Real-time security monitoring
In this page
- What is real-time security monitoring?
- How does a SIEM solution help?
- Why are monitoring solutions imperative?
Understanding the vast and complex network environment is no small feat. It requires continuous observation, in-depth analysis, and quick responses to any irregularities.
This is why a real-time cyber security monitoring tool is an essential aspect of any organization's IT security strategy. Cyberattacks and compliance regulations are the two primary drivers for IT security. Meanwhile, data breaches and non-compliance to regulatory standards can cost your company a fortune.The threats facing businesses are increasingly sophisticated and can go undetected for months. This is why it's important to keep constant vigilance and have proper security solutions in place.
Cybersecurity monitoring provides complete visibility on what's happening in your network. It acts as the frontline defense against security threats, allowing organizations to manage risks proactively and respond efficiently to potential threats.
What is real-time security monitoring?
Real-time security monitoring is continuously overseeing and analyzing the data traffic and activities in an organization's network to detect, alert, and respond to potential security threats as they happen.
Instead of periodically reviewing logs or reports, real-time monitoring offers immediate insight into security events, allowing for a faster mitigation response.
Real-time security monitoring includes:
- Acquiring and storing log data from network devices.
- Real-time monitoring and alerting about critical events as they happen.
- Periodically running vulnerability scans to identify potential security gaps.
- Performing correlation on collected data to identify anomalies and attack patterns.
- Conducting forensic analysis on real-time and historical events.
- Tracking compliance requirements.
These activities are considered security information and event management (SIEM), and effective SIEM often requires a solution.
About this explainer: Regulatory compliance requires continuous monitoring and reporting. Learn how SIEM helps organizations stay audit-ready in our expert series on What is SIEM and SIEM tools.
How does a SIEM solution help?
A SIEM solution provides real-time analysis and alerts for security events. This is achieved through customizable dashboards that display charts, graphs, and reports in a user-friendly manner. This helps you keep cyber attacks at bay by helping you understand network events and alerting you about suspicious activities.
SIEM solutions facilitate this by performing data aggregation, correlation, analysis, alerts, and forensic analysis. It also uses advanced threat intelligence to understand these threats better. The incident response frameworks help users respond to security incidents by raising alerts and executing automated workflows, which helps organizations reduce the attack intensity. These capabilities make SIEM solutions indispensable for real-time security monitoring.
