
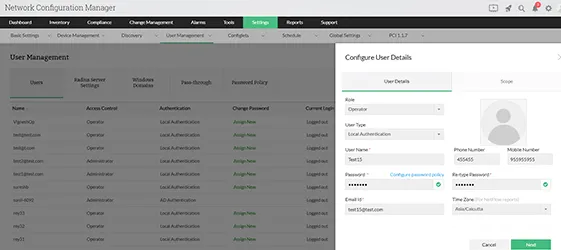
In a multi-user environment, for configuration change management, role based access control is important to prevent any unauthorized changes being made to the devices. The network admin has the authority to create roles and assign users to the roles. The users' access is restricted to particular group of devices based on their role's scope of access. If the role is assigned to the Juniper device group, the user can access only that group and the rest of the network would be inaccessible. The users can backup and sync configurations and also request configuration uploads to the devices. The changes will be applied only if the admin approves them. The admin can choose to approve or reject the changes and leave appropriate comments. Learn more about Configuration change management tool for access control (RBAC)
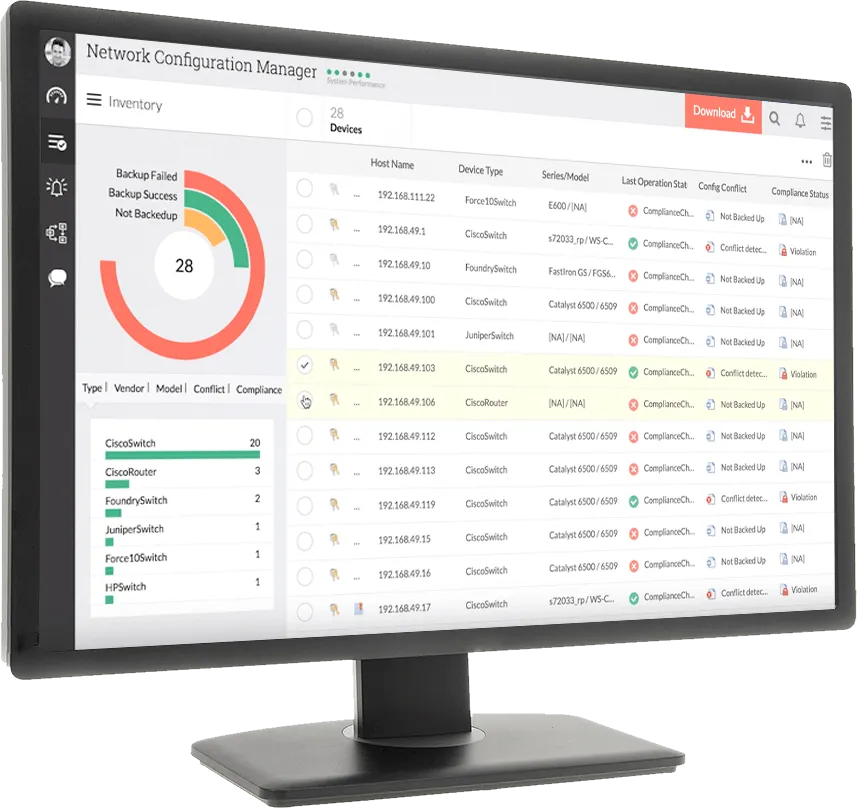
Network Configuration Manager or configuration change management tool provides the option to take manual, automated and scheduled backups for configuration change management. Whenever a backup is triggered, Network Configuration Manager compares the configuration file with the recent configuration backup. If changes are detected, the configuration is versioned and stored. The configuration backup is discarded if there are no changes between the two configuration files. The versioned storage creates a configuration history that can be used to compare configurations and spot differences. Learn more about Configuration change management tools with configuration versioning and storage
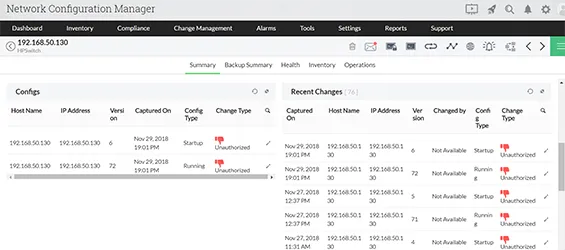
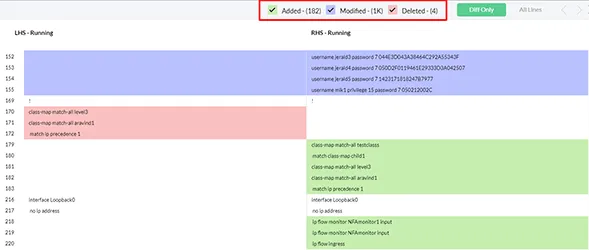
To spot changes in the device configurations, the user has to look through the entire configuration file. This could be time-consuming and difficult to troubleshoot when there are several network devices. In configuration and change management, Diff view simplifies this task by showing the user a side by side comparison of two configuration files. To easily identify changes and their types, the comparison is color-coded. Diff view also gives information about the who and when of the configuration changes and if the version in question is a result of a manual, scheduled or an automated backup. Learn more about Network configuration change management tool for config comparison
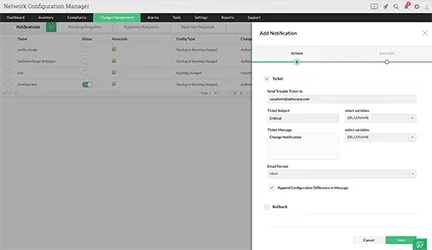
To avoid mishaps due to configuration changes, the network admin must be notified every time a change is made. The configuration change management software Network Configuration Manager sends the admin notifications every time a user makes changes to configurations. In config change management, the notifications are triggered by syslog messages. Everytime a user logs out of a device, a syslog message is generated and sent to Network Configuration Manager's built-in syslog server. On receiving this message, Network Configuration Manager compares the configuration with the recent backup.If changes are found, the admin is notified and a backup of the device is triggered. Network Configuration Manager notifies the admin via email, SNMP traps, syslog messages and trouble tickets. These notifications are called 'change' notifications and the admin can specify what type of changes can trigger notifications. For mission-critical devices, the admin can also automate a rollback mechanism, to prevent unauthorized changes from taking effect. Learn more about Configuration change management process with real-time notifications
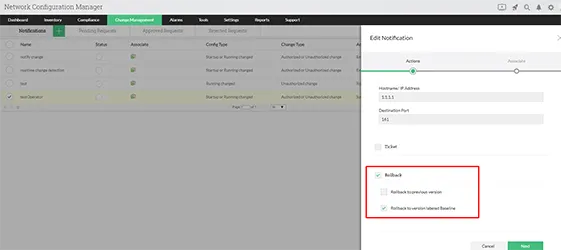
A network disaster caused by a misconfiguration can be fixed in the shortest time with configuration change management if the admin has a way to reverse the changes instantly. Rolling back the device to the previous configuration version or a stable/trusted version could help solve the problem. To help set up a rollback mechanism Network Configuration Manager has the option of labelling a trusted configuration version as 'baseline configuration'. During a network outage, the admin can revert changes that caused the disaster by restoring the device to its baseline configuration. Learn more about Configuration change management tool supporting rollback mechanism