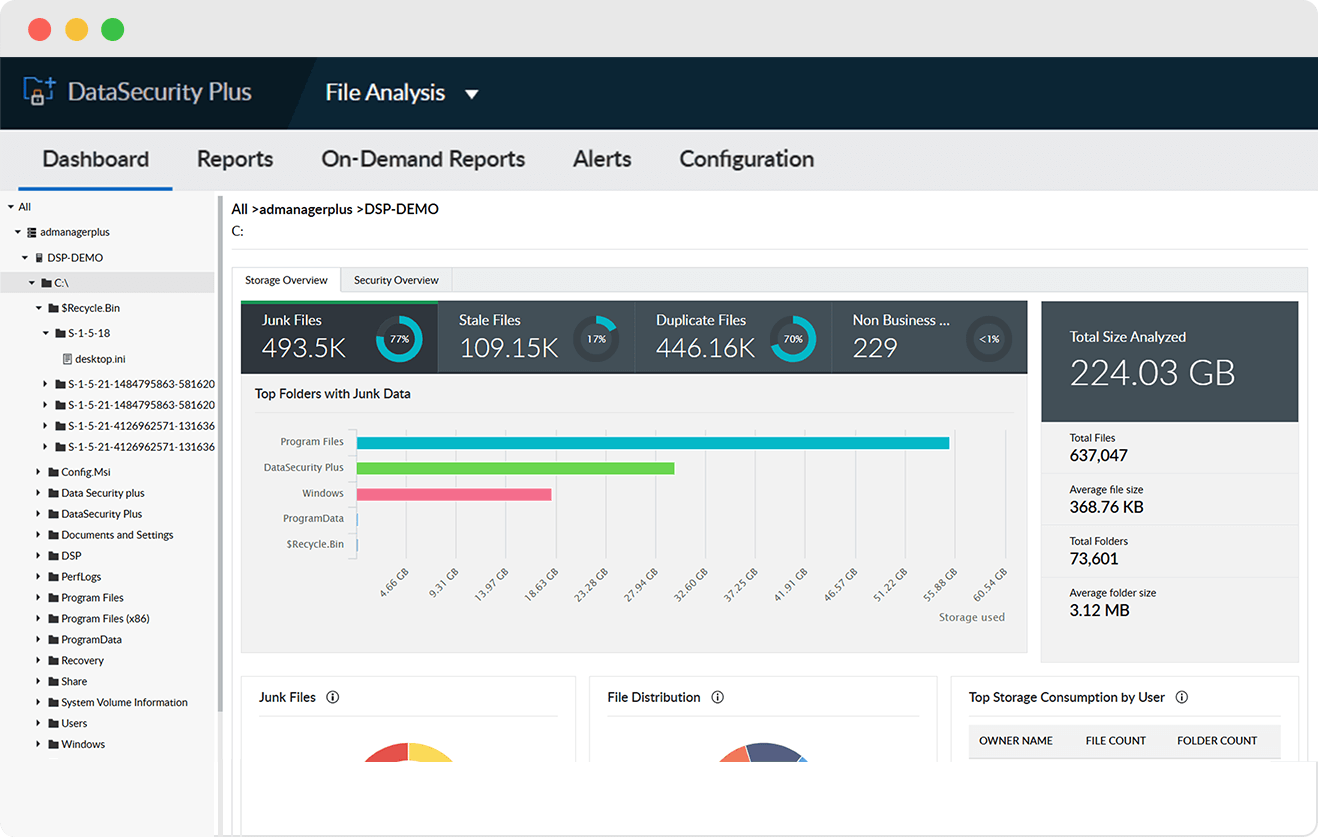
Reclaim storage capacity by locating and purging redundant, obsolete, and trivial (ROT) data from your IT ecosystem.
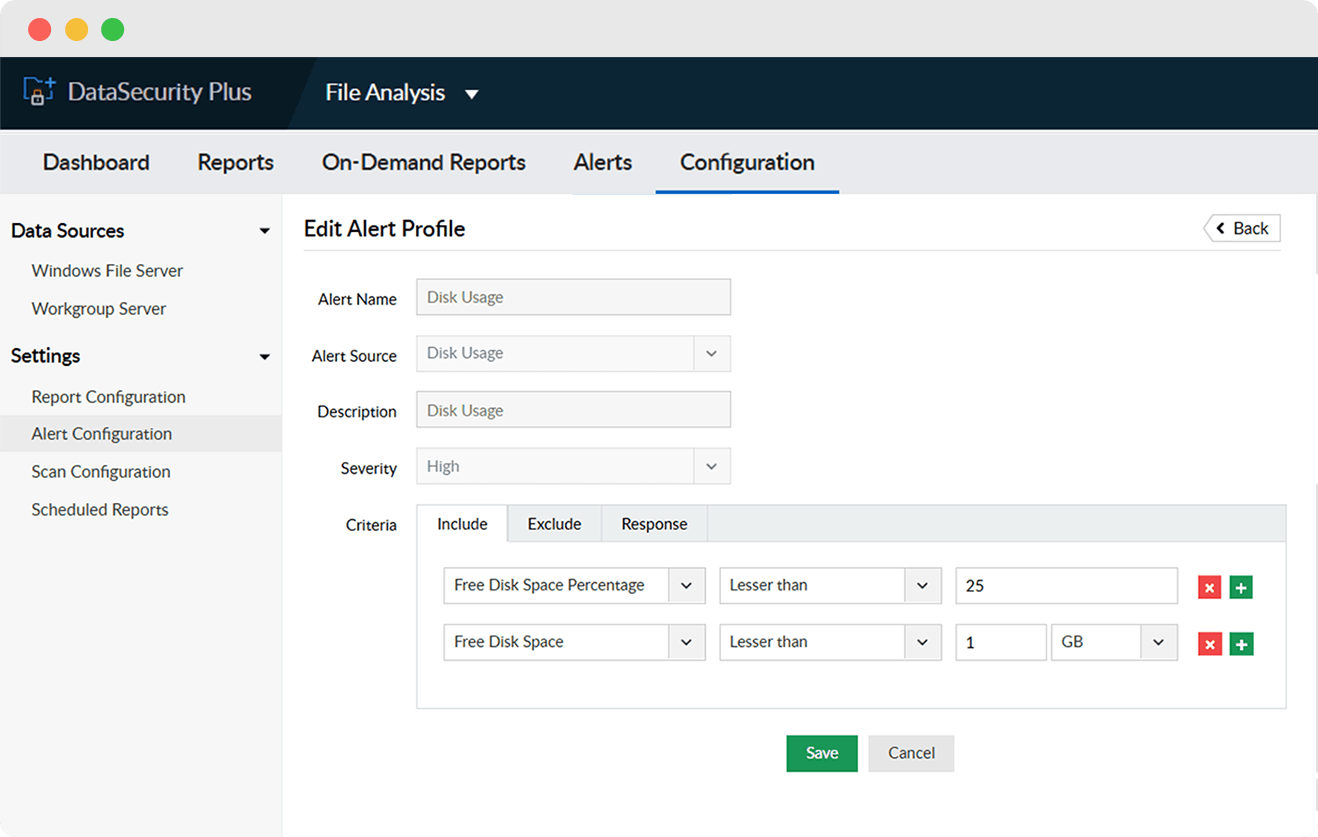
