Just-in-Time Access (JIT)
Enterprises today manage numerous devices, users, and applications, often relying on multiple access policies. However, unforeseen situations not covered by these policies can arise, potentially disrupting productivity. Just-in-Time Access (JIT) provides a contingency solution, addressing these gaps efficiently.
Moreover, temporary user requirements can lead to over-permissioning if handled with permanent policies, causing privilege creep across networks. JIT Access eliminates this by enabling access for only the required duration.
How does Just-in-Time Access work?
Application Control Plus empowers administrators to manage access dynamically:
- Define access policies for specific devices and specific applications.
- Use Endpoint Privilege Management to control privilege levels.
- Grant temporary, on-demand access for unmanaged or blocked applications, ensuring security while meeting user needs.
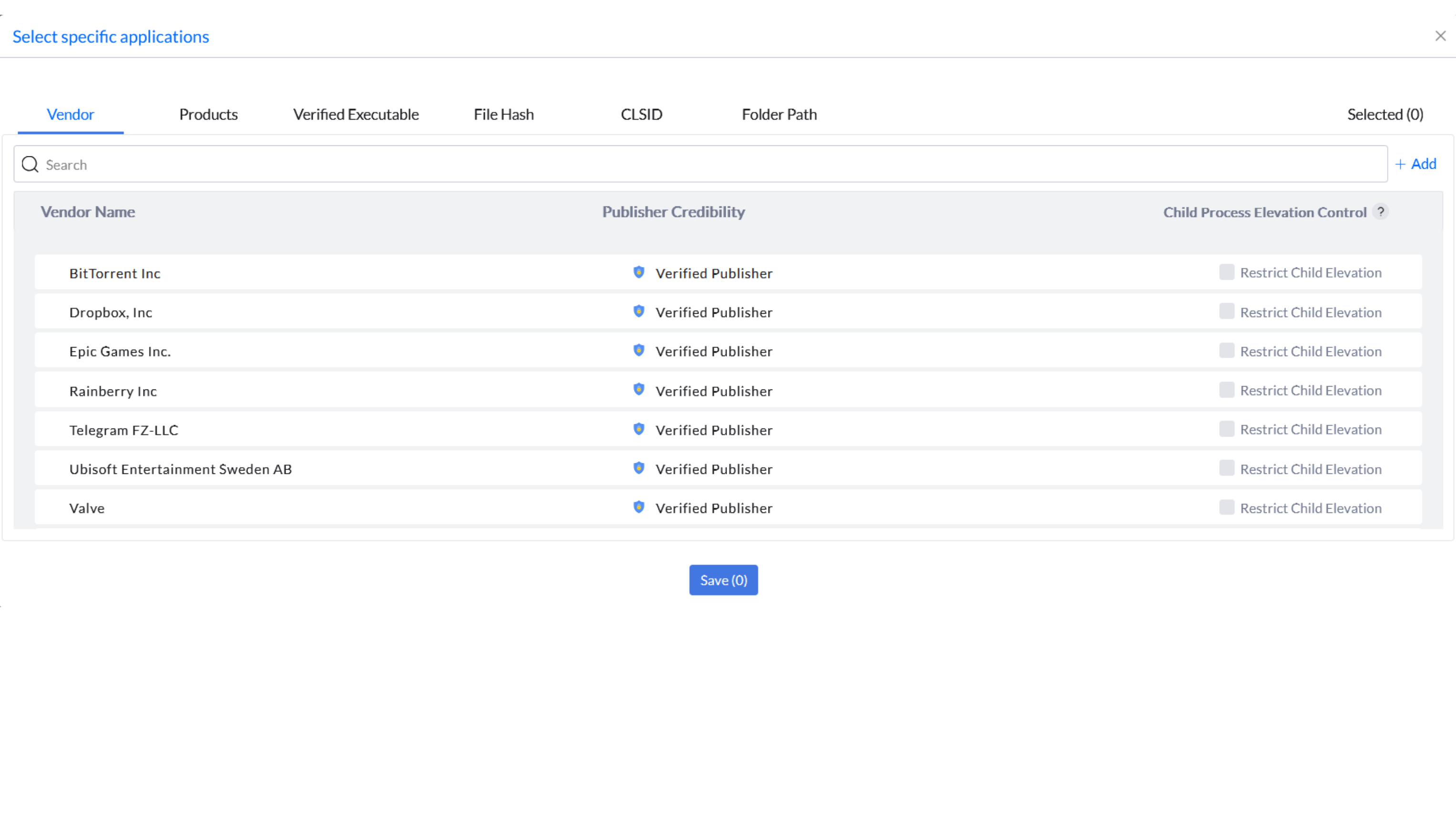
JIT Access eliminates continuous administrative rights, providing granular control and tailoring access policies based on user needs. Policies can target all or specific applications using criteria such as vendor, product name, verified executable, file hash, store apps, CLSID, or folder path.
