What is malware?
Malware is a portmanteau of malicious and software. It refers to a variety of harmful programs designed to infiltrate, damage, or disable computers and computer systems. It includes a variety of harmful programs—like viruses, worms, Trojan horses, spyware, ransomware, and adware—which perform unauthorized actions on affected systems.
This guide offers an in-depth exploration of the types, impact, and evolution of malware, as well as strategies for prevention and mitigation.
The evolution of malware
In the early days of computing, malware was born out of curiosity and mischief. However, as technology advanced, so did the intentions behind these programs, shifting from experimental pranks to tools for digital crime and espionage. We trace this evolution with examples such as the playful yet disruptive Morris worm of the late 1980s to the more sinister WannaCry ransomware that caused global havoc in 2017. As technology has advanced, so too has the motives behind these programs, evolving from playful experiments to a shadowy underground economy.
Objectives behind a malware attack
Data theft
Malicious actors often target sensitive data such as personal information, financial records, and intellectual property. The objective here is to steal valuable information for various purposes, including identity theft, financial fraud, or selling the data on the dark web.
Financial gain
Many malware attacks are driven by the goal of financial profit. Cybercriminals may deploy ransomware to extort money from individuals or organizations, or they may engage in activities such as banking Trojans to steal financial credentials and conduct fraudulent transactions.
Disruption of operations
Some malware attacks aim to disrupt the normal operations of organizations or critical infrastructure. This disruption can be achieved through tactics such as deploying ransomware to encrypt files or launching distributed denial-of-service (DDoS) attacks to overwhelm networks.
Espionage
State-sponsored or corporate espionage is a significant objective of certain malware attacks. Malicious actors may seek to infiltrate systems to gather intelligence, trade secrets, or other valuable information for competitive advantage or political purposes.
Types of malware attacks
| Malware attacks | Characteristics | Behavior |
|---|---|---|
| 1. Viruses | Viruses are self-replicating malicious code that attach themselves to legitimate programs, spreading uncontrollably when these programs are executed. | They can corrupt or delete files and may spread through infected email attachments or removable media. |
| 2. Worms | Worms are standalone programs that replicate and spread independently, often exploiting vulnerabilities in networked systems. | They can congest networks, consume bandwidth, and may carry payloads for additional malicious activities. |
| 3. Trojans | Trojans masquerades themselves as legitimate applications to deceive users into installing them. | Once inside a system, Trojans can create backdoors for attackers, facilitating unauthorized access and data theft. |
| 4. Ransomware | Ransomware encrypts files, rendering them inaccessible until a ransom is paid. | It often spreads through malicious email attachments or compromised websites and can have severe financial and operational consequences. |
| 5. Spyware | Spyware secretly monitors user activities, capturing sensitive information without the user's knowledge. | It can track keystrokes, capture login credentials, and compromise personal privacy. |
| 6. Adware | Adware displays unwanted advertisements, often bundled with legitimate software. | While not inherently malicious, it can compromise system performance and user experience. |
| 7. Rootkits | Rootkits conceal the presence of malicious software by modifying system functions. | They are often used to maintain unauthorized access and can be challenging to detect. |
| 8. Botnets | Botnets are a network or cluster of machines infected with malware that hackers can control to perform attacks. The botnet's strength depends on the number of compromised machines, with attackers gaining remote control through a command and control model. | They are often used for large-scale cyberattacks, such as distributed denial of service (DDoS) attacks. |
| 9. Fileless malware | Fileless malware operates in a system's memory, leaving little to no trace on the disk. | It evades traditional antivirus solutions and relies on exploiting vulnerabilities in system processes. |
| 10. Cryptojacking | Cryptojacking involves using a victim's computing resources to mine cryptocurrency without their consent. | It can slow down system performance and increase energy consumption. |
| 11. Keylogger | Keyloggers are designed to record and monitor keystrokes on a computer or mobile device. | They capture sensitive information—such as usernames, passwords, credit card numbers, and other personal data—by logging the keys pressed by the user. |
| 12. Backdoors | A backdoor is a hidden entry point in a computer system that allows unauthorized access and control. | Once installed, a backdoor enables attackers to bypass normal authentication and gain ongoing, remote access to the system. They can be used for various malicious activities, including data theft, surveillance, or launching further attacks. |
Malware attack examples
The CovidLock malware exemplifies cybercriminals capitalizing on global crises. Emerging during the COVID-19 pandemic, it disguised itself as a legitimate tracking app. Though the app claims to offer heat map visuals and other statistical data about COVID-19, upon installation, it locks users' phones and demands ransom. Despite authorities breaking the encryption, CovidLock serves as a poignant reminder of the unexpected nature of cyber threats.
In a notable ransomware incident, the Colonial Pipeline attack by the DarkSide group in May 2021 targeted a major US fuel pipeline. The shutdown caused widespread fuel shortages and a $4.4 million ransom payment. This event underscored the potential for ransomware to disrupt critical infrastructure, prompting a renewed focus on cybersecurity measures.