Track your disk usage pattern and consumption rate to generate instant alerts when free space falls below a preconfigured limit.
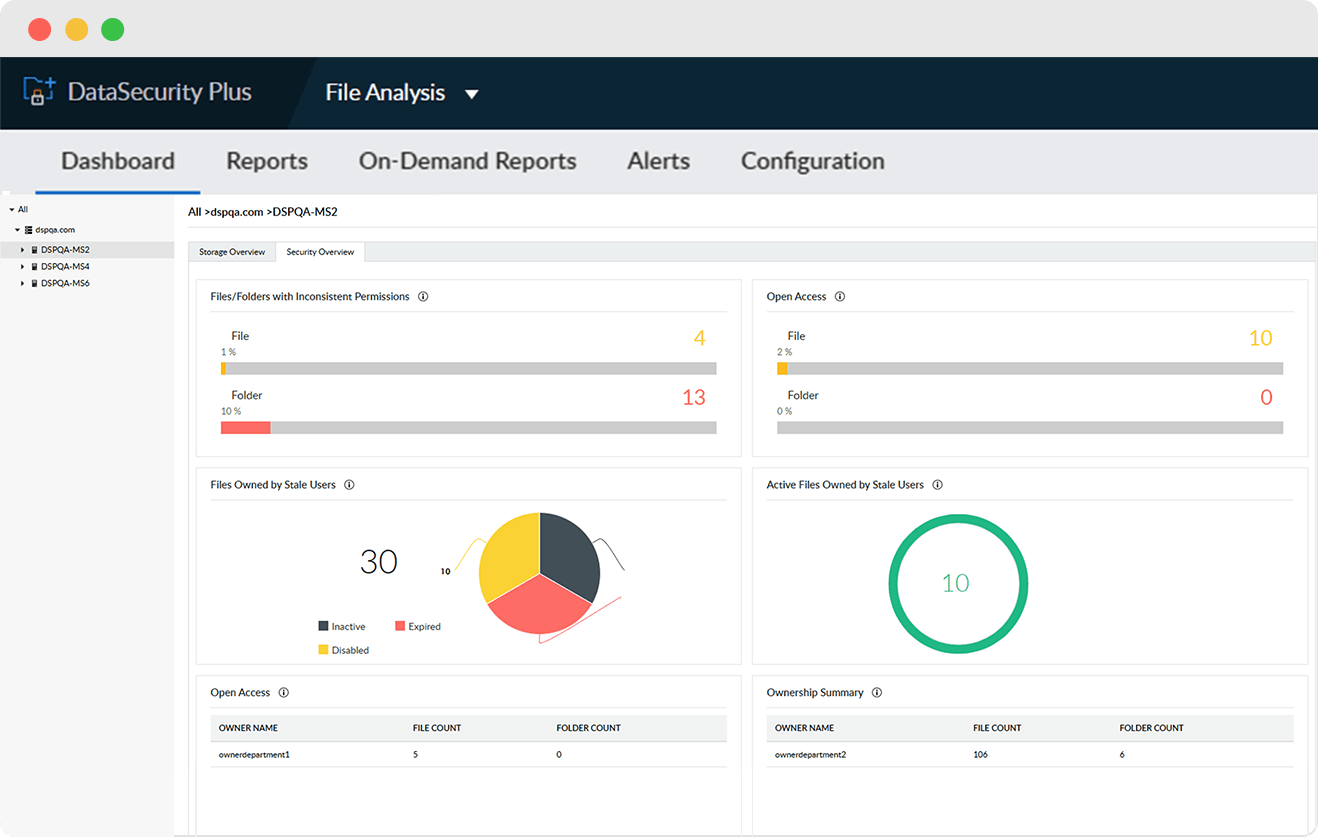
