Cisco Access Control List (ACL) in networking
In a network environment which consists of a large number of employees and network devices, there will be a lot of incoming and outgoing data traffic. This leads to bandwidth bottlenecks, which in turn affects the transmission of important data. In order to control this, you need to identify the network devices which consume a lot of bandwidth using a traffic monitoring tool. Once the devices are identified, you can apply the Access Control List (ACL) policies on the network devices to determine the priority of data during transmission. Network Configuration Manager serves this purpose since it allows you to apply ACL policies in multiple devices by bulk execution of configlets.
Now let us see certain guidelines to follow while configuring ACLs:
Cisco ACL configuration guidelines
- Only one ACL per interface, per protocol, per direction is allowed.
- ACLs are processed top-down; the most specific statements must go at the top of the list. Once a packet meets the ACL criteria, the ACL processing stops and the packet is either permitted or denied.
- ACLs are created globally and then applied to interfaces.
- An ACL in network configuration can filter traffic going through the router, or traffic to and from the router.
How to configure Access Control List in Cisco router
It is important to configure ACL policy before applying it is pushed to the network devices. If the access list is not configured, then all the traffic will be permitted. Here, we have taken three examples to explain how different types of access lists can be pushed to a Cisco router to configure ACL on Cisco router using Network Configuration Manager.
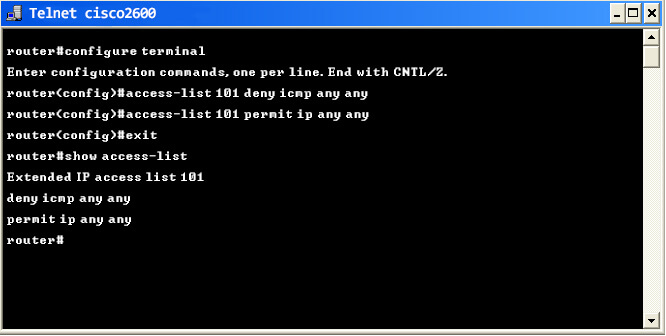
Example 1: If you want to block icmp traffic from any network but allow IP traffic, the following configuration commands can be used to configure ACL in Cisco router:
The corresponding configlet commands for executing the above commands in Network Configuration Manager:
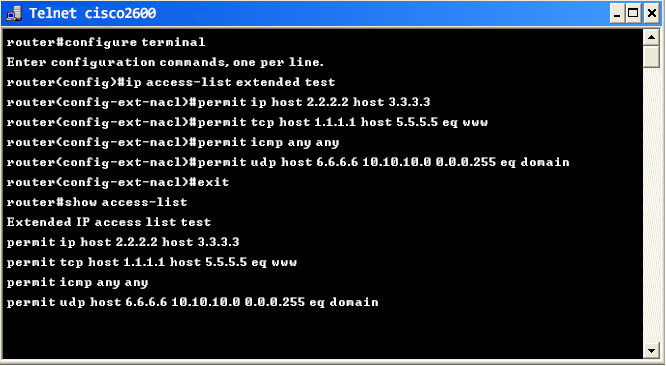
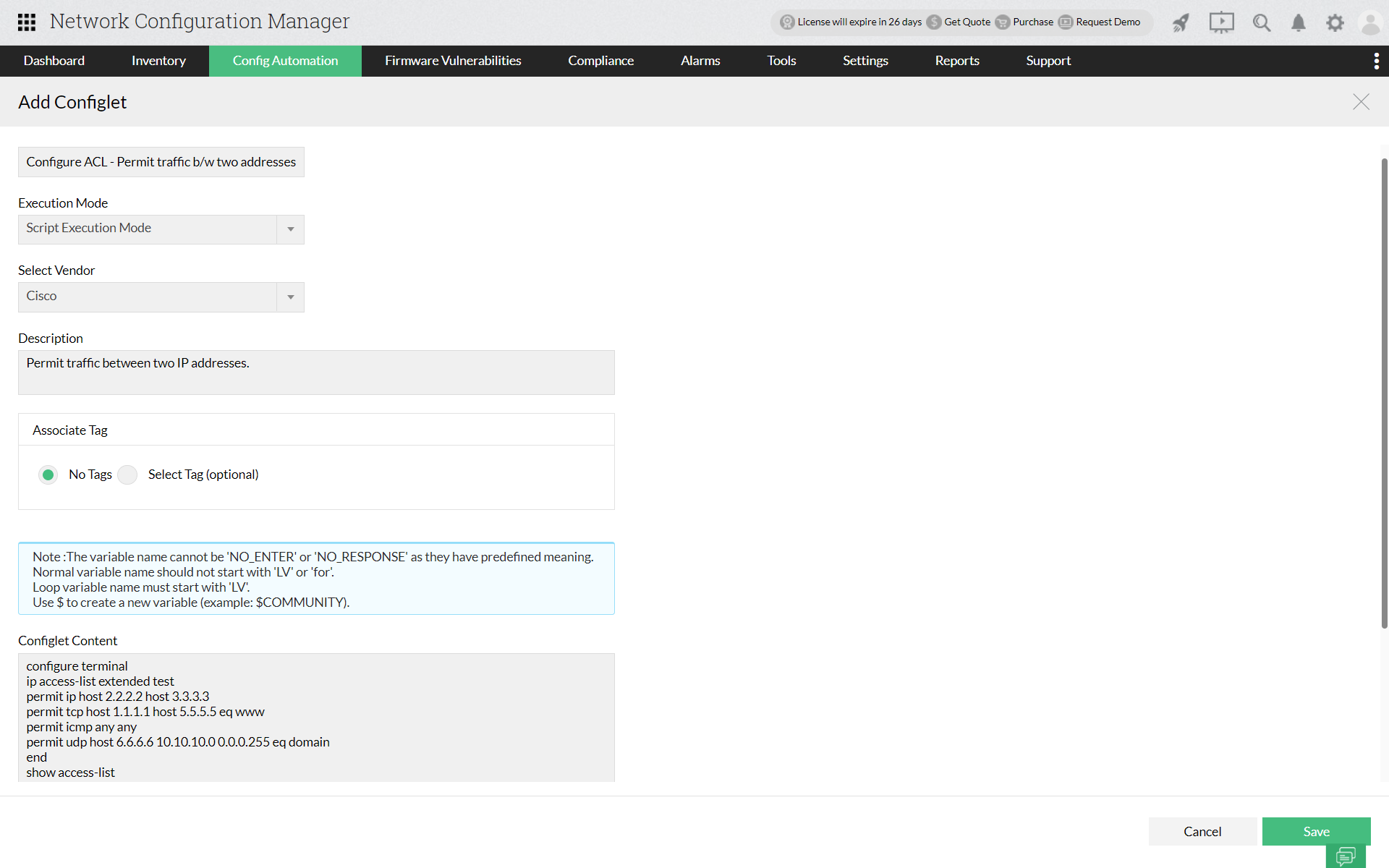
Example 2: If you wish to permit traffic between any two specific IP addresses, you can specify the necessary IP addressees. Further, you can also specify the transmission type as ip, tcp, icmp, udp, etc,. The terminal given below shows the configuration between two specific IPs along with the transmission type.
