- Key components of PKI
- Why is PKI important?
- How does PKI work?
- PKI Certificates: The chain of Trust
- Different models of trust in PKI
- Digital certificates in PKI?
- SSL/TLS certificates used in PKI?
- What are the challenges that PKI solves?
- Common PKI use cases
- PKI best practices
- Importance of a certificate management tool in PKI
Key components of PKI
01. Public and private keys
Public and private keys encrypt communications utilizing the PKI framework. The public key is visible to all, while the private key is used to decrypt the message and remains private to the entity.
Think of the public key in PKI as a lock, unique to users and entities and used for encryption. The lock, although unique to the entity, is publicly visible to anyone looking to access it. The private key is the specific key for that specific lock, used to decrypt messages. Unlike the public key, the private key isn't shared or visible to anyone and is known only to the user and entity that owns it.
When an encrypted message is sent to the entity, the message is encrypted using its public key. If the message is from an authorized source, the entity will then decrypt it using its own private key.
02. Digital certificates
Digital certificates, or PKI certificates, are a pivotal component of PKI. Certificates are the digital world's passports and identity cards—they help verify if the digital entity is who they say they are. A certificate contains information about the user or device that the certificate belongs to along with the entity's public key. Certificates involve expiration dates and need to be renewed periodically. If not renewed in time, they become invalid.
03. Certificate authorities
Certificate authorities (CAs) form the backbone of PKI. A CA is a trusted organization that validates the identities of digital entities and issues signed digital certificates to applicants once verification is complete. The certificate issued by the CA binds a public key and identity details to the subject of the certificate. This ensures that no one can claim to be the entity or replicate its public key, preventing manipulator-in-the-middle (MitM) attacks (also known as man-in-the-middle attacks). Some well known certificate authorities include Sectigo, DigiCert, GoDaddy, GlobalSign, and Let's Encrypt.
04. Registration authorities
CAs use registration authorities (RAs) to help verify the identity of certificate applicants. RAs serve as intermediaries between the entity applying for a PKI certificate and the CA. RAs receive certificate signing requests (CSRs) for issuance and renewals, verify the identity details of the applicant, request proof of identity from the applicant, vet the documents, and pass the application to the CA. RAs include government agencies, banks, and other CAs.
05. Certificate signing requests
A certificate signing request (CSR) is an encrypted message that contains information about the entity applying for the issuance or renewal of a digital certificate. Typically, a CSR is generated on the server that the certificate will be installed on. The CSR contains information about the applicant such as domain name, organization name, organizational unit, location, country, and email address. It will also contain the public key of the server, along with the key size and type.
Why is PKI important?
In a world where the threat landscape is growing and cyberattacks are becoming increasingly common, the need for secure, encrypted digital communications is paramount. Not only does PKI verify the identity of the client and server involved by binding their public keys to their respective digital certificates, it also ensures that the session is end-to-end encrypted, preventing snooping and possible MitM attacks, making PKI a necessity in any digital interaction.
Digital signatures, issued by trusted CAs and in line with PKI chain of trust mechanisms, ensure that data isn't tampered with in transmission. This establishes trust and maintains the integrity of sensitive online activities, such as bank transactions, credential-based logins, and confidential data transfers. Additionally, compliance standards like the PCI DSS and HIPAA require organizations to utilize PKI for digital communication.
How does PKI work?
PKI is a framework that imposes mechanisms to verify the identity of digital entities by mapping and binding public keys to the certificate holder. Since communication in PKI is encrypted end-to-end and happens using asymmetric encryption, only a recipient with the right private key can decrypt information passed to it. Digital signatures in certificates ensure that data is not tampered with in transit and preserve the integrity of the communication.
01. Asymmetric encryption utilized in PKI
PKI uses the asymmetric method of encryption to achieve secure digital communication. Asymmetric encryption utilizes a public-private key pair to establish secure communication. The sender and the receiver share their public keys with each other, and the sender encrypts the message based on the receiver's public key. The receiver then utilizes their private key to decrypt the message received. The key pairs are generated using a suitable algorithm like the RSA algorithm, Elliptic Curve Digital Signature Algorithm (ECDSA), or the Diffie-Hellman algorithm.