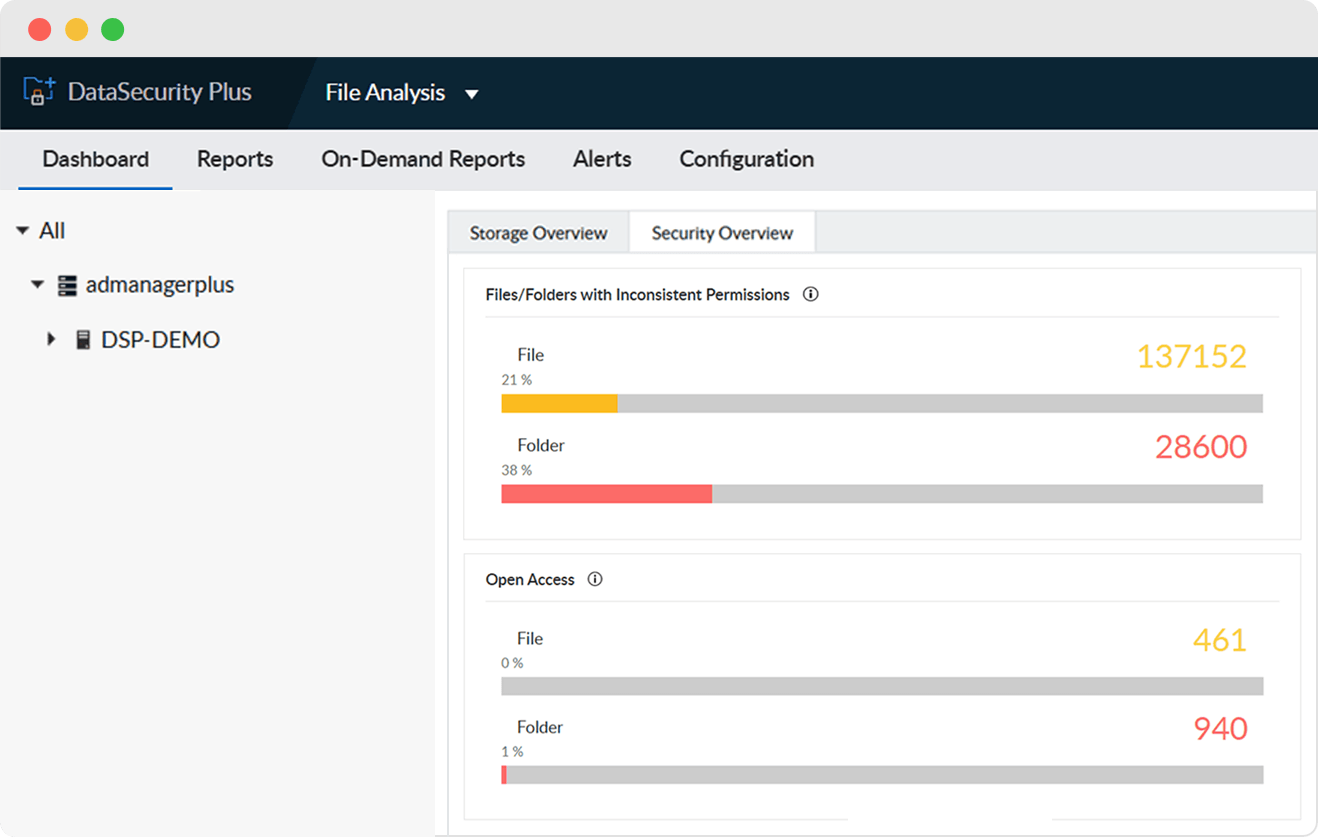
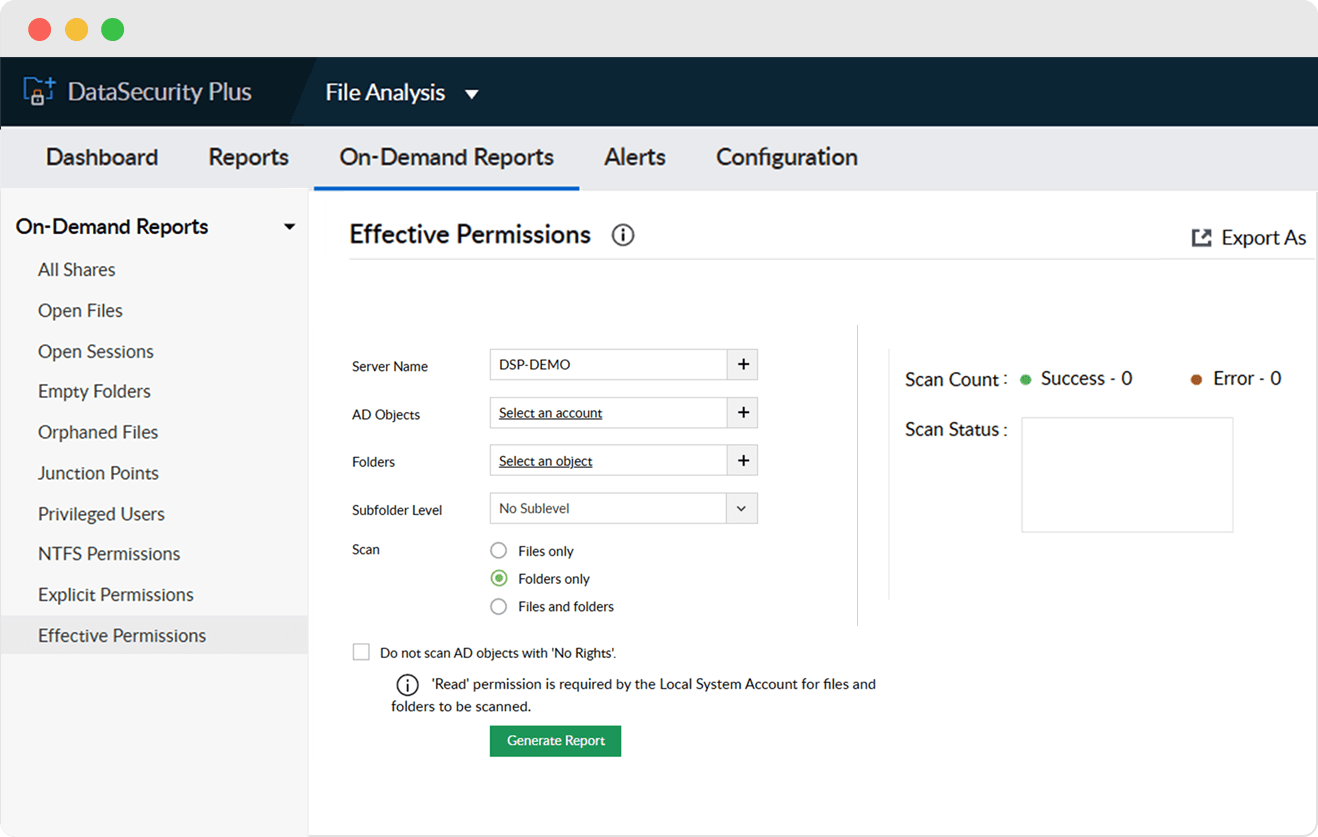
Analyze and report on users' effective access permissions across all files and folders to prevent privilege abuse.
