Last updated on: October 09, 2025
The comprehensive guide to help desk software is a one-stop resource for answers to some of the most common questions related to help desks.
This guide attempts to build a complete understanding of help desks and their implementation, best practices, metrics, and other key aspects. It can help IT teams establish, optimize, and maintain an efficient IT help desk.
In this help desk software guide, we will discuss the following:
- What is help desk software?
- Features of a help desk software
- Help desk software for small business (workflow)
- Help desk vs. service desk
- Choose help desk software for small business
- Help desk best practices
- Help desk automation
- Integrated help desk software
- 6 Challenges faced by help desk
- Future of help desk support
- Help desk software glossary of terms
- Download IT help desk software evaluation kit
IT help desks deliver a variety of IT services in an organization. The help desk typically serves as the single point of contact for any requirement, issue, or assistance end users need to access technology services.
In mature organizations, the help desk guarantees timely assistance and prompt resolution of issues by defining and publishing their assured service levels. By delivering such high levels of service, organizations can meet their business goals and increase their leverage in the market.
What is IT help desk software?
IT teams typically deploy help desk software to manage the IT ticket life cycle, automate routine tasks, and optimize their processes and workflows, which directly results in increased productivity, reduced costs, better service levels, and improved customer experience.
Some key features of help desk software include:

Incident and service request management
Manage the life cycle of incidents or service requests raised by end users.

Problem and change management
Manage the life cycle of a problem or change from creation to closure.

Self-service portal
Allow users to resolve common issues on their own and reduce the help desk technician's workload.

Service level agreement (SLA) management
Manage the quality and timeliness of services provided to end users.

Asset management
Manage an organization's hardware and software assets.

Other features
Some help desk management software may also include other modules for project management, contracts, purchase management, etc.
Help desks can be classified into different types based on deployment method, size of target audience, and source code availability, as listed below:

Cloud
- SaaS help desk
- Hosted on vendor's server
- Scalable in size
- Recurring subscription costs

On-premises
- Hosted on local server
- Requires in-house IT team
- One-time license fee
- Recurring cost for services

Enterprise
- Feature-rich
- Highly customizable
- More than basic help desk
- Part of a bigger service desk

Open source
- Source code is accessible
- Might be free
- Very flexible
- Low vendor dependency
Cloud-based help desk software
- This is a SaaS help desk tool, hosted on the vendor's server.
- Customers usually subscribe to the service on a monthly or annual basis and access it through a local desktop or mobile client, or through the vendor's website.
- Cloud-based help desks are typically preferred by small and medium-sized businesses that lack an in-house IT team. However, many help desk vendors can scale up their offerings to cater to larger organizations as well.
On-premises help desk software
- This type of help desk tool is hosted locally on the customer's server.
- Customers usually pay the vendor a one-time payment to purchase a software license, but recurring payments can be made for associated services like customer support, integrations, etc.
- Since on-premises help desk ticketing software is hosted and maintained locally, customers are typically enterprise-level organizations with in-house IT teams and resources to procure and maintain their own server.
Enterprise help desk software
- A highly feature-rich help desk software solution that supports a number of complex modules.
- Enterprise help desk ticketing software can be customized to fit a particular organization's or industry's workflows.
- Since enterprise ticketing system software supports a wide number of complex modules, it goes beyond IT services and support and helps improve the overall efficiency of an organization.
- Usually, enterprise help desk systems are a part of help desk management, and they frequently come bundled with other modules like CRM.
Open source help desk software
- This type of help desk software allows open access to its source code
- This type of help desk software system is typically preferred by organizations that have strong in-house programming know-how to leverage the unrestricted access to source code.
- With open-source help desk software, users need not depend on the vendor for integrations, bug fixes,
customizations, etc.
Free help desk software
- As the name suggests, such help desk applications can be used free of cost and are therefore known as freeware.
- This software is favored by individuals or small businesses with a minimal number of technicians and end users.
- Such software offers limited functionality and integration options.
For a long time, the terms "help desk" and "service desk" have been used interchangeably and to the average end-user, the difference often remains blurry. Here are some of the key differences between help desks and service desks.
| Help desk software | Service desk software |
|---|---|
| Help desks are user-centric | Service desks are business-centric |
| Help desks are point solutions | Service desks are integrated |
| Help desks are reactive in nature | Service desks are more proactive |
| Help desks are for end users | Service desks are for both technicians and end users |
| Help desks are a subset of service desks | |
Help desks are user-centric, while service desks are business-centric
The core function of a help desk is to handle incidents and service requests.
Help desks aim to provide a quick fix to any issues users face by handling a request through its life cycle and returning the service to its normal state as soon as possible. So the focus of a help desk is largely limited to end users.
On the other hand, a service desk is more comprehensive in nature. Service desks align with organizations' business goals and manage information delivery by using processes that follow industry best practices.
In short, service desks are built to focus on best practice processes and business goals.
Help desks are point solutions, while service desks are integrated
An IT help desk is a stand-alone solution that performs tasks related to resolving help desk tickets.
Help desks most often offer basic incident and problem management capabilities with SLAs and self-service portals.
An IT service desk, however, is a more elaborate system with complete IT management capabilities.
Service desks integrate with other IT and non-IT management applications and are therefore capable of providing advanced services like change management, asset management, network monitoring, CMDBs, etc.
Help desks are reactive in nature, while service desks are more proactive
An IT help desk usually provides support to end users. This firefighting setup makes help desks predominantly reactive to the issues that come up in day-to-day IT operations.
An IT service desk is more proactive since it ensures that IT operations are running as expected and will continue to run in the future.
Although service desks also perform many reactive tasks as well, their major function is proactively ensuring that IT services are always up and supporting the business as needed.
Help desks are for end users, while service desks are for both technicians and end users
An IT help desk usually allows end users to raise tickets and receive support. Help desks generally offer other services like knowledge bases and self-service portals, which are oriented toward end users.
A service desk, however, offers capabilities like change and asset management, which are complex, technician-facing services.
Help desks are a subset of service desks
A help desk can exist as a stand-alone service that provides support to end users. But since service desks offer more complex services in addition to basic incident and problem management, most organizations incorporate the help desk as a part of their service desk.
Simply put, many organizations today use a help desk without a service desk, but not the other way around.
Any organization that uses IT capabilities needs a system for managing them, too. IT trouble ticketing software adds value by helping organizations better manage IT operations. The points below illustrate how organizations can benefit from using a help desk solution.
Single point of contact
An IT support ticket system converges all inbound communication and converts the help desk into a single point of contact for all IT-related questions.
Automation
Help desk software automates tasks, processes, and workflows, reducing human error and the technician's workload.
Customization
Each organization can customize forms, templates, workflows, etc. to meet their needs.
Centralization
All data, requests, queries, and tickets are centralized in one place, which makes it easier to access and manage them.
Efficiency
With well-defined workflows and processes, help desk support software helps eliminate redundant tasks and boosts efficiency.
Continuity
With the right tools, IT teams can minimizes service interruptions.
SLA management
An IT help desk ticketing system allows users to set, track, and manage SLAs to ensure that services are provided on time.
Fosters collaboration
Different teams, technician groups, individual technicians, etc. can collaborate easily through help desk software.
Transparency
Requesters and technicians can view the accurate, current status of their requests and tickets.
Risk management
Users can assign, analyze, and manage risks associated with an incident, problem, or change.
Prioritize requests
Any incoming incident or service request can be given an appropriate priority and handled accordingly.
Self-service
End users can access solutions to common issues to fix problems themselves.
Reporting and metrics
Help desk software allows users to define and track important key performance indicators (KPIs) and generate reports to assess overall help desk health.
Improves customer satisfaction
A better managed IT help desk leads to higher satisfaction among end users.
There are certain must-have features every IT help desk can benefit from. Some of these key features can be found listed below.
The value added by IT help desk management software goes beyond IT operations. Help desk software benefits all the stakeholders of an IT help desk: the technicians, end users, management staff, and the entire organization itself.
End users
- A one-stop solution to all IT-related issues or questions.
- Readily available ticket history and status information.
- Access to self-help articles to solve common issues.
- Timely service, largely due to the SLA management capabilities of help desk ticket management software.
- Real-time notifications about requests or tickets.
- A standardized way to approach the IT help desk with questions or issues.
Technicians
- Centralized database of end user details, tickets, workstation history, and resolution tools.
- History of all tickets and actions performed on them, along with technician details.
- Repository of solutions in a knowledge base.
- Automated workflows and processes.
- Real-time notifications about requests and tickets.
- Multi-tier, organized help desk architecture.
- KPI tracking and measurement.
IT management
- Implemented best practices.
- Increased IT help desk productivity.
- IT workflows and processes.
- Increased transparency in IT operations, leading to better time and resource management.
- High-level or granular reports to aid in decision-making.
Business
- IT help desk converted from a cost center to a profit center.
- IT help desk becomes a strategic asset instead of a tactical one.
- Ensured continuity of IT services and operations.
- Reduced costs associated with higher productivity, a more efficient help desk, and fewer redundant tasks.