Defense strategies against malware attacks
Incident response planning
Swiftly identify and contain incidents through robust monitoring, network segmentation, and disabling compromised accounts. Eradicate malware by removing it, patching vulnerabilities, and analyzing attack vectors. Finally, recover by restoring systems from clean backups and updating response procedures based on insights.
Antivirus and anti-malware measures
Ensure robust defense with regular updates to antivirus software, keeping definitions and software current. Implement behavioral analysis for early detection of unknown threats, and fortify individual devices with endpoint security solutions.
Network security measures
Secure your network with well-configured firewalls, intrusion detection prevention systems, and multiple layers of defense in your network infrastructure.
Data backup and recovery strategies
Protect against data loss by implementing regular, automated backups stored in secure, offline locations. Facilitate quick recovery with snapshot and image-based backup solutions.
Continuous monitoring and threat intelligence
Implement security information and event management (SIEM) for real-time monitoring and response. Enhance defenses by integrating threat intelligence feeds, ensuring awareness of the latest threats for proactive adjustments.
Regular security audits and assessments
Maintain a proactive security stance through regular vulnerability assessments, prioritizing and promptly addressing weaknesses. Conduct penetration testing to simulate real-world attacks and identify security gaps.
Malware mitigation and remediation
Employ reputable antivirus software capable of scanning and eliminating malicious code to remove malware from your network. Isolate infected devices to prevent the malware from spreading and conduct thorough system scans. Additionally, consider restoring affected systems from clean backups to ensure a secure and malware-free environment.
How does Log360 detect malware?
While deploying anti-malware is crucial, it may not provide a comprehensive network security overview. Anti-malware often overlooks factors such as account compromise preceding seemingly legitimate software installations. ManageEngine Log360—a SIEM solution with robust event log correlation and analysis capabilities—is essential for proactive defense against malware attacks.
Behavioral analysis:
Log360 analyzes the behavior of activities across the network with its UEBA add-on, identifying deviations from normal patterns that may indicate malware presence. This includes unusual file access, system interactions, or communication patterns.
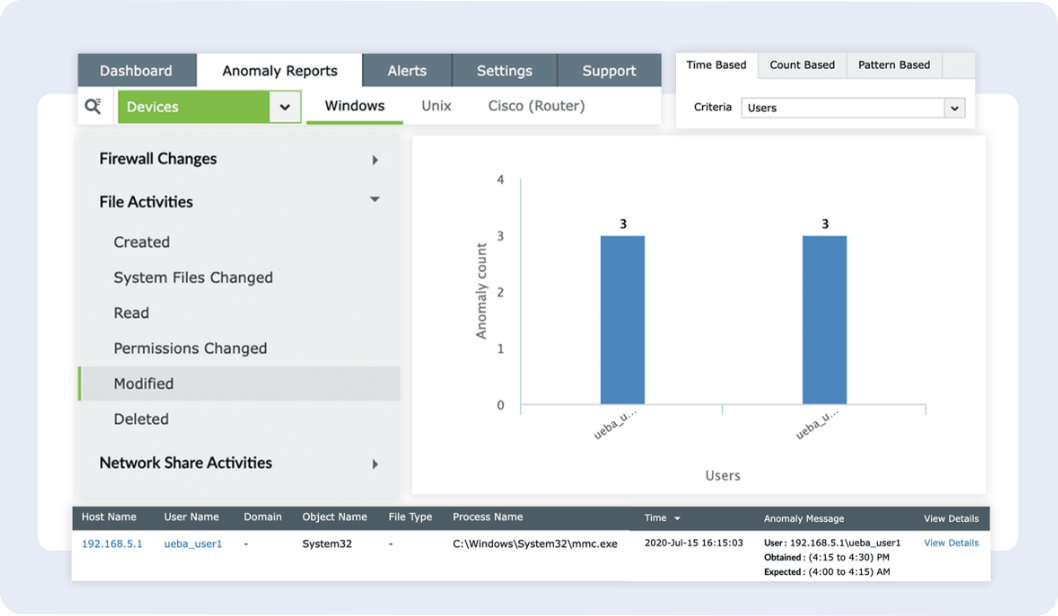
Anomaly detection:
Log360 establishes a baseline of normal network behavior and alerts administrators when there are deviations or anomalies. This helps identify novel or zero-day malware that may not have established signatures yet.
Integration with threat intelligence:
Log360 integrates with threat intelligence feeds, staying updated on the latest information about emerging malware threats, attack vectors, and tactics. This ensures proactive detection and response to the constantly evolving landscape of malware attacks.