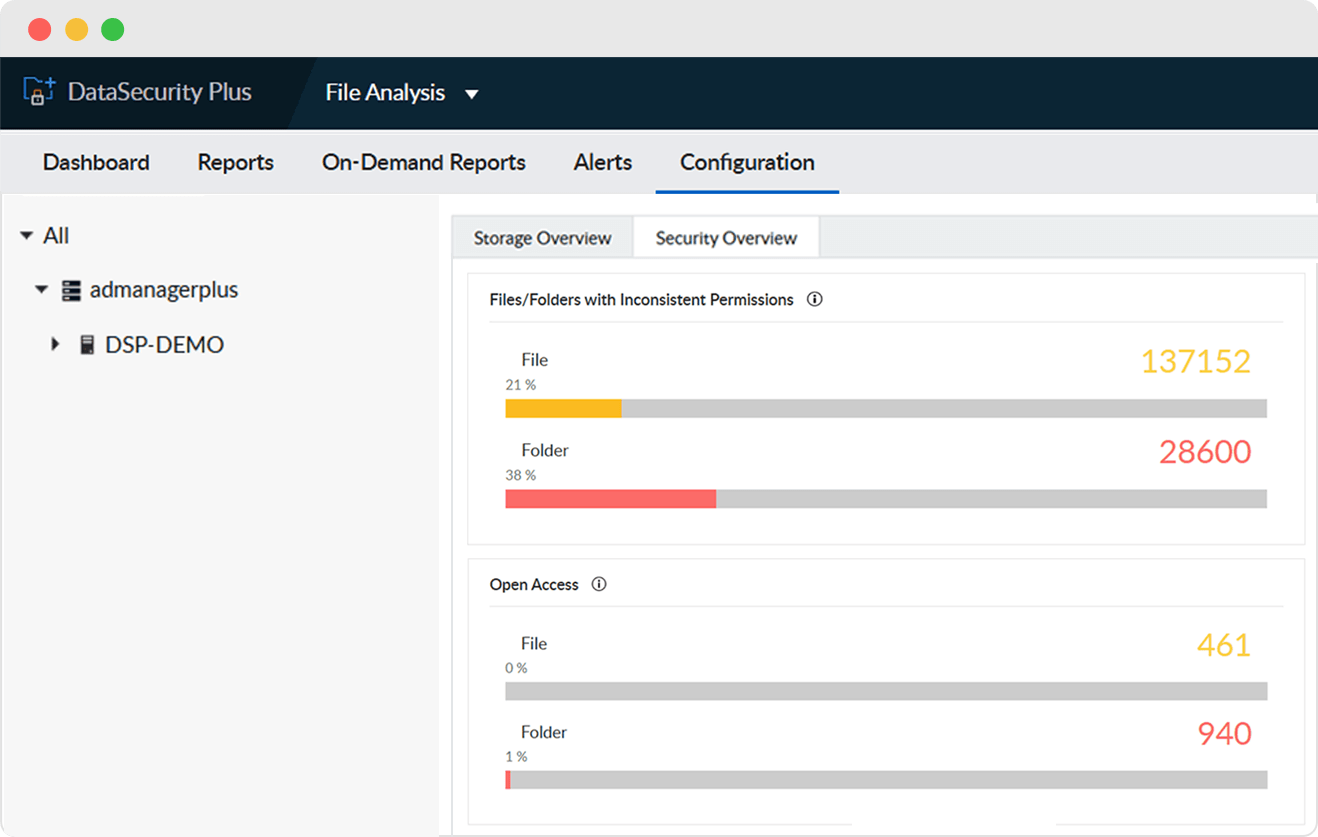
Identify and manage data most vulnerable to security threats, and improve your organization's security posture.
Locate and delete stale, old, duplicate, and other unneeded files to manage disk space better, and lower data storage costs.
