The global growth of cloud infrastructure has been explosive. The pandemic that promoted remote working models has accelerated the adoption of cloud infrastructure platforms and services exponentially. Migration to the cloud landscape has provided organizations with data storage, convenience of access, a reduction in infrastructure costs, and efficiency in team collaborations, among other benefits.
This dynamic work environment has redefined access parameters and boundaries, and hence requires effective security solutions such as a cloud access security broker (CASB) to mitigate security threats. A CASB unifies security measures across the cloud providing visibility to make detection, management, and enforcement possible, all from a single security platform. While the use of a CASB in cloud security measures is on an upward curve, industry insights predict more rapid growth due to modernizing and adapting.
CASB deployment to address gaps in cloud security
CASB ensures an organization achieves data visibility into its cloud applications. The rate at which data is proliferating in the cloud is exponential, so much so that organizations are challenged with keeping up. This necessitates the use of cloud security solutions to adapt to the evolving threat landscape.
Security tools, such as SIEM and DLP, have been constantly updated and developed for organizations to mitigate threats and protect their data. However, preventing malicious advanced data threats against privileged users demands a sophisticated tool that could work as a standalone or be integrated in the existing cloud security premise. CASB evolved from being a specific solution to curb shadow IT concerns to providing multifaceted cloud security functions.
There are four core functionalities of CASB that can explain how it promotes cloud security in an organization's cloud. Simply put, these functionalities can help you understand the importance of CASB in cloud security. Gartner has termed these functionalities as "pillars", and the four pillars of CASB are as follows:
Visibility
From an IT perspective, it is important to know who is using cloud services and how the data is being used. It is no surprise that organizations with many employees access numerous applications across multiple cloud environments, not all of them approved by the IT department. Such applications which are neither explicitly approved nor disapproved by the IT team are called as shadow IT applications. When cloud use is beyond the view of IT, official data is no longer protected by a company's risk and security mitigation policies. In 2022, Gartner predicted that "By 2027, 75% of employees will acquire, modify or create technology outside IT’s visibility – up from 41% in 2022." In one of their earlier studies, Gartner reported that 30 - 40% of IT expenses in enterprises can be attributed to shadow IT.
With little to no knowledge about which applications are in use, by whom, and for what, IT teams are forced to confront the problem of shadow IT, and its dire consequences. Shadow IT significantly reduces data visibility. A CASB solution provides visibility into a company's cloud usage which ultimately helps safeguard users and data. For example, cloud discovery analysis provides insights through risk assessment so professionals can decide the appropriate level of access to grant different users. A CASB-integrated SIEM solution like ManageEngine Log360 provides comprehensive visibility into your employee's cloud usage, including the use of shadow applications. It provides much-needed insights into the category of the app and its reputation, as shown in Figure 1. With these insights, the IT team can determine whether to sanction the applications for official use or ban them instead.