Note: With JIT Access, environments like Strict Mode can allow temporary access to blocked applications without compromising security.
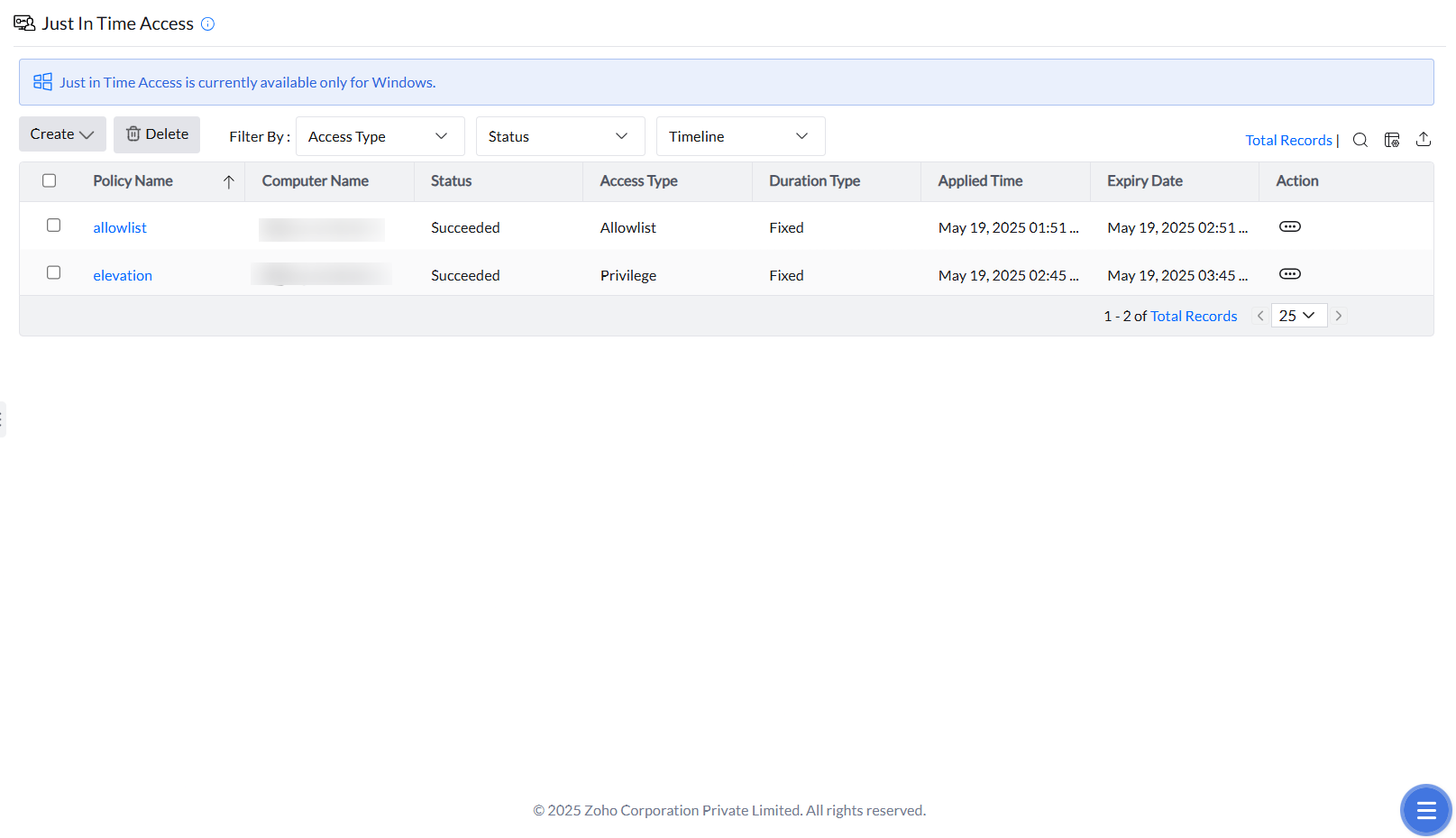
Key features of Just-in-Time Access
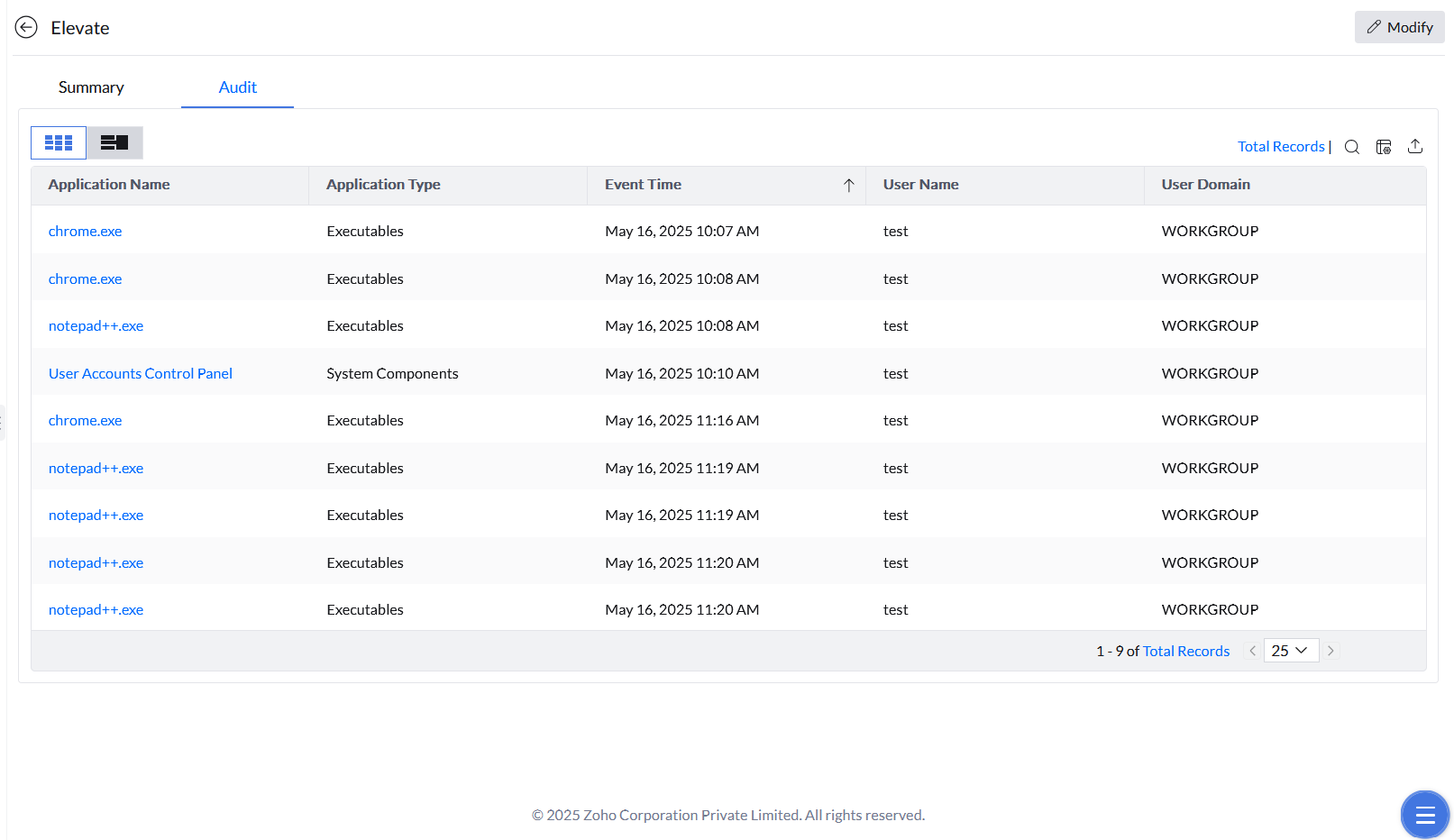
Access to applications
In Strict Mode, only allowlisted applications are accessible. JIT Access temporarily lifts restrictions, granting access to unmanaged or blocked applications for a specified time. Once the time expires, permissions are revoked.
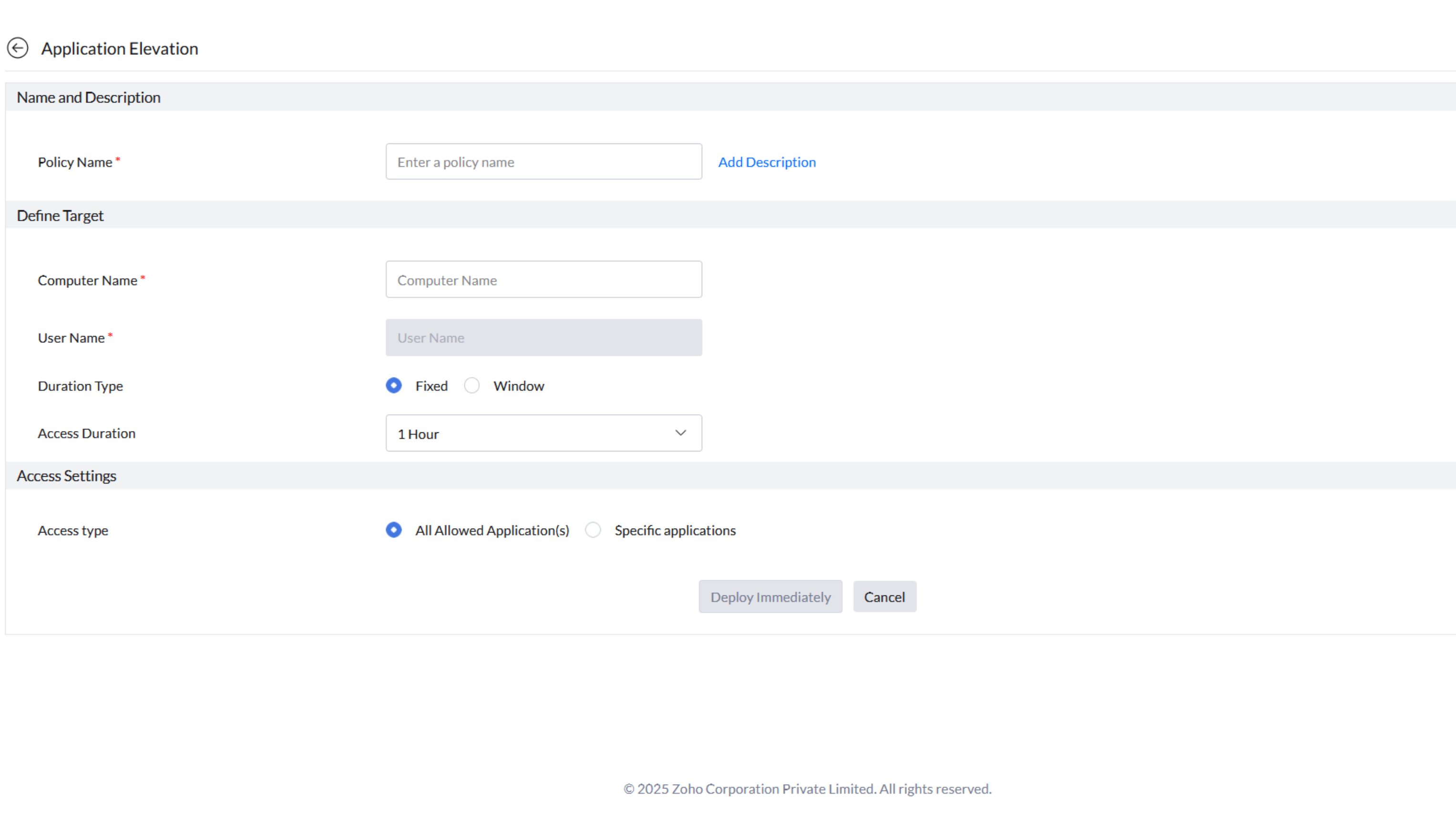
Self-Elevation of privileges
JIT Access enables users to self-elevate privileges for specific tasks, such as running unmanaged applications. This ensures that elevated permissions are time-bound, reducing security risks.