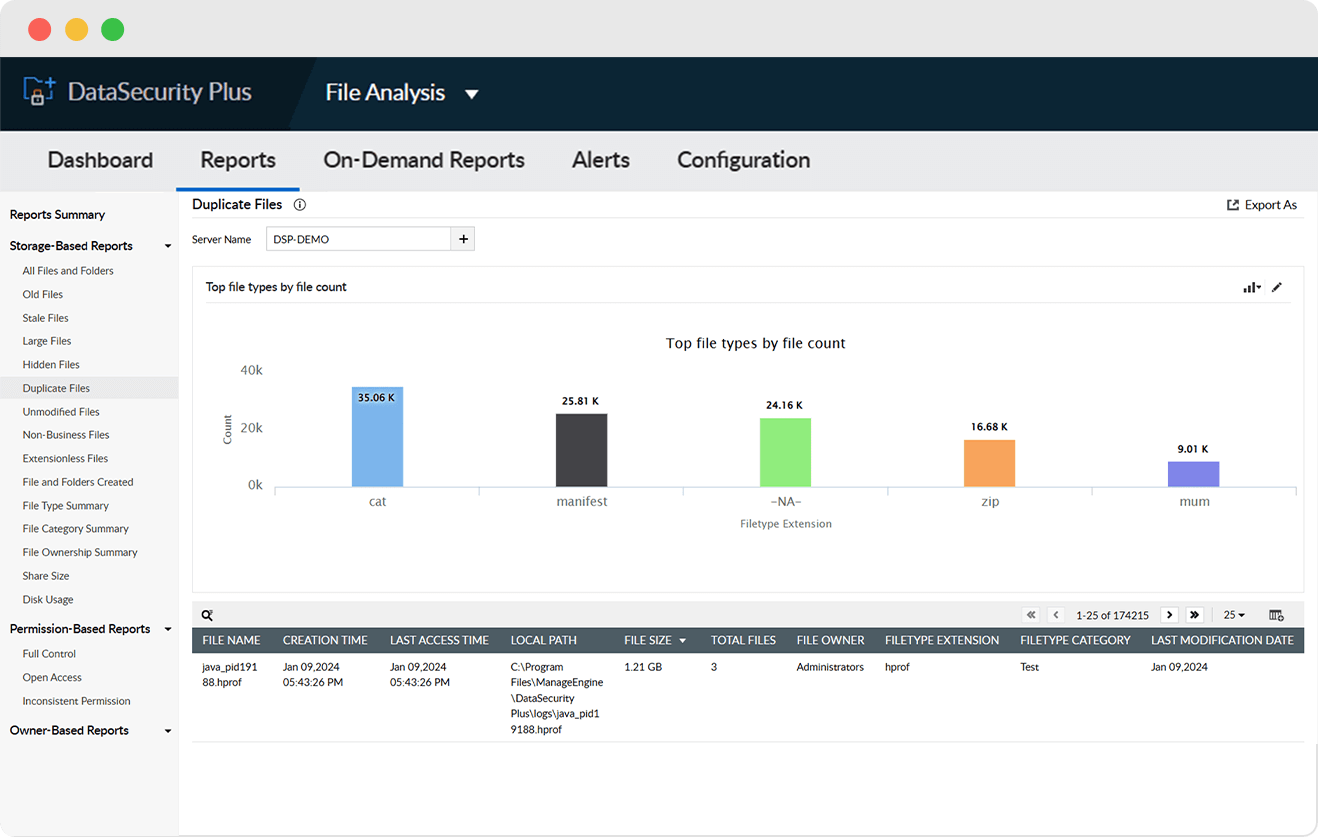
Manage bloated file storage by identifying and deleting multiple copies of the same file across your data stores.
Analyze disk space usage and data growth patterns, and generate instant notifications when free space falls below preconfigured limits.
Get critical insights on file ownership details including identifying the most active user, most common file types, and much more.
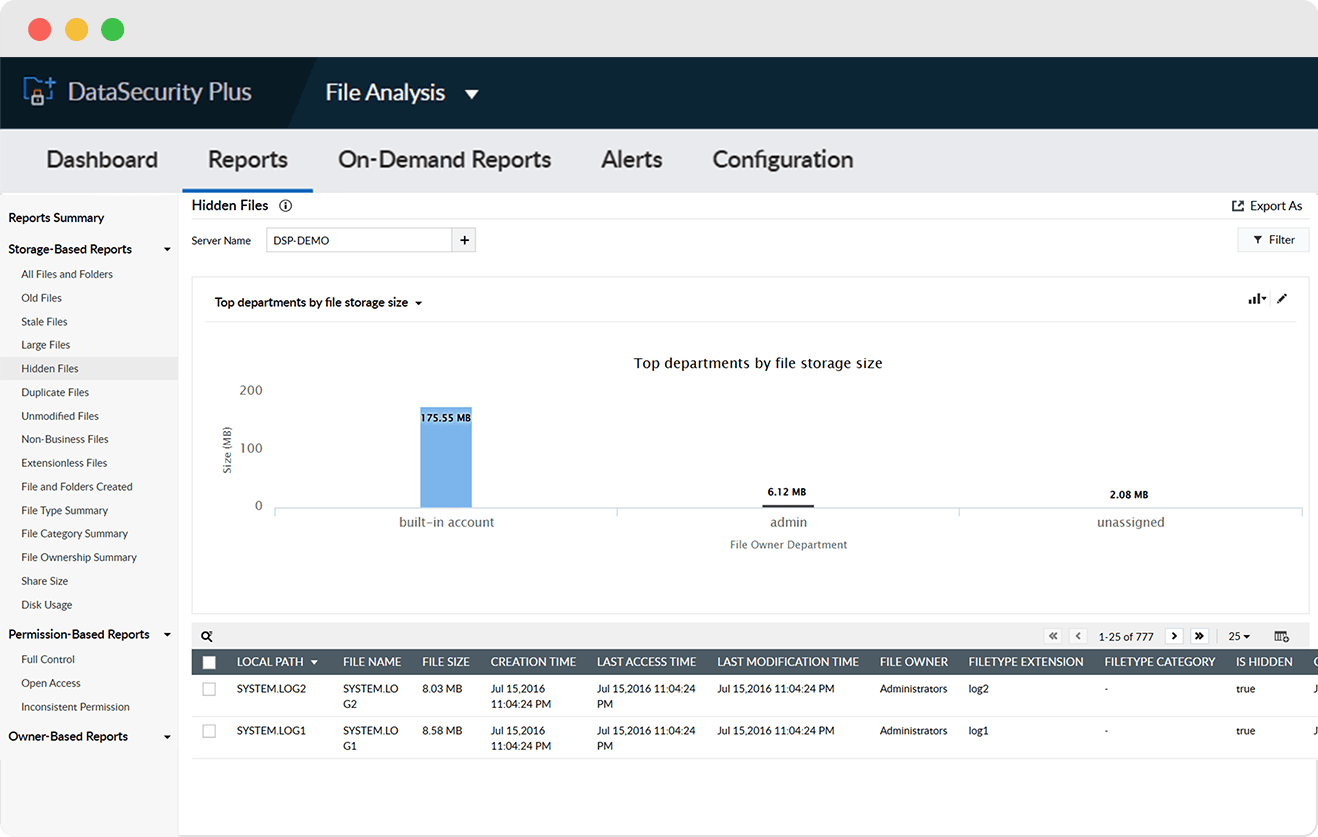
Find instances of all hidden files in your organization including system files, OS files, and business-critical data.
