Did you know that, according to HealthITSecurity, as of the first week of March, 116 healthcare data breaches had been reported to the HHS Office of Civil Rights (OCR) in 2024, affecting over 13 million people?
Why the healthcare industry receives the most cyberattacks
- The large amount of valuable data available in the healthcare sector—such as electronic health records (EHRs), personal identifiable information (PII), financial information, and intellectual property—can be used for identity theft, insurance fraud, extortion, and other illegal activities.
- Stolen medical records can be sold for a good pricein the black market.
- Many healthcare organizations continue to rely on outdated security practices and legacy systems, which may not provide strong security controls or defenses against contemporary cyberthreats.
- Due to financial limitations, a large number of interconnected systems, and third-party apps, many healthcare organizations have little resources allocated to IT security. This may lead to a weak security posture due to insufficient resources for configuration and maintenance, and a lack of automations in place.
How to stop cyberattacks targeting the healthcare sector
- Allocate adequate resources towards constructing resilient cybersecurity infrastructure, encompassing intrusion detection systems, firewalls, encryption protocols, and regular security audits.
- Healthcare staff must have thorough training on cybersecurity best practices.
- Healthcare organizations should adhere to established security standards and regulations such as the Health Insurance Portability and Accountability Act (HIPAA).
- Periodically update software and apply security patches to resolve vulnerabilities and reduce the possibility of cyberattacks taking advantage of known deficiencies.
- Encrypt sensitive data and put strong access controls in place to ensure patient records and other private information is protected from unwarranted access.
- Implement sophisticated threat detection technologies, such artificial intelligence and machine learning, to facilitate the prompt identification and mitigation of cyberthreats, augmenting the overall cybersecurity posture.
How file integrity monitoring can help protect your sensitive files

Figure 1: FIM features that benefit the healthcare industry
Detection of insider threats
Healthcare businesses are particularly vulnerable to insider threats. By keeping an eye on employee actions and identifying any suspicious behavior, such as unauthorized access to important files or any other information, file integrity monitoring (FIM) can help in the identification of insider threats.
ManageEngine Log360's dashboards provides in-depth graphical representation of all the activities performed on files and folders. These are represented as separate sections as shown below:
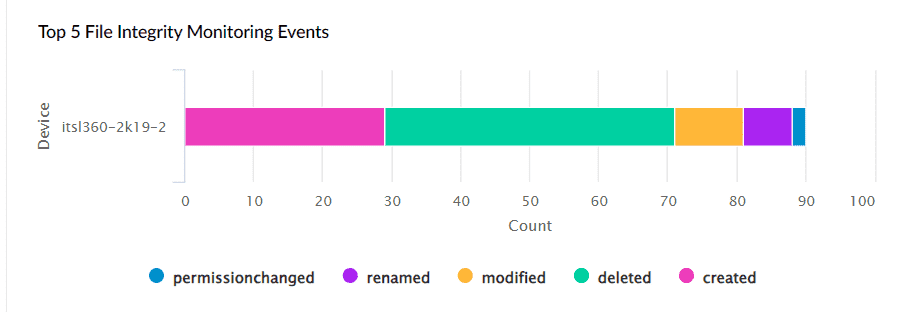
Figure 2: Dashboards in Log360
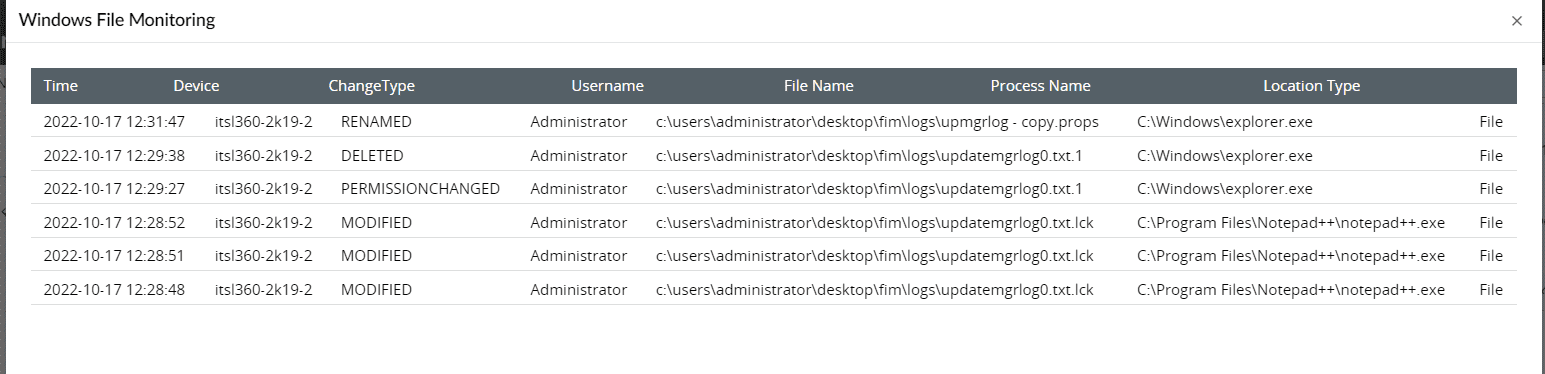
Figure 3: Reports in Log360
Real-time FIM dashboards in Log360 let users view details in graphs and charts on successful and failed file access attempts to spot unauthorized user activity easily.
