The education sector is now the most frequently targeted industry for cyberattacks. More than 700,000 threats were recorded in the educational sector between April and June of 2023, according to the Economic Times.
Why is the educational sector the prime target?
Cybercriminals find the educational sector vulnerable for a number of reasons.
Sensitive data:strong Educational institutions collect and store significant amounts of personal data about students, faculties, and staff, including names, addresses, Social Security numbers, financial information, and academic records. This makes them prime targets for cybercriminals who exploit this data for financial gain.
Inadequate security protocols: Smaller educational institutions, and especially those with limited resources, often do not possess cybersecurity protocols as strong as organizations in other industries.
Large attack surface: Educational institutions often have multiple entry points that hackers can leverage to infiltrate the network and compromise sensitive data. These entry points include computers, servers, mobile devices, and IoT devices.
Lack of security training: Personnel in the education industry often lack the necessary training to identify and address cyberthreats. Inappropriate actions taken in terms of opening files containing malware, clicking on suspicious links, and using weak passwords jeopardize network security.
Competing financial pressures: Cybersecurity might not receive the priority it deserves in educational institutions that frequently operate on tight budgets.
Research findings are attractive targets: Universities and other academic institutions conduct important studies and produce intellectual property, such as patents, research findings, and proprietary data. These might be targeted by cybercriminals looking to steal sensitive data for financial gain or competitive advantages.
How to stop cyberattacks in the educational sector
- Ensure that only authorized users have access to sensitive data and resources by enforce strong access restrictions (like RBAC and MFA) and the principle of least privilege.
- Update firmware, operating systems, and software with the most recent security patches and updates.
- Keep sensitive information, high-risk assets, and vital systems apart from the rest of the network using network segmentation.
- Provide cybersecurity training and awareness programs for students, faculty, and staff to educate them about common cyberthreats, phishing scams, social engineering attacks, and security best practices.
