Firmware vulnerability insights
Overlooking network firmware vulnerabilities can make it easy for unauthorized users and data thieves to get their hands on critical data. It is essential to run periodic vulnerability checks to ensure your network is free from loopholes.
Network Configuration Manager imports the firmware vulnerability listings provided by National Institute of Standards and Technology (NIST), and maintains an updated DB of all the vulnerabilities in your network. It also provides suitable remediation for all the vulnerabilities.
Learn about firmware vulnerability to identify potential network threats and fix them.
Dashboard
Network Configuration Manager provides you with a consolidated view of the status of all the firmware vulnerabilities and affected devices in the form of dashboard widgets. These widgets contain colorful graphs, charts, trends and more to help you identify all you need to know about your network vulnerabilities at one glance. This can be beneficial as you can take immediate actions based on the insights received from these widgets. Now let us see in detail about firmware vulnerability dashboard widgets!
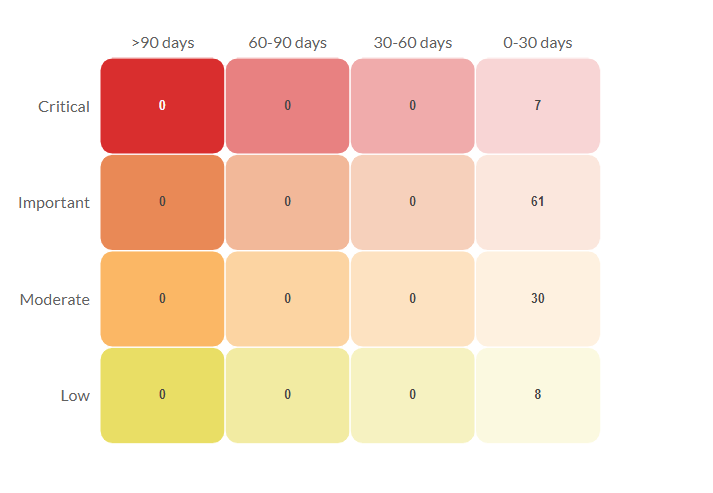
Vulnerability age matrix
This dashboard widget provides a view to help you understand the age and severity of all the discovered vulnerabilities. While X-axis provides the time denoting the age of a vulnerability (The time from its first discovery to present), the Y-axis shows its severity mapping such as "Critical", "Important", "Moderate" and "Low". This can be useful in identifying the vulnerabilities which require immediate attention (Eg: A critical vulnerability that has not been fixed for a long time).
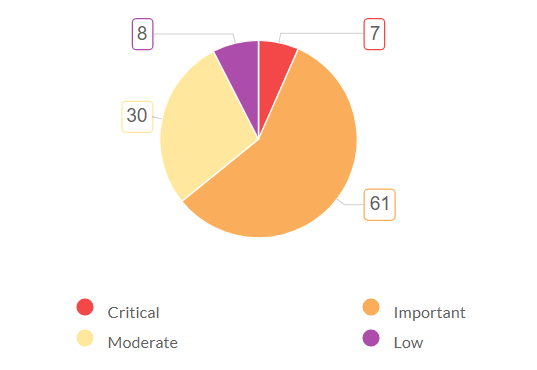
Vulnerability severity summary
This shows the vulnerabilities categorized based on their severity, plotted in the form of a pie chart. You will be able to see the count of vulnerabilities that fall under a particular severity.
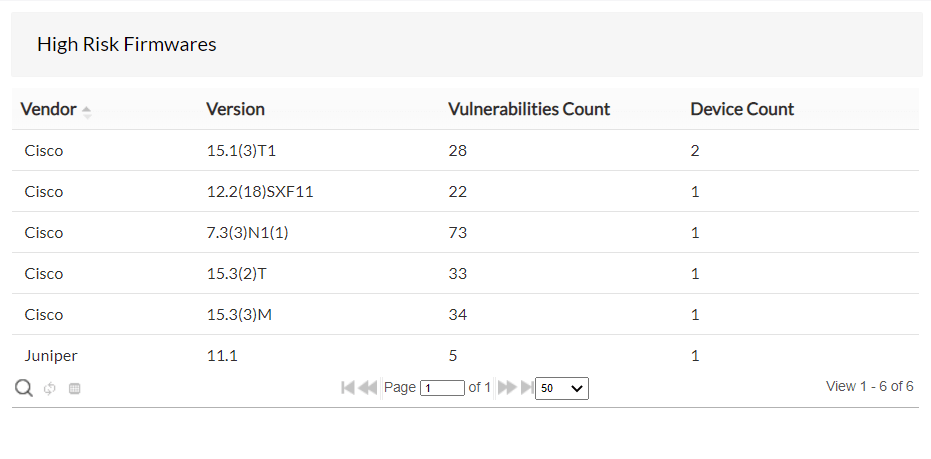
High-risk firmware
This shows the count of vulnerable devices grouped based on their firmware version. This can help you identify all the vulnerabilities and the vulnerable devices that fall under a particular firmware version. Critical and important severities are considerd as high-risk vulnerabilities.
