OAuth is an authorization protocol that allows authenticated access to server and service resources without sharing any logon credentials. OpenID Connect is an identity layer on top of OAuth's framework.
In simpler terms, OAuth helps you access a resource without having to prove your identity after you have already been authenticated.
While OAuth provides the basic framework to achieve this and leaves the decision of choosing which user details to use for authentication up to you, OpenID Connect attempts to standardize such customizable areas in OAuth.
If you are using any application that requires authentication, there is a good chance you are using Security Access Markup Language (SAML) to access the application. SAML 2.0 is the widely used, industry-standard authentication protocol today.
Both SAML and OAuth can be used to implement single sign-on (SSO). Instead of comparing these two protocols, it is better to understand how they can work together to give you the best of both worlds. SAML is an authentication protocol, while OAuth is an authorization protocol. You can use SAML wherever a login is required and use OAuth to provide access to other protected resources like applications and files.
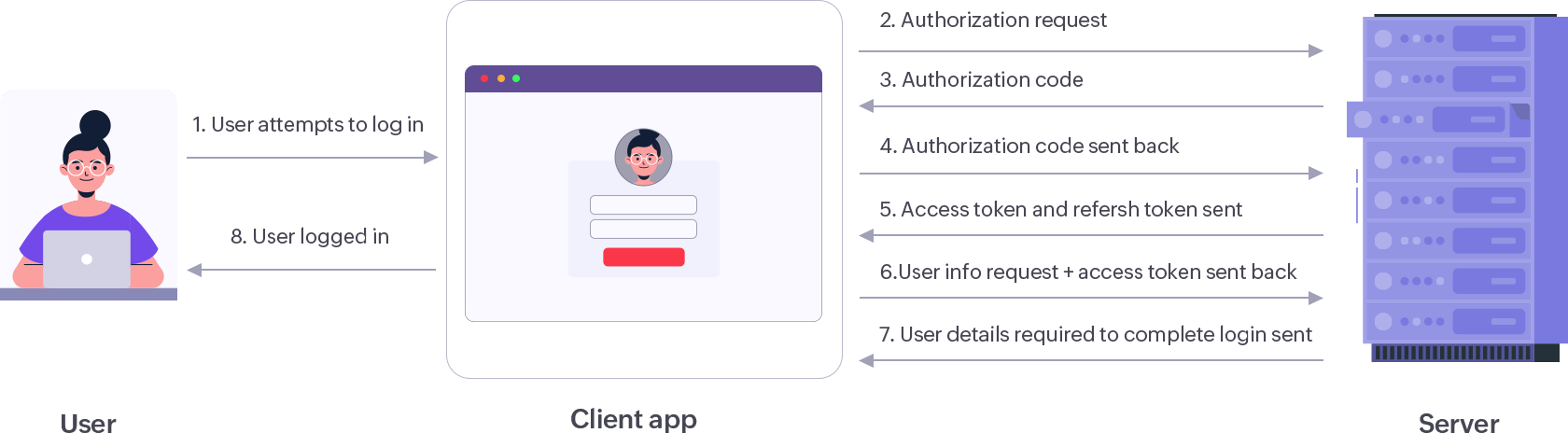
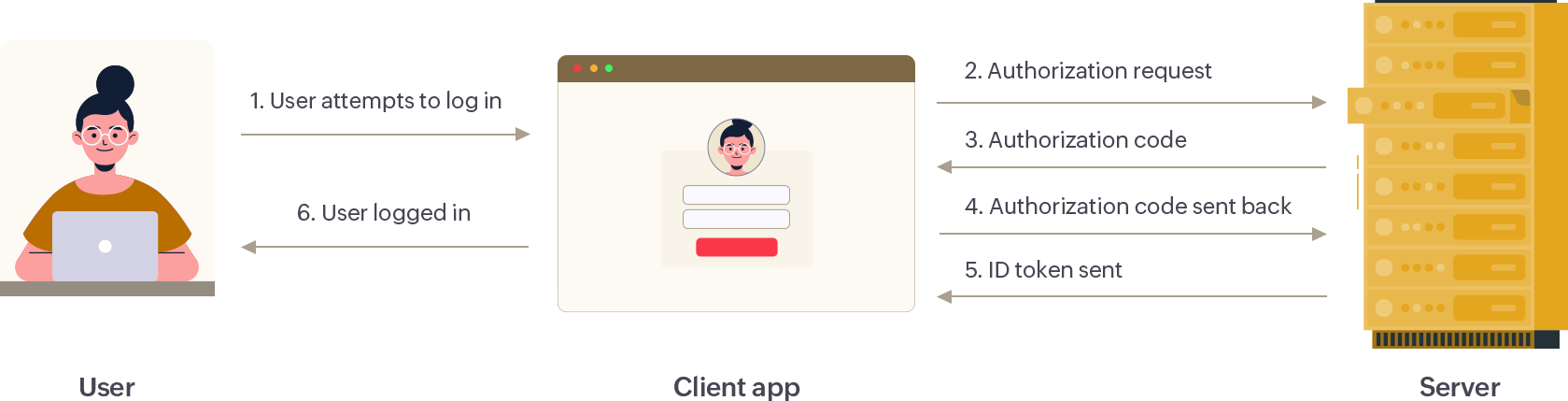
Verifies the user's credentials and provides the key that allows them to log in. As the authorization server owns all the user details, it has control over the scope and duration for which clients can access these details.
Contains the resources the user wants to access. The client application communicates with the server to get information that can verify a user's identity before granting access.
Attempts to log in to the client application. The user information is stored in the server to verify and provide access to the right users.
This is how OAuth provides SSO:
OpenID Connect is similar to OAuth SSO, but an ID token is used here. The ID token contains the signature of the server and the user details. There are two possible scenarios here: application-initiated login and server-initiated login. Let's understand the workflow in both these cases.
Application-initiated login
The most important feature of OAuth is the tokenization of data. Tokens ensure that the actual credentials and other sensitive information of a user account are not exposed to data hacks and other attacks. Also, if any suspicious activity is detected, a token can be easily revoked by the server.
OAuth relies on SSL, which uses cryptography, to ensure that the data transferred between the server and the client remains private, rendering even the tokens secure.
Users are given limited access since the tokens are time-bound. This prevents risks caused due to prolonged availability of protected resources.
Identity360 is a cloud-based SSO and identity management solution. It can centralize access, simplify user management, and audit application access and usage.
Identity360 supports major enterprise applications and in-house applications that use OAuth and OpenID Connect, in addition to SAML-enabled applications. Here are some benefits of using Identity360 to implement SSO:
Allow users to access multiple applications, including on-premises, cloud, and in-house applications, from one secure portal.
Enable SSO for any application that supports SAML, OAuth, or OpenID Connect.
Learn about every application access, successful or failed logon, and much more with prepackaged reports.
Free users from having to remember different usernames and passwords for their enterprise applications; once they log in to Identity360, they will be able to access other applications without going through the verification process multiple times.
Save the time and effort involved in setup and maintenance. Just a few clicks and you are good to go.