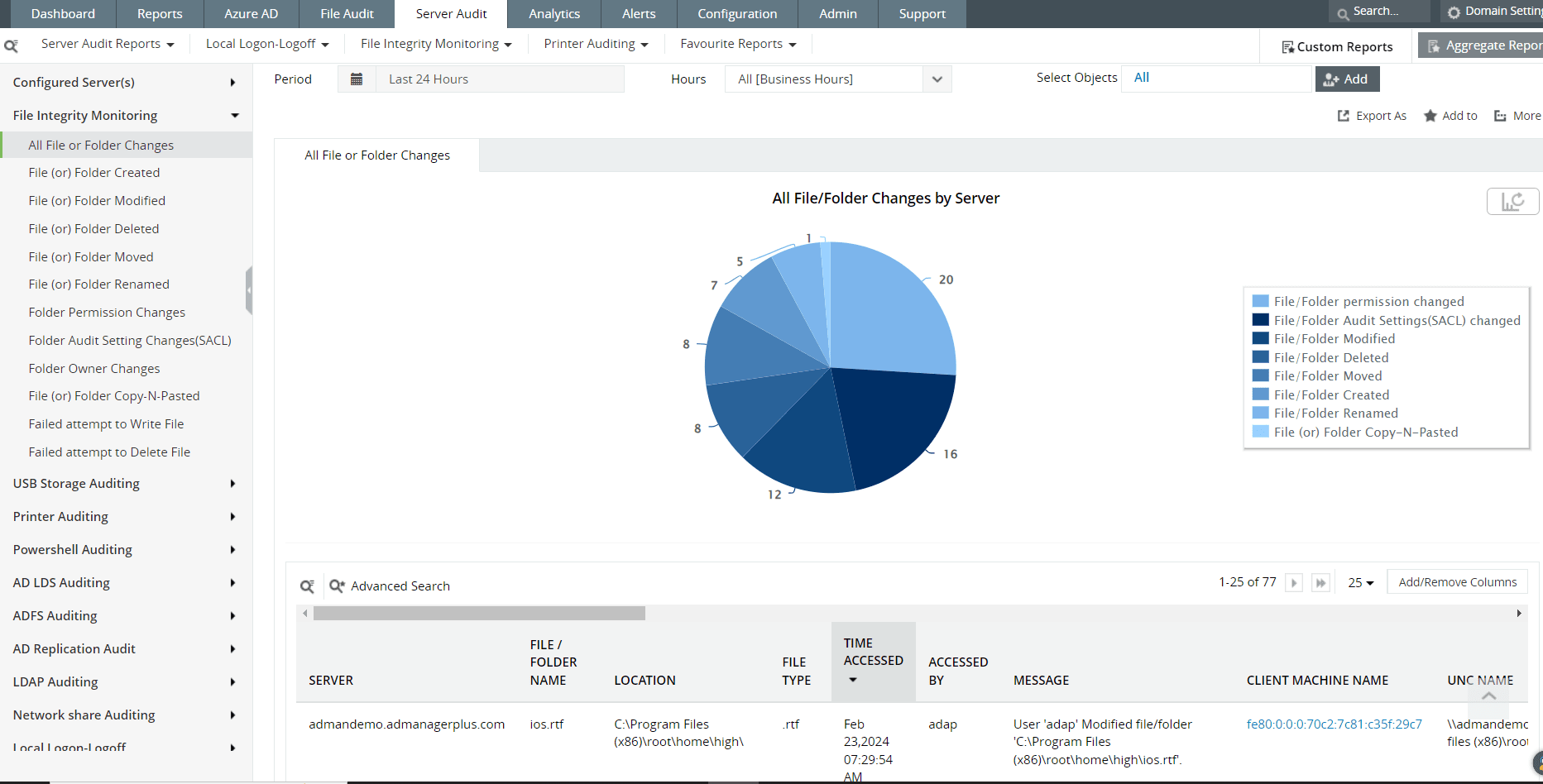
Figure 4: FIM dashboards in Log360
Compliance with regulations
Healthcare organizations must comply with stringent regulations like HIPAA. A FIM solution like Log360 offers access controls to ensure employees can't access patient records, administrative data, or EHRs without the required permissions.
Log360 helps organizations fulfill HIPAA requirements with its compliance reports. These reports containall of the details of the files created, modified, deleted, and renamed; files that had permissions changed; and granular details of what, when, where, and how the file activities occurred.
