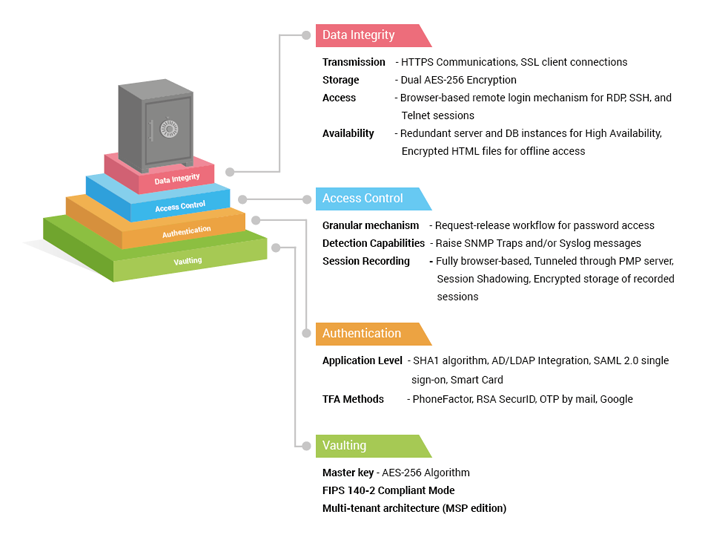
Password Manager Pro serves as a centralized repository for organizations to consolidate sensitive passwords. A strong vaulting mechanism, AES-256 encryption, dual encryption, encryption key isolation, and other standard good practices ensure rock-solid data security.
Password Manager Pro uses 256-bit Advanced Encryption Standard (AES) to protect resource credentials, digital keys, and files. Acknowledged by both the National Institute of Standards and Technology (NIST) and the National Security Agency (NSA) as the strongest-known encryption algorithm to date, AES-256 is an obvious choice for enterprises when it comes to securing super-sensitive information.
Password Manager Pro encrypts data twice: once at the application level and again at the database level, both with built-in AES 256 functions. The first-level encryption key, which is auto-generated and unique for every installation, encrypts the data using the AES-256 algorithm at the application level. Password Manager Pro then pushes the encrypted data to the back-end database for storage, where the next level of encryption takes place, again with AES-256 standards.
Password Manager Pro uses two keys: an installation master key and a database key. By default, the installation master key cannot be kept in the installation folder, ensuring that the encryption key and encrypted data do not reside together. You can store the installation master key in a physically separate server or device to ensure that it is available to the server during application start-up. Thus, the key is held only in the server memory and never written. Password Manager Pro also enforces periodic rotation of installation master keys as a best practice, with easy options to automate the rotation.
Like the installation master key, the database key can also be stored in any secure location, leaving the key accessible only to the server. This makes the vaulting mechanism secure by design.
The RDBMS is always configured to accept only secure connections (forces SSL mode for client connections) and clients can connect only from the same local host. In cases where the web server and the RDBMS have to reside in separate servers, the configuration enforces connections only from configured IP addresses.