Armed with dynamic peer grouping,
Log360 helps you create a stronger security policy
Dynamic peer grouping is a feature within behavior analytics that bolsters the anomaly detection and risk scoring capabilities of a SIEM solution. It is the process of grouping users in a network based on the behaviors they exhibit and establishing a baseline for the group. This baseline is then used as a reference to detect anomalies.
In simpler words, dynamic peer groups provide context to user events in the network, helping to detect threats with higher accuracy.
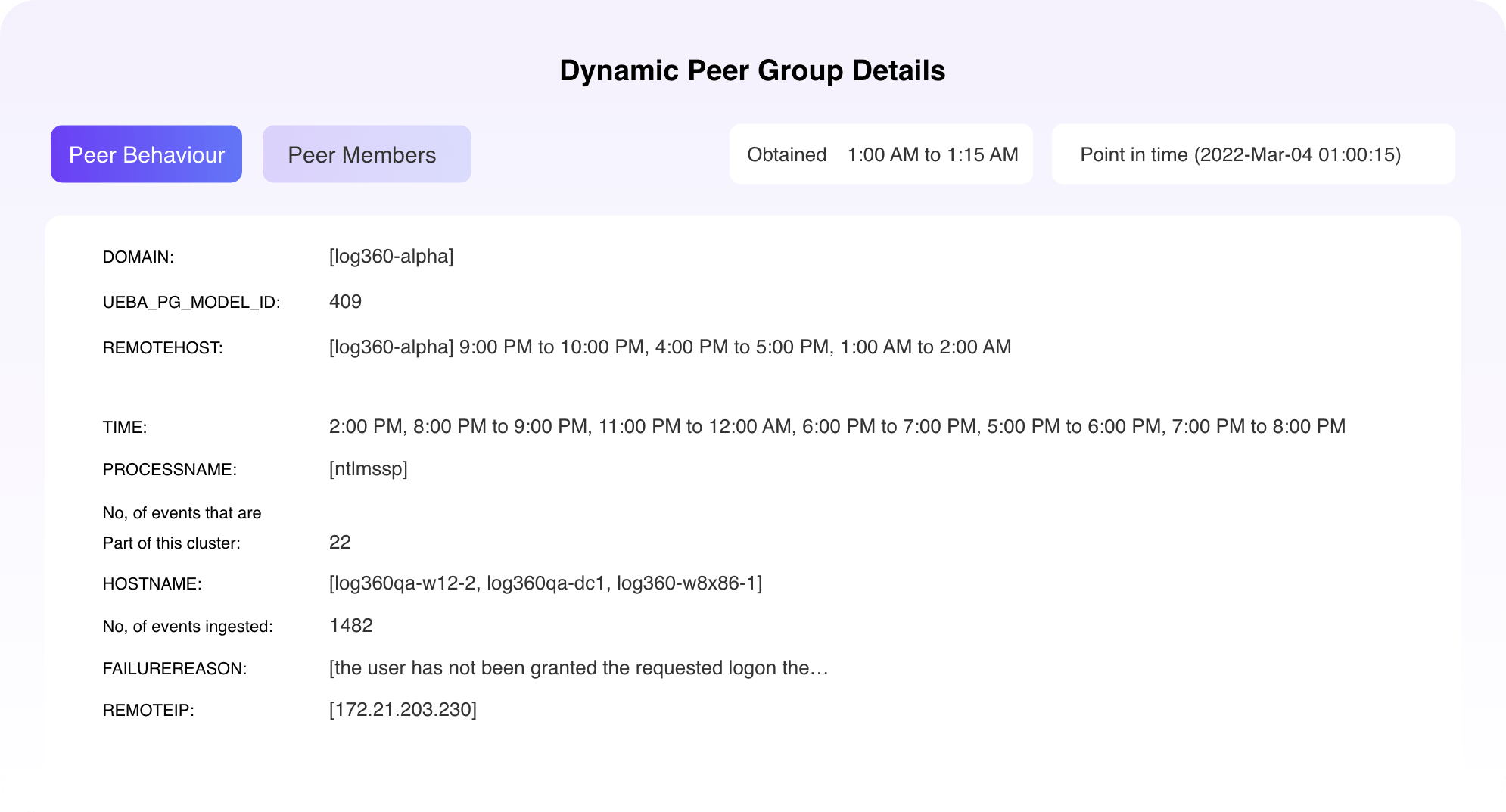
Log360 creates peer groups for each of the reports it has within the UEBA module. These groups are time-based, count-based, and anomaly-based. Any event by a user is evaluated based on the clusters the user is a part of and the UEBA risk score is altered accordingly. If the score rises beyond a set threshold, a high-risk alert is raised.
