The true wealth of a banking organization transcends currency; it resides in the depth and breadth of the data it possesses and the significance of its operations. With cybersecurity threats to the banking industry becoming more sophisticated and pervasive, institutions must constantly improve their strategies to safeguard their data, systems, and clientele. The integration of CASB into banking and finance institutions' IT infrastructure is crucial, given its emphasis on data protection. A CASB solution also offers banking, finance services, and insurance (BFSI) organizations the ability to detect latent threats connected with the usage of web-based and SaaS applications.
Banking on the cloud: Why should data protection be used in BFSI?
The financial sector's increasing adoption of cloud environments—spanning public cloud, private cloud, and SaaS applications—is driven by compelling imperatives:
- Public cloud services like AWS and Azure offer increased performance and scalability, ensuring seamless online services and efficient storage and processing capabilities to manage the burgeoning data volumes.
- SaaS applications—such as CRM, help desk, and chat platforms—deliver productivity gains and streamlined data sharing, characterized by user-friendly interfaces and minimal maintenance requirements.
Application access and data sharing via the cloud can increase risk if not monitored effectively. This is particularly crucial in the finance sector, where any breach or data theft could have profound implications, disrupting critical banking operations. Below, we outline key institutions within the BFSI industry and underscore the significance of their operations:
- Banks: Handle financial transactions and manage vast amounts of personal data, including account details and transaction histories.
- Insurance companies: Handle sensitive information such as policyholder data, health records, and financial transactions, necessitating robust security measures to protect privacy and prevent fraud.
- Stock exchanges: Facilitate trading activities involving sensitive market data and transactions, influencing global economies.
- Payment processors: Facilitate electronic transactions—including credit card payments and online transfers—making them high-value targets for cyber criminals seeking financial gain.
- Credit rating agencies: Hold sensitive data on individuals' credit histories and financial behaviors, influencing lending decisions and thus requiring stringent data protection measures.
- Asset management firms: Manage investments and assets on behalf of clients and handle sensitive financial information and trade secrets, necessitating strong cybersecurity defenses to safeguard against data breaches and insider threats.
- Central banks: Custodians of monetary policy that hold sensitive economic data, critical for economic security.
- Regulatory authorities: Enforce financial regulations, handle sensitive market information, and maintain the integrity and stability of financial systems.
Table 1 below illustrates the diverse array of sensitive data held by institutions within the BFSI sector.
| Financial information | Personal identifiable information (PII) | Health and medical information (for insurance institutions) | Authentication credentials |
|---|---|---|---|
|
|
|
|
Table 1: Types of sensitive data handled by banking and financial institutions.
Cloud IT infrastructure in BFSI institutions
Banking institutions utilize numerous software applications for facilitating and managing backend transactions and operations. Such software can be hosted on private or public cloud environments and made accessible to vendors, employees, clients, and external parties. This includes virtual appliances, application servers, database servers, etc. Also, SaaS applications for help desk, CRM, mail, and chat are accessed by employees from within the enterprise network and remote network.
The financial institution's private networks and public cloud environments are protected with firewalls and IDS/IPS systems to prevent malware, phishing, and other cybersecurity threats. Figure 1 below explains a basic overview of the cloud IT infrastructure in the financial sector.
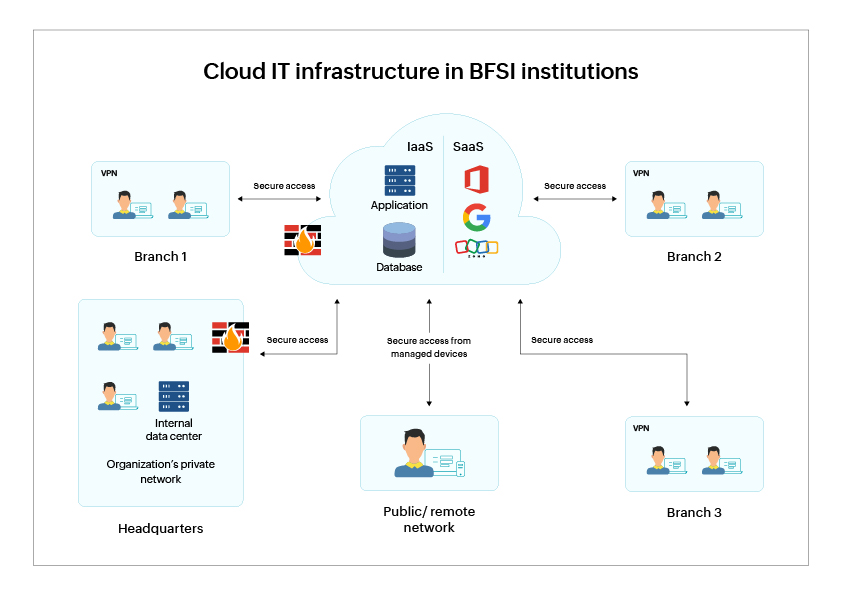
Figure 1: A diagram of cloud IT infrastructure in financial institutions
Risk of cloud applications in BFSI
The cloud application risks in the financial sector stem from the potential for shadow IT, enabling access to unauthorized cloud applications and the ease of download and upload of sensitive data. These factors can lead to data exfiltration and data theft.
When employees use unauthorized cloud services, they may inadvertently expose sensitive financial data to external threats due to the lack of proper security controls and encryption measures in these unauthorized platforms. The IT department may be unaware of the existence of these shadow IT applications, making it difficult to monitor and manage security risks effectively. Additionally, cloud applications enable users to upload, store, and download data from anywhere, using any device connected to the internet.