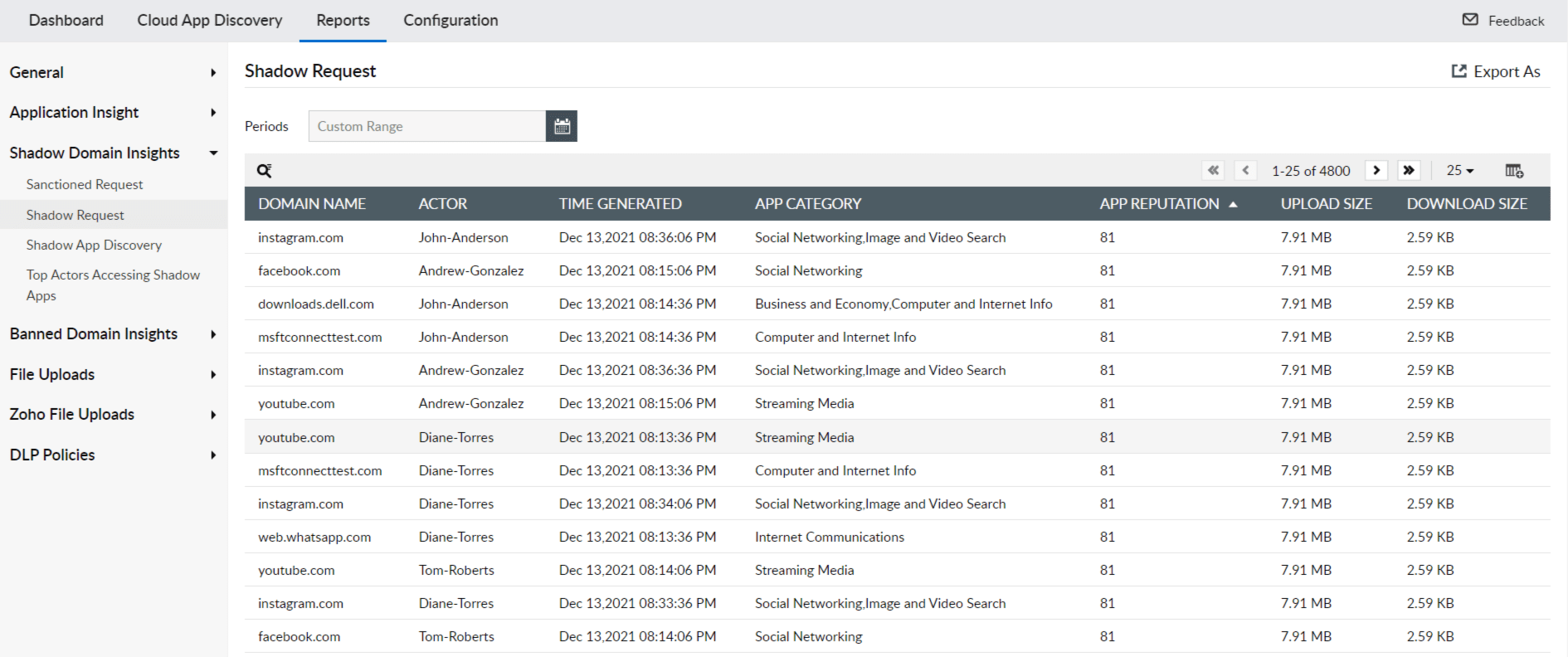
Figure 1: Log360 reports providing insights into shadow application requests
Compliance
Businesses must comply with regulations that govern data privacy and security, irrespective of whether any or all of their systems and data storage is outsourced to the cloud. CASBs help organizations meet cloud compliance requirements for regulations like HIPAA, ISO 27001, PCI DSS, and more. This can be accomplished, for example, by enforcing policies that ensure only authorized personnel gain access to sensitive data. In addition, CASB can detect high areas of risk when it comes to compliance and provide help to the IT team to address and resolve them. Log360 offers comprehensive, audit-ready reports for various compliance standards such as PCI DSS, HIPAA, GDPR, SOX, FISMA, GLBA, and more, as shown in Figure 2.