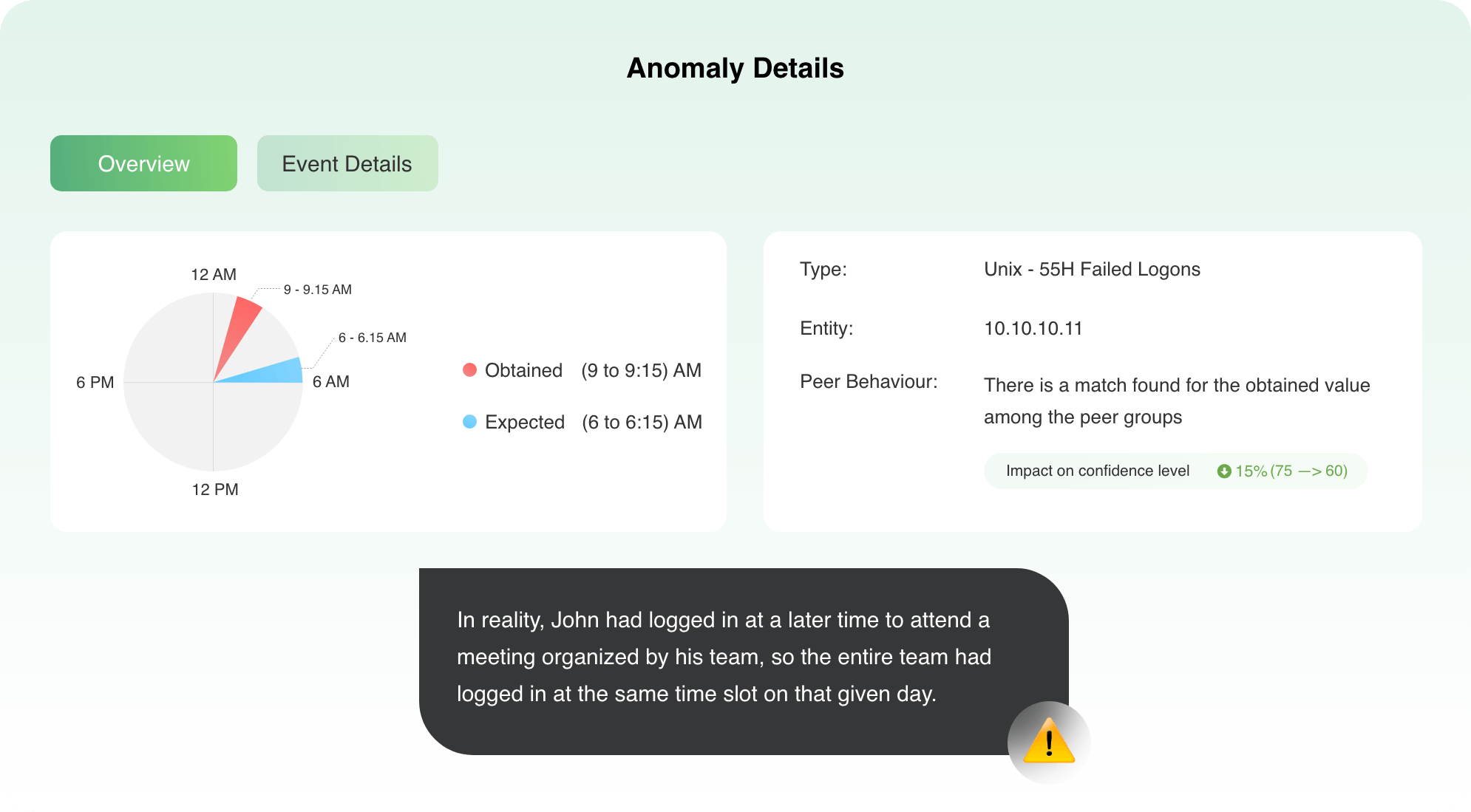
A user, John, logs in between 9am and 9:15am, which is not in accordance with his usual login time between 6am and 6:15am.
