Network Configuration Reports
Network configurations serve as the backbone of any network and demand vigilant management. A slight misconfiguration or error in the setup can lead to a cascading network failure.
In this scenario, real-time configuration reports are the lifeline for administrators to address any configuration-related issues proactively. Network Configuration Manager steps in to meet this requirement by offering six critical configuration reports. These reports empower administrators to effortlessly stay ahead of potential configuration challenges.
Types of configuration reports
- Startup-Running Conflict Report
- Configuration Changes Report
- Configuration Change Trend Report
- Configuration Change Annotation Report
- Configuration Analysis Report
- Security Audit Report
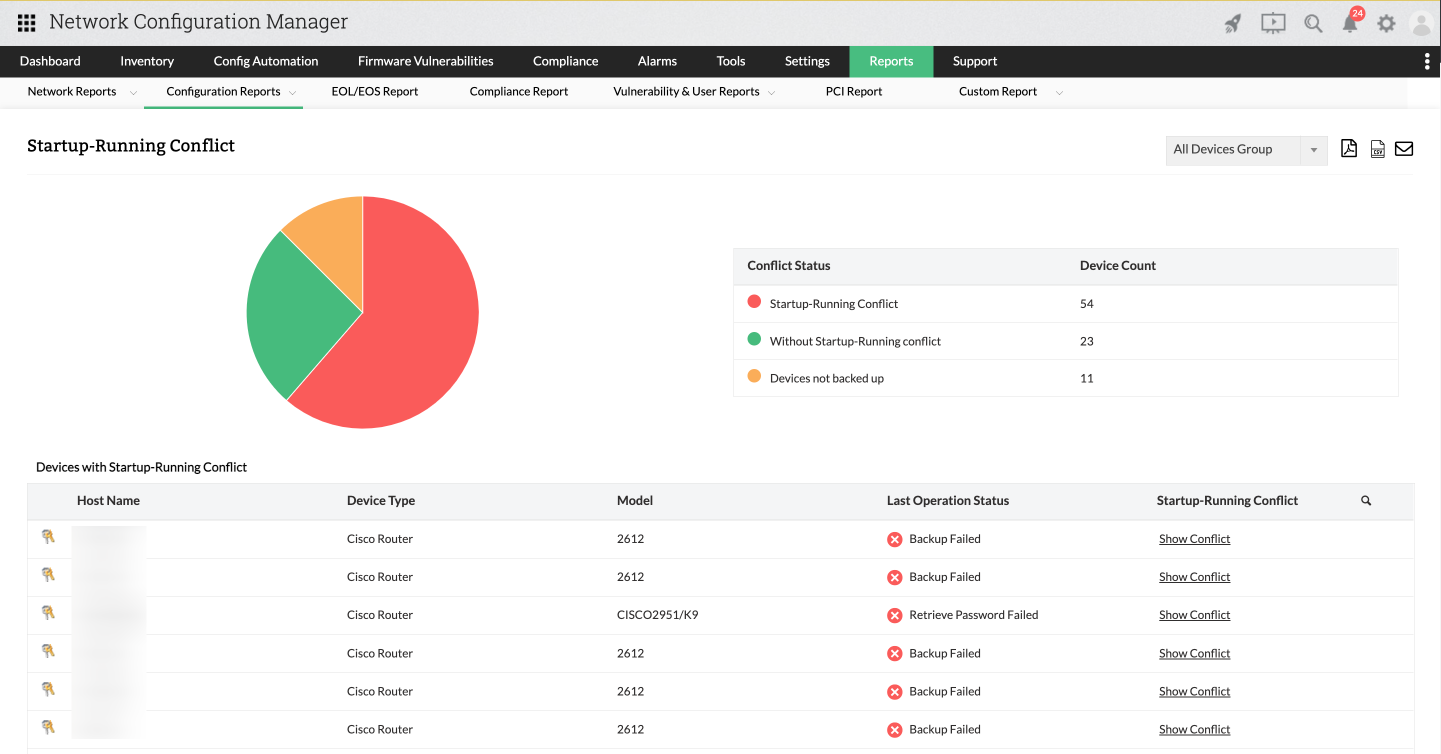
Startup-Running Conflict Report
A significant challenge in network infrastructures revolves around the potential conflict between startup and running configurations. This conflict has the potential to result in network disasters, because most changes are made to running configurations, which are stored in RAM. If an unexpected manual reboot or power failure occurs, all changes in the running configuration can be lost, leading to configuration conflicts that demand immediate attention.
