Access port vs. trunk port: Understanding the differences
Switch ports are fundamental components of your IT that enable network communication. These wired hardware devices are responsible for connecting and allowing data transfer between different devices and parts of your network that are connected to their ports. As they playing a critical role in ensuring network connectivity and availability, it is important that network admins have a clear understanding, mapping, and visibility into their network switch ports.
"Access ports vs. trunk ports" is a discussion that needs to be clearly understood and evaluated to leverage effective switch port deployment and overcome several switch port management challenges in your network. On this page, we'll explain the key differences between access ports and trunk ports including:
Access port 101: What is it and what does it do?
Access ports are network switch ports that are configured to carry network traffic for a specific virtual LAN (VLAN) only. These switch ports are connected with devices such as end user devices within a specified VLAN. This ensures that traffic from these components within the configured VLAN does not interrupt traffic from other VLANs. This in turn isolates the VLAN components from other network VLANs.
Access port frames and VLAN tags
Access ports facilitate communication between components using untagged data packets. Since the VLAN for a particular access port is pre-assigned, the access port does not rely on VLAN identifying 802.1Q or Inter-Switch Link (ISL) tags.
When traffic enters the access port, the switch adds an VLAN tag to the processed data frames to identify which VLAN the traffic belong to.
For instance, when an end device such as a user computer connected to the access port sends a untagged frame through the access port, the switch processes the frames to attach a VLAN tag to the frame. The VLAN tag identifies the appropriate VLAN the data frames are to be forwarded to.
Trunk port basics: What should you know?
These type of switch ports are configured to carry traffic and enable network communication between different VLANs. By default, trunk ports allow traffic from all VLANs in the network. However, network admins can prune or remove the required VLANs to restrict their traffic through the trunk ports. Trunk ports are often used to connect different switch ports in a hierarchical network design. They can also be used to connect switch ports to other network components such as DHCP servers and firewalls.
Trunk port frames and VLAN tagging
Trunk ports facilitate communication between different network components using tagged data frames. Relying on protocols such as IEEE 802.1Q and ISL, trunk ports tag each packet with a VLAN ID. The switch ports processing these data frames use the VLAN ID to forward the packet to its intended destination VLAN.
Since trunk ports process tagged data frames only, it is important to ensure that two neighboring trunk ports are configured the same. That is, if a trunk port is configured to allow traffic from VLAN A to VLAN B, the neighboring trunk port should also be configured to allow traffic from VLAN A to VLAN B.
For instance, trunk ports can be used to connect a core switch to multiple distribution switches, which are then connected to different access switches. This enables better scalability and increased networking efficiency.
Access port vs. trunk port: 7 key differences
Understanding the core data frame processing capability, functionalities, and key differences is critical to effectively configuring access and trunk switch ports in your network switch ports. With the fundamental difference between these ports being the number of VLANs they support, network admins should also consider the following key differences.
| Factor | Access port | Trunk port |
|---|---|---|
| Device connectivity |
|
|
| Configuration |
|
|
| Troubleshooting | Less complex, since access ports only affect a single VLAN. | Difficult, since trunk ports extend support for and affect multiple VLANs. |
| Layer 2 Vs. Layer 3 switching | Used in Layer 2 switching since they do not offer cross subnet data transfer. However, they still can be used in conjunction with Layer 3 switches for providing Layer 2 connectivity to devices on the same VLAN. | Offering cross IP subnet and VLAN data transfers, trunk ports can be used in both Layer 2 and Layer 3 switching. |
| Spanning Tree Protocol (STP) | Configured network STP implementation is supported on a per-VLAN basis. | Configured network STP is implementation is supported on a per-port basis. |
| Security | Offers better security and communication isolation, since access ports are typically configured with port security features, such as MAC address filtering and 802.1X authentication. Also, access ports reduce the chances for a rogue attacker to penetrate the network. | Since it enables communication between multiple VLANs with different security reinforcements, a trunk ports is comparatively less secure. |
| Broadcast domain | Supports only a single broadcast domain. | Supports multiple broadcast domains. |
Access ports vs. trunk ports: When to use which?
When choosing between access ports and trunk ports, along with understanding the core differences, it's also important to consider the specific requirements of the devices being connected and the overall network hierarchy.
Here are a few use case examples of when to use which switch port type:
- Local office workstations: The devices connected here often only require access to just one VLAN or IP subnet. Configuring the connecting switch ports with access ports ensures network admins control and visibility over which devices have access to which network resources and can help to prevent unauthorized access or attacks.
- Shared network devices: Office devices such as IP phones, VoIP gateways, video conferencing systems, and printers are accessed by users operating in multiple IP subnets or VLANs. These devices need to be connected to a trunk port to support this requirement. However, if these devices are to be used within one subnet, access ports are adequate.
- Wireless network environments: Wireless network enablers such as access points are required to enable access to and communication across several VLANs. This requires the access points to be connected to a switch port configured as a trunk port.
- Storage and gateway components: Networks deploying RAID systems and gateway devices, including network firewalls, should connect these devices to trunk ports to enable holistic network communication capabilities.
- High-availability environments: Trunk ports enable redundant connections in high-availability networks while also allowing access to multiple VLANs. By using trunk ports to connect switches in a HA network, network admins can create a resilient network topology that can handle traffic congestion and provide seamless failover in the event of a network failure.
