*These capabilities can be achieved with DataSecurity Plus' File Analysis module.
More on file analysisDiscover, classify, and assess the risks to sensitive data stored within your repositories using our comprehensive data risk assessment tool.
Easily discover PII/ePHI such as citizenship IDs, credit card numbers, driver licenses, and more with over fifty preconfigured rules.
Ensure that your organization is compliant with IT regulations by adding new data discovery rules as needed.
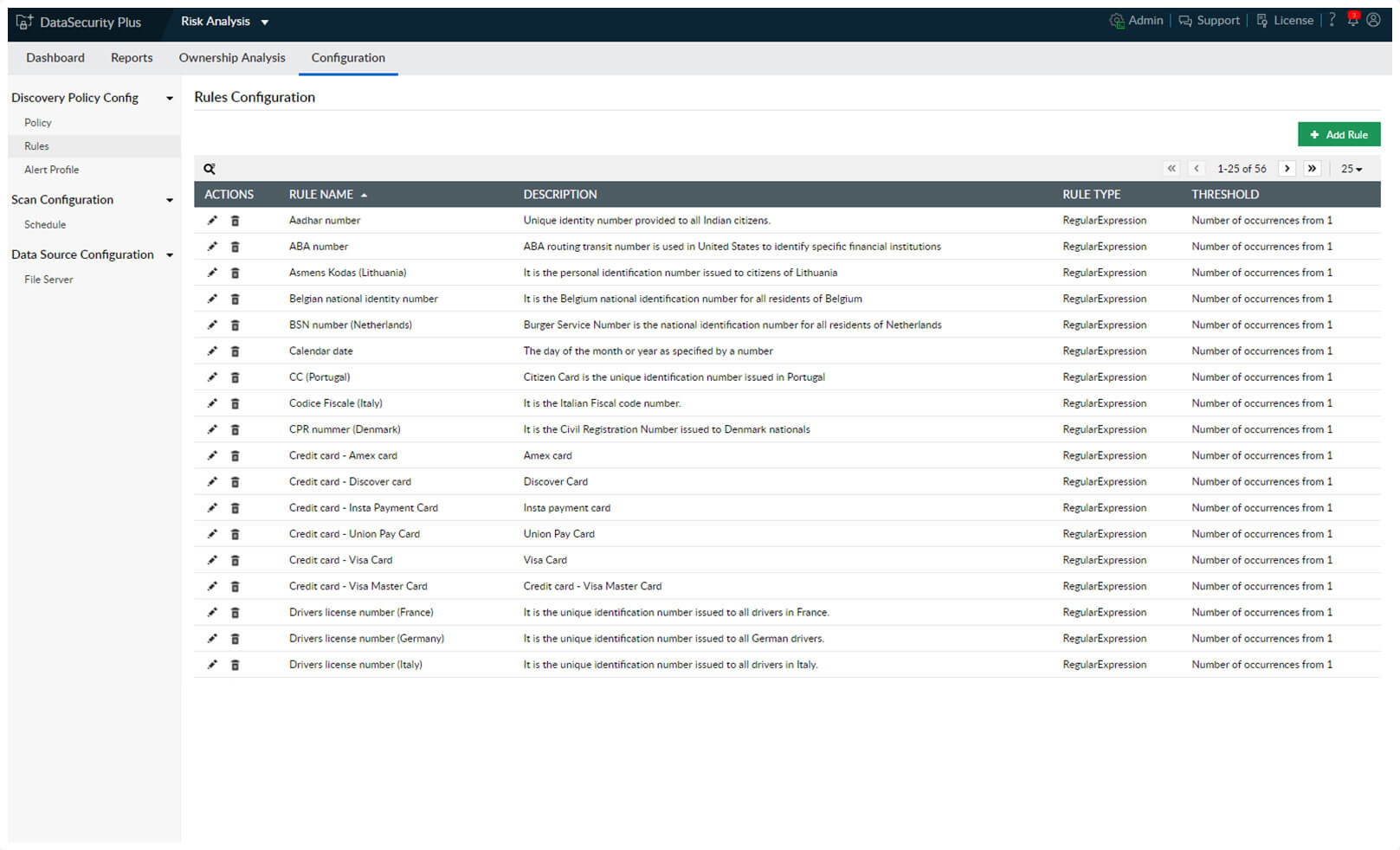
1.No blind spots: Easily discover PII/ePHI such as citizenship IDs, credit card numbers, driver licenses, and more with over fifty preconfigured rules.