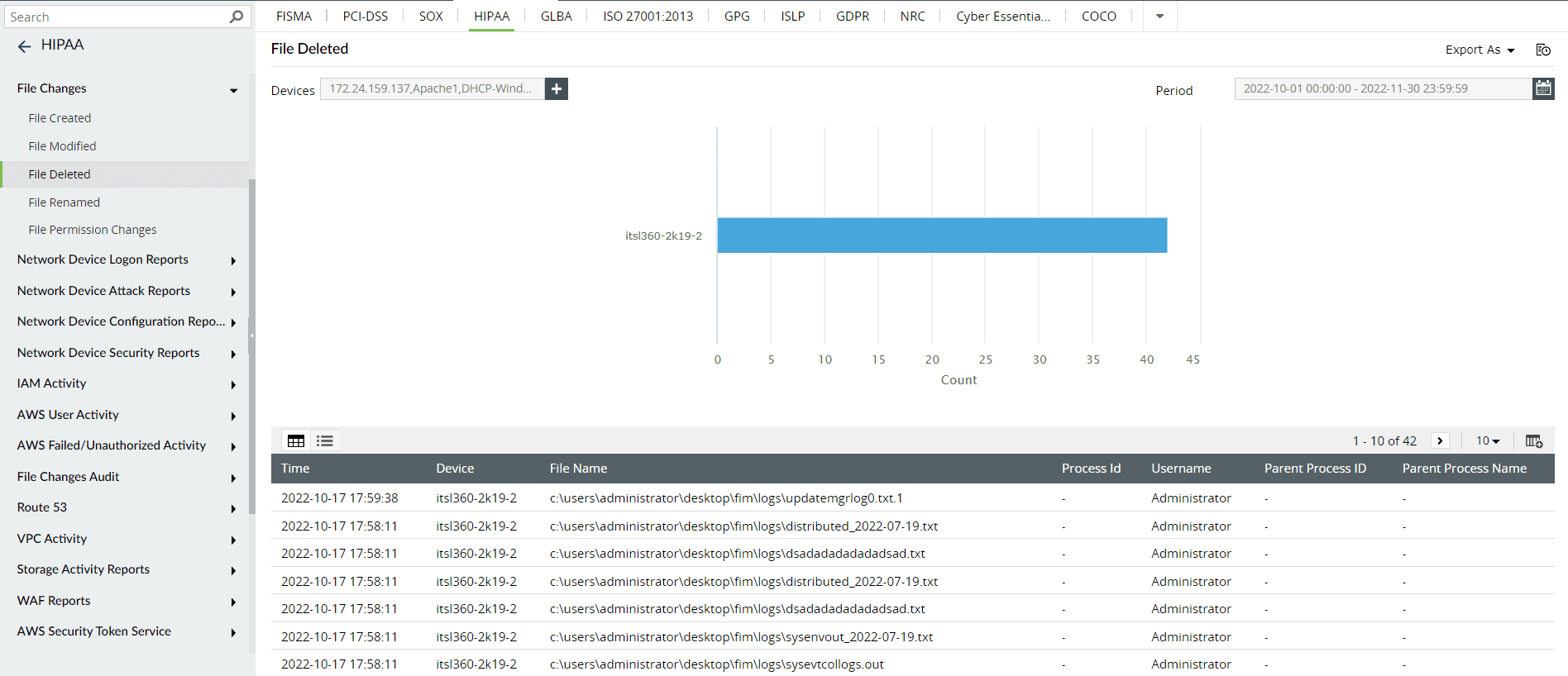
Figure 5: HIPAA: File Deleted report in Log360
Preventing data breaches
Sensitive patient data can be exposed following a data breach, which may have negative financial, reputational, and legal impacts. FIM helps stop data breaches by spotting unauthorized access attempts or suspicious file changes, so you can take action to stop them before they become serious security issues.
Log360 provides immediate alerts for important updates, including change in rules or access policies for database-stored files and folders. You can do this while configuring the alert criteria as per your needs. Alert criteria can also be created based on custom thresholds and user actions.
