Developed by a French programmer, Benjamin Delpy, Mimikatz is a powerful open-source tool that helps to extract credentials on Windows operating systems. Mimikatz basically takes advantage of the weaknesses present in a Windows system and uses many techniques to extract sensitive information, like passwords from Active Directory (AD) domain controllers, the Local Security Authority Subsystem Service (LSASS) process memory, the Security Account Manager (SAM) database, and other credential storage areas.
Adversaries use this tool to steal credentials since many antivirus systems or endpoint protection software find it difficult to detect these attacks. Therefore, with Mimikatz, adversaries can escalate privileges, execute data theft, or perform lateral movement within a network to carry out other suspicious events.
It is also important to note that Mimikatz is also used for legitimate reasons; for instance, pen testers, threat hunters, and white hat hackers use it to detect any vulnerabilities present in a network, enabling organizations or individuals to fix them by employing strong authentication mechanisms and patching vulnerabilities regularly to mitigate risks associated with credential theft.
How does Mimikatz work?
Mimikatz exploits Wdigest, which facilitates single sign-on (SSO) in Windows machines. Wdigest stores plaintext passwords in memory in a reversible format, making it susceptible to password extraction. So, when threat hunters have access to tools like Mimikatz, they can utilize this technique to extract hashes stored in the memory or to extract credentials.
In spite of the fact that Microsoft made it simple to disable the Wdigest function in Windows 8.1, and disabled it by default in Windows 10, if cyber attackers get administrator access, they can easily enable Wdigest and launch Mimikatz to attack Windows endpoints.
Attack techniques used by Mimikatz to access credentials
The Mimikatz tool is used to execute many adversarial techniques and tactics in Windows environment to extract credentials. Below are a few techniques Mimikatz uses to collect credentials:
- Pass-the-hash (ID:T1550.002):In this technique, adversaries use Mimikatz to retrieve the hash string (NTLM or Kerberos) present in the target computer's memory or within the SAM database and access resources without authorization. Using this technique and Mimikatz, adversaries don't even need the plaintext password to authenticate a compromised user's account, making it easier to move laterally within the network.
- Pass-the-ticket (ID:T1550.003): In a pass-the-ticket attack, adversaries extract data from stolen Kerberos tickets, such as ticket granting tickets (TGTs) and ticket granting service tickets (TGS), using Mimikatz. The tool helps them to steal the tickets from memory or the LSASS process. Adversaries can then move laterally through an organization's network to hunt for vulnerabilities.
- Overpass-the-hash (pass-the-key): Overpass-the-hash is a combination of pass-the-hash and pass-the-ticket, but this technique has a unique key which is obtained from the domain controller to impersonate the user.
- Pass-the-cache: A pass-the-cache attack is similar to a pass-the-ticket attack, but the only difference is that it uses the saved and encrypted login data on a Mac, Unix, or Linux system.
- Kerberos golden tickets (ID: T1558.001): With the help of Mimikatz, threat actors can obtain golden tickets, forged Kerberos tickets created by compromising the KRBTGT password hash, which encrypt all authentication tickets. This method helps adversaries to retrieve the password hashes of domain users.
- Kerberos silver tickets (ID: T1558.002): A silver ticket takes advantage of a feature in Windows that lets a user access all the services available in the network. The Kerberos protocol might not check the TGS key after it is issued, enabling adversaries to reuse the key and mimic the user on the network.
How to prevent attacks that leverage Mimikatz
Post-exploitation, it's difficult to contain an attack as the attacker has already obtained the required credentials to perform lateral movement or privilege escalation. Threat defenders will mostly be able to contain the damage caused. To avoid this altogether, defenders can incorporate certain practices to protect their Windows endpoints, and also conduct proactive threat hunting to detect and respond promptly to attacks that use Mimikatz.
- Disable debug privilege: By default, Windows permits local administrators to debug the system. Since Mimikatz uses this privilege to interact with the LSSAS, disabling debug privileges on systems is an effective way to protecting the system from suspicious attacks.
To do this, go to Group Policy (local or domain) > Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment and enable or disable the Debugging Program Policy.
- Restrict admin privileges: According to the principle of least privilege, a user or entity should only have access to the particular information, resources, and applications necessary to carry out a given task. Organizations that adhere to the least privilege principle can strengthen their security posture by drastically decreasing their attack surface and risk of malware infection. This can be done by offering admin privileges to a limited number of people who require these permissions to do their tasks.
