Severity value set to All. You can view top 'N' number of hosts severity wise more number of events generated.
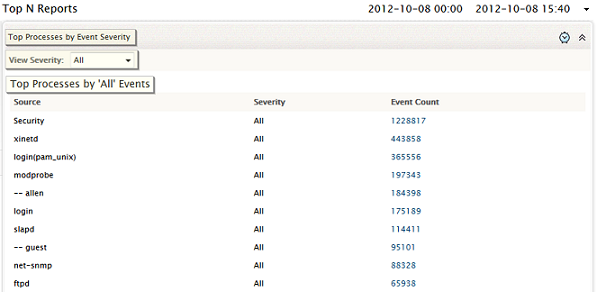
You can use this report to identify the processes with problems, investigate suspicious behavior of critical hosts, determine if there has been a worm or virus attack in the network, and also see which hosts have been affected, thereby reducing network downtime.
|