Since the advent of identity security and multi-factor authentication (MFA), experts have developed a variety of methods to verify user identities. Over the years, as threats to user identities escalated, the security mechanisms used for authentication also advanced. From basic methods like passwords, to advanced methods like FIDO2 passkeys and biometrics, organizations today employ different authentication methods to achieve MFA for Windows and other crucial endpoints. Recent developments like risk-based authentication have further reinforced identity and access security while ensuring unhindered user productivity.
But not all authentication methods are created equal. The technology employed by some authentication methods to validate user identities can be susceptible to attacks and bypasses. For example, a password—the most rudimentary yet widely used authentication method—is vulnerable to various attack forms like brute-force attacks, password spray, and keylogging . Likewise, security questions and answers can falter against malicious impersonators with knowledge of a user's personal information. Although it was popular for a while, SMS-based authentication is vulnerable to exposure by SIM swapping and SIM interference. Email verification codes are also not exempt from exposure.
On the other hand, there are authentication techniques that can stand their ground against hacks. Authenticator apps are one such method.
Authenticator apps are identity verification platforms built for mobile devices. They help include additional stages of authentication to create secure MFA flows for access into network endpoints and resources. Popular examples of authenticator apps include Google Authenticator, Microsoft Authenticator, Authy, and Duo Mobile. They are predominantly available to users at no cost. They are generally developed to work on multiple types of mobile devices and OS platforms.
Authenticator apps primarily offer time-based one-time passwords (or TOTPs) as the authentication method. During setup, the user will configure the authenticator app by scanning a QR code displayed in the endpoint client. In this process, a private key is shared between the client and the authenticator app. The TOTPs are then generated in the authenticator app based on this shared key and the device time. They are then used to verify a user's identity, with each code remaining valid only for a short time before a new one is generated.
Here's how a typical authentication attempt is handled by an authentication app:
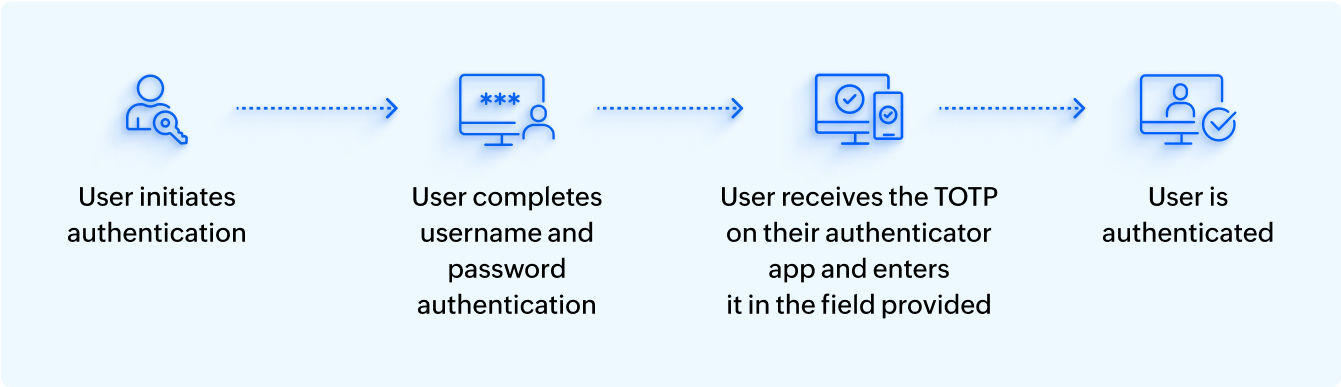
Authenticator apps often provide backup codes when the user cannot access the app or their mobile device; however, users have to generate these codes prior to when they need to authenticate their identity without the app or device.
Authenticator apps have an edge over other identity verification methods—like passwords, SMS- and email-based verification codes, security questions and answers, and push notifications—for the following reasons:
To maximize the benefits authenticator apps have to offer, it is vital to incorporate them as part of a holistic identity security policy. ManageEngine ADSelfService Plus—an identity security solution with MFA, SSO, and self-service password management capabilities—helps achieve this. ADSelfService Plus offers endpoint MFA to secure local and remote machine logins, enterprise application SSO, VPN access, and OWA logins. The solution supports the following authenticator apps for MFA:
Along with these apps, the solution also supports integrating any custom or in-house TOTP provider. By choosing ADSelfService Plus, you can create an effective authentication policy that makes the most of your desired authenticator app with the following capabilities:
For a further look into ADSelfService Plus' identity security capabilities, get your free, 30-day trial of the product here.