Today's enterprise workflow heavily depends on applications that simplify crucial organizational processes like project management, asset management, accounting and finance, employee onboarding, and more. IT administrators are faced with the daunting task of onboarding users onto each of these applications, and users often have to juggle multiple user identities and authentication processes. Ensuring the integrity of these user identities is a crucial responsibility, and IT admins utilize single sign-on (SSO) and Security Assertion Markup Language (SAML) to ensure security. Here's a deeper look at these concepts, their differences, and their correlations.
SSO simplifies the user authentication and access management process. Once enabled, users simply have to authenticate their identity with a central application, and the user identity information is then reprocessed for efficient access to other applications. This means, users can log in once to an application, and easily access others, even switching between them without logging in again.
SSO provides these advantages to enterprise users and IT administrators:
SAML is an open-source XML-based standard that securely exchanges authentication and authorization data between applications without exchanging the actual credentials. Essentially, it is one of the many standards that can be used to achieve SSO. The typical SAML authentication process achieves SSO using these components:
Identity provider: The application that serves as the centralized authentication system. It verifies user identity during authentication attempts and stores the information.
Service provider: The target application(s) the user intends to log into. This utilizes the authentication and authorization data submitted by the identity provider to permit access to the user.
SAML assertions: XML files containing the user's authentication and authorization information.
For SAML authentication to work, the identity provider and service provider need to be configured to send and receive the SAML assertions. The user account's attributes also need to be mapped between the two providers to ensure that the user information is interpreted and used to authenticate and authorize the user into the service provider as intended.
SAML remains one of the most widely adopted standards across industries since:
| SSO | SAML |
|---|---|
| It is a form of user authentication technique that allows access to multiple applications with a single set of credentials. | It is an authentication standard that exchanges authentication and authorization information between applications via XML. |
| It is used to relieve users of redundant logins and improve their productivity by providing a single platform for authentication. | It helps reduce the attack surface and improve identity security by centralizing authentication to the identity provider. |
| This can be achieved via SAML, OAuth, and OpenID Connect. | This can be used to achieve identity provider-initiated and service provider-initiated SSO. |
Most SAML-based SSO providers generally support two ways of SSO: identity provider-initiated SSO and service provider-initiated SSO. Here's the workflow of both methods:
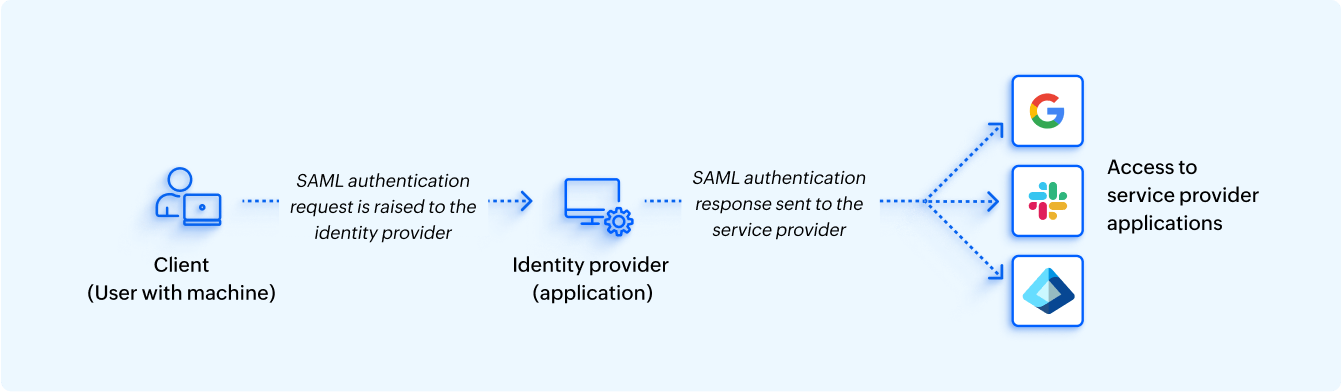
1) During an identity provider-initiated SSO attempt, users first access the identity provider and authenticate themselves. The identity provider forwards the authentication status to the integrated service provider applications. Finally, users will be able to access their accounts in the service provider applications, often from a centralized console, without logging in.