- Defend devices against cyberattacks by implementing endpoint security solutions like antivirus, endpoint detection and response (EDR) tools, and endpoint encryption.
- Encrypt sensitive data both at rest and in transit to prevent unauthorized access and ensure data confidentiality.
- Ensure data availability and integrity in the case of a system breakdown or security compromise by regularly backing up your data, and creating disaster recovery plans.
- Develop and test an incident response plan on a regular basis to ensure that it can effectively handle cybersecurity occurrences such as malware infections, network intrusions, and data breaches.
- Evaluate the security posture of third-party vendors, service providers, and technology partners that have access to educational systems and data.
How file integrity monitoring can help and mapping it with ManageEngine Log360

Figure 1: FIM features that benefit the educational industry
FIM can be a valuable for the educational sector in several ways:
Detecting unauthorized changes
FIM solutions continuously monitor files and directories for any unauthorized changes or modifications.
Log360 generates comprehensive reports with accurate integrity information (file creation, deletion, modification, permission changes, operation changes) in multiple formats, including CSV and PDF. You can automatically receive the reports at regular intervals through flexible report scheduling.
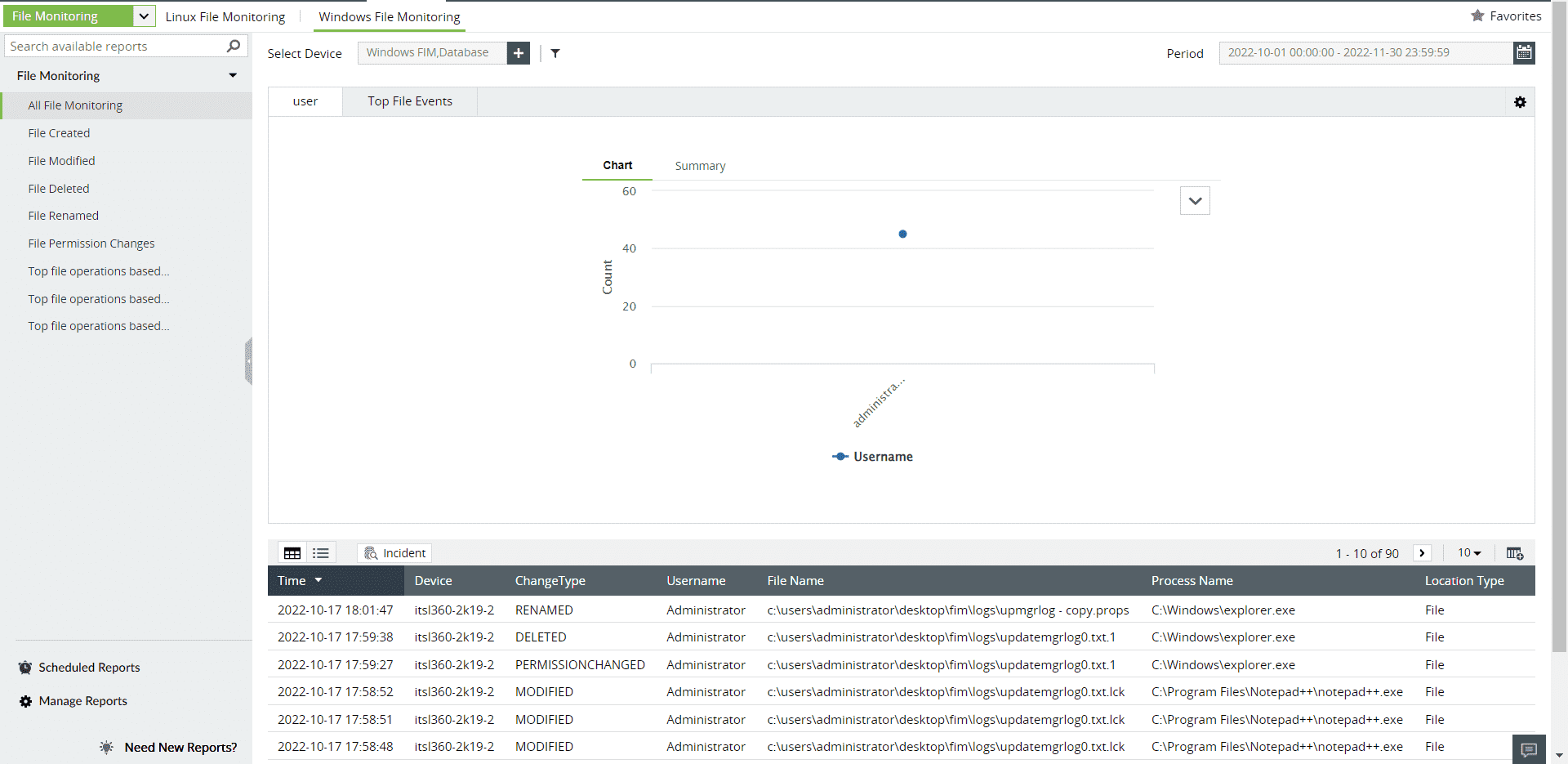
Figure 2: File monitoring reports in Log360
Preventing data breaches
FIM helps prevent data breaches by detecting and alerting administrators to suspicious activities or unauthorized access attempts in real time, enabling them to take prompt action to mitigate potential threats.
Log360 provides immediate alerts for important updates, including changes in rules or access policies for database-stored files and folders. You can accomplish this while configuring the alert criteria as per your needs. Alert criteria can also be created based on custom thresholds and user actions.

Figure 3: Creating alerts in the alerts tab of Log360
Log360 provides immediate alerts for important updates, including changes in rules or access policies for database-stored files and folders. You can accomplish this while configuring the alert criteria as per your needs. Alert criteria can also be created based on custom thresholds and user actions.