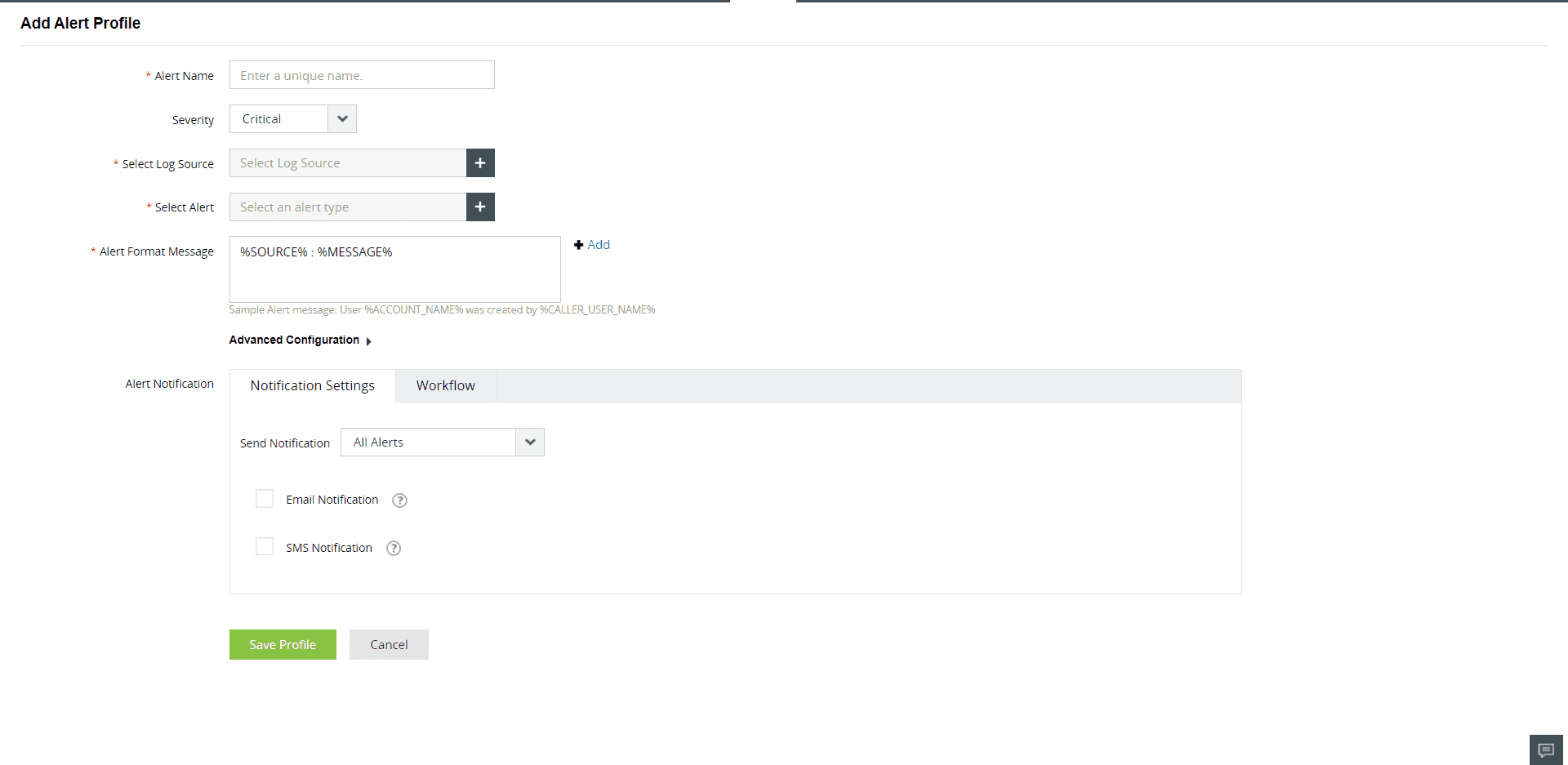
Figure 6: Creating alerts in the alerts tab of Log360
Obtain instant alerts on critical changes that take place in your files and folders.
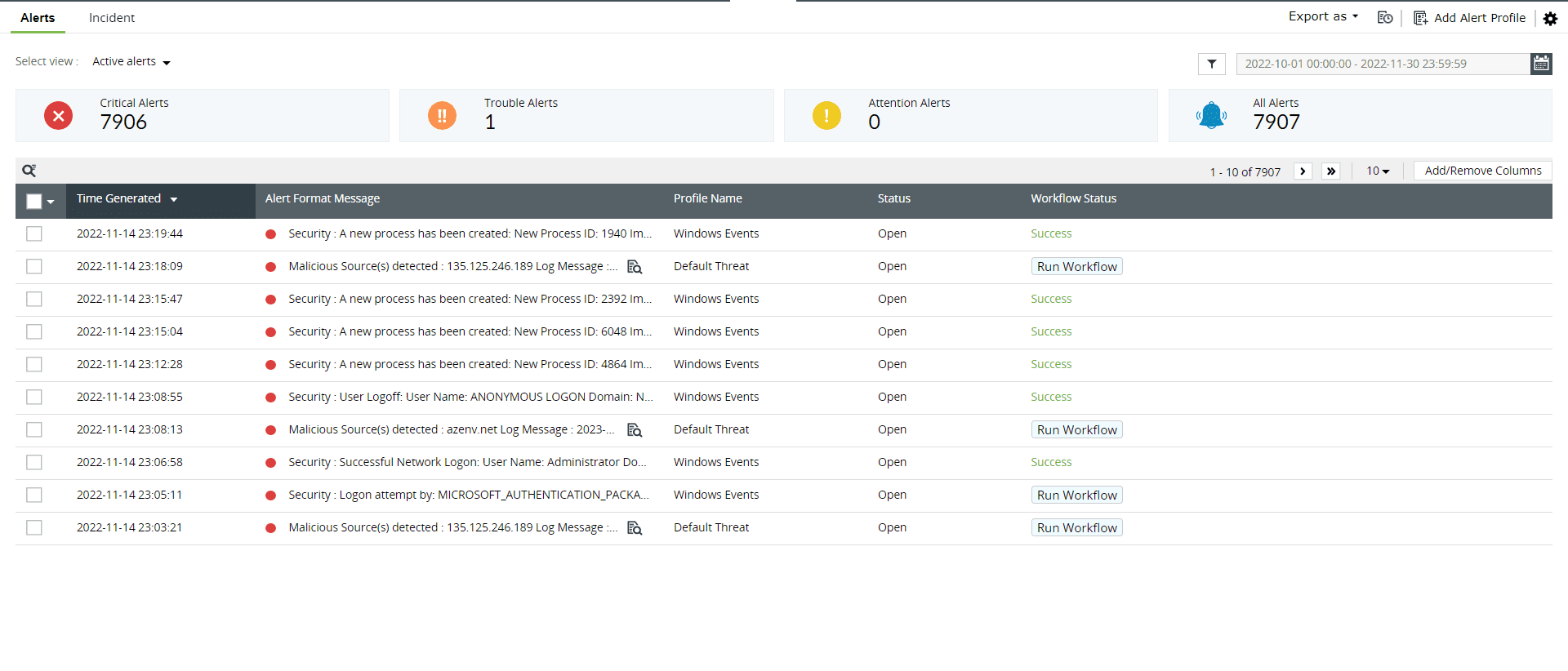
Figure 7: Alerts tab in Log360
Identifying unauthorized access or modification
Unauthorized access to patient information or manipulation of medical data can result in data theft.