Installation and usage
- Straightforward setup
- Easy to use
- Processes and workflows aligned with industry recommended best practices
- Multiple deployment options: On-premises and cloud
- Intuitive user interface
- Multi-channel ticket creation: Email, phone call, and self-service portal
- Minimal learning curve
Modules
- Incident management
- Request management
- Problem management
- Change management
- Service level agreement
- Service catalog
- Self-service portal
- Asset management
- Knowledge base
- Reporting
- End-user surveys

Automation
- Create tickets from emails
- Automatic escalation of SLAs
- Automatically assign tickets to technicians
- Automated password reset tool
- Automated workflows
- Automatic notifications for requesters and technicians
Customization
- Customizable dashboards
- Customizable self-service portal
- Customizable forms and templates
- Customizable KPIs and reports
- Drag-and-drop widgets

Reporting
- Standard reports
- Custom reports
- Query reports
- Scheduled report generation
- KPI tracking and analysis
Mobility
- Native mobile apps for major platforms like Android, iOS, Windows, and Blackberry OS
- Complete capabilities and features, as supported by desktop version, in mobile apps
- Features and interface optimized for mobile devices
Security
- Role-based access permissions
- Secure communication with data encryption
- Audit logs
Integration
- Seamless native integration with other IT management tools to build an ITSM suite
- API integrations with third-party solutions
- Central command center for managing all IT operations

Implementation
- Quick and easy implementation
- Client Software
- Support for open standards
- No additional programming for client or database customization
- Documented database

