Network disaster recovery plan with Network Configuration Manager
A network disaster recovery plan is a set of policies to help you restore all your organization's network operations after a network disaster. A network disaster can range from performance degradation to complete network outage. While network disasters are often caused by human error, this page will list the common sources of network disasters, and how Network Configuration Manager acts as a network disaster recovery tool and helps solve them.
1. Network disaster due to bandwidth hogs
Organizations often invest a lot of money into acquiring large amounts of bandwidth that is shared by every user on the network. When a single user disproportionately consumes a lot of bandwidth on a typical network, it can affect the entire network. Situations like these lead to other users on the network experience lag, causing performance degradation.
Network disaster recovery plan to fix bandwidth hogs
This network disaster recovery can be done by capping bandwidth consumption using access control list (ACL) configlets in Network Configuration Manager. With these configlets, you can use limiters to restrict certain users' bandwidth or choose to block their access to the network entirely.
2. Network disaster due to violation of industry standards
The network industry has laid out certain industry standards like CIS, SOX, and HIPAA. Each of these standards have a specific set of rules that your organization must comply with. Violating any of these rules could easily cause a network vulnerability that leads to a network disaster.
Network disaster recovery plan to fix compliance violations
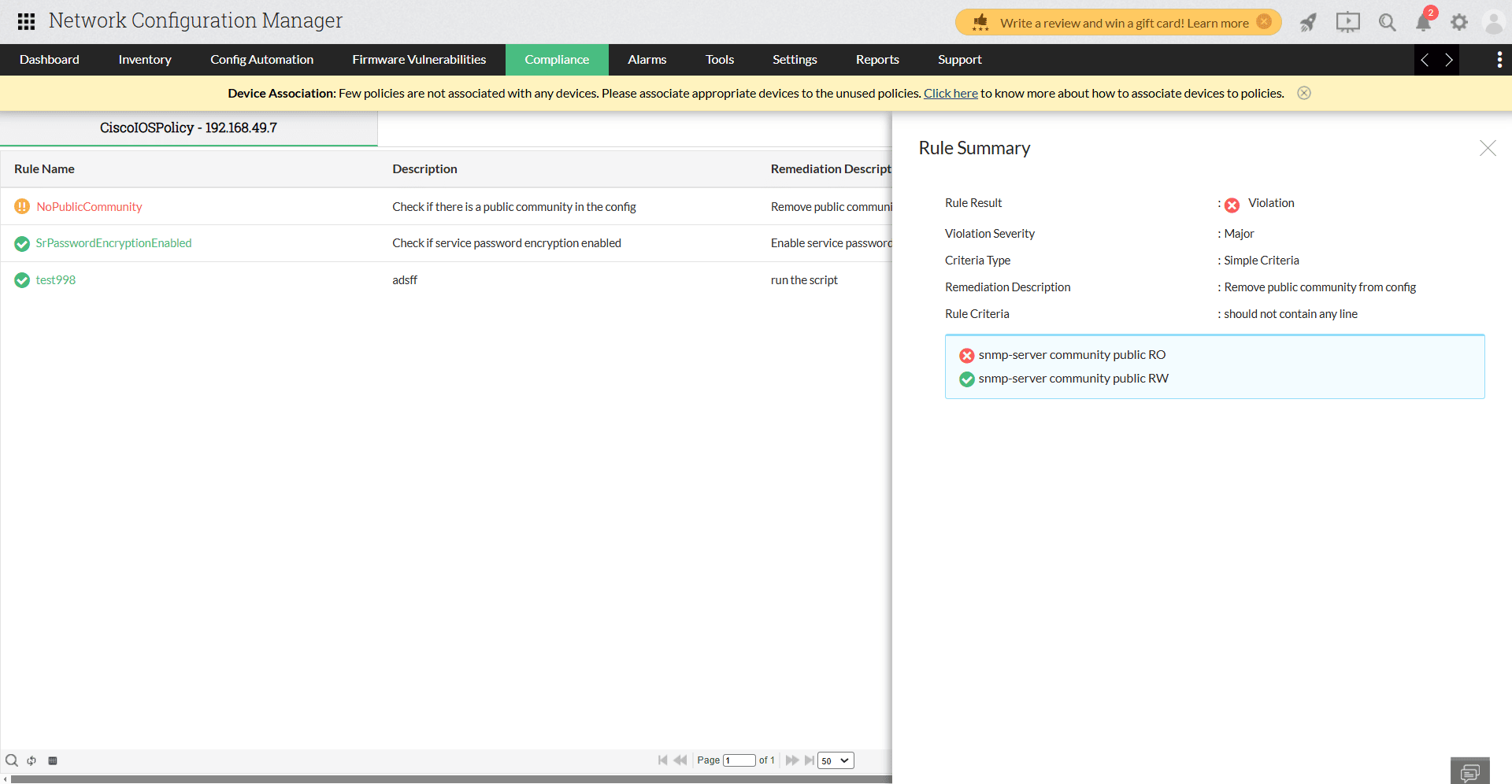
Let's take the example of a company using TELNET. TELNET is a communication protocol that the network industry has recommended not to use due to security concerns. All communication that happens via TELNET is unencrypted, which can lead to a data breach. By executing configlets on Network Configuration Manager, you can check whether TELNET has been enabled. If the protocol is enabled, Network Configuration Manager automatically notifies the admin so that the violation can be remediated. Network Configuration Manager also speeds up the remediation process by allowing each compliance rule to be associated with a remediation configlet. The admin can instantly fix violations by executing a remediation configlet.