02. PKI: A step-by-step process
- 01
The first step in the PKI management process is for the applicant to generate a public-private key pair. Once the public-private key pair is generated for the server, the server creates a CSR based on the type of certificate needed.
- 02
The CSR is then passed on to a CA to be vetted, and for the issuance of a signed digital certificate. The CA, either by utilizing a registration authority or independently, verifies if the information pertaining to the applicant as provided in the CSR is correct, and if the applicant is who they claim to be. Do note that the verification process varies depending on the type of certificate requested.
- 03
Post verification, the CA creates and signs the certificate for the server and issues it to the applicant, while also storing a copy. The digital signature of the CA certifies that the information mentioned in the certificate and the public key belongs to the entity holding the certificate. The CA signs certificates using its private key, authenticating the signature and ensuring that it cannot be duplicated.
- 04
When a user or client reaches out to the entity to establish communication, it verifies the digital signature in the certificate using the CA's public key and establishes secure, encrypted communication with the server. This is also known as an SSL/TLS handshake.
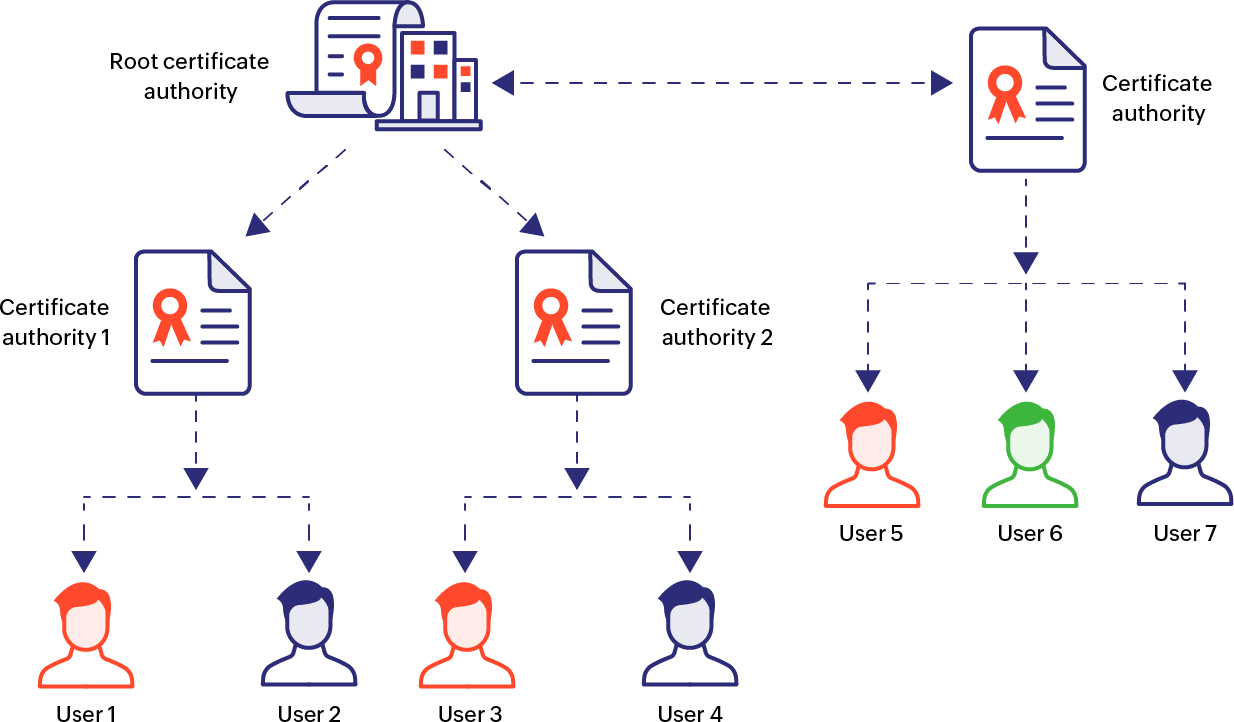
PKI certificates: The chain of trust
The chain of trust in PKI helps verify the authenticity of a certificate and the digital signature by tracing it back to the issuing or root CA. It is a sequential trust system, established from the root CA to the digital entity to whom the certificate belongs. Between the server or digital entity and the root CA, there are usually one or more intermediate certificates.