2.Customize data discovery rules: Ensure that your organization is compliant with IT regulations by adding new data discovery rules as needed.
Identify if discovered data violates any regulations, and view information about the users and servers with the most violations.
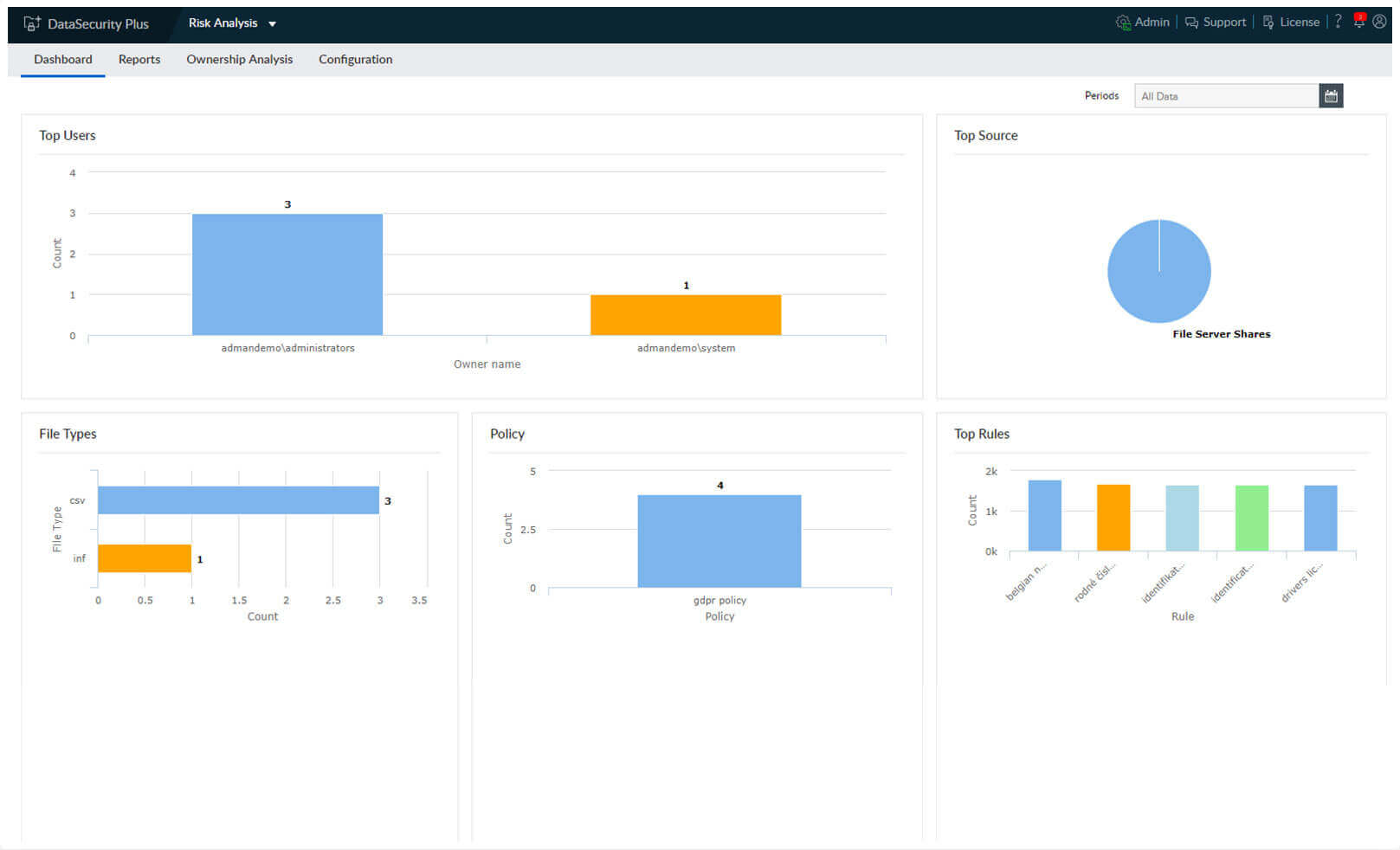
1.Analyze and classify data: Identify if discovered data violates any regulations, and view information about the users and servers with the most violations.