System requirements
- Operating systems supported
- Linux
- Windows
- MacOS
- Databases supported
- Oracle
- SQL
- MySQL
- Postgres
- Browsers Supported
- Firefox
- IE
- Chrome
There are a vast number of ITSM solutions available in the market, and each one has its own strengths and weaknesses. This might complicate the decision-making process, making it hard to arrive at the best fit when an organization decides to invest in ITSM software.
A systematic approach to decision making can help simplify the evaluation process.
Follow these four steps to find the right help desk solution for your organization's requirements:
Set objectives
The first step is to arrive at an unambiguous understanding of the problem you need ITSM software to solve. For example, the problem might be managing tickets or assets, implementing changes, and so on.
This helps narrow the focus down to a specific problem area and provides direction for the decision-making process. You should also define your expectations at this stage.
For example, does your team expect the software to aid in communication via email and notifications, or do you expect powerful reporting facilities? Setting your expectations beforehand will help you get the most out of demos and trials later.
Gather requirements
In this step, you should create a detailed list of requirements. You can use the problems and expectations identified earlier to begin charting your requirements. Performing a gap analysis can also help you build an exhaustive list of requirements.
This involves drawing up the existing and desired states and then comparing them to understand the gaps between them. Based on this, you can create a list of requirements that will help plug the identified gaps.
Budget and ROI
As is the case with any purchasing decision, it is important to know what your budget is to streamline the evaluation process. Besides your budget, you should also consider your return on investment and payback period.
Depending on your organization's structure and practices, returns can sometimes appear in terms of savings on resources and increased output as a result of better and more consistent service quality.
In some cases, organizations choose to use the charge-back model where other departments pay the IT department to use their services. In such scenarios, you can calculate ROI and payback period directly.
Evaluation
After completing the first three steps, you'd have narrowed your search for an IT support ticket system down to a few options. Listed below are some criteria you can use to evaluate your short list of help desk software:
- Feature fit: The help desk software's features should be able to plug the gaps identified during the requirement gathering stage and should help achieve the goals you set in the objective setting stage.
- Deployment: When considering deployment, you should ask yourself two questions: Is your organization allowed by law to use software hosted in the cloud? Can you host the application in-house? These considerations can help you decide between on-premises or cloud deployment.
- Business model fit: The structure, processes, command chain, and work culture of your company should fit the solution. If your organization has a multi-tier help desk, or offices in multiple locations, you'll need a help desk tool that supports this structure.
- Adherence to industry best practice frameworks: Industry recommended best practice frameworks provide a solid foundation for delivering efficient IT support services. By choosing an ITSM solution that aligns with globally recognized and proven standards, you can ensure a higher level of service quality and user satisfaction.
- Scalability: The solution should be scalable to provide room for future business growth. It should be able to adjust for more technicians, end users, modules, and other IT management tools.