The corresponding configlet commands for executing the above commands in Network Configuration Manager:
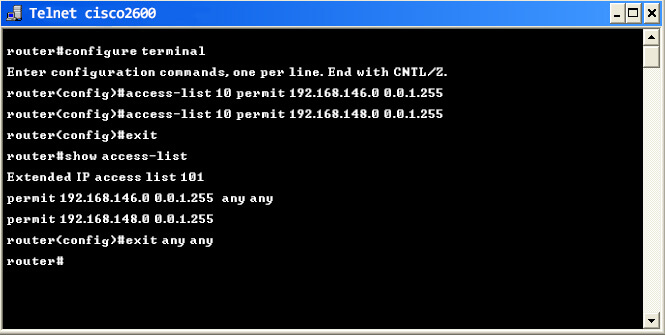
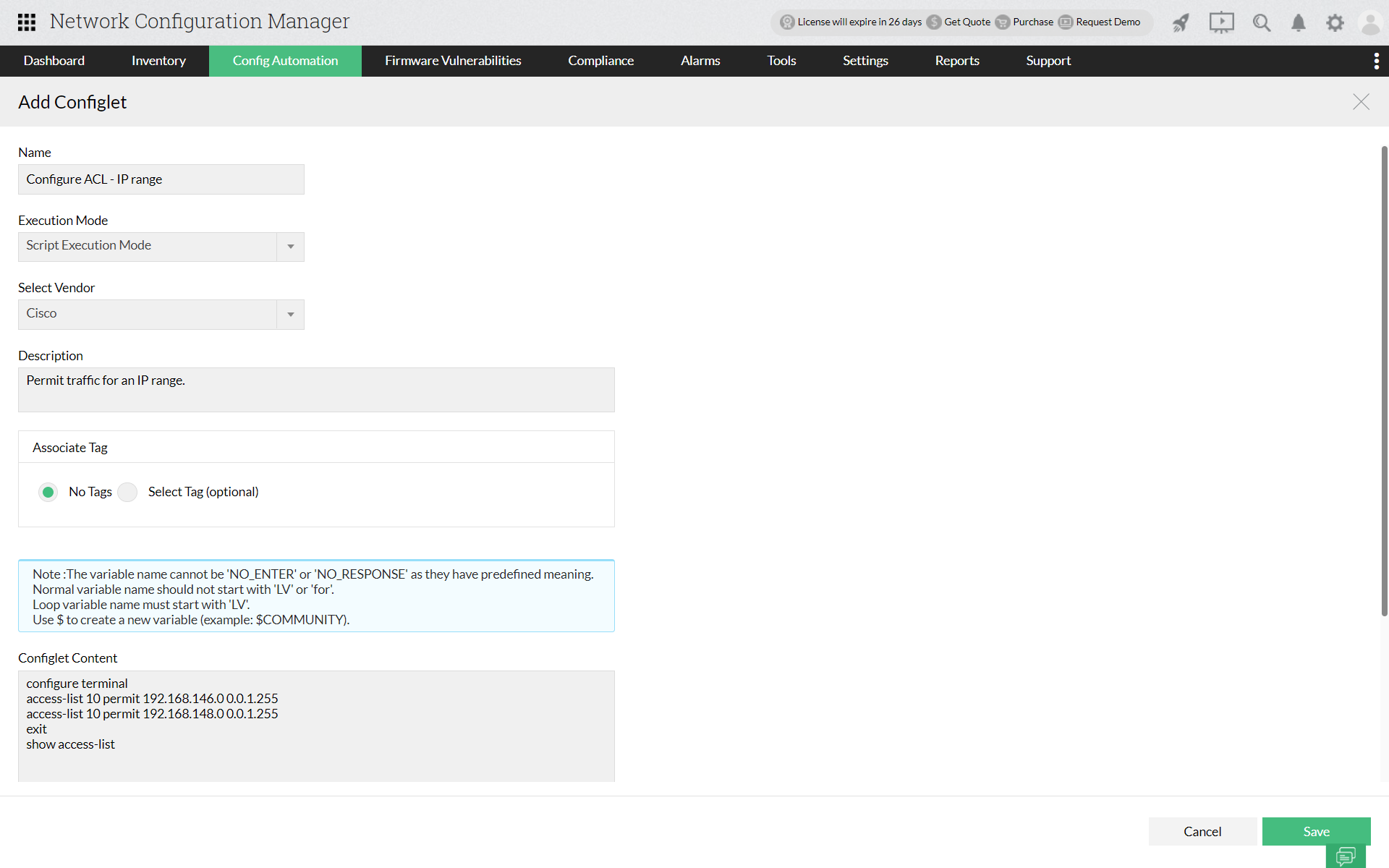
Example 3: If you wish to permit traffic from ip addresses which fall within a particular range, you can do so by specifying the start IP and the end IP. Thus, you can ensure that all the IP ranges which fall in between receives and transmits data traffic. The terminal given below shows the configuration of ACL commands to permit traffic in all the IP's falling within a particular range.