Log360 generates thorough reports with accurate integrity information (file creation, deletion, and modification; permission changes; operation changes) in multiple formats, including CSV and PDF. You can automatically receive the reports at regular intervals with the help of flexible report scheduling.
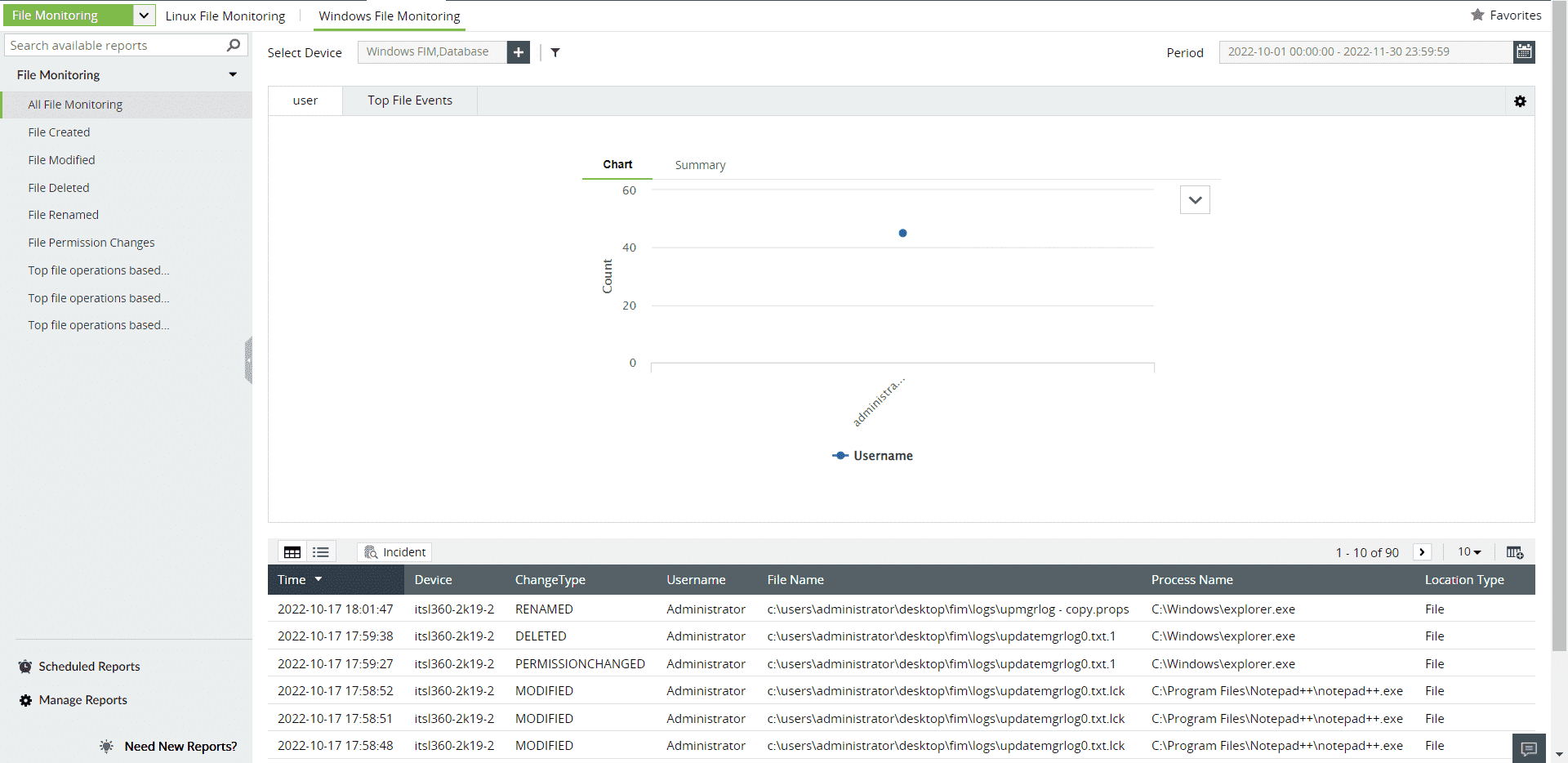
Figure 8: File monitoring reports in Log360