- User experience: The application should be easy to use and come with an intuitive interface. That way, your technicians remain productive and end users don't feel averse to using your help desk for raising tickets.
- Support: You should always consider the quality of support provided by the vendor while evaluating alternatives. Within this, timeliness and available support channels can be two important decision points.
- Multi-language support: If your organization operates in more than one country, you may want a solution that supports multiple languages.
- Pricing: ITSM solutions usually come with different licenses at different prices. While choosing help desk software, maintain a balance between features and license price based on your budget. Look into the cost of scaling up, receiving support, and annual maintenance.
- Security: To protect company information, the solution should offer security features like data encryption and access permissions.
- Integrations: If you're looking to convert your IT help desk into a central command center for all IT operations, or to make your help desk work with other applications like CRM, you should consider native or API integrations.
Small businesses
Small businesses usually operate with small IT departments and only a handful of technicians. The small staff size makes it a challenge to handle all the incoming requests on time. Carrying out changes or maintaining assets is also difficult to do manually.
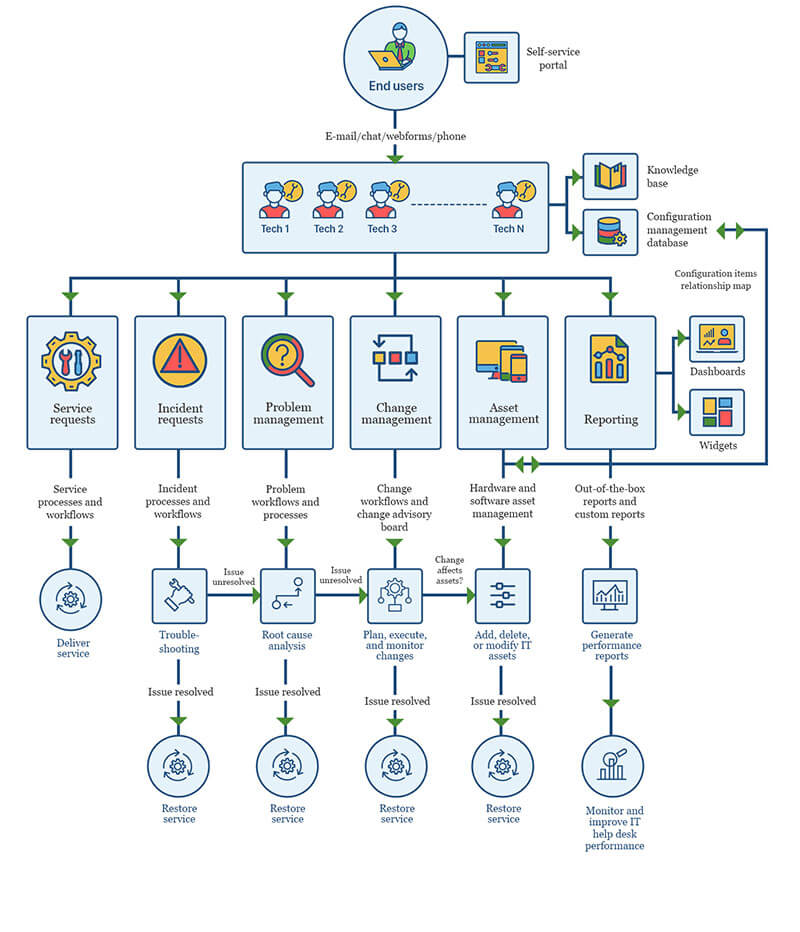
Therefore, small businesses can gain many benefits from implementing IT ticketing system software, such as:
- Organized management of IT operations from a central location.
- Less burden on IT staff to carry out tasks manually.
- Empowering end users through a self-service portal.
- Reliable data automatically generated and stored in the system instead of manually updated in spreadsheets.
- Automatic generation and maintenance of asset inventories through network scans.
- Safeguards against hefty penalties by ensuring compliance during audits.
- Readily available reports to improve performance and demonstrate value.
Healthcare
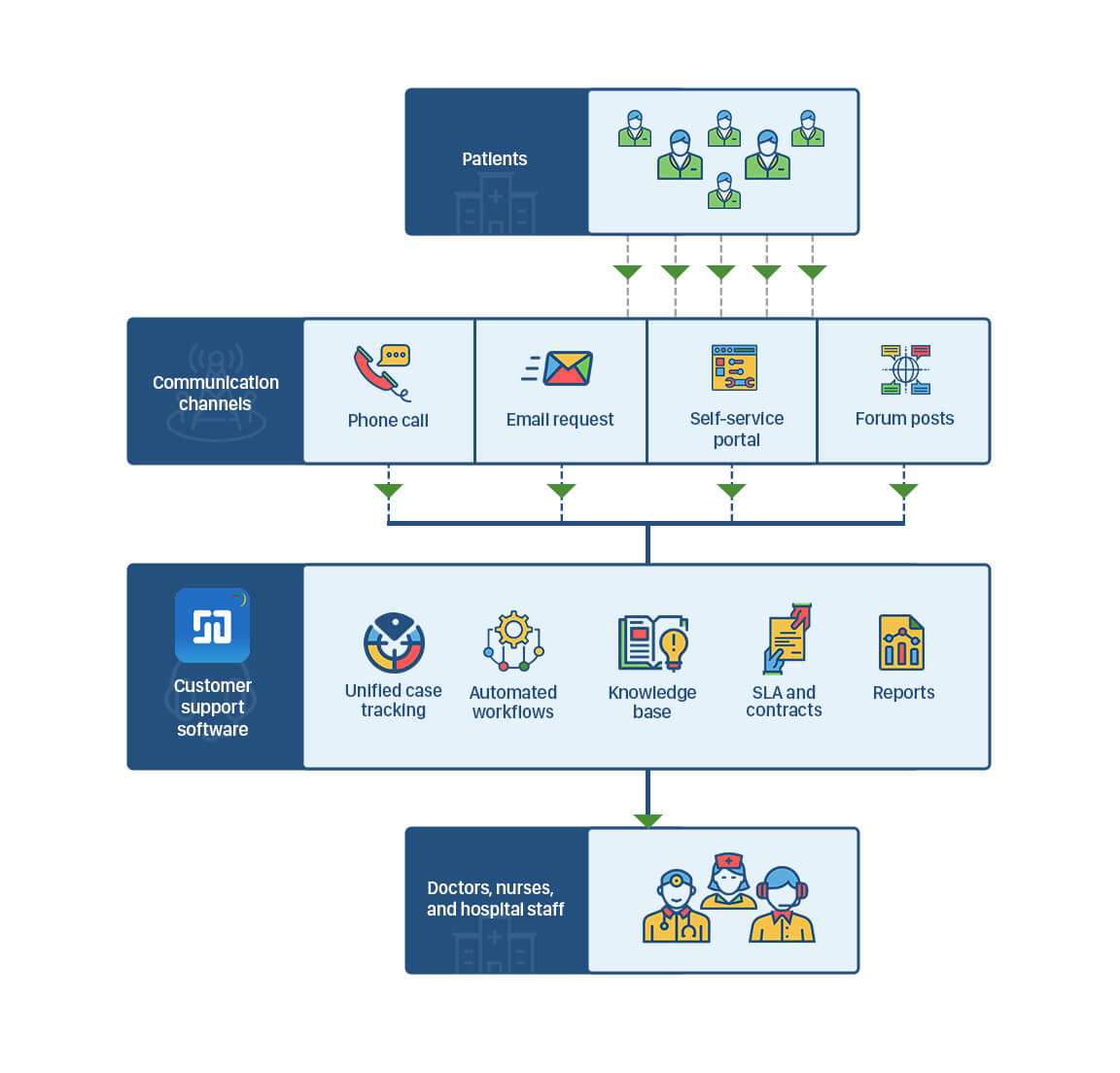
In the healthcare industry, time is critical. A hospital's help desk must be able to offer quick service when needed. Hospitals usually use a lot of equipment that is critical to patient's lives. This makes it important for help desks to manage equipment efficiently and without any errors.
IT support desk tools can help healthcare organizations in the following ways:
- Assign priority to tickets that are crucial to the hospital's operations. For example, an issue with a workstation/node in the ER needs immediate attention, while a workstation in the payroll department can wait.
- Automatically route the tickets to the right technician or support group to ensure immediate resolutions.
- Help ensure that incidents are resolved on time with SLAs and automated escalations.
- Use vendor and contract management capabilities to optimize purchasing of expensive medical equipment.
IT support
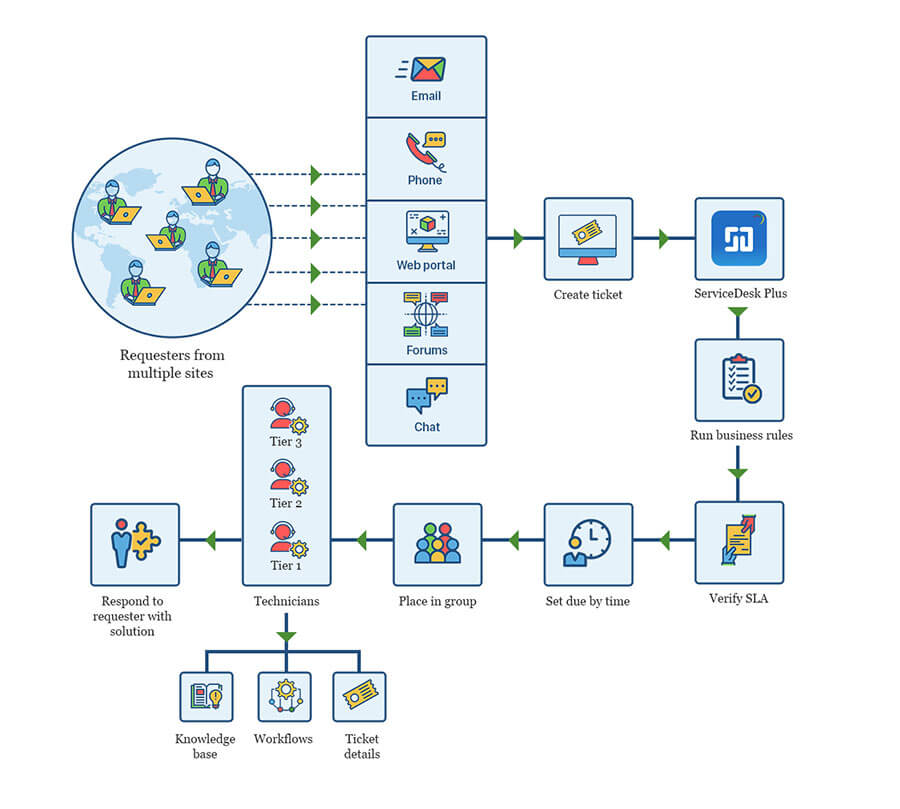
IT support professionals are naturally the best fit for an IT help desk ticketing tool. In the absence of a solution, IT teams usually work with spreadsheets and email, which is a slow, inefficient, and error-prone approach.
Out of the numerous benefits that IT help desk solutions offer IT support teams, a few key benefits are listed below:
- Centralized control of all IT operations.
- A comprehensive knowledge base to help end users and technicians alike with known and approved solutions to common issues.
- Automated processes and workflows that reduce time, effort, and errors.
- Simplified communication through emails from within the application as well as notifications.
- Native problem, change, and asset management capabilities in addition to incident and service request management.
- Tracking KPIs and metrics and generating in-depth reports.
Education