The corresponding configlet commands for executing the above commands in Network Configuration Manager:
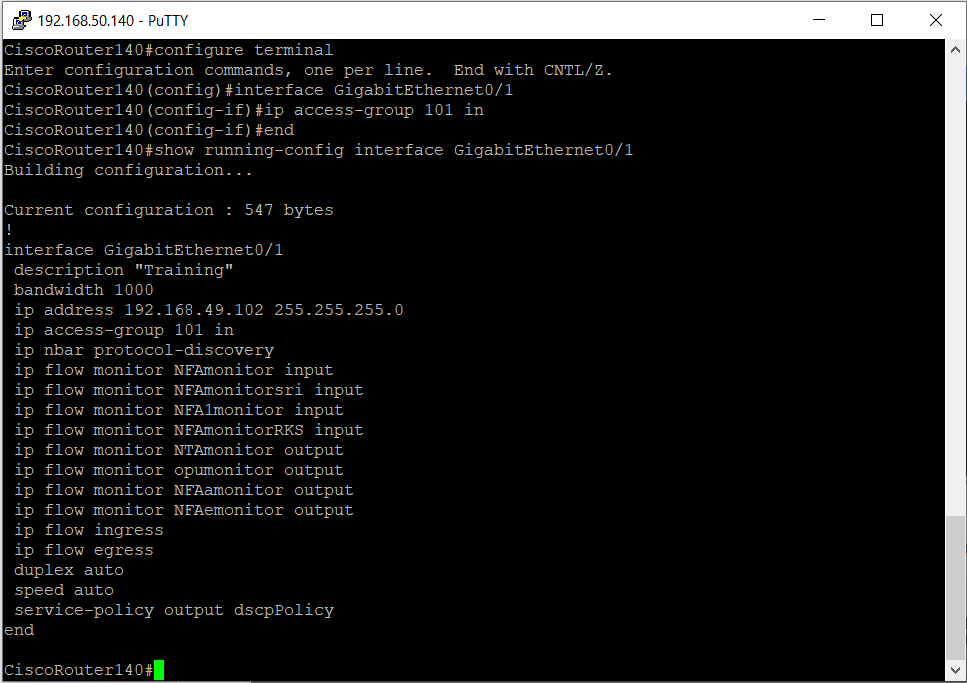
Example 4: If you want to apply an access list to an interface, you can do so by specifying the interface and the access list. The terminal given below shows the configuration of ACL commands to apply the access list created in Example 1 to an interface.
Executing ACL in Network Configuration Manager
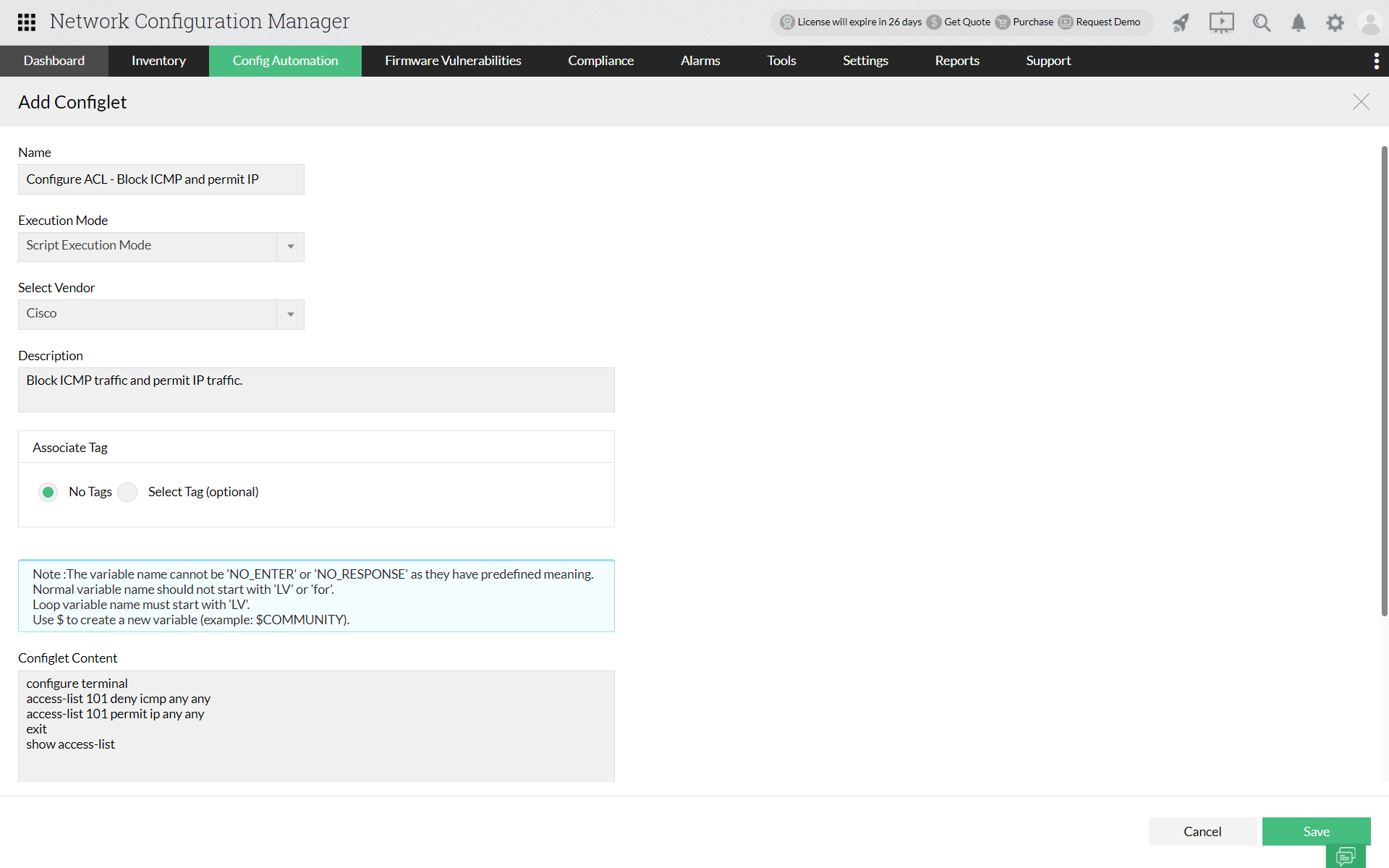
Access Control List commands can be executed in Network Configuration manager using
Configlets. The user can select the most suitable type of Access Control List based on their network needs. Network Configuration Manager primarily uses script execution mode to carry out ACL commands. Once the suitable ACL commands are entered in the "Configlet Content" box, that particular configlet can be pushed to multiple devices in bulk.Thus, Network Configuration Manager helps to keep network traffic under control along with saving users from manually executing commands for every single network device.
Not just that, with the help of configlets you can also
upgrade firmware and execute commands to fix errors and to make bulk changes. Click
here to know more about Configlets!
FAQ on configuring Cisco ACLs
What is an Access Control List (ACL)?
+An Access Control List (ACL) is an ordered set of rules for filtering traffic. Access control lists can be used to filter incoming or outgoing packets on an interface to control traffic. Access lists also help in defining the types of traffic that should be allowed or blocked at device interfaces. For example, if you wish to permit e-mail traffic to be routed and block the TELNET traffic from entering a network, an Access Control List can be used. Access Control Lists play a major role in controlling bandwidth bottlenecks and is crucial for every organization to maintain a consistent network performance.
What is access control in Cisco?
+ACLs in Cisco are rules applied to Cisco router interfaces or network devices that control the flow of network traffic. They can permit or deny traffic based on IP addresses, protocols, ports, and other criteria.