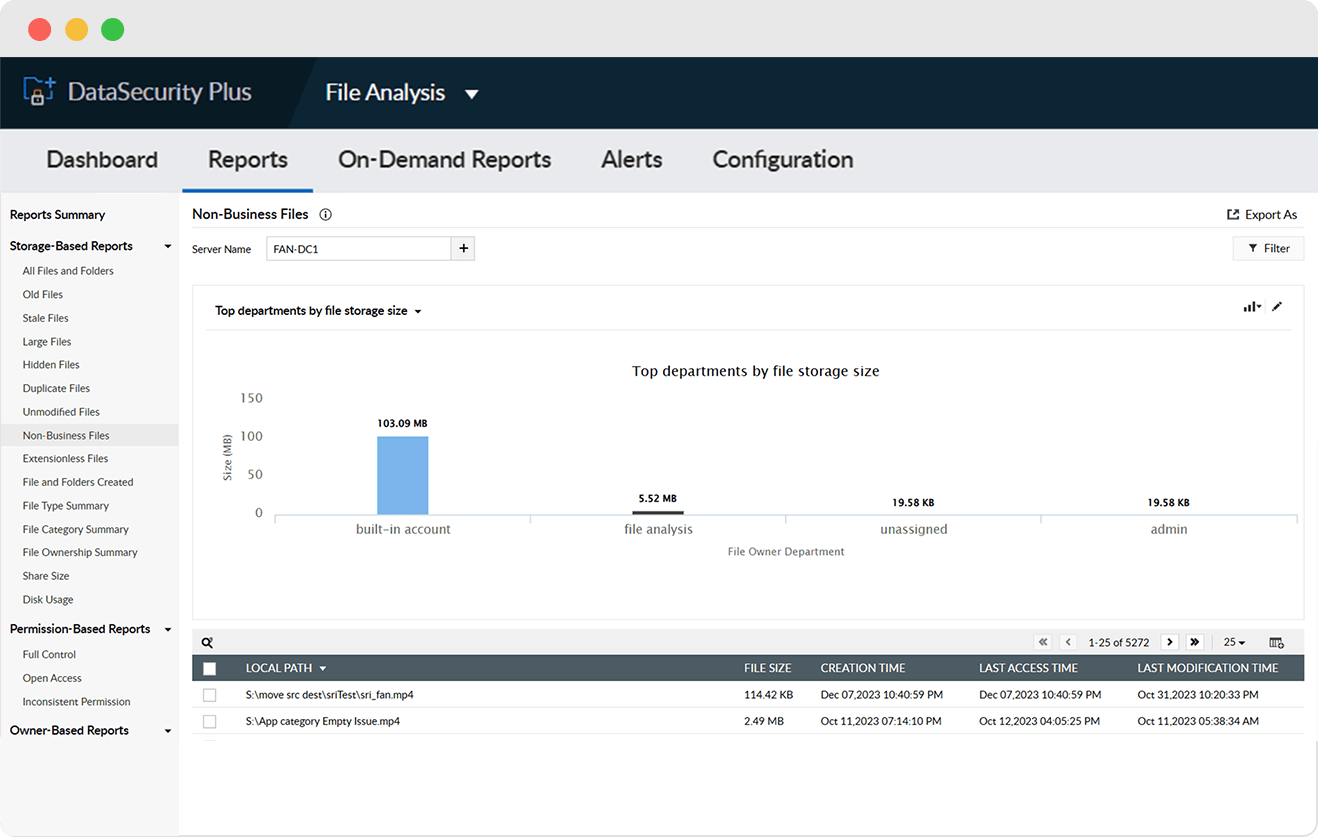
Scan for specific file types or sizes that are unwanted or unnecessary in your organization..