This is where the Startup-Running Conflict Report comes into play. This report provides details about the number of conflicts, devices without conflicts, and devices that have not been backed up yet.
The report also includes information such as: the device's host name, device type, model, the status of the last operation, and a Show Conflict button that reveals conflicts using the Diff View feature.
Moreover, you have the flexibility to export this report in both PDF and CSV formats, or send it via email if necessary. Additionally, if you have organized device groups, you can view the report for a specific group of devices.
To access this report, navigate to Reports -> Locate and click Startup-Running Conflict Report within the Configuration Reports section.
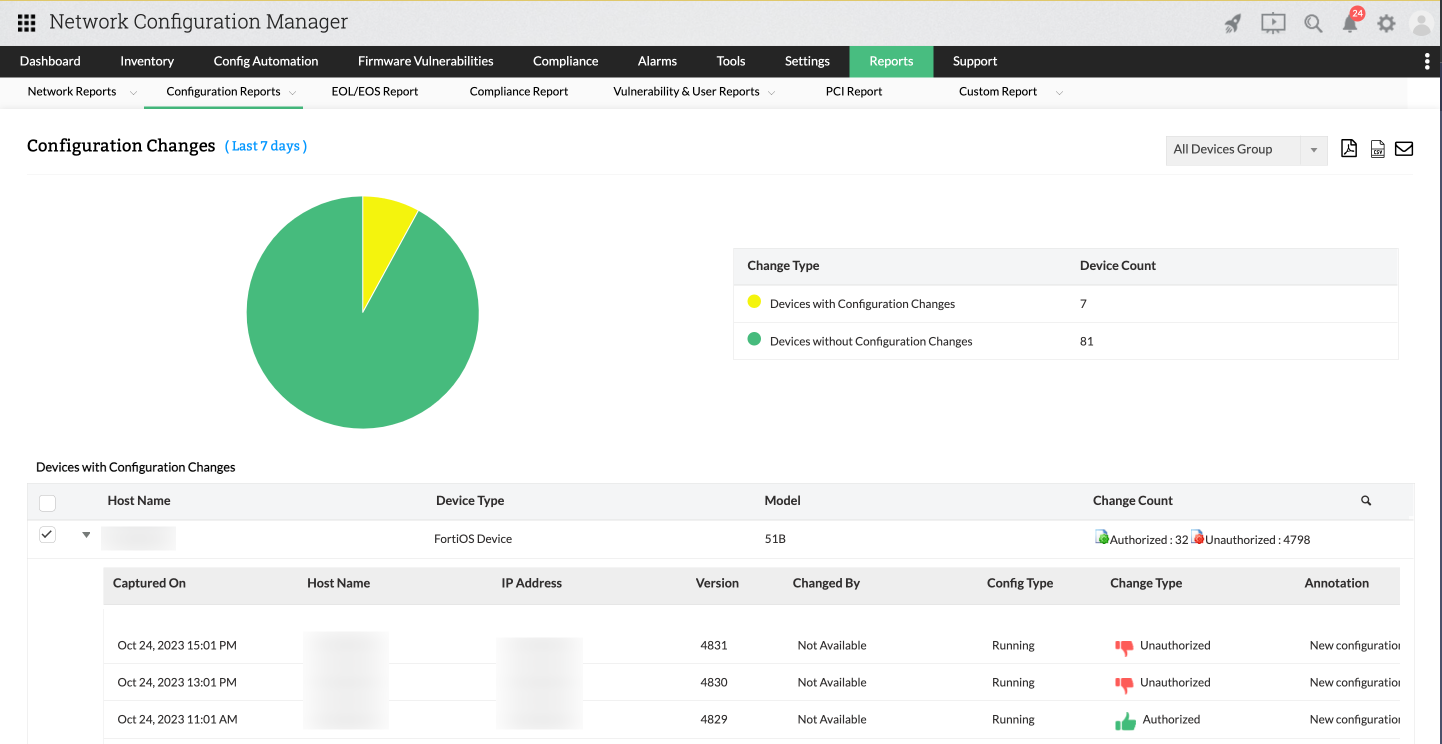
Configuration Changes Report
Effective configuration changes are pivotal for the seamless operation of any network infrastructure. Changes that are incorrectly implemented can have a profound impact, especially if unauthorized alterations find their way into the production environment and potentially cause catastrophic consequences for the organization.