3. Network disaster due to faulty configuration changes
Network infrastructures are prone to human errors since they are subject to frequent manual changes. Such errors can cause vulnerabilities in the network that lead to network disasters. Shutting down interfaces is one such common error. Users shutting down an interface can render a group of devices inaccessible to everyone on the network.
Network disaster recovery plan to fix faulty configuration changes
Moderation of network infrastructure changes can be achieved through role-based access control and change notifications in Network Configuration Manager. With a role-based access control, every user is assigned a role which will define the devices they can access. With Network Configuration Manager you can assign operator or admin roles to users. While admins have access to all devices in the network, operators will have to make a request to the admin each time they try to change a configuration. Once a change is processed, the operator receives a notification of the status of the configuration upload.
Network Configuration Manager also has a rollback mechanism to undo any configuration changes that disrupt network performance. The rollback mechanism helps you maintain business continuity.
4. Network disaster due to loss of configuration changes
While network admins frequently make changes to network devices, it's important that each change is also applied to the startup configuration of the device. If not, this disparity will lead to a startup-running configuration conflict, and the changes will be lost when the device turns off. In cases where these changes are mission-critical or security-related, losses can lead to network disasters.
Network disaster recovery plan to prevent loss of configuration changes
Network Configuration Manager gives admins a unified look into all the devices that have a startup-running conflict. These conflicts can be remediated by using Network Configuration Manager to sync the startup and running configuration of the devices. Admins can also choose to schedule configuration syncs to occur monthly, weekly, daily, or just once.
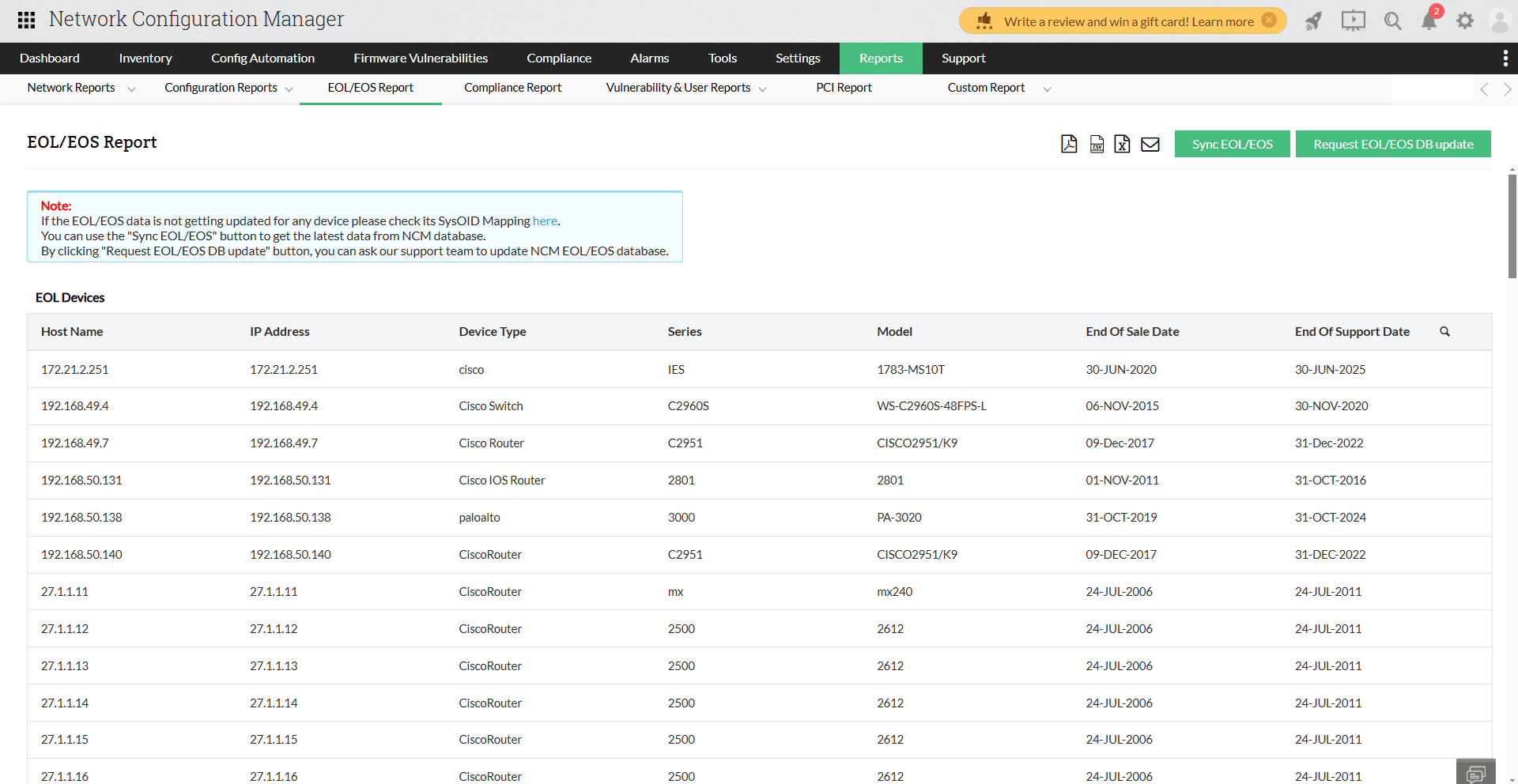
5. Network disaster due to hardware failure
A hardware failure can cause as much damage to a network as a misconfiguration. Regularly checking your hardware components is crucial to your network's continual function. End of sale, end of support, and end of life must be checked frequently. Any device that's being used beyond its EOL/EOS has a higher risk of malfunctioning or failing.