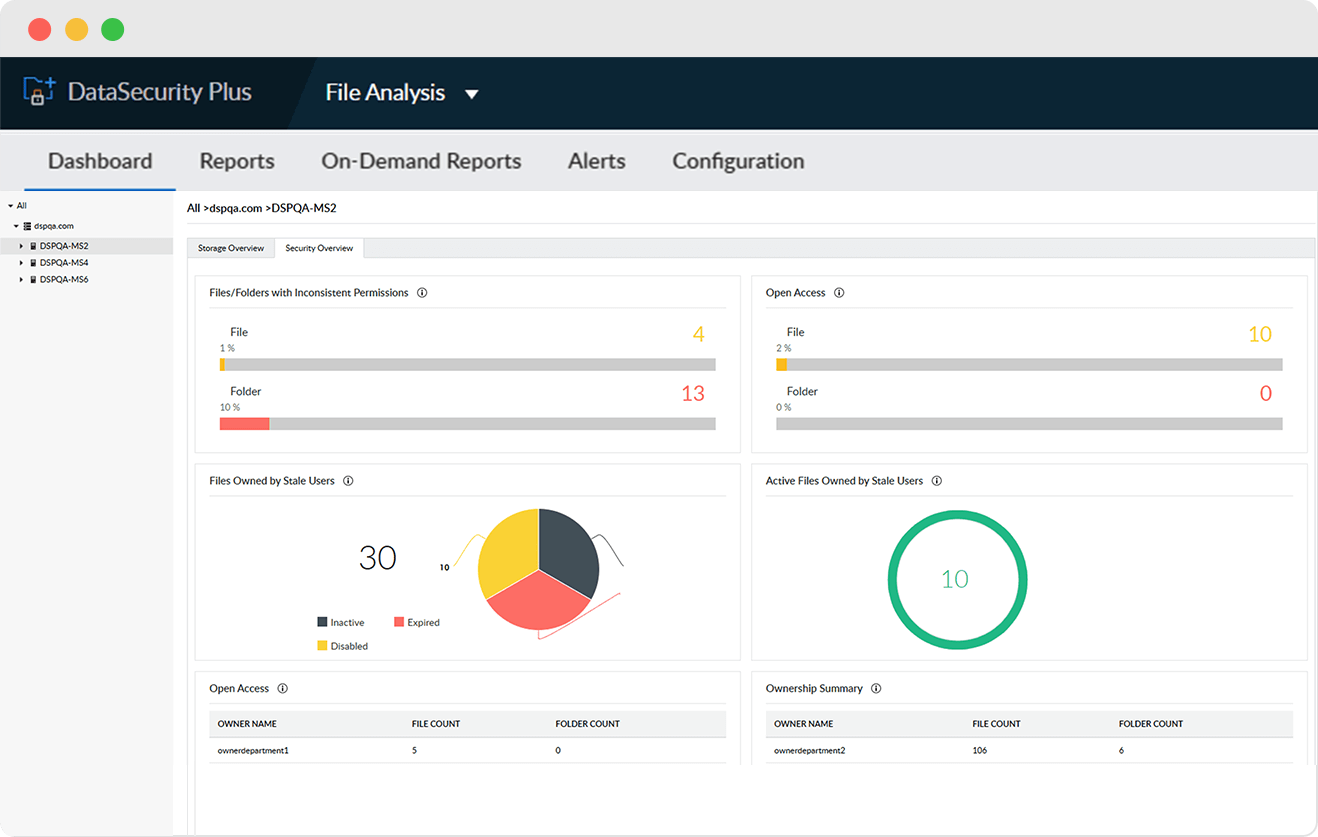
Find folders and shares with excessive access rights such as those open to everyone or those that allow full control access.
Identify and manage files owned by inactive, disabled, or deleted users to minimize the risk of privilege misuse.
Locate files with broken or disrupted permission propagation to prevent instances of excessive or inadequate permission levels.
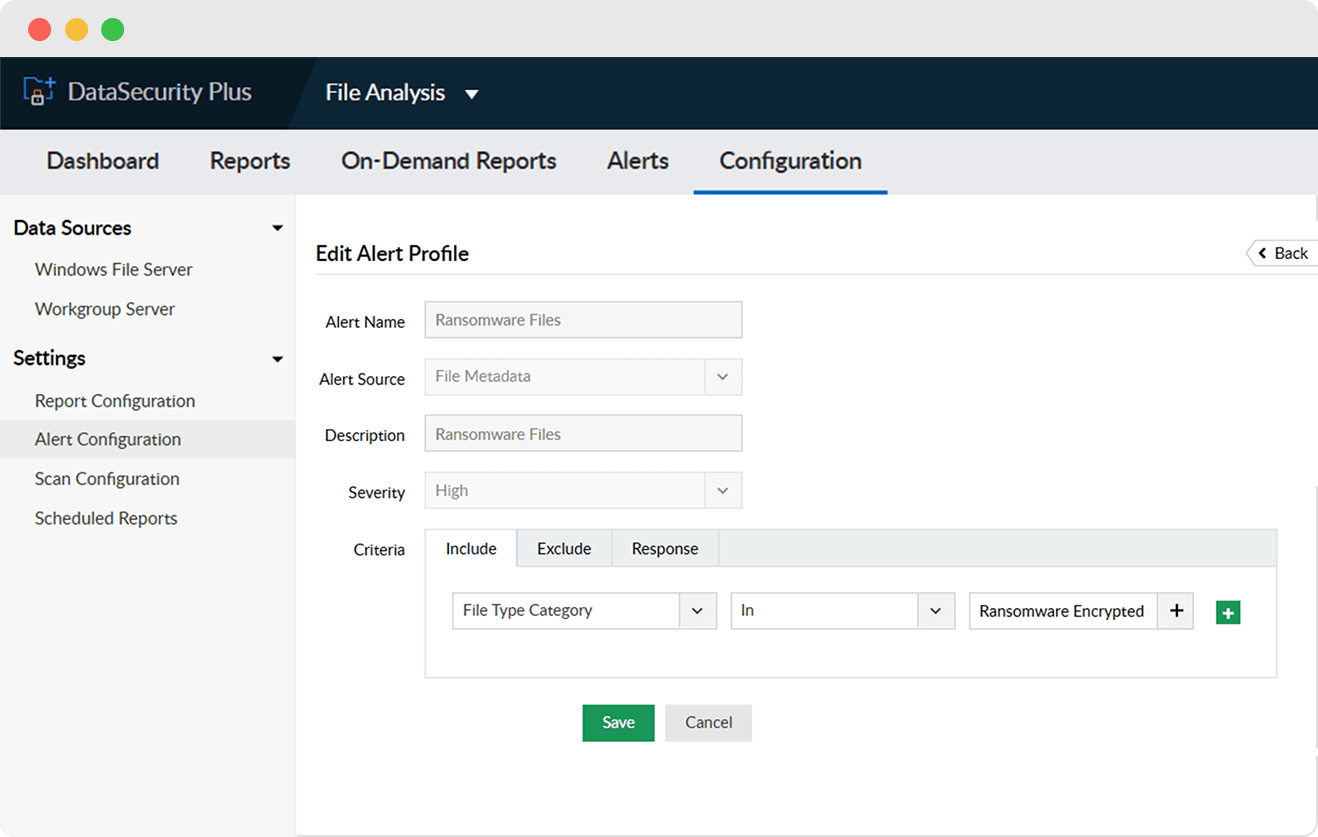
Notify admins on finding any instance of ransomware-infected files in your data stores using our library of known ransomware file types.