Maintain a detailed record of all discovered sensitive data, and prove compliance with IT regulations such as PCI DSS, GDPR, and more.
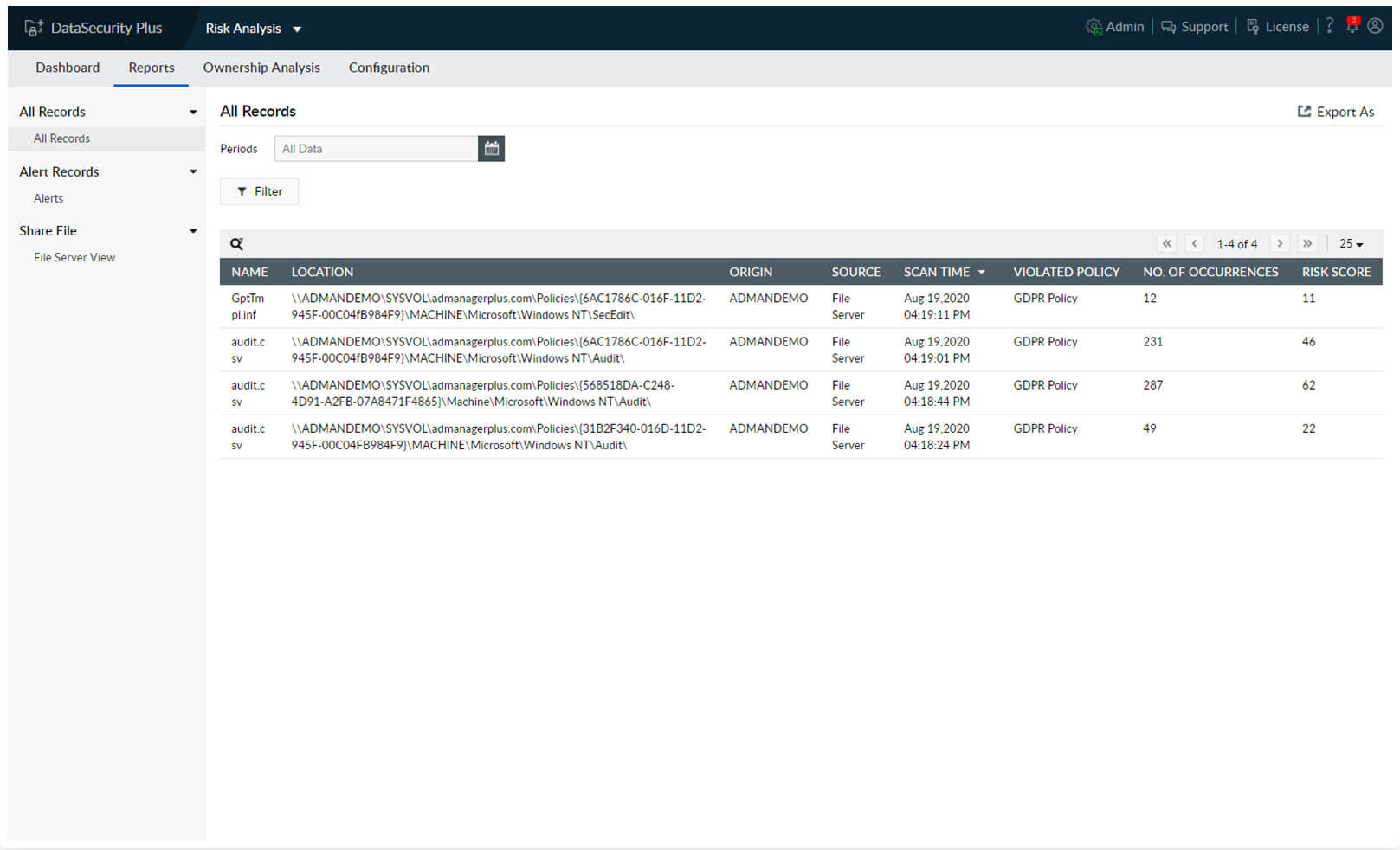
1.Detailed reports: Maintain a detailed record of all discovered sensitive data, and prove compliance with IT regulations such as PCI DSS, GDPR, and more.
Use the File Analysis component to gain contextual information on sensitive files such as their size, age, and who can access them.
