Last updated on: April 24, 2020
SSH (Secure shell) keys are authentication credentials in the SSH protocol. Technically, they are cryptographic keys responsible for encryption, but functionally they work in ways very similar to passwords. Within an enterprise, SSH keys are primarily used to grant secure access to remote systems. Key-based authentication, commonly known as public key authentication, uses a pair of keys—a public key and a private key—to authenticate users on remote devices.
Public keys or authorized keys are responsible for granting login access to users accessing the remote system. One can imagine authorized keys as locks, granting access to those who possess the right key (in this case, the corresponding private key). Authorized keys are configured separately for each user account, and are usually present in the .ssh/authorized_keys file in the user's home directory.
Private keys or identity keys allow users to authenticate themselves on an SSH server. A private key is analogous to a real key that, when matched, can open one or more locks. As opposed to public keys, private keys need to be safeguarded in a secure place or they might end up in the wrong hands, resulting in misuse of privileges.
SSH-based public key authentication is achieved by generating a pair of distinct keys (a public and a private key) in order to establish connection with remote systems. The user authenticating themselves on the remote machine needs to possess the private key, while the public key should be placed in the target system(s) that the user wants to connect to.
Here's how the SSH key authentication process happens in the background.
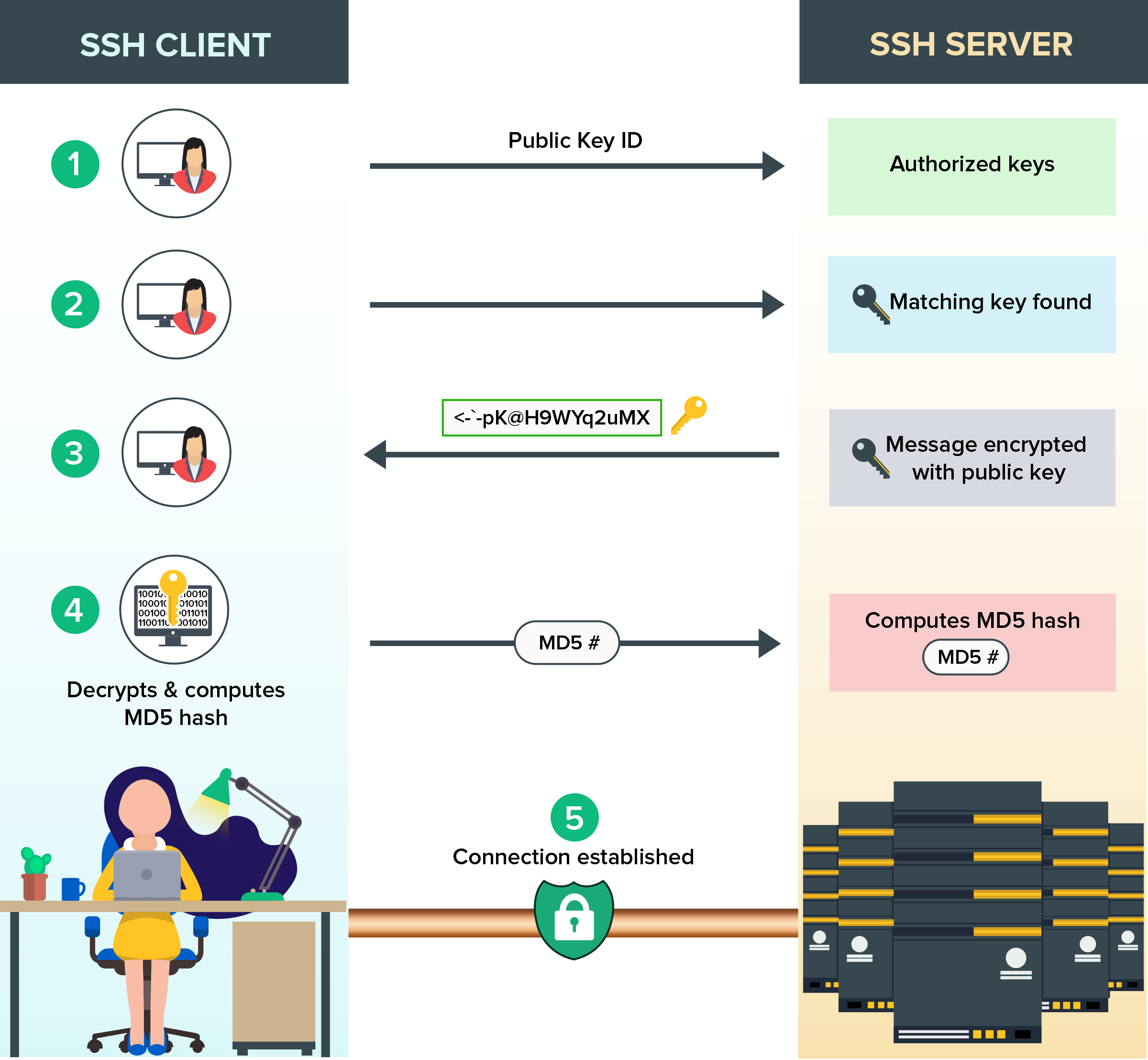
Before beginning the SSH key authentication process, make sure both the client and server have a working version of SSH installed. One great advantage of key-based authentication is that, when implemented correctly, it hugely simplifies the authentication process and increases its security multifold.
On average, a large organization easily houses about one million SSH keys. And despite the awareness created around SSH key mismanagement and risks, most enterprises follow a decentralized approach to key creation and usage. Over time, this results in key proliferation with much less visibility on the extent of access each key provides. SSH key mismanagement can bring trouble to enterprises in many ways, including the following:
One tricky thing about these attacks is that since SSH keys are seldom rotated they’ll continue to remain in the wrong hands until they are somehow discovered and have their access terminated.