This is flagged as an anomaly by Log360's UEBA feature and a high-risk score is generated.
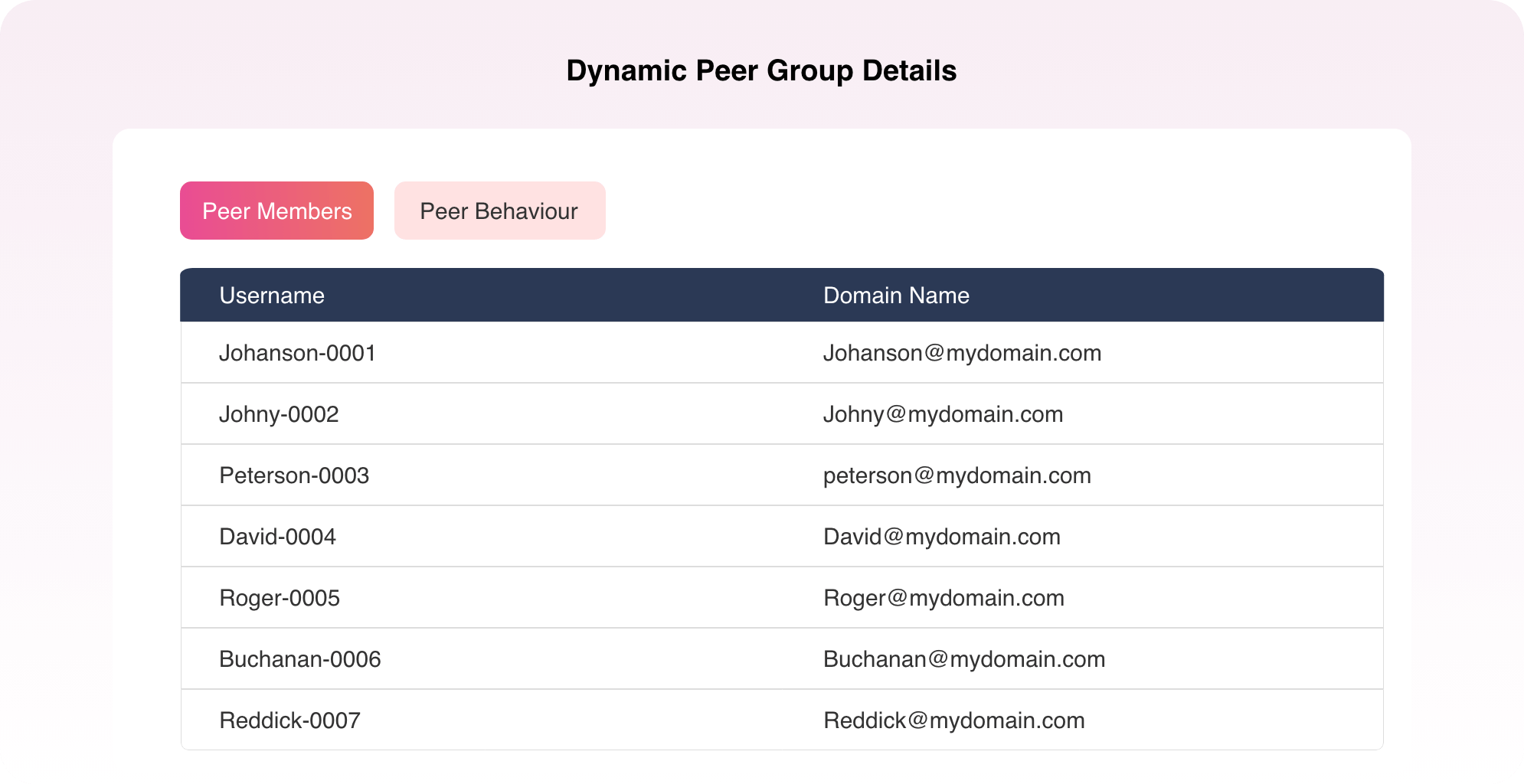
This is where dynamic peer grouping comes into the picture.