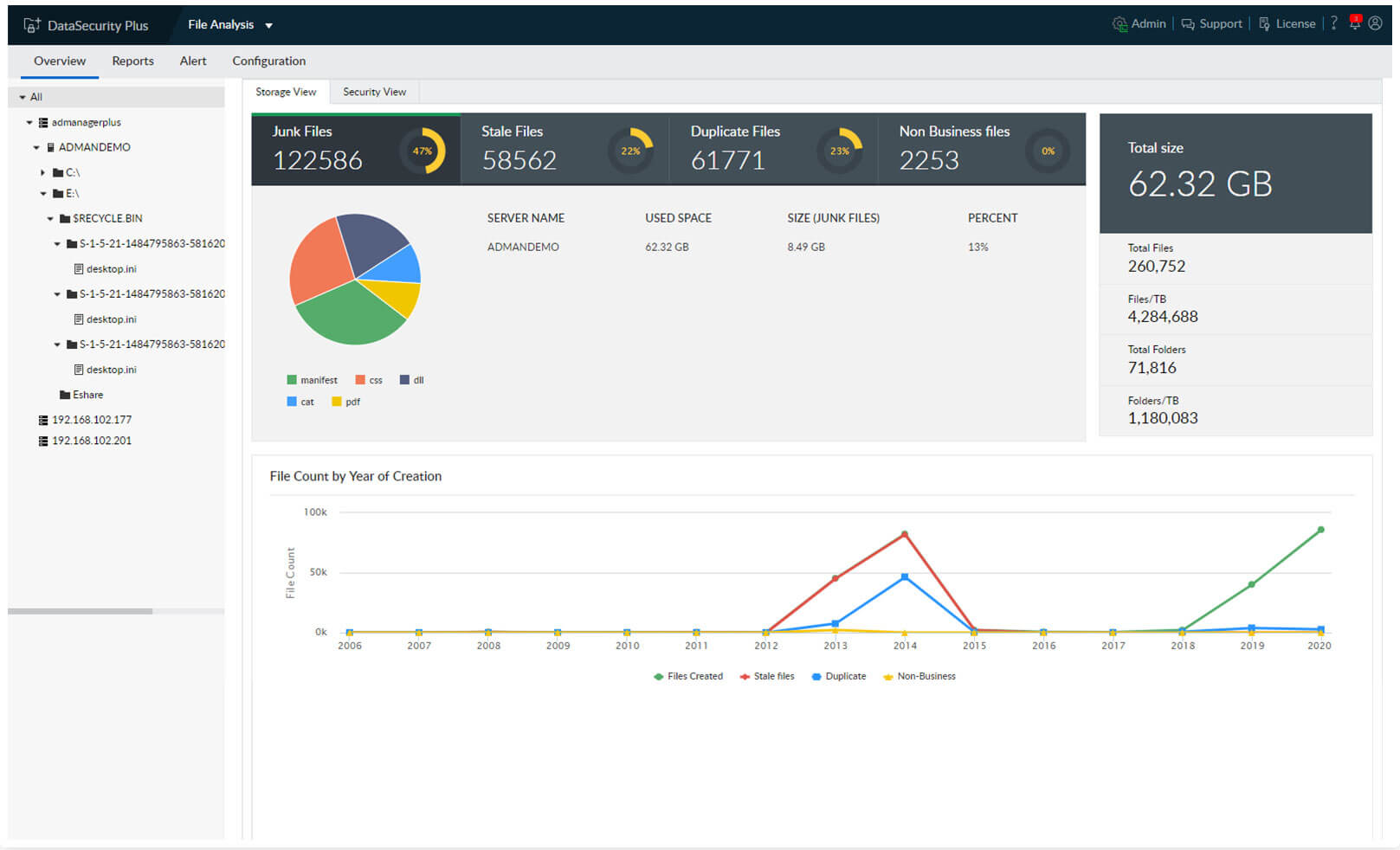
1.Effective risk analysis: Use the File Analysis component to gain contextual information on sensitive files such as their size, age, and who can access them.
Thanks! One of our solution experts will get in touch with you shortly.
Monitor, analyze, and report on all file server accesses and modifications.
Learn MoreDetect, disrupt, and prevent sensitive data leaks via endpoints, i.e., USBs and email.
Learn MoreReport on enterprise web traffic, and control the use of web applications.
Learn MoreDiscover sensitive personal data, and classify files based on their level of vulnerability.
Learn MoreLearn why data discovery is crucial to becoming GDPR-compliant using our free e-book.