Educational institutions usually deploy workstations for teaching staff, administrative staff, and students, making their user base fairly large.
In many cases, schools rely on IT for computers, projectors, and software applications. So, to provide reliable IT service to a large user base, educational institutes can use IT help desk software to:
- Provide a central portal for students to create service requests like access to the college Wi-Fi network.
- Provide a common platform for IT announcements.
- Simplify student enrollment and the onboarding process.
In order to maximize your help desk's efficiency and effectiveness, implementing best practices is crucial for improving help desk performance. Here are some key best practices that you should consider:
Ensure that the IT help desk is the single point of contact (SPOC)
Your help desk should be the only point of contact for all IT-related issues. This reduces confusion among end users, collects all tickets in a central repository, and streamlines help desk processes.
Build a knowledge base
Building and maintaining a knowledge base allows users to find resolutions to common problems, which results in fewer tickets being logged. A knowledge base also helps technicians provide resolutions by assisting them with known solutions.
Archive known resolutions to expand your knowledge base
Solutions to common issues should be archived in the knowledge base after approval by designated technicians.
Set up automation
Automated processes and workflows provide numerous benefits to an IT help desk, like timeliness, accuracy, cost savings, higher efficiency, etc.
Implement a self-service portal
Empowering end users to create their own tickets accurately with the help of self-service portals allows technicians to focus on more critical tasks.
Offer multiple communication channels
Emails from within the application and notifications to both users and technicians help disseminate critical information and maintain transparency in the help desk.
Track and analyze KPIs
You should measure and analyze key metrics and KPIs to understand how well your help desk is performing and build future roadmaps.
Generate and schedule reports
You can use help desk reports to present a quick overview of the state of IT operations to high-level management or to give detailed data points to IT staff and managers.
Implement native asset management
You can manage your organization's hardware and software assets if your help desk application offers native asset management. This leads to better license compliance, purchase management, hardware asset scanning, and tracking.
Utilize native problem and change management
In addition to incident management, your help desk should also offer problem and change management. Bringing them together on the same platform streamlines overall IT operations.
Set up integrations
An IT help desk solution that supports integration with third-party applications has the potential to scale up into a bigger system capable of managing all IT operations from a single application.
Develop SLAs
IT help desks should support SLAs with automatic escalations to ensure that service is consistently delivered on time.
Offer technician training
Technicians should be trained regularly to keep them up-to-date with the latest technologies, best practices, and company policies. Also, feedback from technicians should be collected and considered to balance out each technician's workload.
Implement a multi-tier architecture
Structure your help desk in a multi-tier architecture to maximize its efficiency. This structure supports a better flow of tickets, with complex issues finding quick resolution by higher level technicians and simpler issues being serviced at lower levels.
Send out end-user surveys
Collecting feedback from end users helps organizations understand the pain points users face and paves the way for continuous service improvement (CSI). You can administer surveys either periodically or every time a ticket is closed.
KPIs are measurable values that help you assess the success of a particular activity. Any organization with an IT help desk should always have a set of KPIs dedicated toward monitoring its health, operational efficiency, and output.
The most important reasons to measure help desk KPIs are listed below:
Setting tactical help desk goals
Similar to any function in an organization, every help desk has its own goals. KPIs help system administrators and managers visualize and quantify these goals, making it easier to understand, communicate, and achieve them.
For example, an IT help desk with a goal to resolve as many tickets as possible can measure its turnaround time and set a suitable target value.
Supporting strategic business goals
The output of a business is the sum total of the output of all its individual activities. The help desk, being an important support function in an organization, contributes significantly to a business's output. By setting and tracking KPIs, help desks can ensure they're aligned with business goals.
For example, if the goal of a business is to minimize costs, it would be useful to measure and minimize the cost of handling each ticket.
What gets measured gets managed
KPIs help manage IT help desks better by quickly identifying pain points and bottlenecks. Once issues are identified, admins can address them promptly.
Focused monitoring
With a multitude of data points and qualitative factors, it's easy to lose focus of what exactly needs to be measured in an IT help desk.
This might have two undesirable consequences: wasted resources on measuring irrelevant factors and/or missing out on measuring the relevant ones. Setting and tracking KPIs ensures that all, and only, relevant factors are measured.
Achieving and maintaining optimum efficiency
It's easier for managers to understand and achieve quantifiable targets. So if each KPI is set towards optimizing the help desk ticketing processes to a certain level, it's simpler for help desk teams to achieve that level. It's also easier to maintain that level since it can be done by maintaining specific metrics.
Simply put, setting KPIs provides a systematic approach towards optimizing help desk operations.
Building roadmaps
Knowing the bottlenecks and target values for KPIs can help managers build short-term roadmaps.