- Log management
- Alerts and incident
response - Compliance
- Comprehensive
reports - Correlation
Engine
Log management
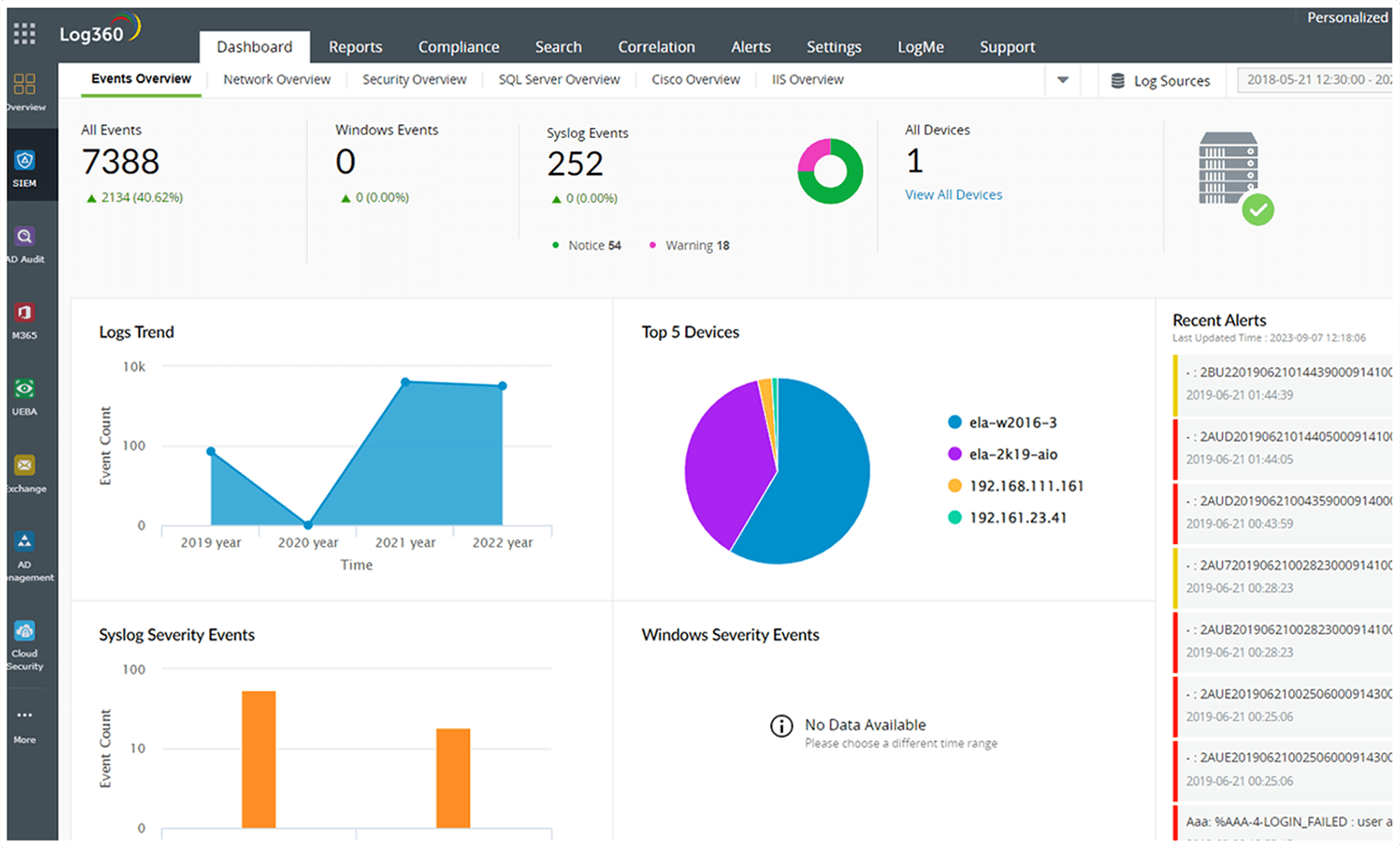
Transform raw logs into visually intuitive dashboards for easy data interpretation.
Get a clear visibility of all events, alerts, and their details directly from the overview dashboard.
Alerts and incident response
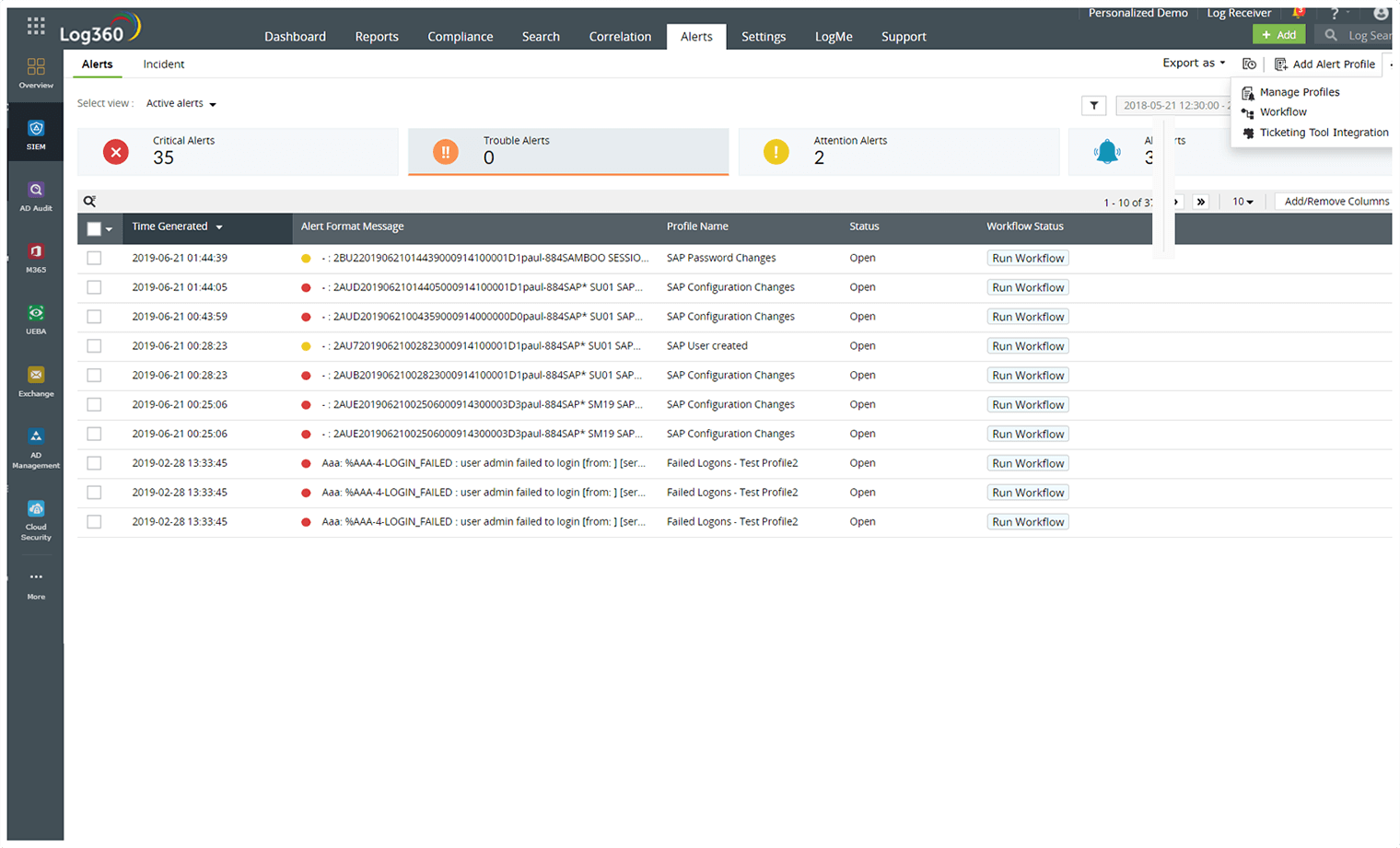
Seamlessly Create and manage workflows to initiate predefined activities upon specific alert detection.
Automate alerting about security events when an incident is detected.
View a detailed breakdown of all your incidents, their current statuses, and associated categories.
Compliance
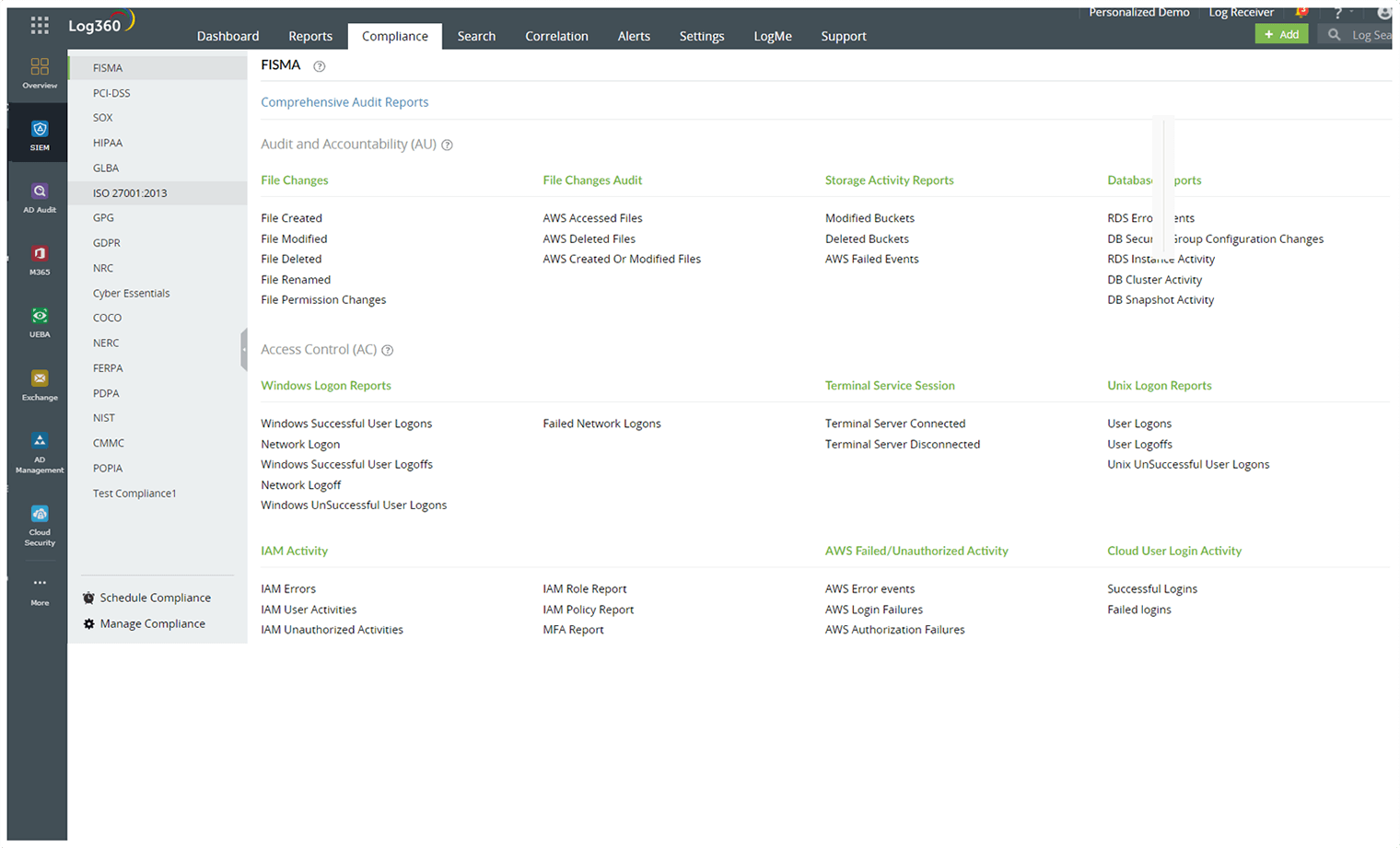
Generate predefined compliance reports for prominent IT regulatory mandates.
Set up your compliance reports to be generated on a schedule that fits your organization's needs.
Customize additional compliance reports to align with your organizational demands.
Comprehensive reports
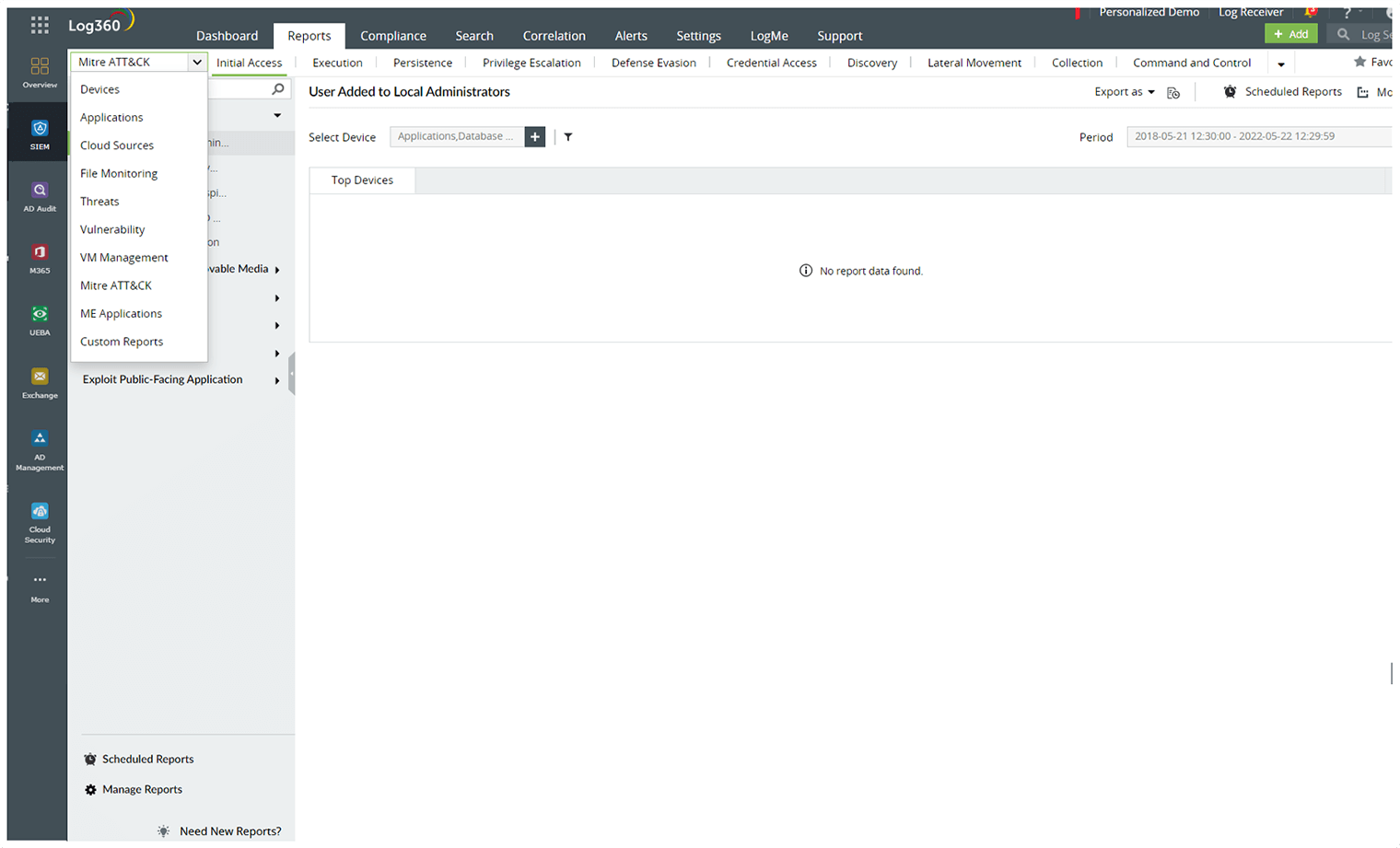
Customize your own reports here to meet specific requirements.
Utilize MITRE tactic reports for enhanced threat detection and response, all aligned with the renowned ATT&CK framework.
Find specific reports from different log sources and application for a wide network visibility.
Correlation Engine
Create a manage all your latest correlation rules for improved threat detection.