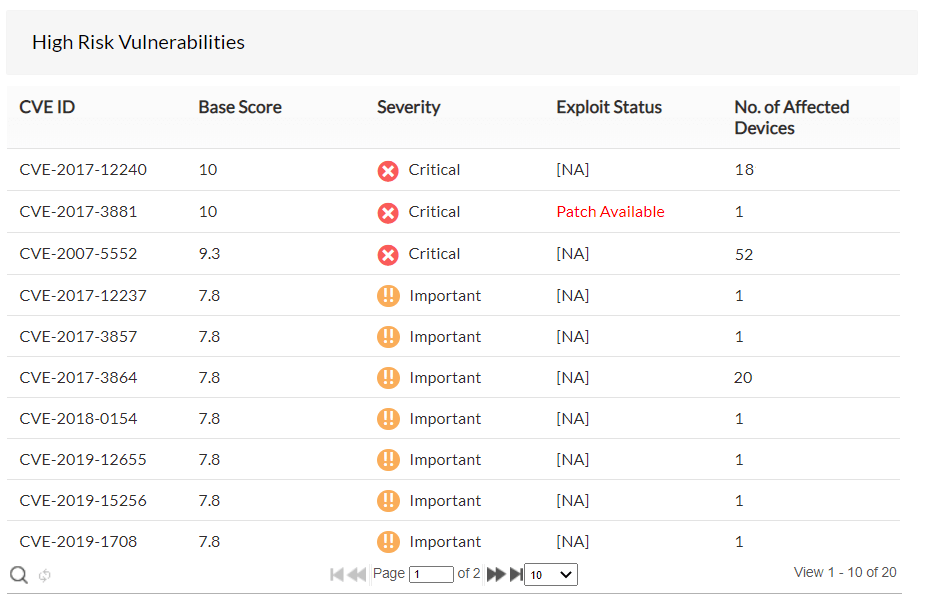
High-risk vulnerabilities
All the vulnerabilities that fall under the severity criteria - Critical and Important are listed in this view, which are considered as high-risk vulnerabilities. This gives you an idea of all the vulnerabilities that are in a critical status and can help you take immediate remediation action.
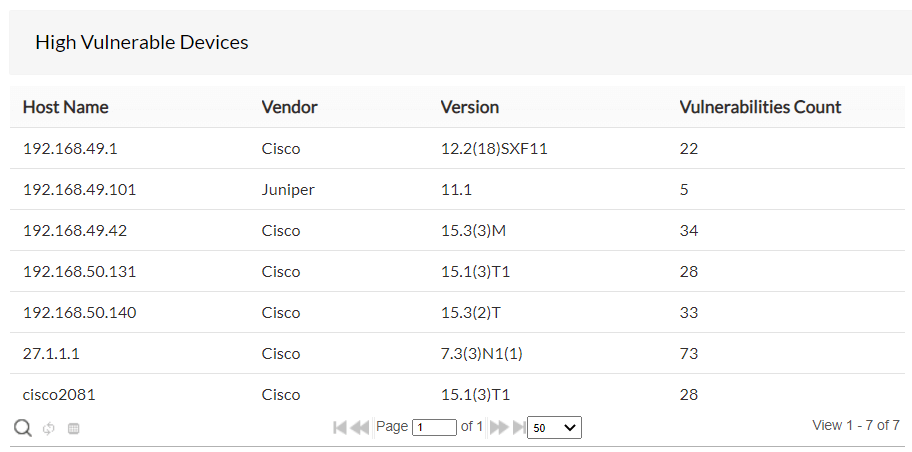
High vulnerable devices
All the vulnerable devices that fall under the severity criteria - Critical and Important are listed in this view, which fall under high-risk vulnerabilities . This helps you identify the device that need immediate remediation/patch.
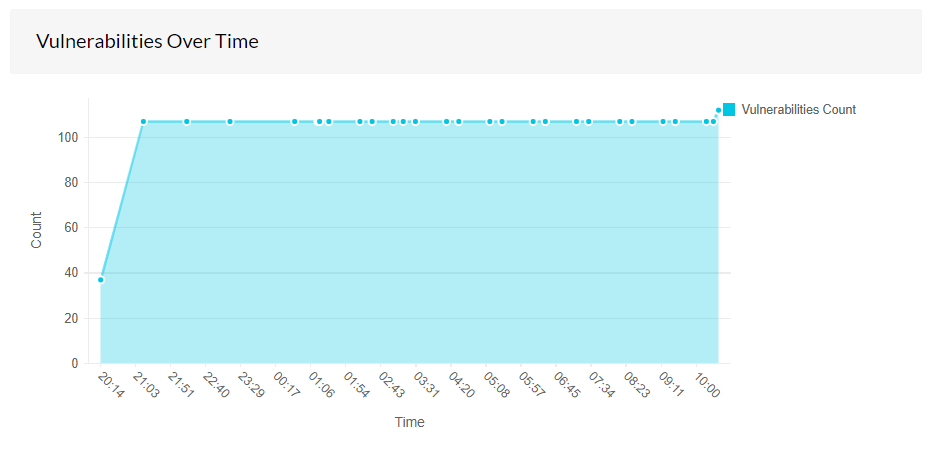
Vulnerabilities over time
This view shows the progress of the vulnerabilities over time from the day it is first reported in your network. This graph shows whether the vulnerability count increases or decreases over a particular time. If more number of vulnerabilities are fixed, the line will project downwards, if vulnerabilities are not fixed but if no new vulnerability is reported, the graph will show a steady line. However, if vulnerabilities are not fixed and new vulnerabilities are reported, the line will project upwards.