For example, if the help desk has a high average turnaround time, then the immediate task at hand is to minimize it. Similarly, if they have a target of providing timely service, then their roadmap will be to minimize SLA violations.
As for implementing KPIs, the most basic requirement is knowing what to measure. While there are certain common KPIs that every help desk can track and harvest value from, it's also useful to know how to determine custom KPIs.
A simple four-step process for this is described below:
Identify relevant business goals
As discussed earlier, KPIs are effective at aligning IT help desks with overall business goals. So the starting point of determining KPIs is to understand the business goals that are supported by your help desk and then identify the factors that impact those goals.
Identify key enablers and impact areas
Once you've identified the business goals your help desk supports, the next step is to understand which enabler, medium, or area those goals impact. In general, there are three key enablers and impact areas for an IT help desk: processes, technicians, and technology.
In the example above, cutting costs is largely dependent on staff size, so that business goal is likely to affect technicians. In some cases however, cutting costs can affect technology as well, for instance if the organization decides to downgrade to cheaper infrastructure or software.
Identify critical success factors (CSFs)
A CSF is an actionable statement that clearly states what needs to be done or what is expected. A CSF defines when an activity can be considered successful. In the previous example, a CSF could be "Cost of handling tickets should be reduced by 50 percent."
Determine KPIs
By combining your findings from the above steps, you can derive KPIs and give each KPI a target value. Continuing the cost-cutting example from above, you could define a KPI as the "average cost of handling one ticket" and set the target value to half of the existing cost.
As a reference, some common KPIs for help desks are listed below:
| Key impact area | KPI |
|---|---|
| Technicians | Staff responsiveness |
| Technicians | Turnaround time |
| Technicians | Agent utilization |
| Technicians | First contact resolution (FCR) rate |
| Technicians and processes | Cost per ticket |
| Technicians and processes | Average resolution time |
| Processes | Ability to reach a technician |
| Processes | SLA violations |
| Processes | High-priority tickets backlog volume |
| Processes | Tier 1 resolutions |
| Technology | Ease of communication |
| Technology | Infrastructure stability |
| Technology and processes | Ease of raising a ticket |
| Technicians, processes and technology | User satisfaction |
| Technicians, processes and technology | Change success rate |
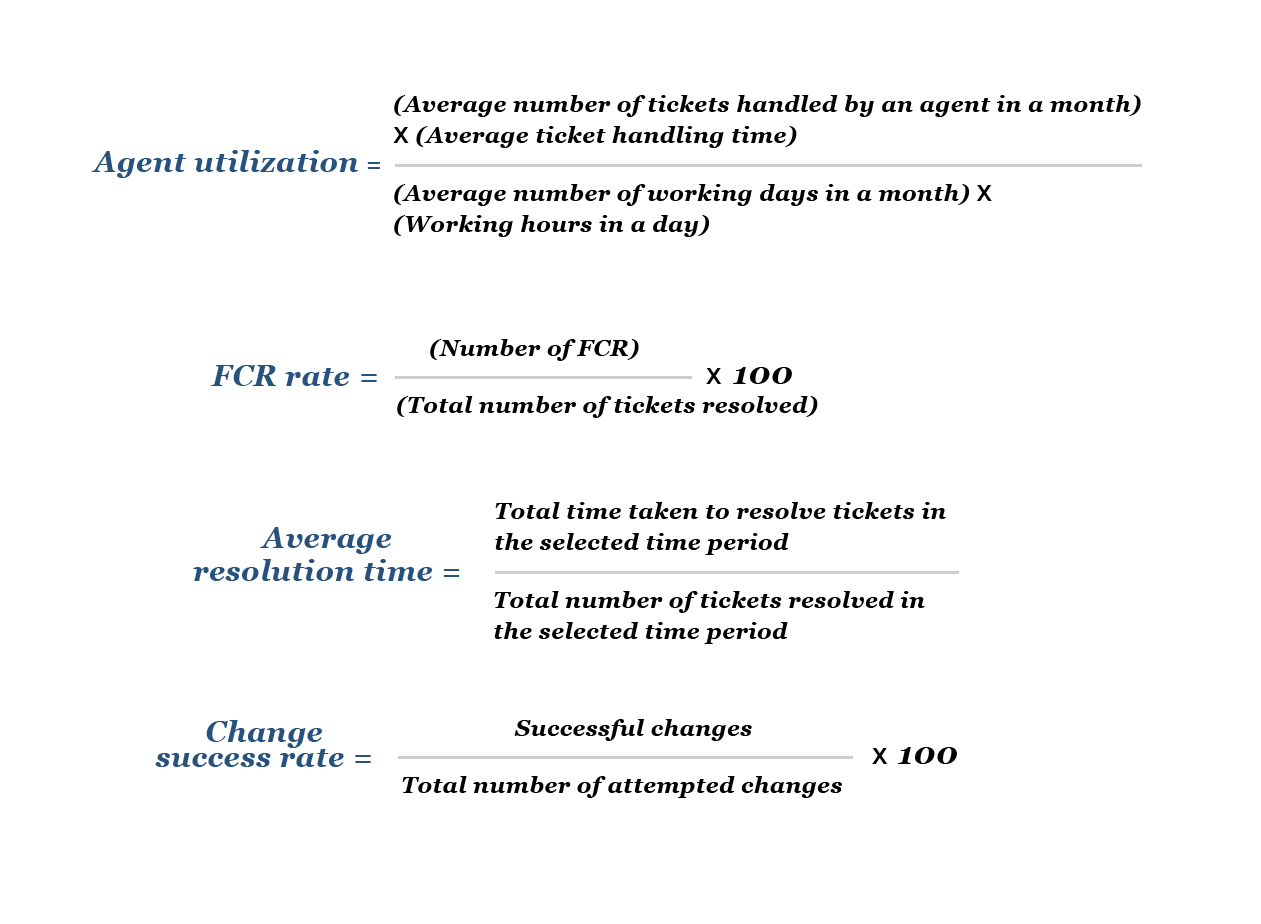
You can determine some of the above KPIs using simple calculations. Here are a few key KPI formulas for reference:
An IT help desk combines a large number of individual processes and workflows. For example, incident management is broken down into tasks, change management into stages and statuses, project management into milestones, and so on.
Manually carrying out each and every task is not only cumbersome and time-consuming, but can also introduce human error into the process. That's where automation can help.
Benefits of automation:
Faster processes
Automation helps reduce the time it takes to resolve a ticket (turnaround time), and it also helps to create asset inventories, log events for audits, and generate reports.
Reduced cost
With a shorter time per ticket and smaller IT staff requirements, automation can help reduce the overall cost incurred per ticket.
Error-free operations
With automated processes and workflows, the chances of human error, like setting the wrong priority for a ticket, are greatly reduced.
Increased tech productivity
With automated processes taking care of routine, repetitive tasks, IT staff have the freedom to focus on more critical projects. Error-free tickets also reduce the chances of technicians having to go back and forth with requesters, so they can focus on resolving tickets instead.
Higher efficiency
Reduction in errors, costs, and time leads to higher overall help desk efficiency.
Improved customer satisfaction
Faster and more accurate resolutions, coupled with fewer interactions with IT staff, result in higher customer satisfaction.
Higher end user productivity
Timely ticket resolution ensures that downtime is minimized for end users. With accurate ticket logging, end users in the critical roles always receive priority resolution. Also, by automating routine resolutions, like password reset requests, end users can spend less time waiting on requests.
Enforced best practices
With automated processes, it's easier to enforce best practices every time a process is carried out.
Industrialization of processes
A process is said to be industrialized if it can be a repeatable function that is easily executable, delivers consistent results, and provides a scope for improvement over time.
Consistent experience
Automation makes sure that processes and workflows are executed in the same way every time. This makes the experience of technicians, and the behavior and outcome of processes, consistent.
Automatic scheduling
Tasks can be scheduled and carried out automatically.
The breadth of IT operations in an organization can cover a wide range of activities and processes like ticket handling, endpoint management, Active Directory management, network management, etc. If these activities are conducted in silos, it's unlikely the separate teams overseeing them will have the means to effectively collaborate and communicate with each other, which negatively impacts the entire organization's level of efficiency.
This roadblock is overcome by integrating all such activities into one solution. In other words, integration turns an IT help desk into a control center for all IT, not just another point solution.
Benefits of integration and integrated solutions:
Centralization
The biggest advantage of integration in an IT help desk is that it turns the help desk into a central command center for all IT operations.
By integrating with other ITSM applications, all IT inventory and processes can be managed from a single application, requiring less effort and boosting efficiency.