Network disaster recovery plan in case of a hardware failure
Network Configuration Manager can help in network recovery with a repository of device configuration backups. This repository is built over time through scheduled, automated, and manual backups. Whenever there's a network outage due to hardware failure, you can replace the failed device with an identical one, then upload the failed device's configuration from the repository. This will quickly restore all network functions.
Network disaster recovery plan template:
An efficient network disaster recovery plan should have the following things in place to ensure efficient recovery for all your network functions:
1. Backup: Take regular network backups using a network disaster recovery system so that you have a repository of trusted versions of device configurations.
2. Role based access control: Assign user roles to make sure no unauthorized changes or configuration uploads are made to your network devices.
3. Change rollback: Implement a rollback mechanism to a trusted version so that you can quickly restore your network when there's a misconfiguration.
4. Compliance: Conduct regular compliance audits to ensure you adhere to industry standards and enhance your network's security.
5. Configlets: Implement the use of configlets (executable configuration templates) to execute configuration tasks in bulk.
Why ManageEngine's Network Configuration Manager is an ideal network disaster recovery tool
ManageEngine's Network Configuration Manager (NCM) is a powerful solution designed for organizations to streamline network configuration management and strengthen disaster recovery processes. Its advanced features and user-focused design make it a dependable choice for ensuring business continuity during unexpected network disruptions.
Automated and secure configuration backups
NCM simplifies disaster recovery by enabling automatic and on-demand configuration backups for all network devices. These backups ensure that the latest configurations are always available, reducing downtime and simplifying the restoration process. The ability to schedule backups and store them securely minimizes the risk of losing critical configuration settings in case of unexpected events.
Real-time change monitoring and alerts
A unique aspect of NCM is its ability to track configuration changes in real-time. It immediately notifies administrators of unauthorized modifications, allowing them to take corrective actions swiftly. This proactive monitoring reduces the likelihood of configuration errors escalating into major network issues.
Enhanced compliance and security
NCM includes built-in tools to check network configurations against industry regulations and internal policies. This ensures that all devices are compliant and secure, reducing vulnerabilities that could compromise recovery efforts. Regular compliance audits and detailed reports offer insights into any deviations, helping teams address them promptly.
Firmware management for risk mitigation
The tool identifies devices with outdated or vulnerable firmware, offering insights into potential security risks. NCM provides detailed vulnerability information and links to patches, enabling quick remediation. This feature ensures that devices are up-to-date and less susceptible to threats, enhancing overall network resilience.
Role-based access for configuration control
To maintain strict security during disaster recovery, NCM enforces role-based access control. This limits access to configurations based on user roles, ensuring that only authorized personnel can perform changes. This approach prevents unauthorized or accidental modifications during recovery.
Streamlined recovery with automation
ManageEngine’s NCM incorporates "configlets," reusable scripts that automate configuration tasks across multiple devices. These scripts allow administrators to apply updates quickly, rollback changes, or standardize configurations during recovery. Automation significantly reduces manual errors and speeds up the process of bringing the network back online.
What sets network configuration manager apart?
Unlike other tools, NCM integrates all essential features—automated backups, compliance checks, vulnerability management, and automation—into one cohesive platform. Its user-friendly interface, detailed reports, and real-time alerts provide complete visibility and control over network configurations. This makes it not only a disaster recovery tool but also a comprehensive solution for ongoing network configuration management.
By combining automation, security, and proactive monitoring, ManageEngine's Network Configuration Manager empowers organizations to recover from disruptions quickly and maintain uninterrupted network operations. It ensures that your network is prepared for the unexpected, minimizing downtime and protecting critical business services.
Ready to secure your network from disasters? Try Network Configuration Manager for free, or get a free personalized demo today, and get started in a few minutes.