Network Configuration Manager offers a Configuration Changes Report, granting you an overarching view of all configuration modifications occurring within your network. This capability allows you to intercept and prevent any unauthorized changes from progressing to production.
The report includes two sections: one highlighting devices with configuration changes, and the other focusing on devices without any alterations to their configurations. The Devices with Configuration Changes Report provides details such as the device's host name, type, model, and a breakdown of authorized and unauthorized changes.
For a more detailed examination, you can delve further into the report on devices with configuration changes. This section offers comprehensive information on both authorized and unauthorized changes. For instance, if there were 10 authorized and three unauthorized modifications, it specifies when they were recorded, which version was affected, who made the change, the type of configuration it pertains to, and a brief annotation. Clicking on the details directly navigates you to the corresponding version page.
The Devices without Configuration Changes Report presents the device's host name, type, model, and the status of the last operation performed.
Moreover, you have the flexibility to export this report in both PDF and CSV formats, or send it via email if necessary. Additionally, if you have organized device groups, you can view the report for a specific group of devices.
To access this report, navigate to Reports -> Locate and click Configuration Changes Report within the Configuration Reports section.
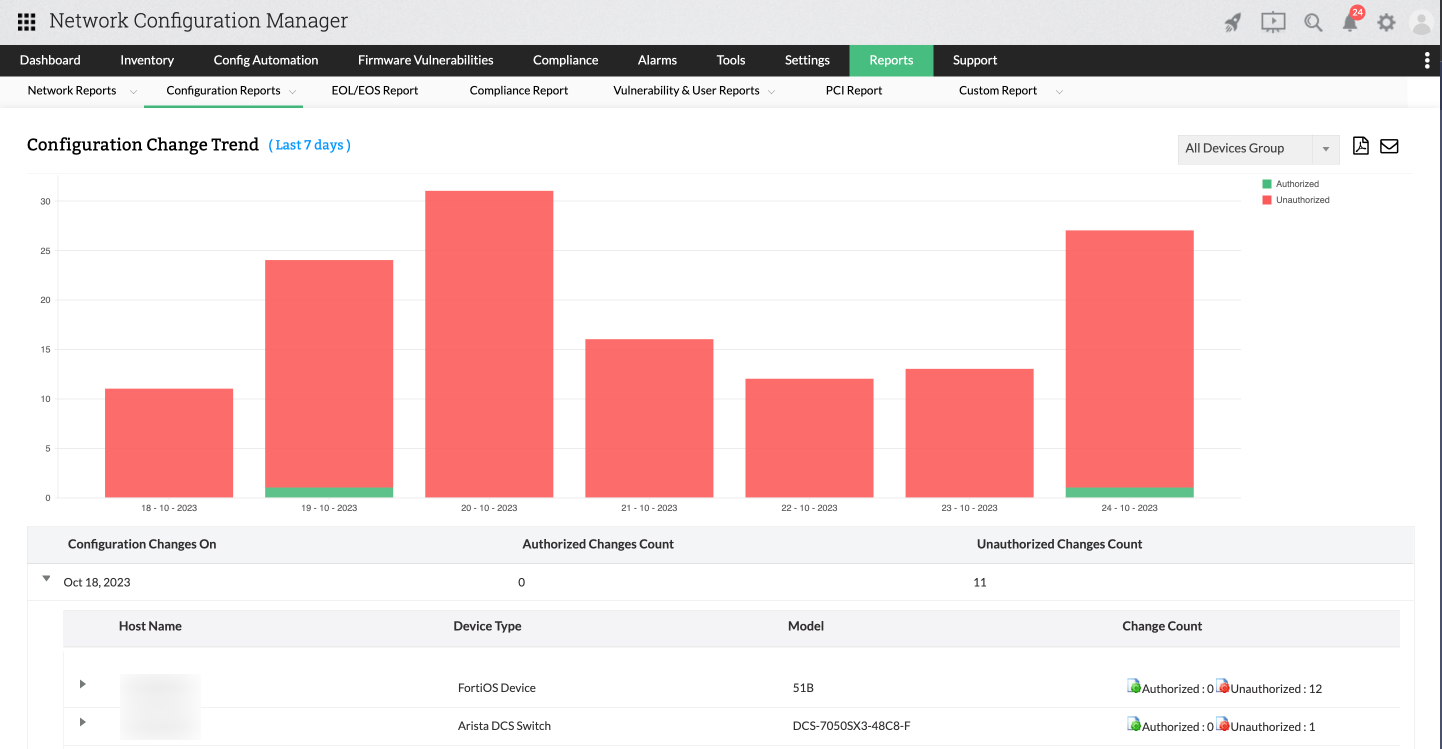
Configuration Change Trend Report
Another crucial element is keeping a record of the quantity and nature of configuration adjustments made within a specific timeframe. This information proves invaluable for administrators when conducting RCA.
The report offers a trend graph depicting changes made over the last seven days. It outlines the total number of modifications, distinguishing between authorized and unauthorized changes. This feature empowers administrators to enhance their change management capabilities.
Furthermore, the report itemizes the date of each configuration alteration, along with the amount of authorized and unauthorized changes.The report also provides additional details such as the host name, device type, model, and the corresponding counts of authorized and unauthorized changes for each device.
For example, if on October 18, 2023, the graph indicates 25 unauthorized changes and 25 authorized changes, administrators can delve into the specifics of which devices these alterations occurred in. Then, they can choose to drill down even further into the device to retrieve detailed information, including: when the change was recorded, who executed it, which configuration it affected, the version involved, and a brief annotation.
Moreover, you have the flexibility to export this report in a PDF format or send it via email if necessary. Additionally, if you have organized device groups, you can view the report for a specific group of devices.
To access this report, navigate to Reports -> Locate and click Configuration Change Trend Report within the Configuration Reports section.