Simplifying switch port management with OpUtils
ManageEngine OpUtils is a powerful switch port mapping and management software that provides a comprehensive set of tools for network administrators to manage their access and trunk switch ports with ease. Here are some feature highlights of OpUtils' reliable switch port mapping capabilities:
- Accurate and up-to-date port mapping: Enable a holistic, real-time view into your network's switch port connectivity. Easily identify the devices connected to each port and troubleshoot network issues quickly.
- Monitor ports with a centralized inventory: Maintain a centralized inventory of your network switches and their associated ports, their status, type of network connectivity, and network address of all connected end devices.
- Automate port scanning and mapping: With the customized port scanning schedule option, automate the process of port mapping. This eliminates the need for manual port mapping, which can be time-consuming and prone to errors.
- Integration with other OpUtils modules: The Switch Port Mapper module tightly integrates with other OpUtils modules, such as IP Address Manager and Rogue Detection, to enable hassle free switch port and end IP device monitoring.
- Easy-to-use UI and dashboard widgets: OpUtils has a user-friendly interface that is easy to navigate and use. This makes it simple for network administrators to quickly find the information they need within just a few clicks. Also, the dashboard widgets display up-to-date critical switch port metrics that offer insights into the status of network switch ports at a glance.
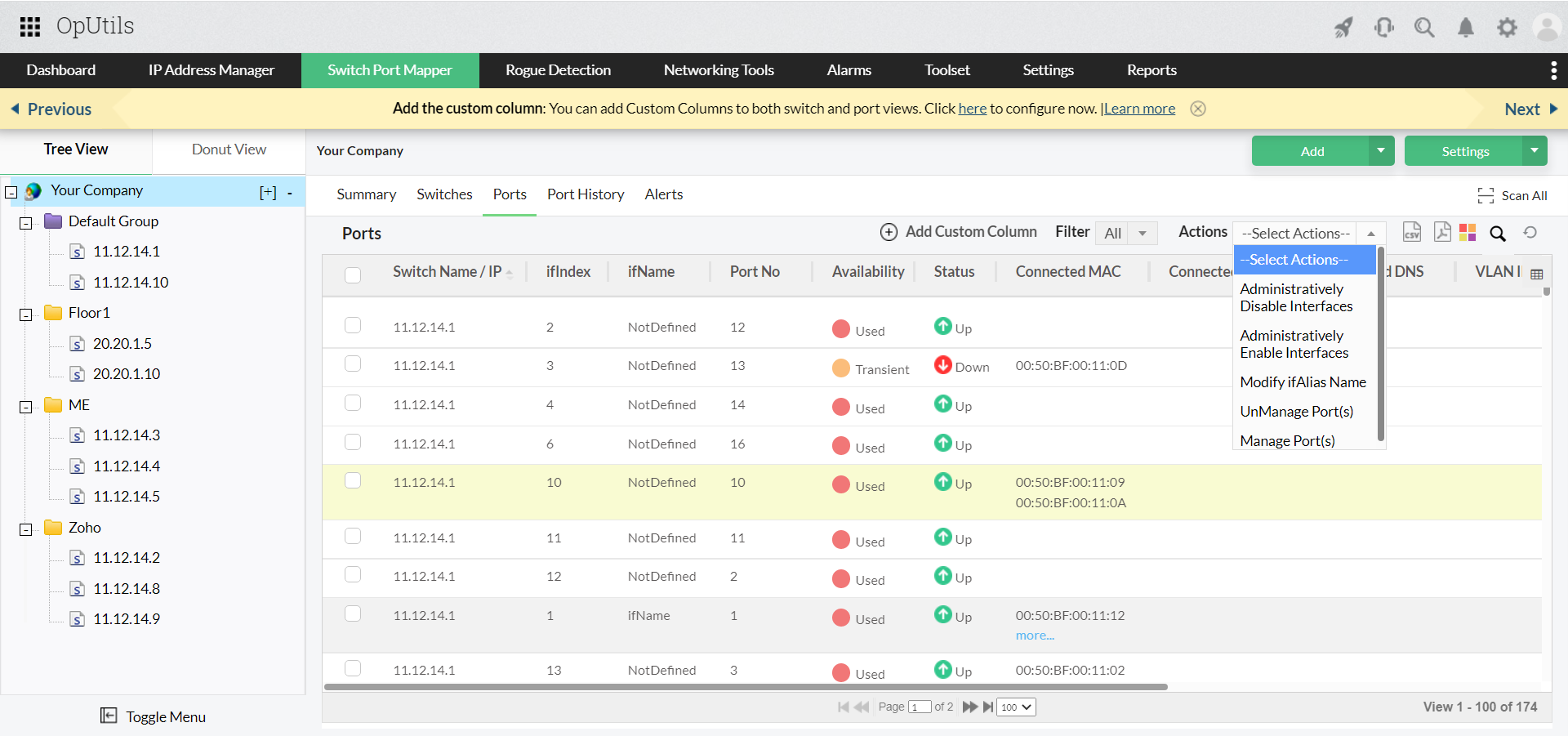
Overall, OpUtils is a reliable choice for switch port mapping and management, providing network administrators with accurate, up-to-date, and customizable information about their network, while also providing a user-friendly interface and seamless deployment with no additional requirements.
So why wait? Download a free, 30-day trial of OpUtils or schedule a personalized live demo with one of our product experts.
Ensure simplified switch port management with OpUtils
Try OpUtils for free today