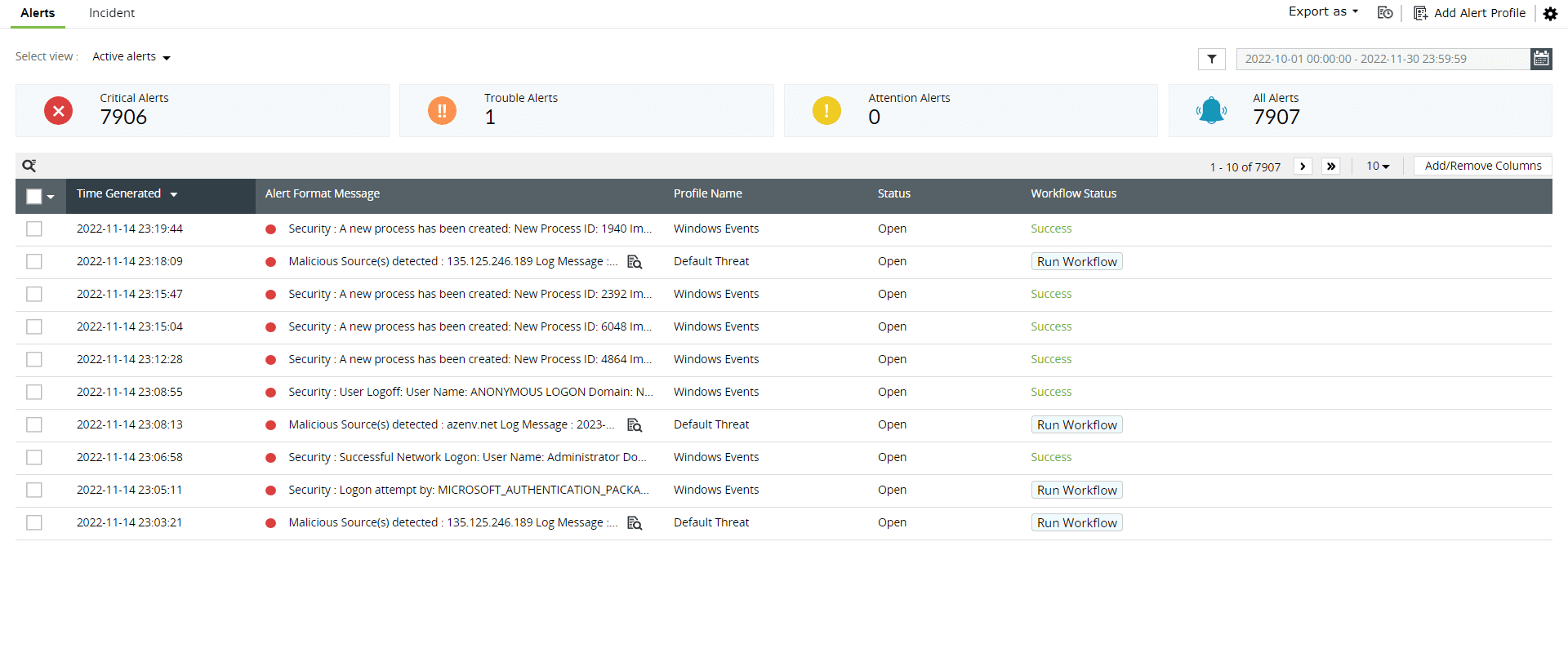
Figure 4: Alerts tab in Log360
Mitigating insider threats
FIM solutions can help mitigate insider threats by monitoring user activity and identifying anomalous behavior patterns that might indicate unauthorized or suspicious activities by students, faculty, or staff members.
Log360's dashboard's provides in-depth graphical representation of all the activities performed on the files and folders. These are represented as separate sections as shown below:
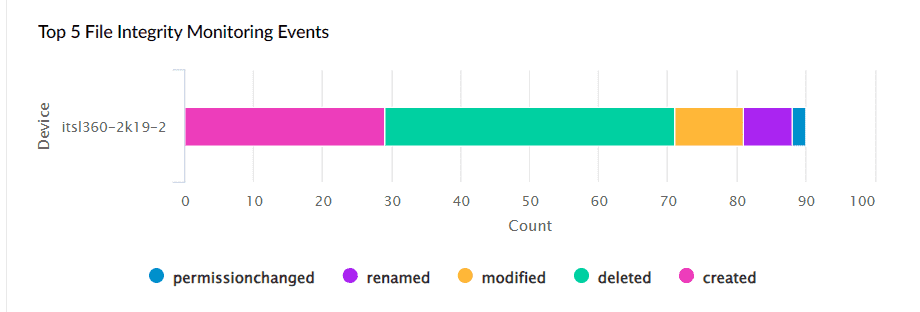
Figure 5: Dashboards in Log360
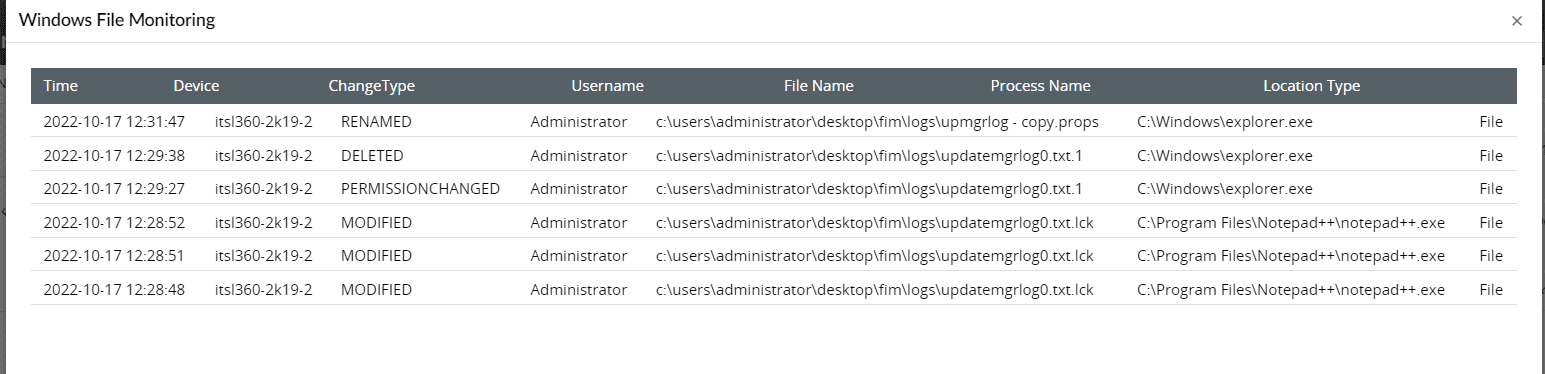
Figure 6: Dashboards in Log360
The real-time FIM dashboards of Log360 enable users to view details in graphs and charts on successful and failed file access attempts to easily spot unauthorized user activity.