01. Root certificate
The root certificate is a self-signed certificate of the issuing CA and is stored securely in a browser's trust store. The root certificate is an established token of trust and follows the X.509 certificate standard. Since the certificate is signed using the private key of the root CA, if the private key is compromised, all certificates signed by the root CA will have to be replaced.
To prevent this possibility and ensure the private key of the root is not exposed, the root does not sign the end-server certificates directly. Instead, there exist one or more intermediary certificates that link the server to the root.
02. Intermediate certificates
Intermediate certificates serve as connecting links between the end-server and the root. In the hierarchical model of the chain of trust, the intermediary certificate that is directly under the root in the chain of trust hierarchy is signed by the root CA.
If there are more than one intermediary CAs between the root and the end—server, then the primary intermediate CA—that is the CA immediately under the root in the chain of trust hierarchy—signs the certificate of the second intermediary, and so on, until the end-server's certificate.
03. End-entity certificates
The end-entity certificates are installed on the end-server and verify the identity of the certificate holder. This could be an SSL/TLS certificate, email certificate, EMV certificate, or code-signing certificate.
In the context of web communication where a web browser is trying to establish connection with a website or domain, the end-server certificate is the SSL/TLS certificate of the domain. The SSL/TLS certificate will contain information about the domain, organization, and public key of the webserver the certificate is stored in, along with the signature of an intermediate CA. This signature can be traced back hierarchically to the root CA, which serves as the trust anchor at the top of the chain.
The hierarchical trust method, although the most popular, isn't the only method of trust used in the PKI. Learn more about the different methods of trust used in PKI below.
Different models of trust in PKI
- 01
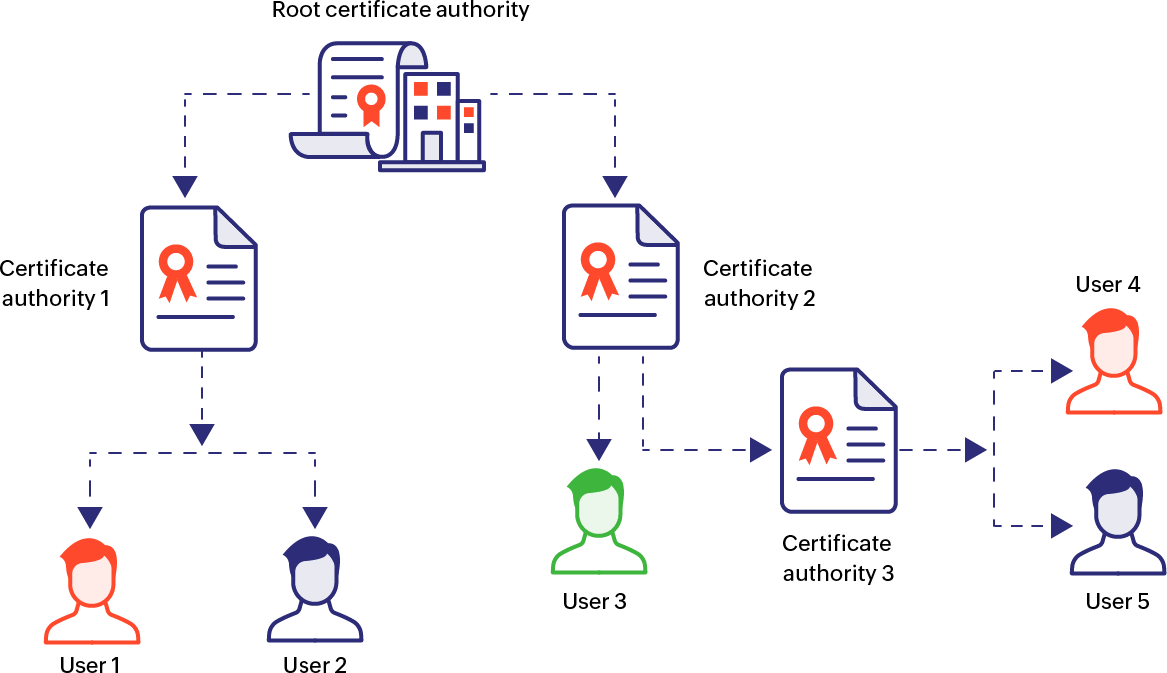
Hierarchical trust model
The hierarchical method is the method of trust to understand how root, intermediary, and end-entity certificates work. It is a top-down, unidirectional approach to trust, where the root certificate serves as the trust anchor and sits at the top of the chain. Between the end-entity certificate and the root certificate, there exist one or more intermediate certificates that eventually trace back to the root CA.
- 02
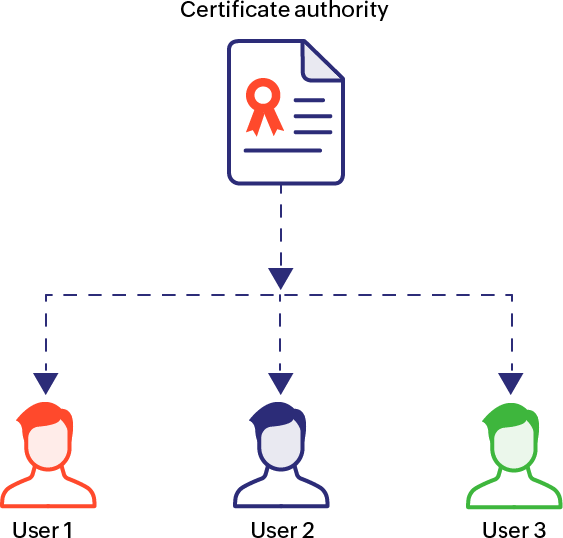
Single CA model
