Logging and monitoring events happening in Amazon Web Services (AWS) DynamoDB is essential to ensure the availability, reliability, and security of your AWS infrastructure. Log360, a comprehensive security information and event management (SIEM) solution, automatically aggregates DynamoDB logs from AWS CloudTrial, a console where all DynamoDB activities are logged. It also gathers DynamoDB access logs from Amazon S3 Server, then instantly analyzes these logs to generate insightful reports.
Log360 constantly monitors DynamoDB for activities such as:
Log360 records who carried out what changes from where and when for security concerns. Any unauthorized activity taking place in the database will be flagged as a threat.
Maintaining an audit trail of the DML and DDL changes happening in DynamoDB is essential for you to detect unauthorized commands being executed and changes being made to your database structure.
Log360 monitors your DynamoDB logs, analyzes them, and provides detailed reports on logon and logoff activities; DDL changes; DML changes; tables created, deleted, and modified; and schema altered, added, modified, and deleted.
These comprehensive and intuitive reports, presented to you in the form of interactive dashboards, can help you identify the right places to spot anomalies in the huge pile of logs.
Log360's machine learning-based user and entity behavior analytics (UEBA) component baselines activities for every user who can access your DynamoDB.
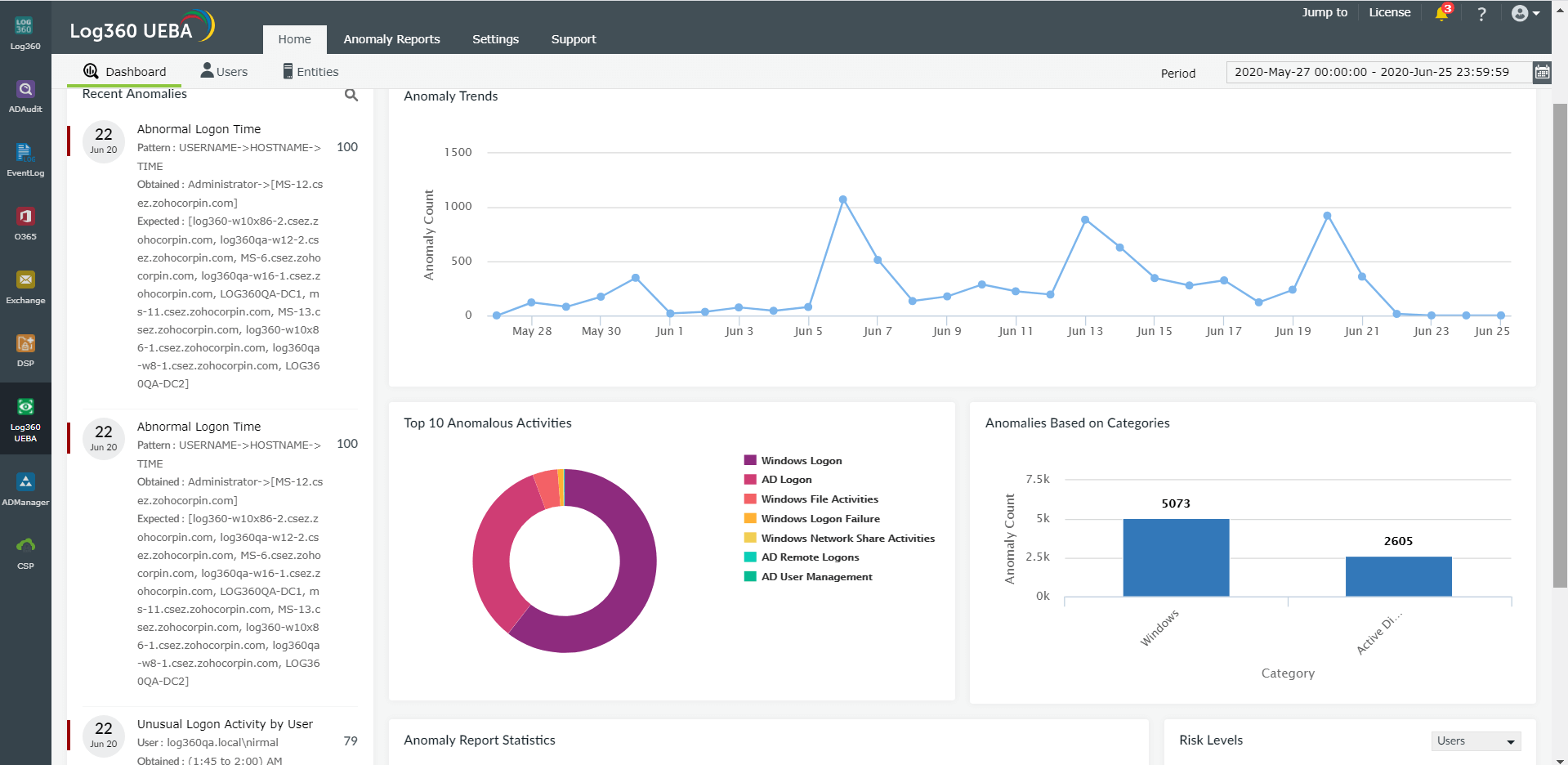
Say a privileged user logs on at an unusual hour of the day and takes snapshots of the database in their system, then proceeds to email the snapshots to a blacklisted domain. Log360's UEBA component flags the unusual logon activity of the privileged user as a threat, and raises an alert to mitigate the attack. Furthermore, the snapshot activity is reported and you can check what data was captured, by whom, and when. This solution spots deviant behaviors based on unusual time, pattern, and event count.
Log360 can flag malicious activities taking place in DynamoDB as threats, and alert you in real-time through SMS and email. You can also configure incident response workflows to be executed in case of a breach or threat to mitigate it and prevent a potential attack from taking place.