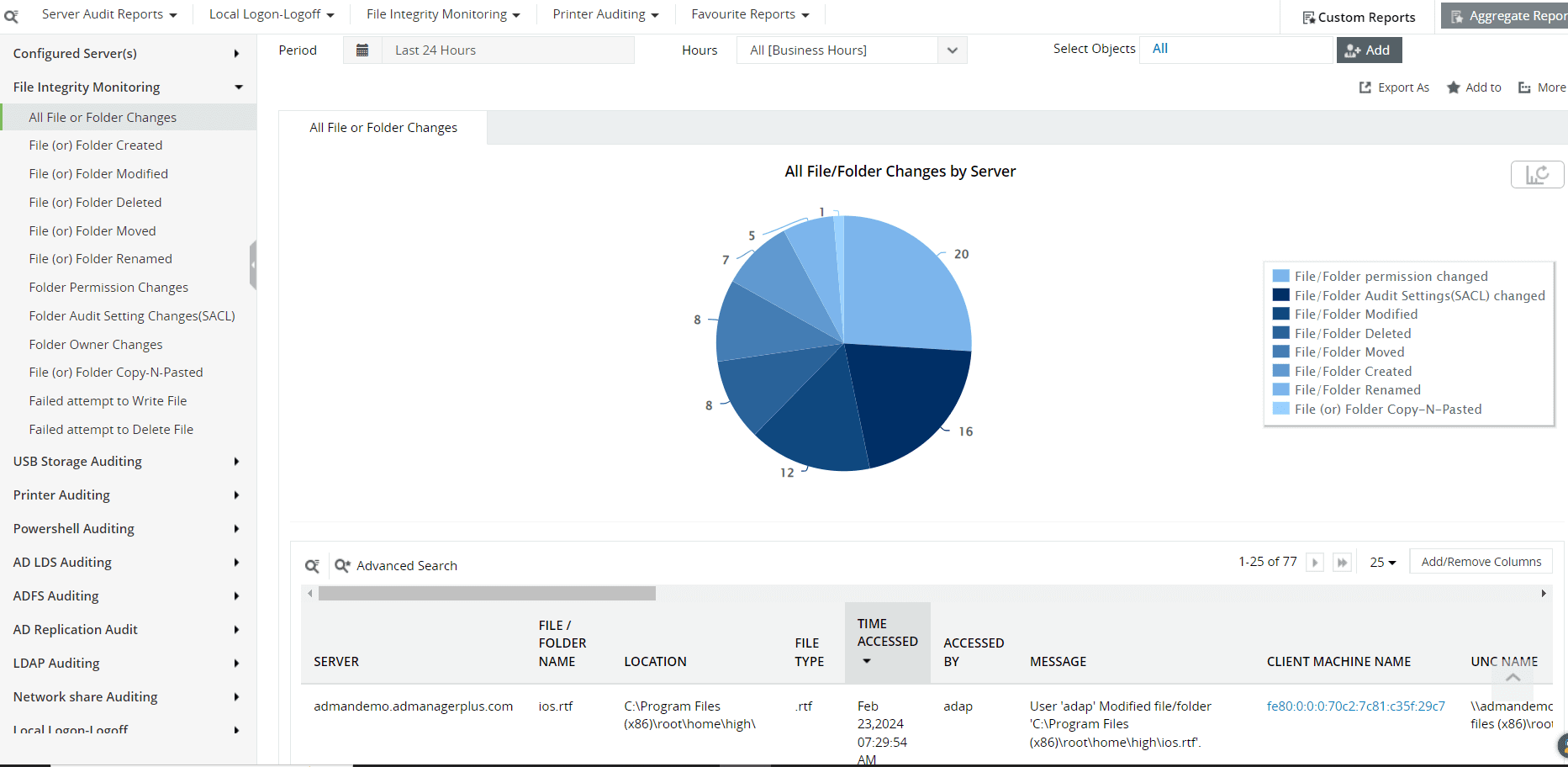
Figure 7: FIM Dashboards in Log360
Supporting incident response
In a security incident or data breach, FIM supports incident response efforts by providing forensic evidence and detailed logs of file access and changes.