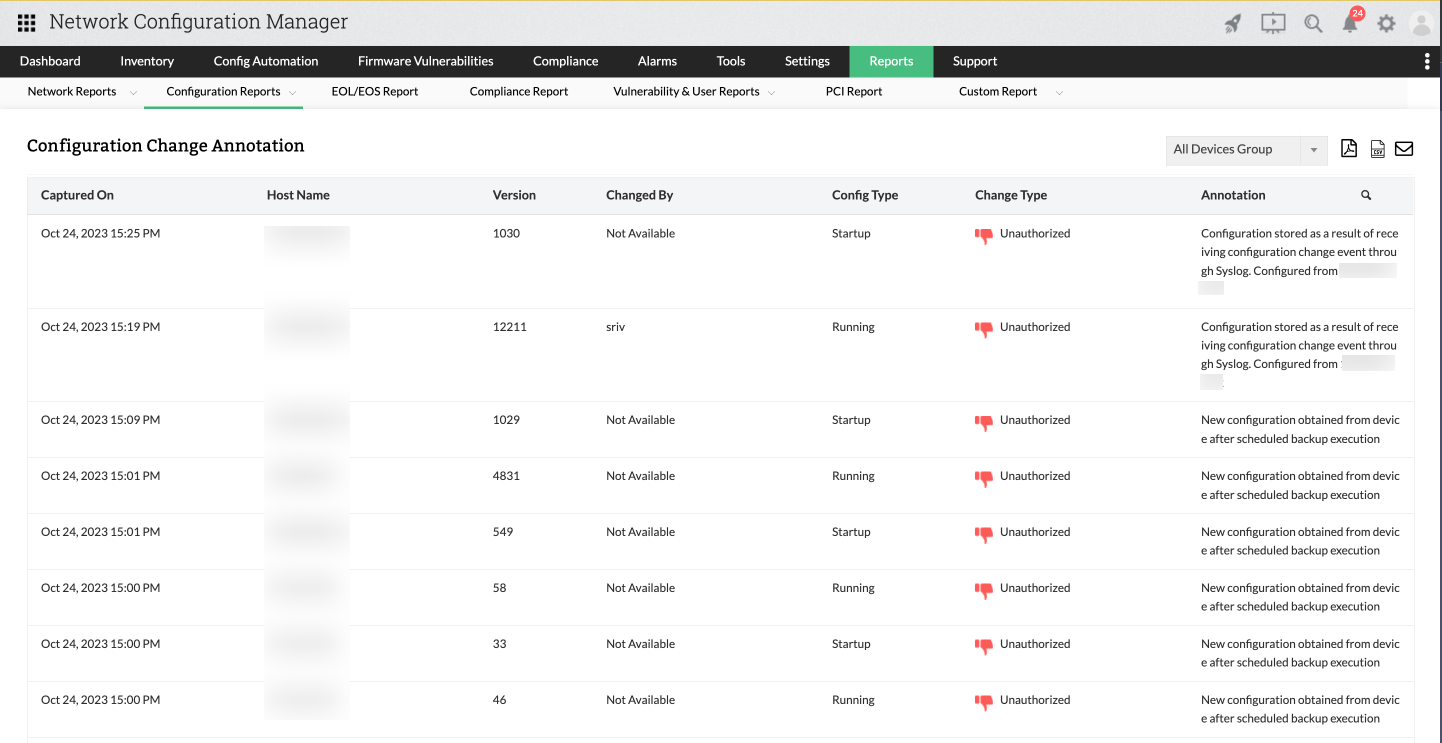
Configuration Change Annotation Report
Annotations serve as a pivotal element in network reports, offering administrators valuable insights into the purpose of a report or the processes within it. This significantly eases the workload for administrators and provides instant clarity on the objectives of each process.
This report fulfills this role precisely, cataloging device details that have undergone changes, organized by their respective annotations.
The report outlines the date and time of each recorded change, along with the device's hostname, the version in which the alteration occurred, the individual responsible for the change, the specific configuration involved, the classification of the change as either authorized or unauthorized, and an associated annotation. Clicking the details will seamlessly redirect you to the version page of the corresponding device.
Moreover, you have the flexibility to export this report in both PDF and CSV formats, or send it via email if necessary. Additionally, if you have organized device groups, you can view the report for a specific group of devices.
To access this report, navigate to Reports -> Locate and click Configuration Change Annotation Report within the Configuration Reports section.