The File Audit tab will let you view reports that are specific to a file audit action.
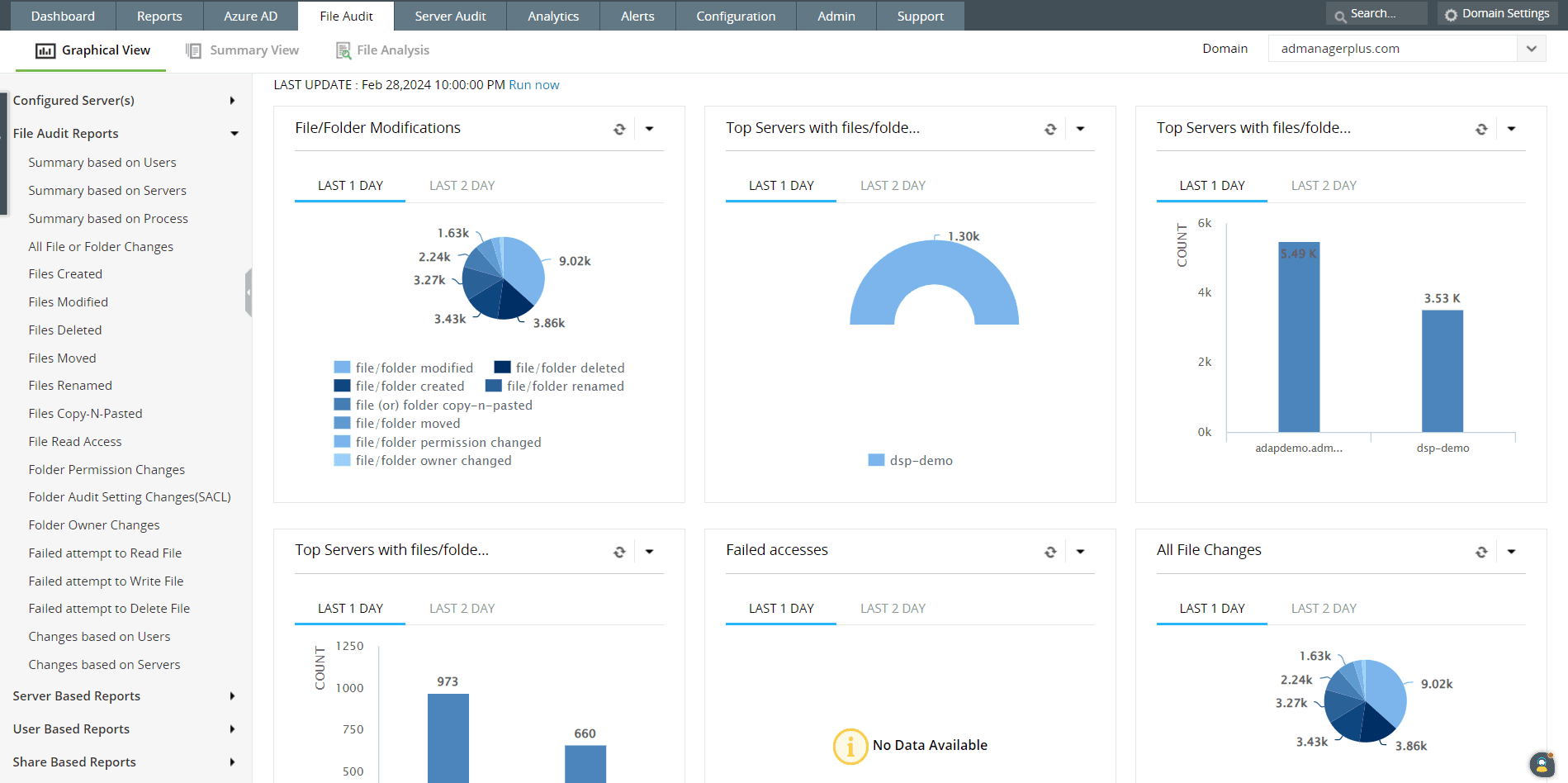
Figure 9: File audit reports in Log360
Protection of EHRs
FIM keeps track of modifications to files and system configurations within the systems that store EHRs, helping to guarantee the confidentiality and integrity of important documents.