A thorough audit record of every modification made to files and folders is available. All modifications have real-time answers to the "what, when, where, and how" in the correlation reports of Log360.
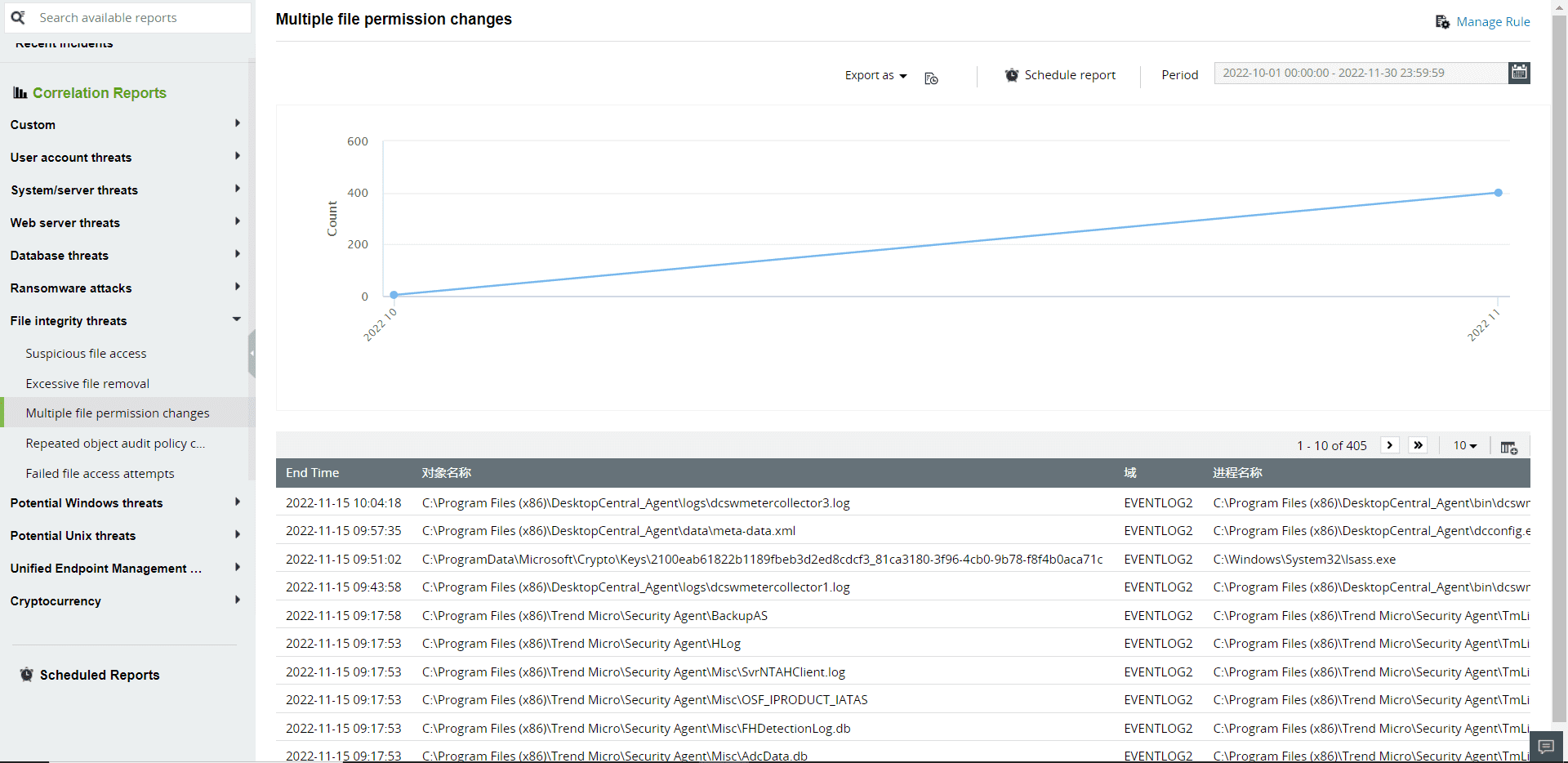
Figure 8: Correlation reports in Log360
Anomaly detection
Leverage UBA to investigate suspicious file activities by employees, such as an unusual volume of file activity.