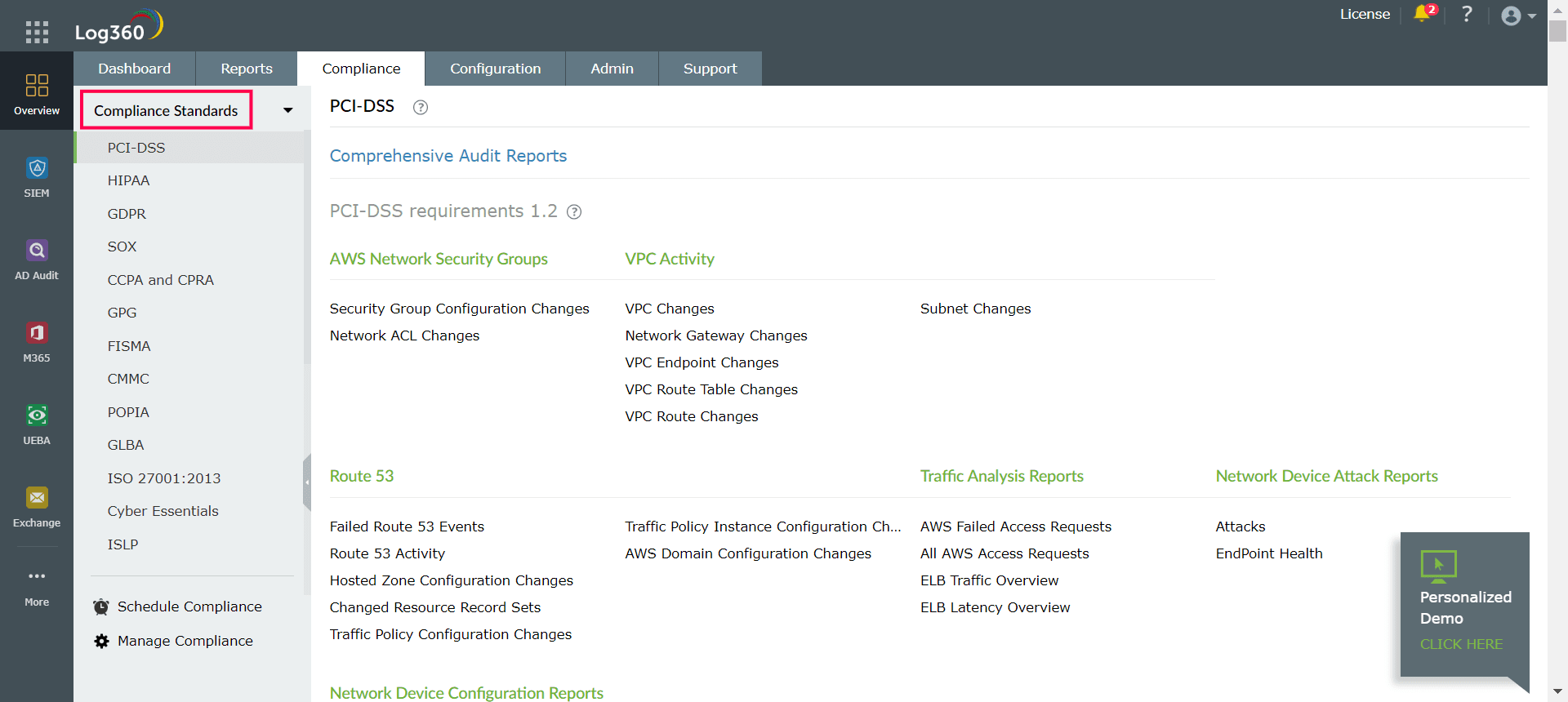
Figure 2: Comprehensive audit reports offered by Log360 for various compliance standards
Threat protection
CASB is able to create a comprehensive view of user patterns and behaviors to help detect anomalous user behavior. Attacker or insider actions, malicious or unintentional, can be involved in data leaks or confidential data theft that greatly affects an organization. CASB using user and entity behavior analytics technology mitigates the risk of stolen data. On the other hand, CASB is able to make use of other capabilities, such as adaptive access control, malware analysis, prioritized analysis, and threat intelligence, specifically against malware when the threats appear from external cloud services and applications. Log360 can monitor all file uploads made by users and hence prevent data exfiltration attacks, as shown in Figure 3.
