Out-of-the-box compliance reporting. Security Analytics. Real-time alerts
SIEM solutions are essential to help organizations comply with regulatory mandates and pass their security audits. With capabilities to improve the security posture of business by monitoring Security Operation Centers (SOC), logging network activities, and providing alerts, SIEM solutions can help meet the IT requirements of compliance mandates.
Most compliance requirements including PCI DSS, HIPAA, FISMA, SOX, GDPR, CCPA, and more share a common framework for security controls including privileged user monitoring, sensitive data monitoring and protection, and incident response. Log360’s integrated compliance management aims to simplify the audit process, minimize security risks, and ease the compliance demonstration for enterprises.
Out-of-the-box. Up to date.
The high-speed search engine of Log360 helps narrow down and track the exact log entry that serves as the evidence for the incident. Further, export the evidences as incident reports that can be passed on for data breach investigation.
Continuously audit changes to critical security configurations such as firewall rule modifications, security groups, GPOs and more to detect user-based threats.
Log360 automates log data collection from firewalls, routers, switches, workstations, servers, critical application and more. See the list of supported log data sources.
With Log360's real-time event response system's Compliance Alerts get notified whenever there's a compliance requirement violation or suspicious data breach activity. Workflows can be associated with these alerts to automate the remediation process.
Spot security threats with rule-based real-time correlation engine, machine-learning driven user and entity behavior analytics, and MITRE ATT&CK framework mapped threat detection system.
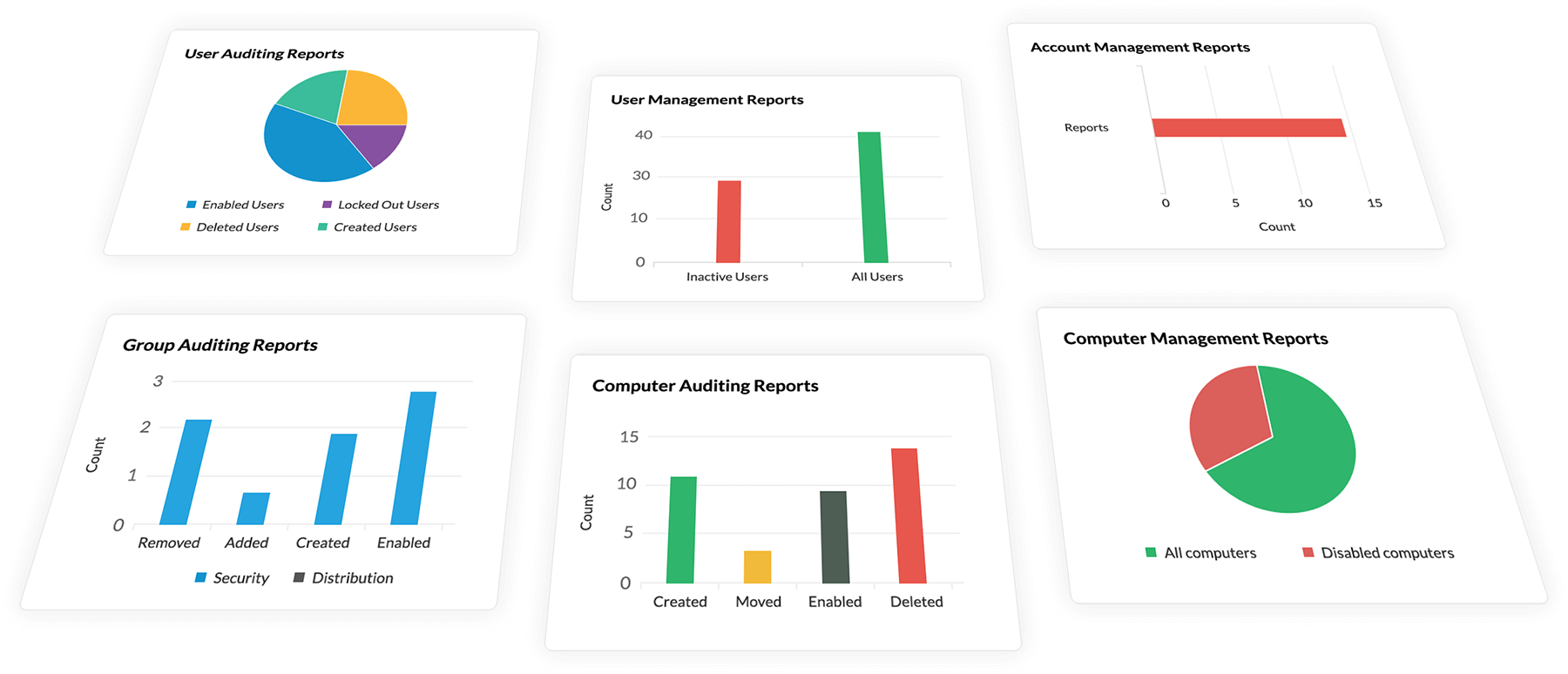
Log360 comes with out-of-the-box compliance reports for PCI DSS, HIPAA, FISMA, GDPR, SOX, ISO27001, and more. These reports provide evidence for your adherence to requirements stated out in the compliances simplifying your security auditing.
Dive deep into admin and other privileged user activities using Privileged User Monitoring security analytics dashboards and reports. Get alerted for anomalous user behaviors.
Automatically neutralize security threats by associating workflow profiles with alerts. Streamline incident resolution by tracking and monitoring the resolution process with Incident Management console.