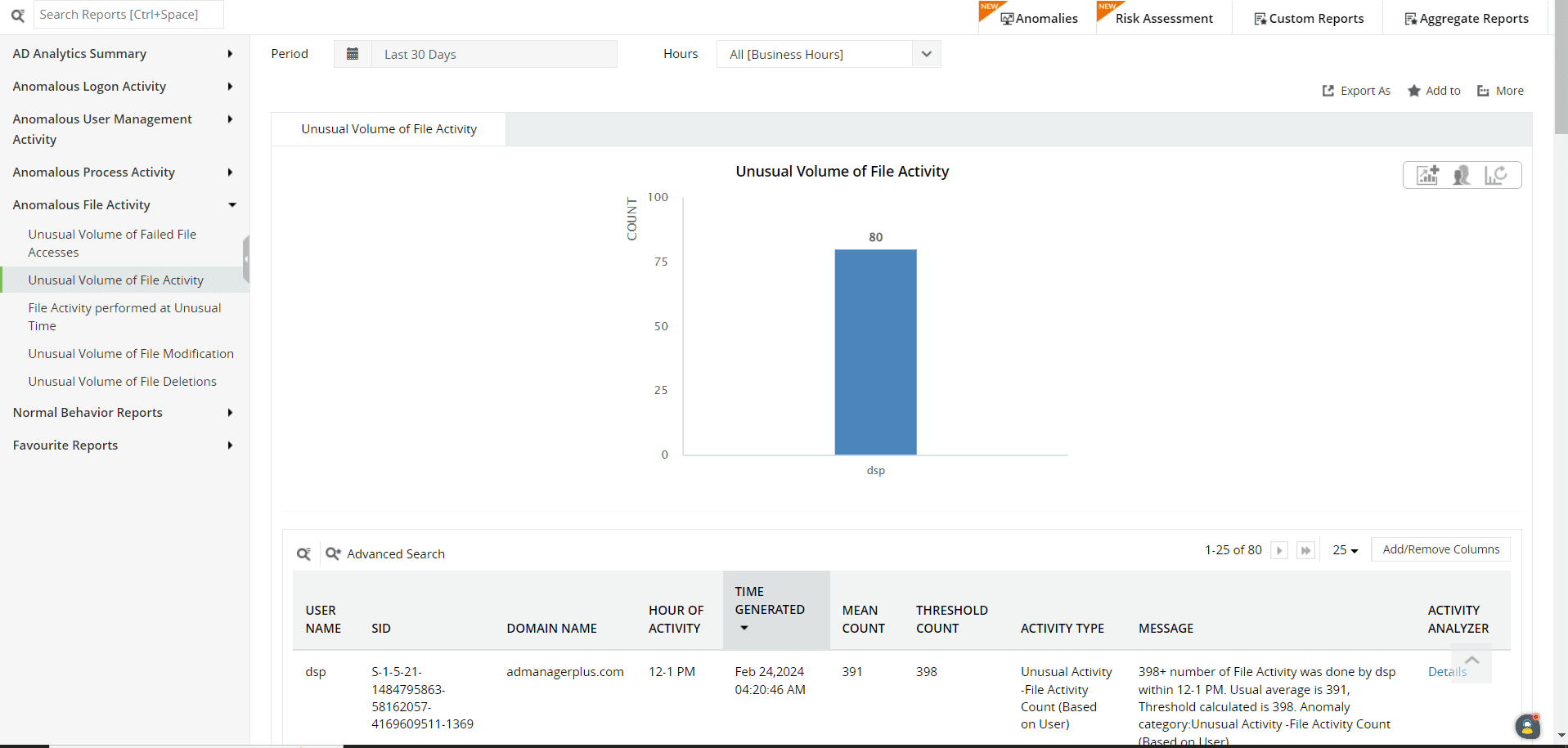
Figure 9: Analytics reports in Log360
Ensuring compliance
Assure compliance to pertinent industry standards, cybersecurity regulations, and data protection law, including the FERPA and the GDPR. To preserve student privacy and regulatory compliance, maintain documentation, conduct periodic audits, and demonstrate adherence to security standards. Educational institutions can exhibit regulatory compliance with the aid of FIM solutions, which provide comprehensive audit trails and reports on file access and modifications.