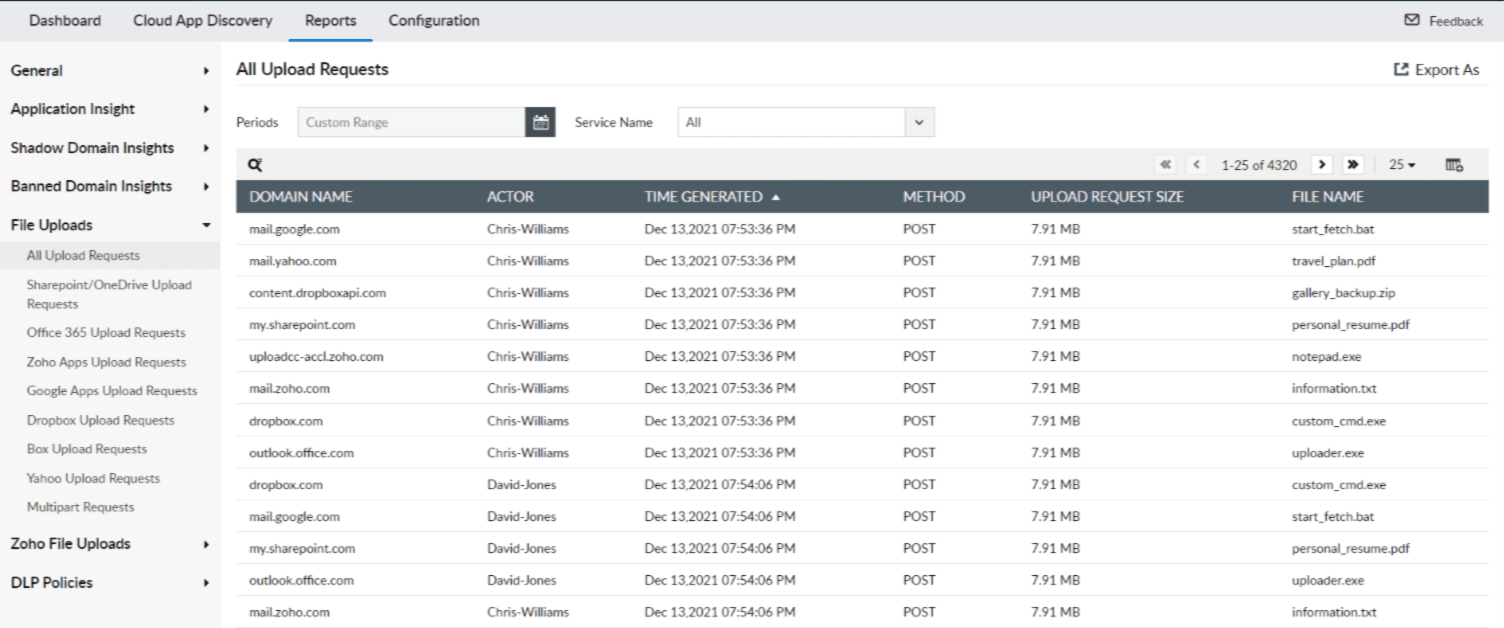
Figure 3: Log360 reports offering insights into all file uploads and the users uploading them.
Data security
The convenience of team collaboration and efficiency over distance brings with it a potential heavy cost for businesses to pay if cloud usage is not configured and protected. DLP solutions are designed to safeguard data, however they don't provide much support for cloud scenarios. DLP provides considerably less coverage for cloud security than a sophisticated CASB solution.
CASB promotes data security in the cloud through:
- Access and collaboration control
- Information rights management
- Tokenization
- Encryption
Collectively, a combination of on-premises DLP solutions and sophisticated CASB provides visibility into how sensitive information travels, from, to, and within the cloud. Log360 provides data visibility across your on-prem and cloud environments. It also helps you configure and implement cloud DLP policies that can help you improve your data security.
CASB in cloud landscape
Cloud security is clearly a necessity rather than a luxury. As data production, storage, and sharing increases, organizations have a heightened need to invest in competent cloud security solutions. CASB helps ensure security functions are easier for cloud infrastructure platforms and services, and saves time and resources so they can be dedicated to other important functions in an organization. Due to its enhanced data visibility, support for cloud compliance regulations, threat detection and protection features, and promotion of data security strategies, CASB is your best go-to solution for protecting your users, network, and data. Sign up for a personalized demo of Log360, a CASB-integrated SIEM solution, to evaluate how it can fortify your organization's cloud security.