Leverage correlation reports specifically designed to help you detect prominent attack patterns.
Have a singular, unified place to view all your most recent incidents for efficient management.
- Log management:
The solution facilitates log management by centrally collecting, storing, and archiving network logs in real-time.
- Correlation engine:
The solution can identify potential threats in real time by comparing and correlating network activities against known attack patterns or anomalous patterns.
- Threat intelligence feeds:
Real-time monitoring solutions integrate with threat intelligence services and update their databases with the latest threat indicators to enhance detection capabilities.
- Real-time security analytics:
Real-time intuitive dashboards display a visual representation of network activity, and offer immediate insights into the current security posture with alerts and readily available reports.
- Automated incident response:
When a potential threat is detected, real-time monitoring solutions can take predefined protective actions. This includes automatically starting off a series of predefined workflows designed to counteract the threat like blocking malicious IP addresses,and more.
- Instantaneous alerts:
Apart from taking predefined protective actions, the system immediately sends alerts to security personnel or other designated parties upon detecting suspicious or unauthorized activities.
- Compliance and regulation:
Industries are inevitably bound by regulations that require continuous monitoring to ensure the security and data privacy. Real-time monitoring aids in compliance management and aims to simplify the audit process, minimize security risks, and ease the compliance demonstration for enterprises.
Why are monitoring solutions imperative?
- In a world where data breaches regularly make headlines, ensuring the security of an organization is of utmost priority. This ensures a stable workflow and minimizes the possibility of being attacked by malicious actors.
- Protecting user data, a segment of protecting the network, has also become an imperative part of maintaining customer trust. By having real-time monitoring in place, organizations send a message to their users that their data is taken seriously and protected around the clock.
- Organizations need to be proactive about their security. Real-time monitoring facilitates a proactive stance, constantly checking for vulnerabilities and potential threats, and allowing businesses to address them before they can be exploited.
- While setting up a cyber security monitoring tools might require initial investment, the ROI can save organizations significant costs in the long term. Companies can avoid financial penalties, legal issues, and reputational damage by preventing major data breaches or minimizing their impact.
- SIEM solutions keep your organization's security in check by analyzing data, sending alerts, and helping you respond promptly.It's like having a watchful eye on your network 24/7, catching threats as they happen.