Log360 enables organizations to fulfill the requirements of the GDPR and FERPA regulatory mandate in various ways, such as:
- The file changes report helps users know about the various actions, such as created, modified, deleted, renamed, and permission changed, that are performed on the files.
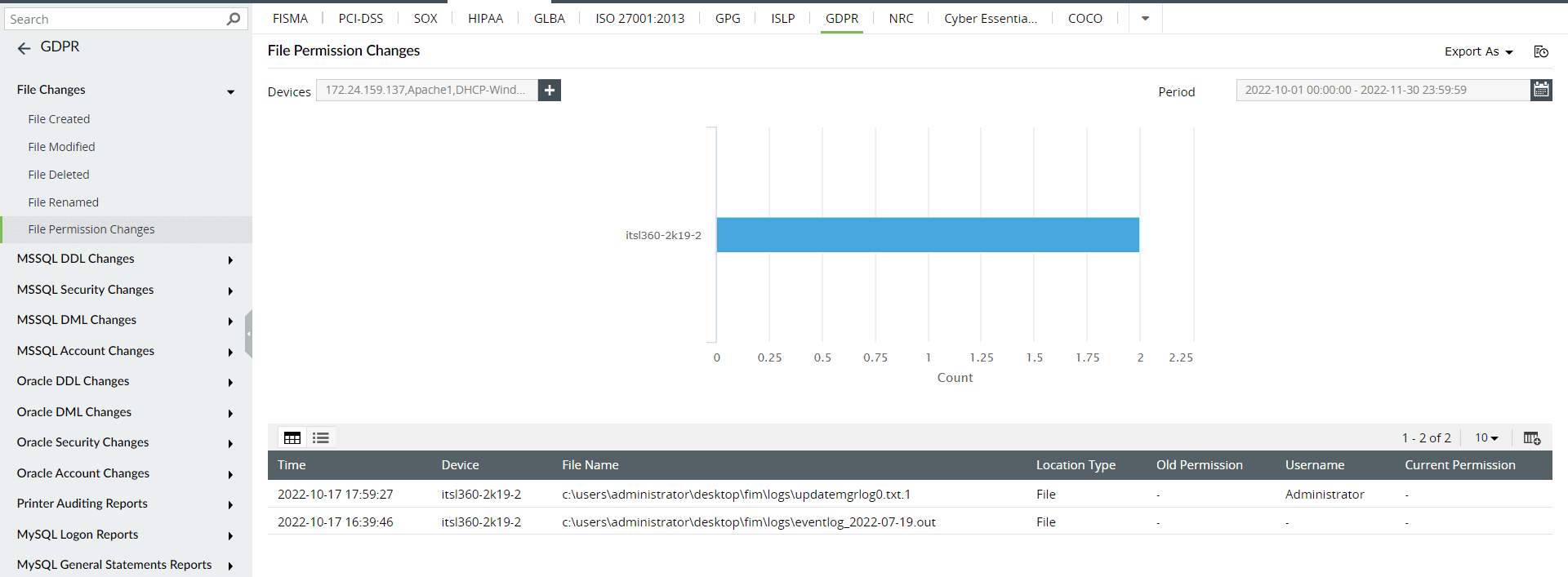
Figure 10: The GDPR File Permission Changes report in Log360
Also
- We can learn more about the users who have read the files from the File Read Access report.
- Information regarding unsuccessful attempts to read the file are made available to users through the Failed Attempt to Read file report.
- We can view the specifics of the file alterations using the Files Modified report.
- The Folder Permission Changes report shows permission modifications that have been applied to the folders.