The single CA model, like the name suggests, involves only one CA. There is no intermediate CA or certificate between the issuing CA and the end-server. This model poses a risk of collapse—should the private key of the root certificate be altered, all certificates issued by the root CA must be replaced.
- 03
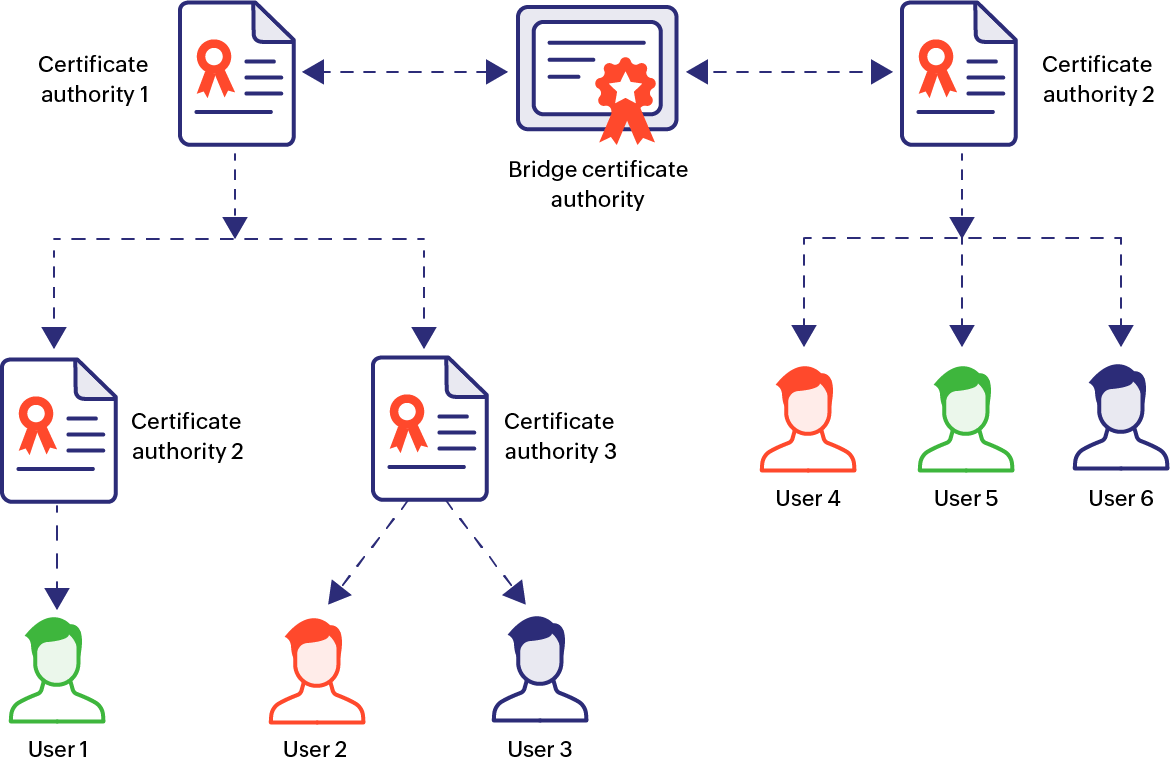
Bridge model
The bridge model involves the root CAs of multiple hierarchical PKI trees and domains connected to each other through one or more bridge CAs. The bridge CAs act as a bidirectional hub for peer-to-peer trust verification between different CAs and establishes trust between different PKI domains. This establishes trust between different PKI domains such that digital certificates of one PKI domain are trusted by entities in the other, enabling secure communication.
- 04
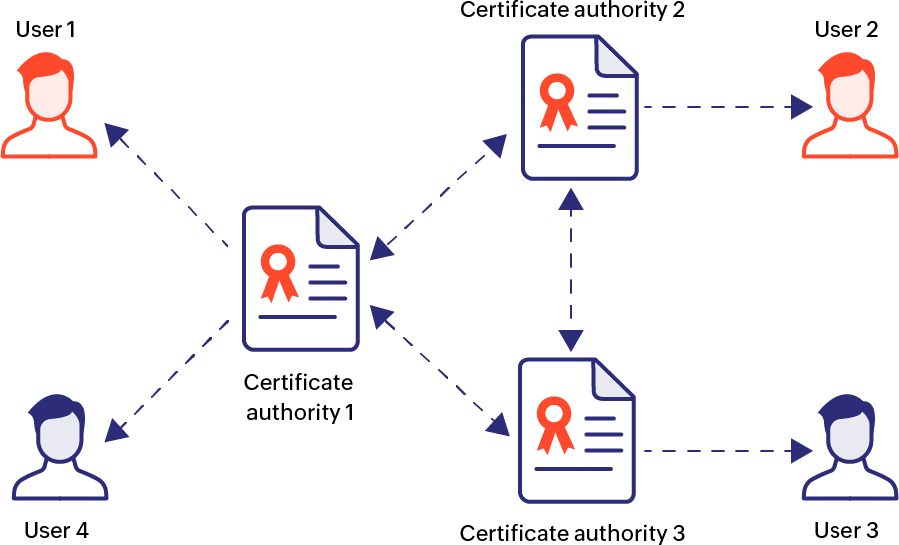
Mesh model
Unlike the hierarchical or bridge models, the mesh model has a decentralized trust system, where every local CA serves as a trust anchor in its own right. In the mesh model of PKI, different CAs are interconnected with each other, where they verify information in a bidirectional manner with other CAs connected to them. Since there is no root CA or a superior trust anchor based on hierarchy, the mesh model of PKI does not entail a single point of failure.