The analytics report will let you investigate suspicious file activities by admins, such as an unusual volume of file activity.
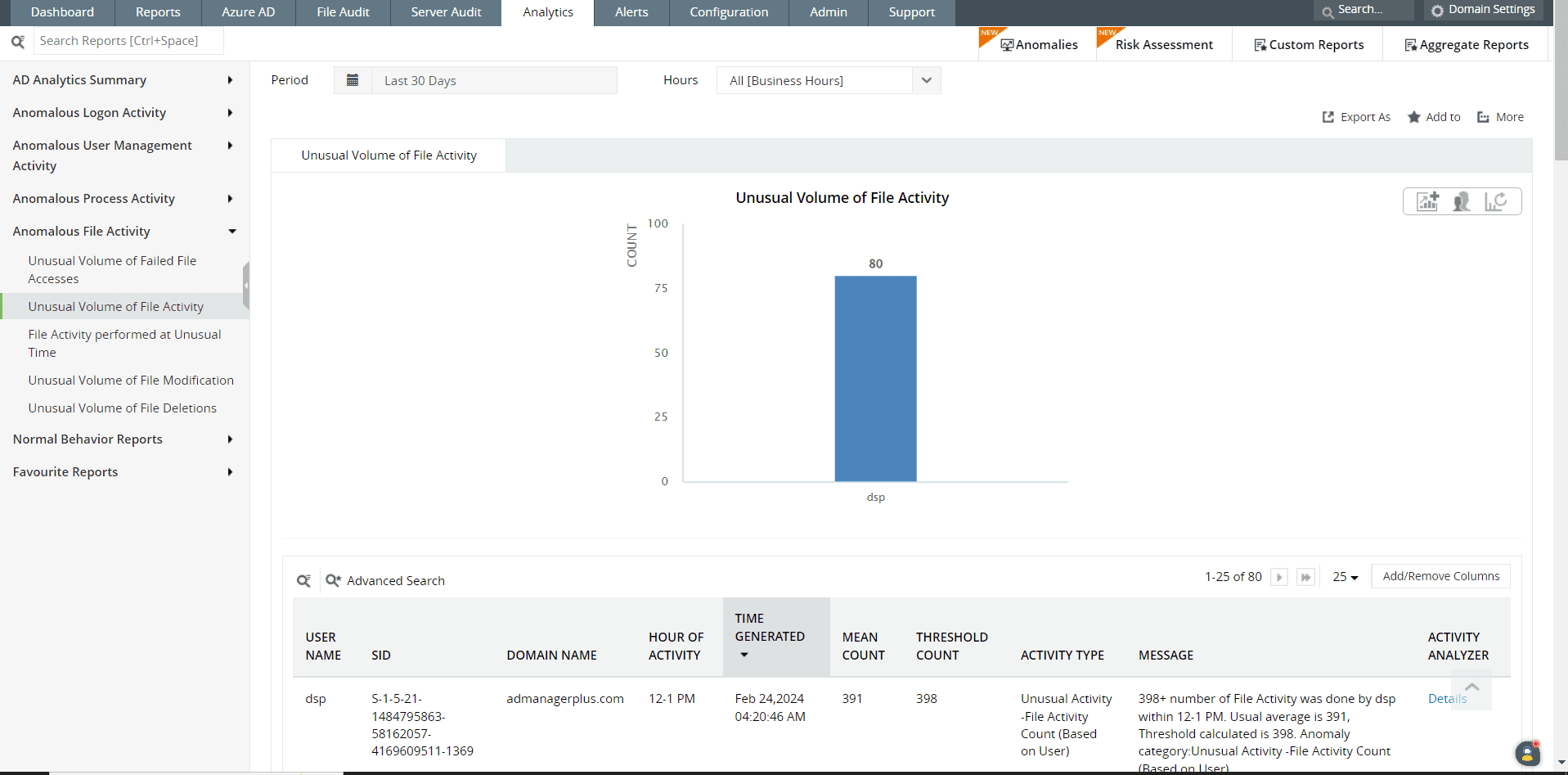
Figure 10: Analytics reports in Log360
Continuous monitoring and auditing
Healthcare organizations can track changes to files and configurations in real time with the help of FIM, which offers continuous monitoring and auditing capabilities. This proactive strategy helps in identifying compliance problems and security vulnerabilities before malicious actors or regulatory authorities can take advantage of them.