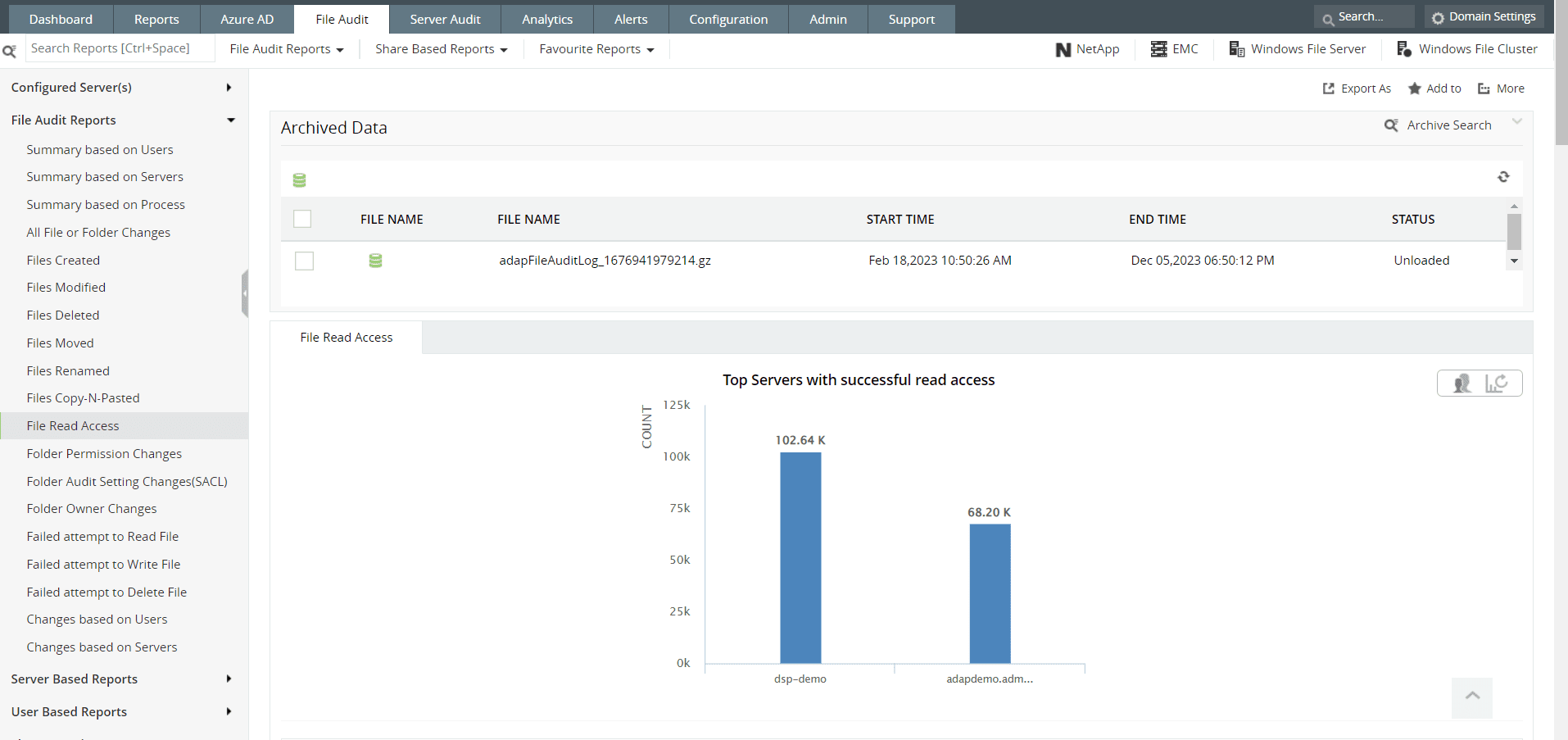
Figure 11: File Read access report in Log360
Each of these reports will include comprehensive information about the file activity and changes based on users, servers, and folder permission changes in the domain. These actions include the summary of all the file audit actions with data on files created; files deleted; files modified; files accessed; and failed attempts to read, write or delete files.
For instance, the File Read Access audit report will have all of the specifics, like server name, file/folder name, location, time the file was accessed, how the file was accessed, what kind of access was made, client machine name, client domain, client IP address, and much more.

Figure 12: File Read Access report in Log360
All things considered, FIM can improve educational institutions' cybersecurity posture by giving them visibility into file system activity, identifying unauthorized changes, and assisting them in upholding data integrity, confidentiality, and regulatory compliance.
Ready for the next step?
Are you looking for ways to protect your organization's sensitive information? Sign up for a personalized demo of ManageEngine Log360, a comprehensive SIEM solution that helps you detect, prioritize, investigate, and respond to security threats.