Here are examples of cloud application risks in the finance sector
- Shadow IT (data exposure): A financial analyst accessing risky cloud applications from the office network. It can be an analytics solution, a spreadsheet tool, or a PDF editor that the employee is using without the IT team's oversight. This action, whether intentional or not, poses a significant risk of exposing the bank's private data to unauthorized parties.
- Insider threat (data theft): An analyst downloads sensitive bank customer data from the CRM onto their work machine, a managed device. The analyst then uploads this data to their personal Dropbox account from the same managed device. The acquisition of this data allows for potential sharing and transfer to personal devices, creating a significant risk of data theft and unauthorized dissemination.
Financial institutions must carefully evaluate the security posture of their cloud service providers and implement additional controls—such as encryption and access controls—to mitigate the risks associated with shared cloud environments effectively.
Benefits of using CASB in BSFI
CASB solutions in BFSI can help discover shadow application usage and provide detailed analysis on top cloud apps used, top users accessing banned applications, and more. This can help organizations in the BFSI industries gain better visibility and control over their cloud usage, ensuring compliance with industry regulations and data protection laws.
A CASB can monitor HTTP/HTTPS traffic flowing out of the organizational network with the help of deep packet inspection (DPI) and provide in depth details about file uploads and downloads such as file name, file size, user, and file type. This will help detect and prevent unauthorized transfer of sensitive data in the cloud, thus mitigating insider threats.
By implementing CASB solutions, BFSI organizations can improve their overall cybersecurity posture and mitigate the risks associated with cloud adoption. CASB solutions can help BFSI organizations actively enforce access controls, data encryption, and data loss prevention policies in the cloud, thereby protecting critical business information from unauthorized access and potential data breaches. Figure 2 below shows the CASB dashboard in ManageEngine Log360.
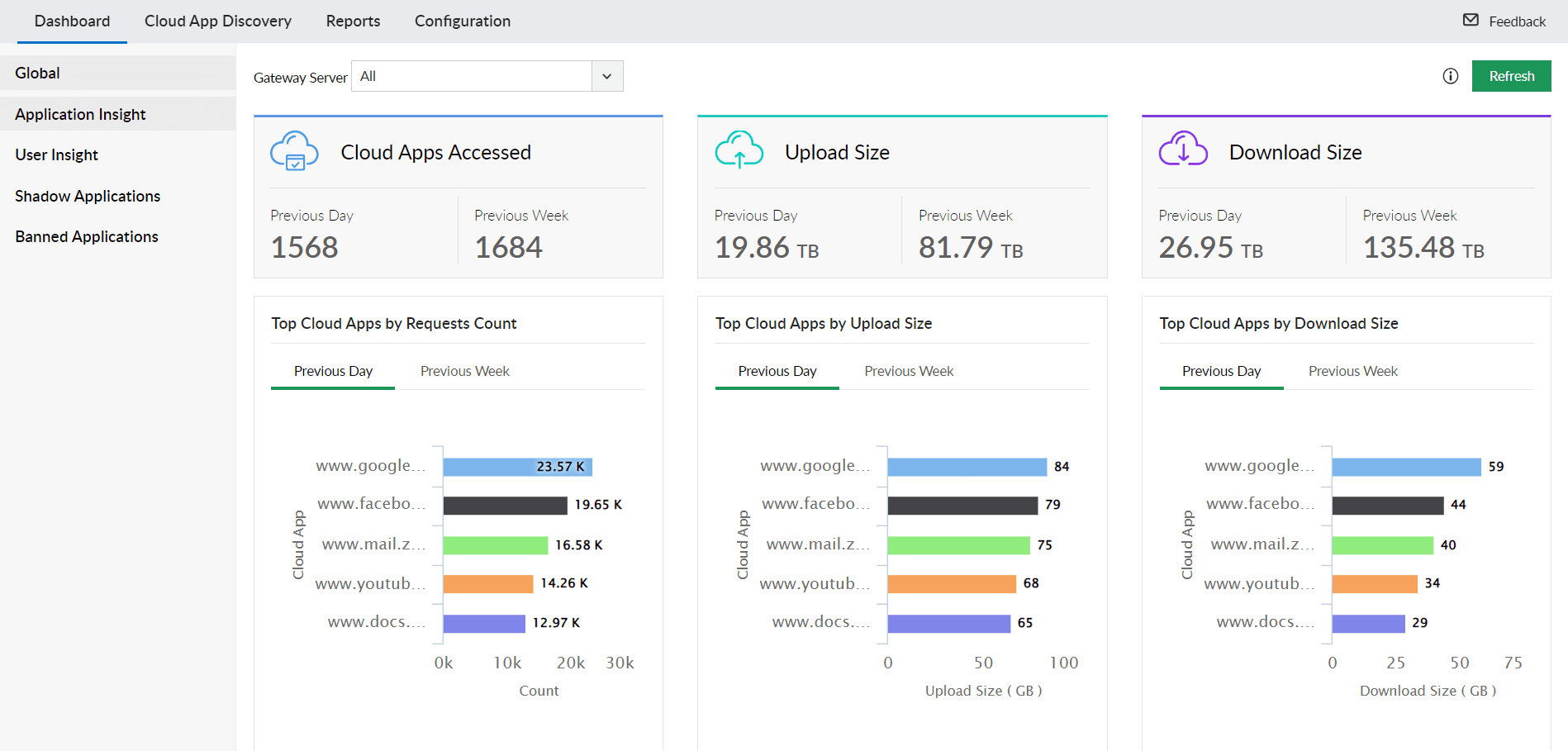
Figure 1: CASB dashboard in ManageEngine Log360
ManageEngine Log360 combines CASB with powerful threat detection, investigation, and incident management capabilities to provide comprehensive security for the BFSI sector. It can help IT teams in the finance sector monitor user activity in the cloud and enforce security policies to protect sensitive data.