View thorough audit records of every modification made to files and folders. Log360's correlation reports provide real-time answers to the what, when, where, and how of file modifications.
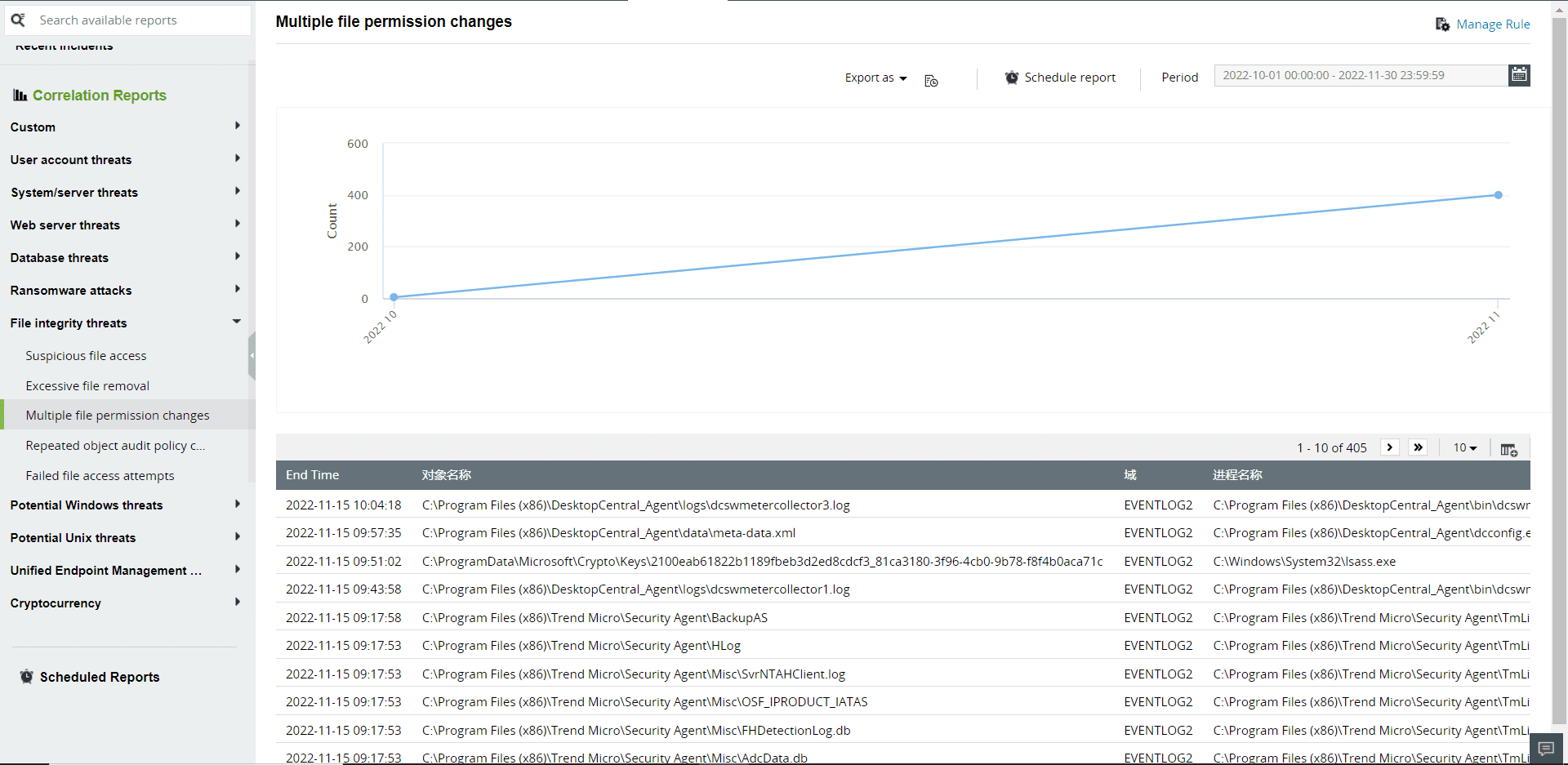
Figure 11: Correlation reports to detect file integrity threats in Log360
All things considered, FIM is essential to safeguard confidential patient information, comply with regulations, tighten security, and eliminate unwanted access.
Ready for the next step?
Are you looking for ways in which you can protect your organization's sensitive information from being misused? Sign up for a personalized demo of ManageEngine Log360, a comprehensive SIEM solution that can help you detect, prioritize, investigate, and respond to security threats.