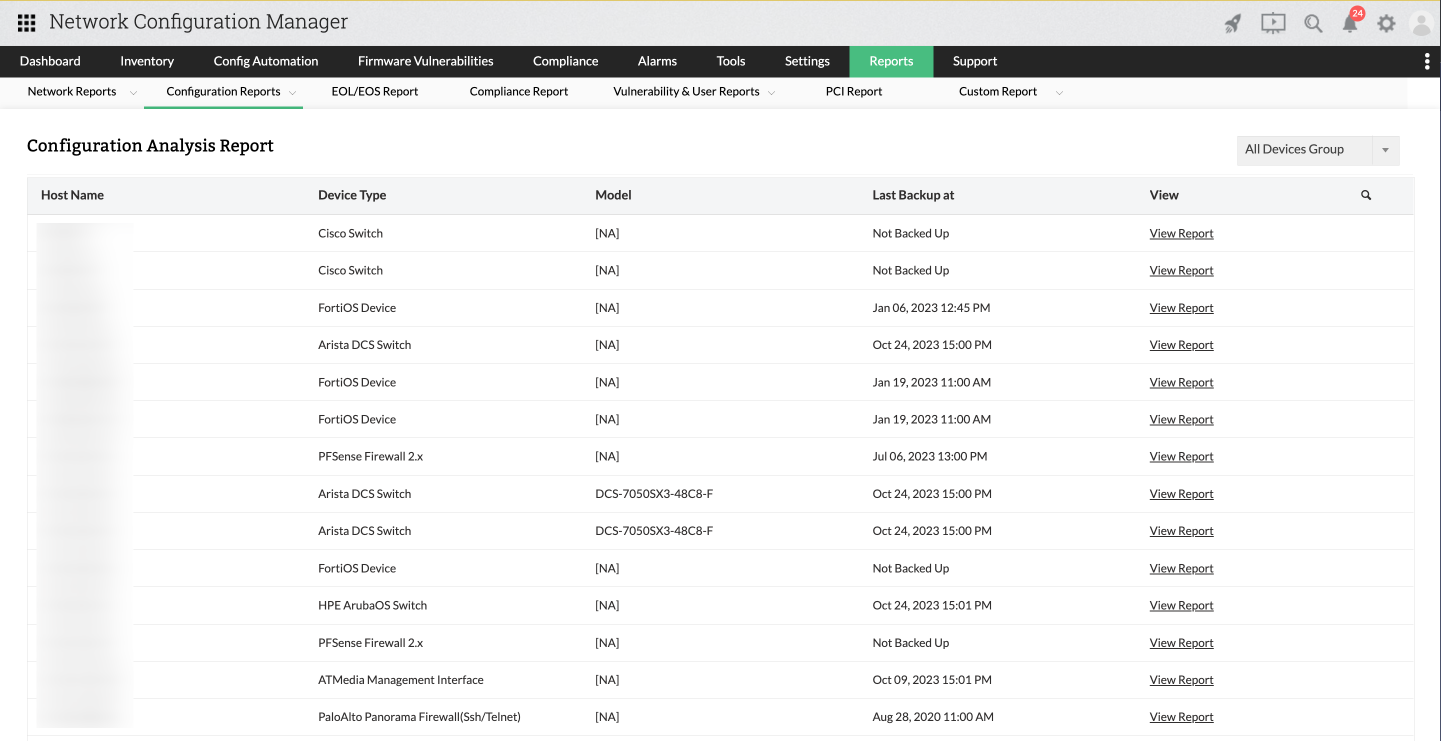
Configuration Analysis Report
It is crucial for administrators to have up-to-date information about the devices and their configurations, including both startup and running configurations.
This report fulfills this role by offering thorough details regarding device configuration settings, covering both startup and running configurations.
The report includes the device's host name, device type, model, the timestamp of the most recent backup, and a comprehensive report containing detailed information about the device's configuration settings.
Additionally, if you have organized device groups, you can view the report for a specific group of devices.
To access this report, navigate to Reports -> Locate and click on Configuration Analysis Report within the Configuration Reports section.