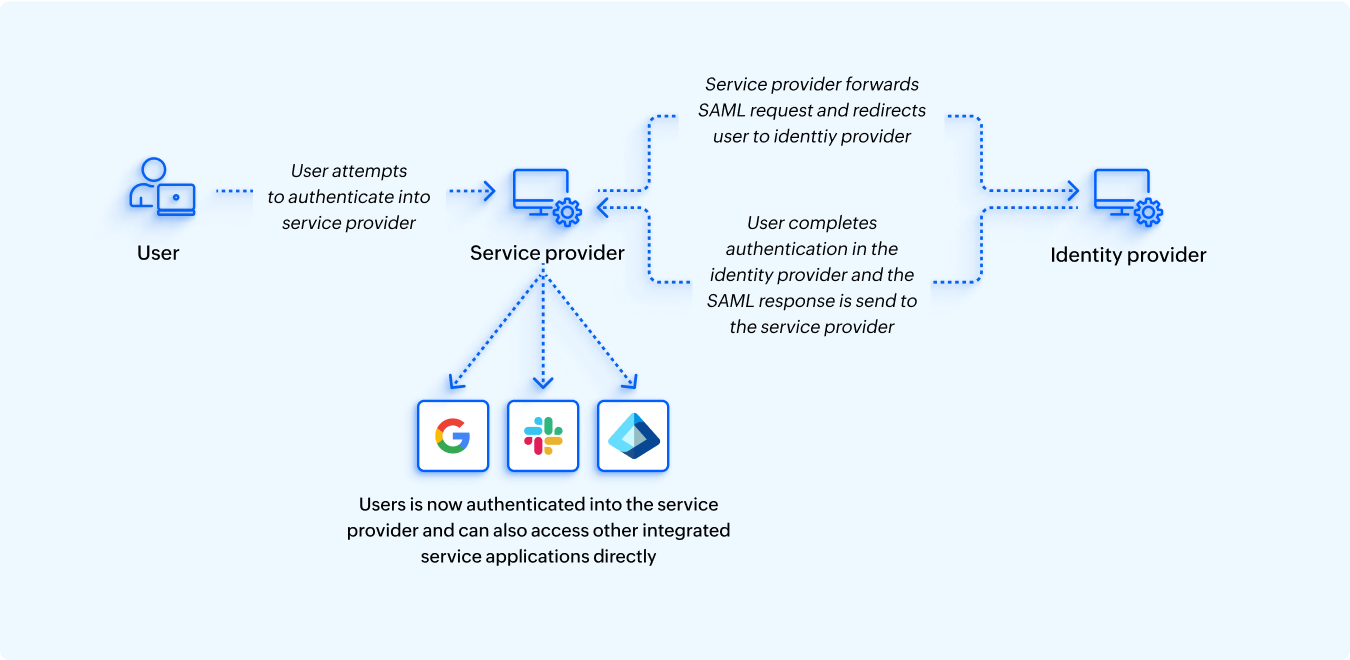
2) During a service provider-initiated SSO attempt, users first access the service provider application and initiate authentication. The service provider redirects the user to the identity provider and the user authenticates themselves with the identity provider. The identity provider then relays the authentication data to the service provider and provides access to the application. The user can then access any other SSO-integrated application, and the same authentication information will be used to permit access to these applications as well.
SAML SSO can benefit the enterprise and the end user in multiple aspects when implemented effectively. ManageEngine ADSelfService Plus, an identity security solution with MFA, SSO, and self-service password management capabilities, provides enterprise SSO for applications using SAML, OAuth, and OpenID Connect protocols. Here are some factors that help you create an ideal SSO system using ADSelfService Plus:
No, SSO is a user authentication process that allows a user to access multiple applications or services with one set of login credentials. SAML is a standard used to enable SSO by exchanging authorization and authentication data between the identity provider and service provider.
Yes, SAML is one of the many standards that can be used to enable SSO. Some other standards are:
| SAML | OpenID Connect |
|---|---|
| The SAML standard is used to perform authentication and authorization into enterprise applications for SSO. | The OpenID Connect standard is mainly used to authenticate users accessing protected resources. It can be used along with OAuth, which can perform authorization, to achieve SSO. |
| SAML uses XML-based messages to exchange authentication and authorization information. | OpenID Connect uses JSON web tokens to exchange authentication information. |
| In a SAML flow, the user attempts to access a service provider. The service provider redirects the user to an identity provider for authentication. After successful authentication, the identity provider sends a SAML assertion to the service provider, which grants access to the user. | In an OpenID Connect flow, the user attempts to log in to an application-relying party, which redirects them to the OpenID provider for authentication. The OpenID provider authenticates the user and issues an ID token and optionally an access token. The relying party uses the ID token to verify the user's identity and possibly uses the access token to access additional resources. |
Yes, passkeys are easy to create and use when compared to other authentication mechanisms, like passwords and passphrases. They are a preferred option for identity verification because they don't need to be memorized, they use secure cryptographic keys, and they cannot be hacked.
| SAML | OAuth |
|---|---|
| The SAML standard is primarily used for authentication and authorization into enterprise applications. | The OAuth standard is primarily used to authorize access to protected resources. To achieve SSO, it can be used along with OpenID Connect, which can perform authentication. |
| SAML uses XML-based messages to exchange authentication and authorization information. | OAuth uses JSON web tokens to exchange authorization information. |
| In a SAML flow, the user attempts to access a service provider. The service provider redirects the user to an identity provider for authentication. After successful authentication, the identity provider sends a SAML assertion to the service provider, which then grants access to the user. | In an OAuth flow, the user's client attempting to access specific resources is redirected to an authorization server, where they are granted the required permissions. The authorization server issues an authorization code, which the client exchanges for an access token. The client then uses this token to access the resources on the resource server. |
While SAML and OAuth2.0 are different standards, they can be used to create a hybrid authentication and authorization system. For example, SAML assertions can be used to authenticate the user into the application, while OAuth tokens can be used to authorize users to access protected resources in the application.