- 05
Hybrid model
The hybrid model of PKI is a blend of the different models we have seen above. It utilizes characteristics of the hierarchical, bridge, and mesh models where suited in its architecture. The hybrid model is largely built to be flexible—depending on different organizational needs—making it agile and scalable.
What is the role of digital certificates in PKI?
SSSL/TLS certificates are a fundamental component in ensuring secure web-based communication. They are typically used to establish encrypted communication between a web server and a web browser or client. They protect the integrity of the information that is transmitted and prevent data tampering.
SSL/TLS certificates can be broadly classified into three main subtypes:
- Domain validation (DV) certificates: Along with verifying the ownership of a domain and if the certificate holder has the rights to use the domain, OV certificates also verify organizational information.
- Organization validated (OV) certificates: Along with verifying the ownership of a domain and if the certificate holder has the rights to use the domain, OV certificates also verify organizational information.
- Extended validation (EV) certificates: These certificates are subjected to a stringent validation process. EV certificates verify organizational details of the certificate holder such as their legal status and physical existence.
Different ways in which SSL/TLS certificates are used in PKI
- Code signing certificates: Code signing certificates are certificates that are signed by software developers to certify their code or application and verify their ownership. The purpose of code signing certificates is to ensure that the code hasn't been tampered with, verifying that it can be safely downloaded and used.
- Email signing and encryption certificates: Email signing certificates or secure/multipurpose internet mail extensions (S/MIME) certificates are signed to verify the authenticity of the sender and to protect against email spoofing. Meanwhile, email encryption certificates are used to encrypt email messages to maintain privacy of the contents of the email. They do this by using the recipient's public key, so that only the recipient's private key can decrypt it.
- Client authentication certificates: Client authentication certificates help authenticate a client—that is, a digital entity such as a user or device—and verify their identity. Client authentication certificates convey to the server that the client is trying to connect, that the client is who they say they are, and they can be trusted. Servers can implement access control restrictions based on the client certificate.
- Server authentication certificates: Server authentication certificates are SSL/TLS certificates used to verify the identity of servers when clients attempt to connect to it. Clients (e.g., web server) can verify that they are connecting to the right server (e.g., website) and not an imposter or malicious site.
What are the challenges that PKI solves?
Strong cryptography and digital certificates play a vital role in securing modern enterprise infrastructure, but managing them efficiently across a large organization poses significant challenges. Without proper PKI management, organizations struggle with authenticating users and devices, securing communications, and maintaining compliance with security standards. The lack of a robust PKI solution can lead to unexpected certificate expirations, security breaches, and service disruptions.
As organizations increasingly rely on digital transactions and remote access, the need for reliable identity verification and encrypted communications is paramount. Traditional password-based systems are vulnerable to various attacks, while manual certificate management processes are error-prone and resource-intensive. The complexity multiplies when dealing with numerous endpoints, applications, and services spread across different networks and locations
PKI addresses these challenges by providing a framework for managing digital certificates and encryption keys throughout their life cycle. It enables organizations to establish trust relationships, secure sensitive data transmission, and implement strong authentication mechanisms. A comprehensive PKI software helps automate many aspects of certificate management, reducing human error and ensuring timely certificate renewals. This systematic approach of PKI management helps organizations maintain security standards while scaling their digital operations
Common PKI use cases
- 01
Secure email communication
Email PKI enables users to digitally sign and encrypt their email messages, ensuring confidentiality and authenticity in business communications. Using protocols like S/MIME, recipients can verify the sender's identity and be confident that the message hasn't been tampered with during transmission.
- 02
Digital certificates for websites
Website certificates form the backbone of secure internet browsing by enabling HTTPS connections that encrypt data between browsers and servers. When users visit a website with a valid certificate, they see the padlock icon indicating a secure connection for protecting sensitive information like passwords and credit card details.