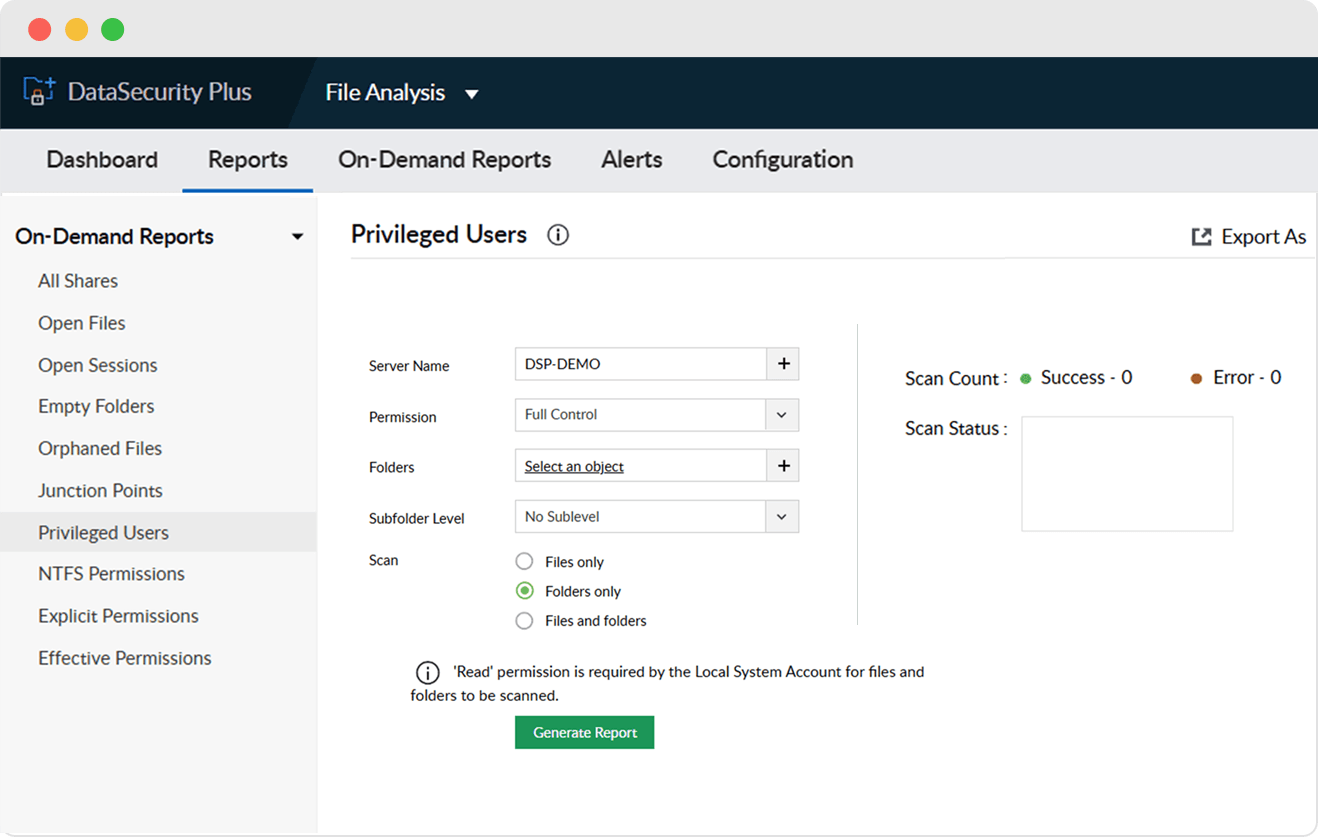
Identify users with elevated privileges to files and folders at all sub levels to ensure the confidentiality and integrity of sensitive data.
Generate instant reports on users' effective permissions, and identify who has access to do what to your sensitive data.
Understand and manage your data stores better with FileAnalysis
Download a free trial





Understand and manage your data stores better with FileAnalysis
Download a free trial





Get a quick glimpse of all the capablities offered
by FileAnalysis.
Audit, monitor, receive alerts on, and report on all file accesses and modifications made in your file server environment in real time.
Detect, disrupt, and respond to sensitive data leaks via USB devices, emails, printers, and more through real-time security monitoring.
Perform content inspection and contextual analysis to discover sensitive data in files, and classify it based on vulnerability.
Track enterprise web traffic, analyze the use of shadow applications, and enforce policies to safeguard employees against inappropriate or malicious web content.