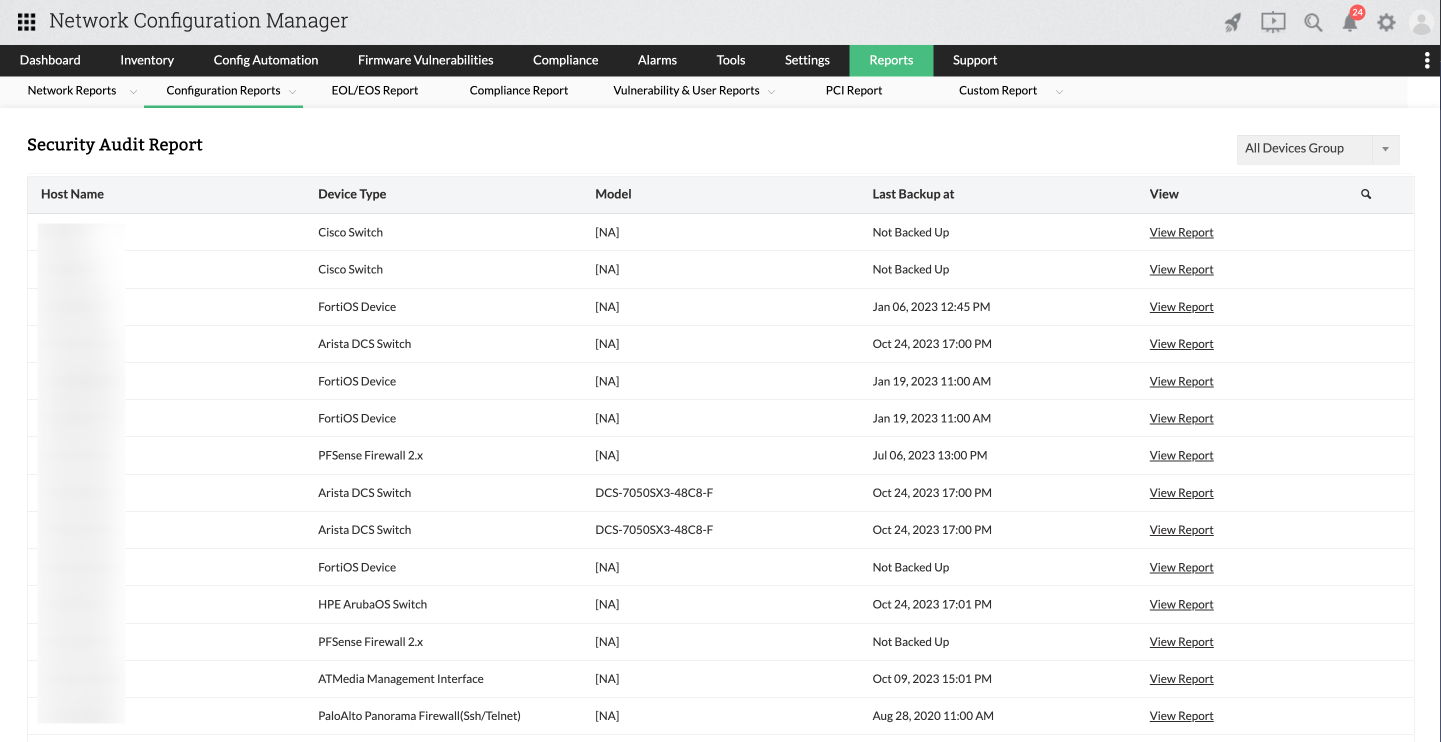
Security Audit Report
Conducting security audits on devices is a critical component of contemporary network management. However, in certain manual settings, auditing each of the potentially 1,000 devices can be extremely time-consuming, may lead to human errors and admins can potentially miss crucial elements in the process.
This report serves as a solution to this challenge by presenting the results of a security audit, complete with an evaluation of their impact and recommendations for rectification.
The report includes details such as the device's host name, device type, model, the timestamp of the most recent backup, and a comprehensive summary of the security audit data pertaining to the device.
Furthermore, if you have established device groups, you can view the report for a specific group of devices.
To access this report, navigate to Reports -> Locate and click Security Audit Report within the Configuration Reports section.
Download Network Configuration Manager now and enjoy these and various other kinds of reports and audits with a free, 30-day trial.
Want to see the reports in action? Request a free, personalized demo.
You can also get a price quote based on your usage and needs.