Since the team regularly would have logged in around the same time, John would be a part of a cluster with other team members. And when this anomalous event is viewed in the context of the login time of other members of that peer group, it is less likely to be a threat. In cases like these, the risk score is reduced based on ML algorithms.
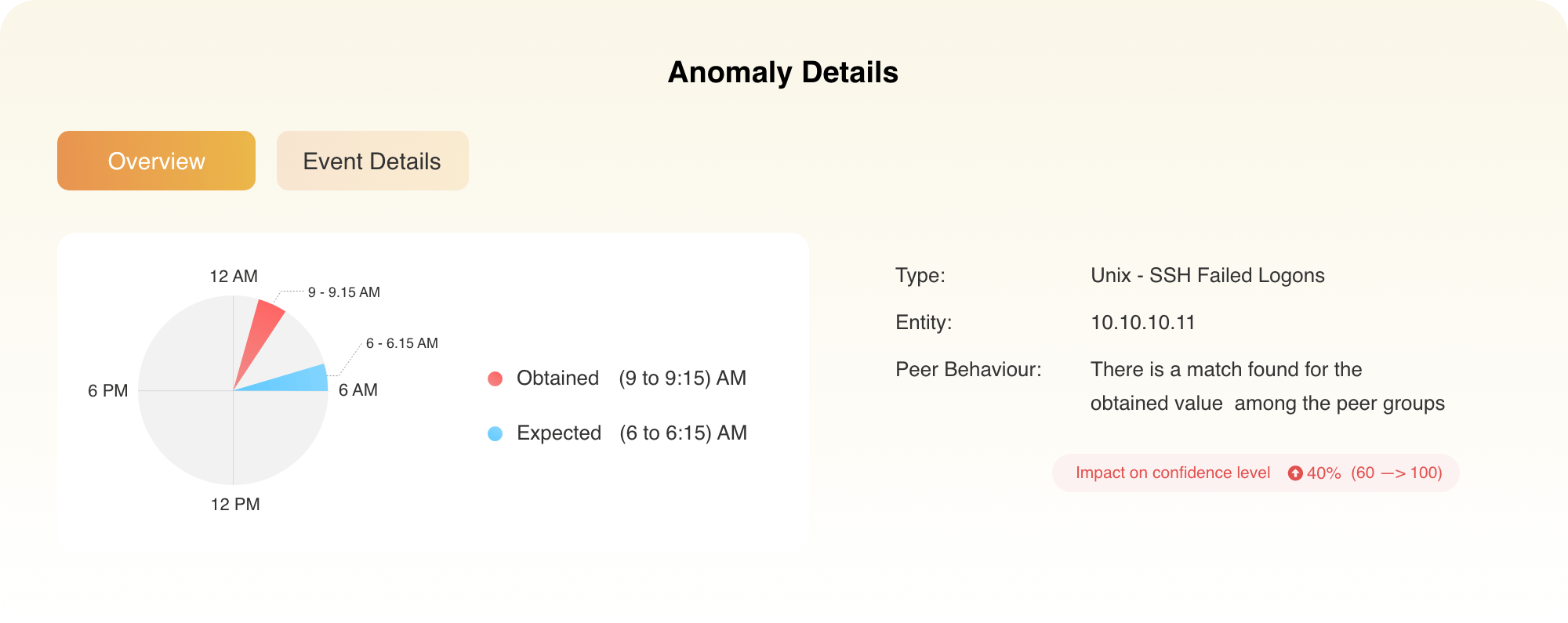
In another case, Maria logs in between 9am and 9:15am, which is not in accordance with her usual login time between 6am and 6:15am.
This is again flagged as an anomaly by Log360's UEBA feature and a risk score is generated accordingly. When this behavior is not in line with the user's peer group, the risk score of this event is increased further to flag an alert.
This is how dynamic peer grouping in Log360 works and helps to accurately detect user event anomalies occurring in the network in real time. This paves the way for a strong and successful threat defense system.