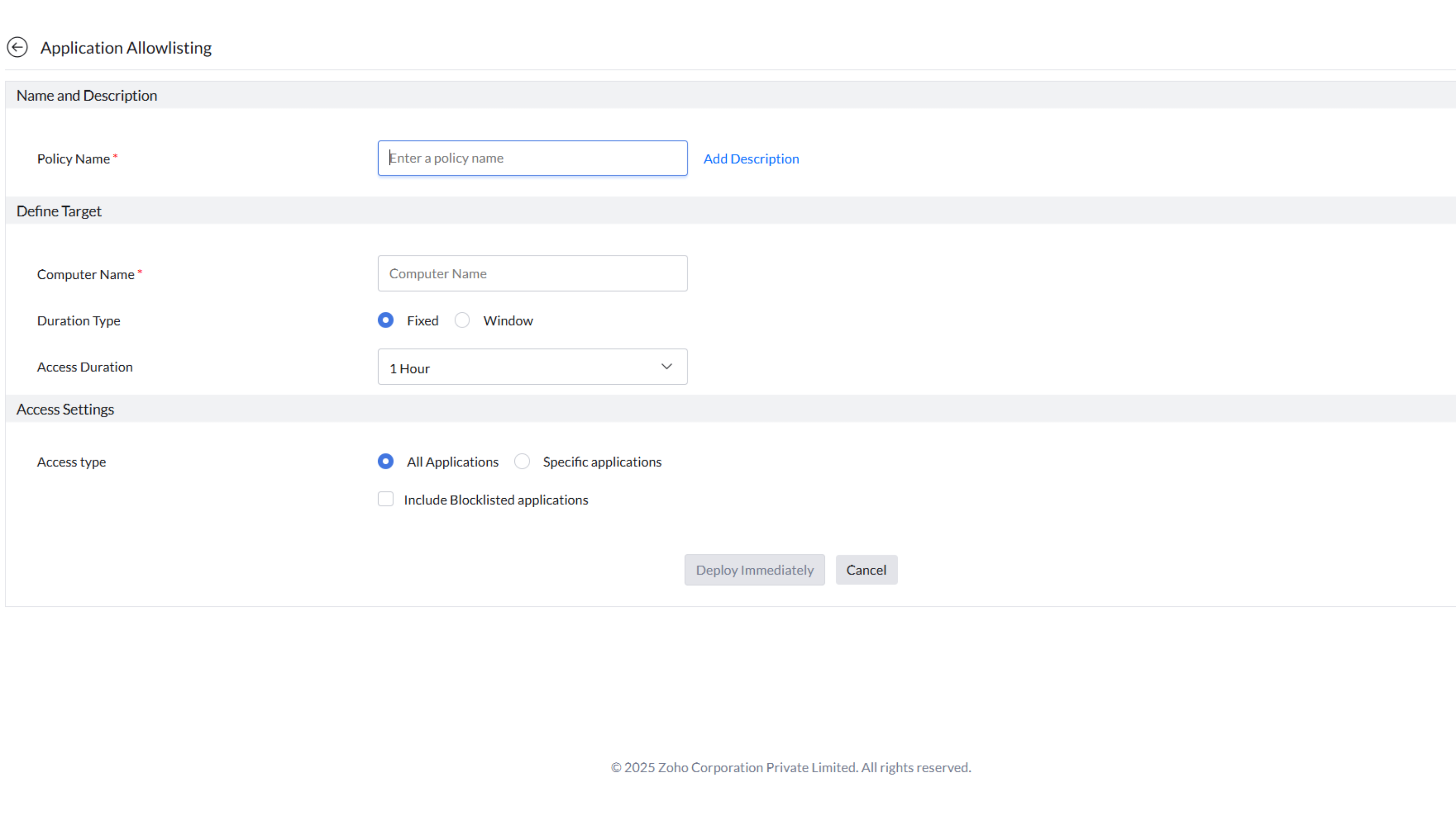
Specific applications for allowlisting and elevation
Administrators can configure JIT Access for specific applications using criteria like:
- Vendor: Approve entire suites of applications from trusted vendors.
- Product: Enable specific software tools for elevated access.
- Verified executables: Restrict elevated access to trusted files, enhancing precision.
- File hash: Approve execution for binaries with verified hashes to ensure file integrity and prevent tampering.
- Store apps: Allow execution solely of applications sourced from verified app stores to maintain a controlled ecosystem.
- CLSID: Allow access to COM objects, enabling granular control over component-level behavior and preventing misuse of system interfaces.