Gain complete visibility over your SSH environment now.
Download solution briefSSH key management is the process of securing and automating the life cycle of SSH keys distributed across an enterprise—right from creation to deploying them to necessary endpoints, launching remote sessions, monitoring key-user mappings, performing key rotation, and periodically deleting the unused or unwanted keys. SSH keys belong to the category of crucial digital assets that are constantly undermanaged. Implementing a well-defined management process helps enterprises gain complete visibility over their SSH environment and prevent misuse of privileges stemming from unauthorized access to SSH keys.
Now comes the next obvious question: Where do you begin?
Here are a few steps that will help you get started with the process of SSH key management.
The first step in managing your SSH keys is to discover the existing keys within your network and consolidate them in a centralized repository.

Once you've gathered all your SSH keys in a single place, you have to trace the existing trust relationships to get a clear picture of the extent of access each key grants. Then, you have to lay down the key-user mapping, which will help you identify the number of users in your network who have root access to privileged accounts.
Now that you have complete visibility over your SSH environment, scan and remove SSH keys that are no longer in use. The best practice approach here is to start afresh by deleting all SSH keys associated with the various user accounts in your network, and replace them with freshly created key pairs.
For key generation, it's highly recommended that you streamline the process by administering a centralized framework that only allows users with specific privileges to create and deploy keys to systems within your network. This way, you have the upper hand over the trust relationships within your organization, and you’re able to keep SSH key proliferation at bay.

Once fresh key pairs have been deployed to target systems, it's important to define permissions for each key based on user roles, i.e. restrictions on the host the key can be used from, and which commands the key can execute.
SSH Key rotation is the practice of tossing out the existing SSH key-user association and deploying fresh key pairs from time to time to combat the unfortunate event of SSH key compromise. Both the authorized keys (placed on target systems) and identity keys need to be rotated periodically to avoid potential privilege misuse.

Set up a tamper-proof auditing mechanism to track all user activities involving SSH keys and generate categorized reports. This will enhance the sensibility and readability of the data collected and help administrators make informed business decisions.
When it comes to practical implementation and operational efficiency, these steps are easier said than done. Imagine the amount of workload on the IT administrator who has to carry out all the above mentioned operations for a million SSH keys in their environment! The best way to achieve this is through automation, implementing centralized SSH key management solution that can do all the heavy lifting for you.
Key Manager Plus, the web-based SSH key and SSL certificate management solution from ManageEngine, helps you discover, consolidate, create, deploy, rotate, and track SSH keys from a single pane of glass. It's an all-in-one solution that provides IT administrators complete visibility and control over their SSH environments, makes management hassle-free, and helps them preempt breaches and compliance issues.
If you want to learn more, send an email to keymanagerplus-support@manageengine.com and our product experts will get in touch with you right away!

Key Manager Plus is integrated with ManageEngine’s Password Manager Pro, to provide unified privileged identity management platform.

ManageEngine’s Key Manager Plus enables us to stay on top of SSL certificates for all of our websites. With Key Manager Plus, we’re able to monitor which certificates are nearing expiration and roll out new certificates in a timely manner.Ken Odibe Senior cloud infrastructure consultant, Sapphire systems.