Faster operations
Integrating with other applications reduces the time it takes to manually import data and execute tasks. Without having to switch between applications, a single team or individual technician can carry out tasks, saving the time it takes to coordinate between teams or technicians.
Reduced costs
Similar to automation, help desk integrations also lead to a reduction in IT staff requirements by centralizing all IT operations.
Increased scalability
Integrating applications with the help desk sets the foundation for scaling the entire help desk software system to include non-IT capabilities like CRM for better data sharing between them.
Information sharing
Communication between two or more applications, and sharing of data between them, is made simpler through integration.
Fewer redundancies
In an integrated system, similar data need not be stored in separate instances. Also, help desk integrations help eliminate overlap of processes and tasks.
Coherent data
Since all data is stored in a single instance and shared with all integrated applications, data remains coherent and defragmented.
Real-time system data
When all integrated applications access and modify data on the same database, the data available across all applications is always up-to-date.
Flexibility
Available integrations make help desk ticket management software more flexible, since admins can add modules as needed.
Agility
Since integration brings the control of all IT operations under a single interface, IT teams can quickly address shifts in user preference, technology, policies, etc.
With technologies changing rapidly and processes following suit, the ITSM industry is at the brink of a major evolution.
According to Markets and Markets, the ITSM market is expected to grow at a compound annual growth rate (CAGR) of 15.9 percent between 2023 and 2028, with the cloud-based ITSM market reaching a CAGR of 13.5 percent between 2024 and 2029.
However, before thinking about what the future of ITSM and help desk support software will look like, it's important to understand the challenges that IT help desks will have to overcome to be on top of this technology wave.
Some of the key challenges that IT help desks will face going forward are:
Churning out dated tools
Technologies are changing so fast that old tools are becoming outdated very quickly. The inability of existing tools to adapt to emerging technologies poses a major challenge to companies.
In addition to that, old technologies might cost more to maintain compared to adopting new ones because of operational inefficiencies. This results in the need for continuous investment and divestment due to rapid digitization.
Embracing mobility
Business users are becoming more comfortable using their personal devices in their work environment.
For a mobile workforce, this enables access to corporate data anytime, anywhere. IT, which typically has had control over end users' tools and devices, is slowly losing its grip. With this comes the risk of data misuse, which cannot be treated lightly.
At the same time, increased mobility is providing businesses with a productive and well-connected workforce. This indicates the need for comprehensive BYOD policies that encourage mobility but also ensure data security.
Managing shadow IT
Rapid consumerization of IT has enabled business users to access IT solutions and technologies that are outside their IT infrastructure. More often than not, end users bypass their internal IT guidelines to acquire applications that supplement their work.
But over time, the number of unapproved applications skyrockets to such an extent that they appear to be a "shadow" of IT. Shadow IT lays the groundwork for non-compliance, and in some cases, a security breach.
While unauthorized IT infrastructure comes with security risks, with the right guidelines, shadow IT can enable a more productive workforce. Organizations need to accept and embrace this trend to create more value from IT investments.
Committing to compliance
Businesses operate in a dynamic environment with a lot of interrelated IT components. Such a complex setup is governed by an equally complex set of standards and regulations put in place by industries and/or governments.
Therefore, organizations will sometimes inadvertently violate one of the many regulations placed upon them.
Such nonadherence to maintaining compliance can result in not only a loss of customer trust, but also penalities and fines.
It's important for companies to have processes set and roles assigned to constantly govern, plan, and monitor their compliance with the various aspects of IT infrastructure, from software licenses to BYOD, and all the way to cloud security.
Securing growing data and applications
As businesses adopt more democratized technologies, they are often challenged by data proliferation across a fragmented web of applications.
This is challenging because not all of the applications they use are compliant with the security standards established by internal IT.
While many applications come with documentation that aims to achieve transparency and ease of use, lax security policies provide a level playing field for both users and regulators, which, in turn, increases the chances of a data breach.
For many organizations, such data breaches are a costly affair both in terms of monetary and brand value. This creates a need for an agile cybersecurity standard that makes adopting compliant technologies easier, not only for individual organizations, but also for the ITSM industry as a whole.
Staying relevant
The concept of service is going through a major shift as customers are not only looking for quicker solutions, but a better support experience as well.
Staying updated with changing technologies poses another challenge.
Consumerization of IT has resulted in quick adoption of mobile devices and technologies in the work environment. In order to stay relevant, ITSM has to keep up with such changes so that it can continue to add value to businesses.
As has always been the case with help desks, it will be shaped by upcoming technologies and the needs of technicians and end users.
Based on the challenges discussed earlier, including business, user needs, and technological changes, there are a few different ways IT help desk can evolve:
Personalized self-service across multiple platforms