- Folder path: Limit execution privileges to applications residing in approved directories.
Why organizations need Just-in-Time Access control
JIT Access addresses common challenges in enterprise environments, including over-permissioning and productivity loss. It ensures temporary access with automatic revocation, reducing risks while meeting business needs.
- Cost of Breaches: According to IBM's 2023 Cost of a Data Breach report,28% of breaches involve compromised credentials, with an average cost of $4.35 million per incident. JIT Access reduces this risk by limiting exposure.
- Operational Efficiency: Organizations using JIT Access report a36% reduction in time spent managing access controls, as per a study by Forrester Consulting in 2022.
Benefits of Just-in-Time Access
- Enhanced security posture: JIT Access minimizes attack surfaces by revoking unnecessary permissions, protecting critical systems from unauthorized access.
- Regulatory compliance: Compliance frameworks like GDPR, HIPAA, and ISO 27001 require organizations to implement least privilege principles. JIT Access helps ensure compliance.
- Operational efficiency: Automated workflows for granting and revoking access reduce administrative overhead and streamline operations.
- Zero trust integration: JIT Access aligns with Zero Trust models, ensuring continuous verification and least privilege enforcement.
Stat: According to Verizon's 2023 Data Breach Investigations Report, over 74% of security breaches are linked to privilege misuse or over-permissions.
Frequently Asked Questions (FAQ)
Just-in-Time Access is a security strategy that grants temporary and time-limited permissions for users to access resources. These permissions are revoked automatically after the task is complete, reducing the risk of privilege misuse.
Traditional models often grant standing or permanent privileges, increasing the risk of exploitation. JIT Access provides time-bound, need-based permissions, aligning with modern security principles like Zero Trust.
Industries handling sensitive data, such as healthcare, finance, and government, benefit significantly from JIT Access due to strict compliance requirements and the need to protect critical systems.