- LSA protection: The LSASS is provided by Windows and helps to validate user accounts and remote logins. Local Security Authority (LSA) protection helps to prevent suspicious processes from communicating with the LSA. If an attacker manages to interact with this service, then they can easily gain unencrypted credentials that are stored in memory.
- Credential caching: Windows has a system registry where it caches password hashes that were recently used. Since the Mimikatz tool can obtain these credentials, it is necessary to change the caching policy to cache zero recent passwords, otherwise attackers might use the credentials to impersonate user accounts. To do this, navigate to Windows Settings > Local Policy > Security Options > Interactive Logon.
- Implement effective security tools: The best way to defend against Mimikatz attacks is to implement a reliable security tool, such as a SIEM solution or a network detection and response system. A SIEM solution provides a centralized platform for collecting, correlating, analyzing, and responding to security events and logs generated by various systems and applications within an organization's network.
For instance, pass-the-hash attacks are challenging to identify, but Log360 uses log analysis and Sysmon analysis to identify successful anonymous authentications. Additionally, the solution offers information on the logon type, the remote device from which the pass-the-hash attack occurred, and other crucial variations of this method.
Defending against attacks that leverage Mimikatz using Log360
Log360 is a unified SIEM solution that implements the MITRE ATT&CK threat modelling framework's tactics and techniques in its threat detection system to help with threat hunting, contain security threats, and investigate them.
For the purpose of identifying various lateral movement strategies, Log360 combines a signature-based threat detection framework that relies on the MITRE ATT&CK threat model, and an anomaly module based on machine learning. Log360 is an effective and precise instrument for lateral movement technique identification since it combines the two threat detection frameworks.
Log360's use of the MITRE ATT&CK framework provides a range of reports that helps in detecting and mitigating Mimikatz-related activities:
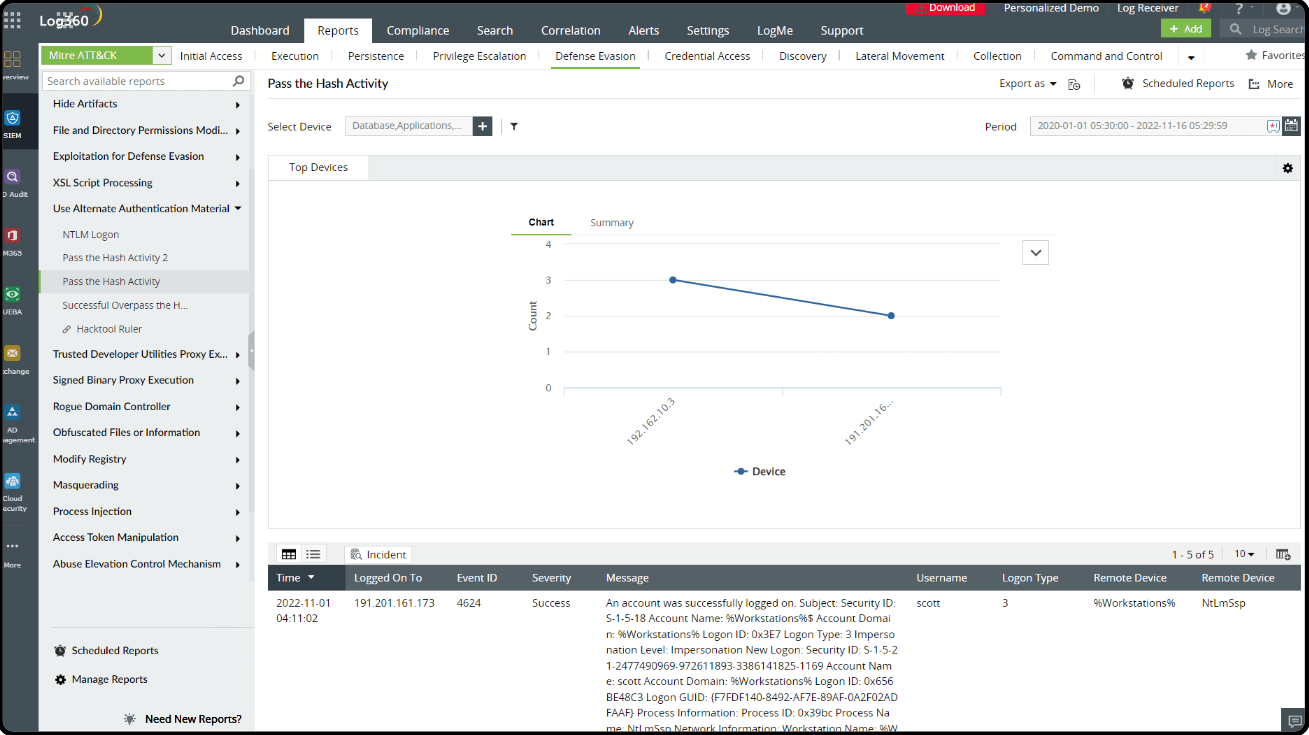
To detect pass-the-hash activity (T1550.002), IT admins need to examine event ID 4624 (An account was successfully logged on), along with Logon Type = 9, Authentication Package = Negotiate, Logon Process = seclogo, or Sysmon event ID 10. There are other event IDs that can be monitored to identify a potential pass-the-hash attack:
- Event ID 4648: This event is generated when a process attempts to authenticate on behalf of a user. Monitor logon events with Logon Type 4 (batch logon) or Logon Type 8 (network clear text logon).