With the advent of consumer-centric practices in the business-to-consumer (B2C) arena, the end users of tomorrow will expect equal quality of service from their IT teams.
As a response, IT teams can leverage technologies like gamification and artificial intelligence to create a personalized self-service experience that is consistent across all channels.
Cognitive automation of help desks
Going a step further from simple process automation, the help desks of the future can use advancements in machine learning technology to implement cognitive automation in their help desks. Cognitive automation will speed up the time it takes to identify and solve issues.
Proactive identification and resolution
Another upcoming technology is the Internet of Things (IoT). It can link any and all IoT-enabled "things," creating a virtually limitless network.
With the help of IoT sensors, IT teams can monitor device performance, and automatically report impending issues. These issues can then be solved proactively, mitigating the risk of downtime.
Intuitive insights into help desk performance
Reporting and analytics are a crucial part of ITSM as it exists today. Looking forward, help desk software will try to leverage big data technology to capture more data points and analyze them for better efficiency.
The ability to study a higher volume of data generated in IT operations will empower IT teams to make more informed decisions and achieve optimum performance levels.
Help desk software glossary of terms
Asset
Any resource or capability. A service provider's assets include anything that can contribute to the delivery of a service. Assets can be one of the following types: management, organization, processes, knowledge, people, information, applications, infrastructure, or financial capital.
Asset management
A generic activity or process responsible for tracking and reporting the value and ownership of assets throughout their life cycle.
Change
The addition, modification, or removal of anything that could affect IT services. The scope includes changes to all architectures, processes, tools, metrics, and documentation, as well as changes to IT services and other configuration items.
Change management
Transitioning something newly developed (i.e., an update to an existing production environment or something entirely new) from the service design phase into service operation (also known as business as usual), all while aiming to ensure that standardized methods and procedures are used for efficient handling of all changes.
Cloud
Refers to accessing computer, IT, and software applications through a network connection, often by accessing data centers using wide area networking (WAN) or internet connectivity.
Customer relationship management (CRM)
The practices, strategies, and technologies that companies use to manage and analyze customer interactions and data throughout the customer life cycle, with the goal of improving business relationships with customers, assisting in customer retention, and driving sales growth.
Incident management
The process responsible for managing the life cycle of all incidents. Incident management ensures that normal service operation is restored as quickly as possible and that business impact is minimized.
IT help desk software evaluation kit
An exclusive package of a feature checklist and a request for proposal (RFP) template
IT service management (ITSM)
The implementation and management of quality IT services that meet the needs of a business. IT service management is performed by IT service providers through an appropriate mix of people, processes, and information technology.
Knowledge base
A logical database containing information used by the service knowledge management system.
KPI
A metric that is used to help manage an IT service, process, plan, project, or other activity. KPIs are used to measure the achievement of critical success factors. Many metrics may be measured, but only the most important of these are defined as KPIs and used to actively manage and report on processes, IT services, or activities. Help desks should select KPIs to ensure that efficiency, effectiveness, and cost-effectiveness are all managed.
On-premises
Software that is installed and runs on computers within the premises (in the building) of the person or organization using the software, rather than at a remote facility such as a server farm or cloud.
Portal
Generally synonymous with a gateway, a portal is a website that is or proposes to be a major starting site for users when they get connected to the web, or that users tend to visit as an anchor site.
Problem
It is the cause of one or more incidents. Problem records are created for repetitive incidents to investigate the root-cause. The problem management process aims to troubleshoot, document, and find permanent resolution for incidents.
Problem management
The process responsible for managing the life cycle of all problems. Problem management proactively prevents incidents from happening and minimizes the impact of incidents that cannot be prevented.
ROI
A measurement of the expected benefit of an investment. In the simplest sense, it is the net profit of an investment divided by the net worth of the invested assets.
SaaS
A software licensing and delivery model in which software is licensed on a subscription basis and is centrally hosted. It is sometimes referred to as "on-demand software."
Self-service portal
A self-service portal is a website or app that enables users—whether they are customers, employees, suppliers, or partners—to perform high-value transactions, from simple account updates to paying bills, managing support tickets, and more.
Service catalog
A database or structured document with information about all live IT services, including those available for deployment. A service catalog is part of a service portfolio, and it contains information about two types of IT services: customer-facing services that are visible to the business, and supporting services the service provider requires to deliver customer-facing services.
SLA
An official commitment that prevails between a service provider and a client. When defining SLAs, the service provider and service user agree on particular aspects of the service, including quality, availability, and responsibilities.






