- 03
Code signing
Code signing certificates allow software developers to sign their applications digitally, proving their identity as the legitimate publisher. This helps ensure code integrity. When users download or install signed software, their OS can verify the signature and warn them if the code has been modified since it was signed. This protection is essential in preventing malware distribution and maintaining trust in software distribution channels. PKI software helps in discovering and managing code-signing certificates.
- 04
Document signing
Digital document signing enables paperless workflows by providing legally binding electronic signatures that are impossible to forge. Each signature is uniquely tied to both the signer and the document content, creating a tamper-evident seal that maintains the document's integrity. This technology has revolutionized contract management, legal proceedings, and government services by reducing processing time from days to minutes while maintaining security and authenticity.
- 05
Internet of things
In the internet of things (IoT) ecosystem, PKI provides a scalable way to authenticate and secure millions of connected devices. Each device receives a unique identity certificate, enabling secure communication with other devices and central management systems. This infrastructure is crucial for protecting smart homes, industrial IoT deployments, and critical infrastructure from unauthorized access and tampering.
- 06
Internal IT infrastructure
Organizations utilize PKI management to secure their internal networks by issuing certificates to servers, workstations, and network devices. These certificates enable secure authentication and encrypted communication between different components of the IT infrastructure, protecting sensitive data and services. Comprehensive PKI software helps provide centralized control over security policies and certificate life cycle management.
PKI best practices
Some best practices for organizations to keep in mind while implementing a robust PKI solution:
- 01
Secure private keys with hardware security modules (HSMs)
As mentioned in the above sections, private keys are the cornerstone of PKI, so protecting them is critical. Organizations can use HSMs to store private keys securely, as they provide a high level of security and physical protection. Limiting access and enforcing strict controls around HSMs can further reduce the risk of private key compromise.
- 02
Use strong cryptographic algorithms and key lengths
To protect against evolving threats, organizations can utilize strong encryption algorithms such as RSA-2048 or ECDSA with P-256 and SHA-256 for hashing. They should also regularly review and update algorithms and key lengths as cryptographic standards evolve to stay resilient against emerging vulnerabilities.
- 03
Automate certificate life cycle management
Organizations should look to automate certificate provisioning, renewal, and revocation processes as part of their PKI management strategy to minimize the risk of certificate expiration and outages. Effective certificate life cycle management with the right PKI solution in place prevents security incidents and ensures continuous protection by maintaining the validity and authenticity of certificates.
- 04
Implement access controls and maintain comprehensive audits
Administrators should enforce strict access controls for PKI components, ensuring only authorized personnel can access sensitive systems. Regular audits and logging are essential to detect unauthorized access attempts and maintain accountability. Auditing also helps organizations with compliance and ensure there are regular checks and balances. A comprehensive PKI software can help implement the right access controls and maintain continuous audit trails.
- 05
Disaster recovery and business continuity
A comprehensive disaster recovery and business continuity plan is crucial for maintaining PKI operations during critical situations. Organizations must establish clear procedures for responding to key compromises and maintain secure offline backups of all critical PKI components. Regular testing of recovery procedures ensures that organizations can maintain effectiveness and helps identify potential gaps in the recovery process.
Importance of using a PKI management tool
Modern enterprises usually have thousands of digital entities in their environment, all of which each have a certificate associated with them, and tracking them is nearly impossible. For example, if a certificate renewal is missed, an entire domain can go down, causing financial and reputational damage. If certificates are invalid or expired, the whole PKI structure falls apart. Similarly, mismanaged cryptographic keys can lead to security breaches, data loss, and more. Therefore, PKI solutions form an essential cog in the functioning and implementation of PKI.
A comprehensive PKI management tool like ManageEngine Key Manager Plus helps organizations bring all the certificates and keys in their enterprise environment to a central panel. Using Key Manager Plus, enterprises can manage the end-to-end life cycles of all of their digital certificates and keys. This includes tracking certificate expiry dates and setting up alerts, creating CSRs, rotating and managing keys, mapping certificates to their respective devices, tracking where they are stored, and more.