- Event ID 4672: This event is logged when an account successfully logs on with elevated privileges. Look for events indicating the use of administrative accounts during network logons.
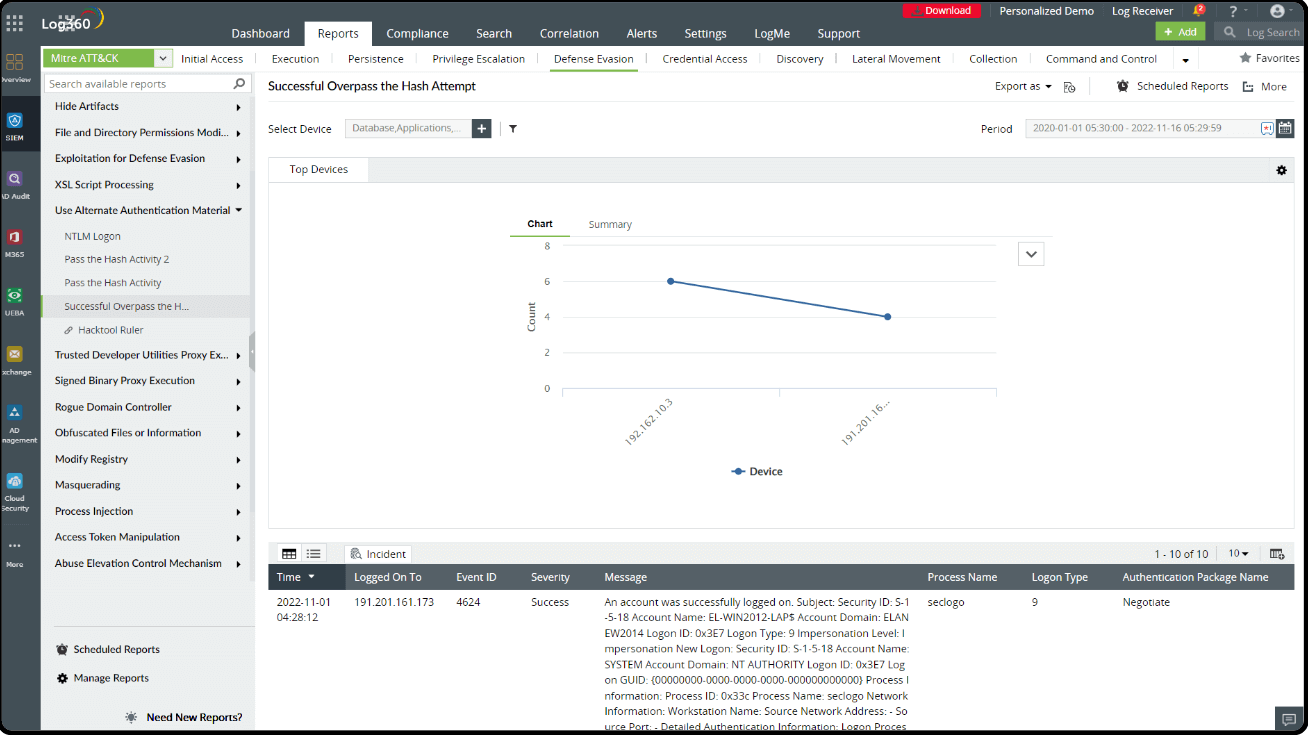
The best way to detect an overpass-the-hash attack is by using the same strategy of detecting a pass-the-hash attack. IT admins can figure out if it is an overpass-the-hash attack if the event log shows a Kerberos authentication ticket in the domain controller.