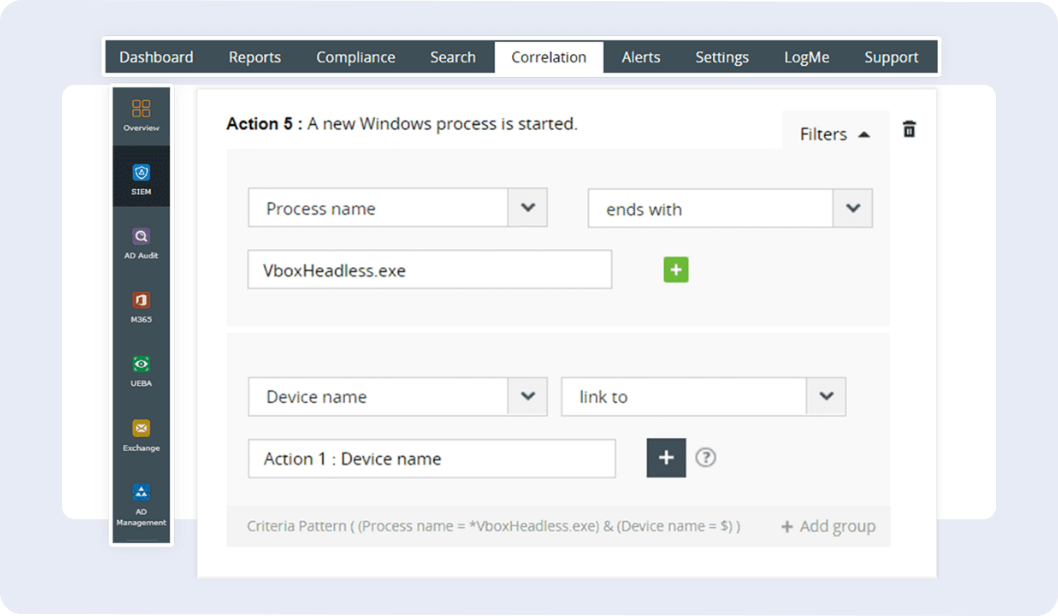
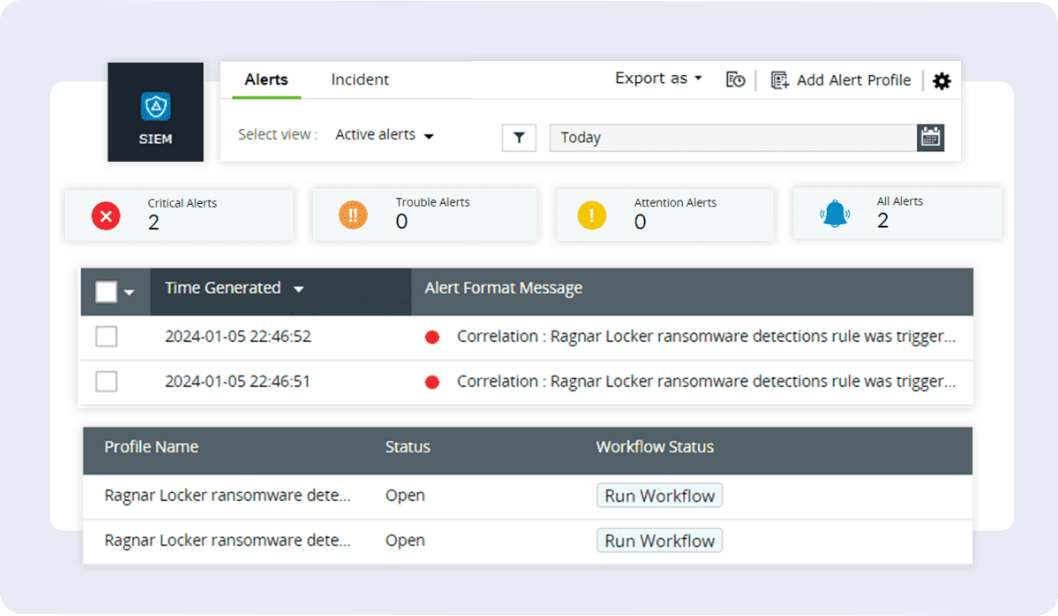
Rule-based correlation:
Log360 employs a rule-based correlation engine, swiftly detecting malware by analyzing patterns and anomalies in network logs, ensuring proactive threat identification and response. The following is an example.
- Correlation rule: Identifying ransomware activities on Windows
This rule is crafted to detect ransomware attacks, where a newly started process quickly modifies multiple files across network devices for encryption. It achieves this by correlating the initiation of a process with subsequent file modifications. - General action flow: Process started > File modified > File modified > (...) > File modified (all within a few minutes, on the same device)
- Specific action flow: Process started > At least 15 file modifications on the same device, by the same process, within the next 5 minutes
Real-time alerts:
Log360 enables the creation of custom workflows through a user-friendly interface. These workflows automatically respond to raised alerts, mitigating the impact of malware attacks without the need for immediate security administrator intervention.
What's next?
Interested to explore how ManageEngine helped enterprises across the globe to tackle malware attack and other cyberattacks? Get in touch with our solution experts.
- What is malware?
- The evolution of malware
- Objectives behind a malware attack
- Types of malware attacks
- Malware attack examples
- Defense strategies against malware attacks