- Event ID 4768 and 4769: These events pertain to Kerberos authentication and can provide insights into potential overpass-the-hash attacks. Monitor TGT requests with encryption levels 0x17 for RC4, 0x11 for AES128, and 0x12 for AES256.
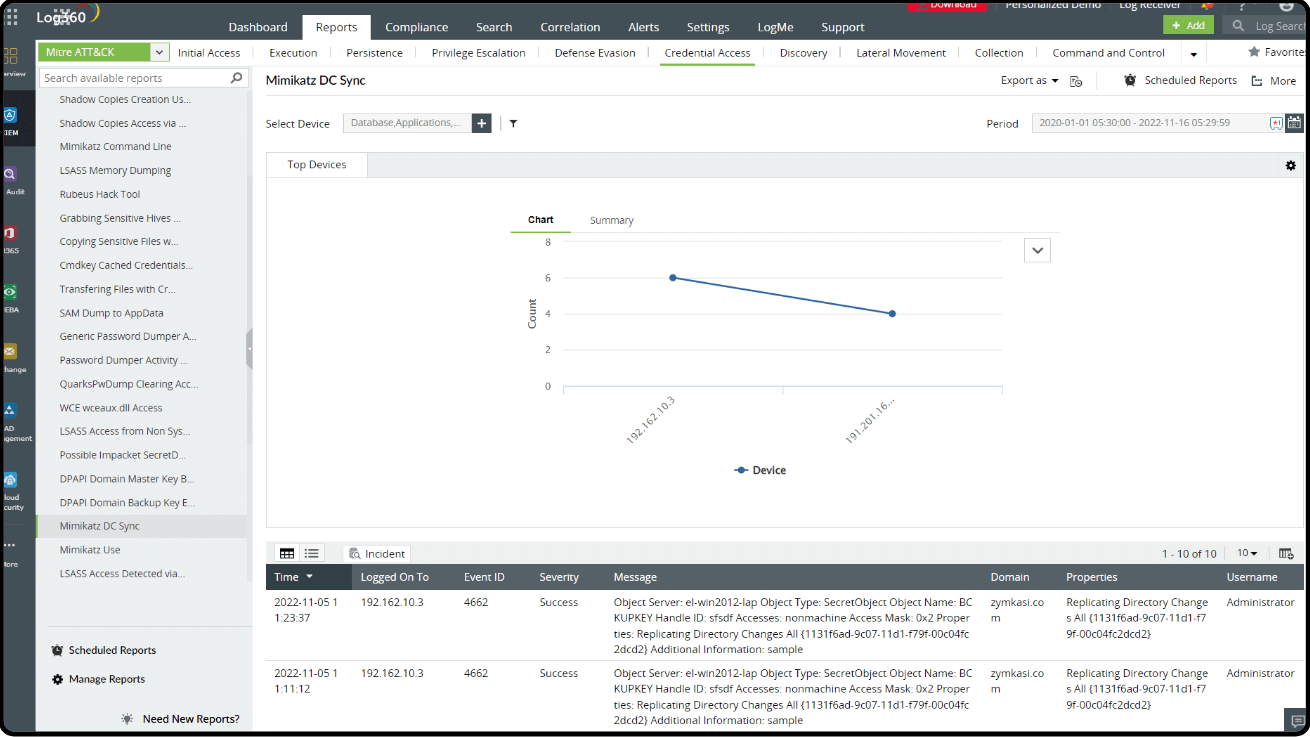
Examining some specific event IDs will help to detect potential Mimikatz DCSync activity within an AD environment.
- Event ID 4662: This event is generated when an object's access permissions are modified. Look for modifications related to AD objects associated with replication, such as changes to replication groups or directory partitions. Check event log 4662, where the Object Server is "DS" and the properties contain "1131f6ad-9c07-11d1-f79f-00c04fc2dcd2" (DS-Replication-Get-Changes-All) and "19195a5b-6da0-11d0-afd3-00c04fd930c9" (Domain-DNS class WRITE_DAC).
What's next?
Implement defensive strategies and incident response measures using the advanced security features of Log360.
- How does Mimikatz work?
- Attack techniques used by Mimikatz to access credentials
- How to prevent attacks that leverage Mimikatz
- Defending against attacks that leverage Mimikatz using Log360