Network Compliance Reporting
With network security threats increasing everyday, businesses need to ensure that they follow strict protocols to protect their data. The network industry has also set certain regulatory standards to overcome such threats. However, the task of manually ensuring these standards is time-consuming and prone to errors. A compliance monitoring and reporting tool can automate the entire process to help you get audit ready. With network audit reports showing you the compliance status of individual network devices, you get complete visibility into your network.
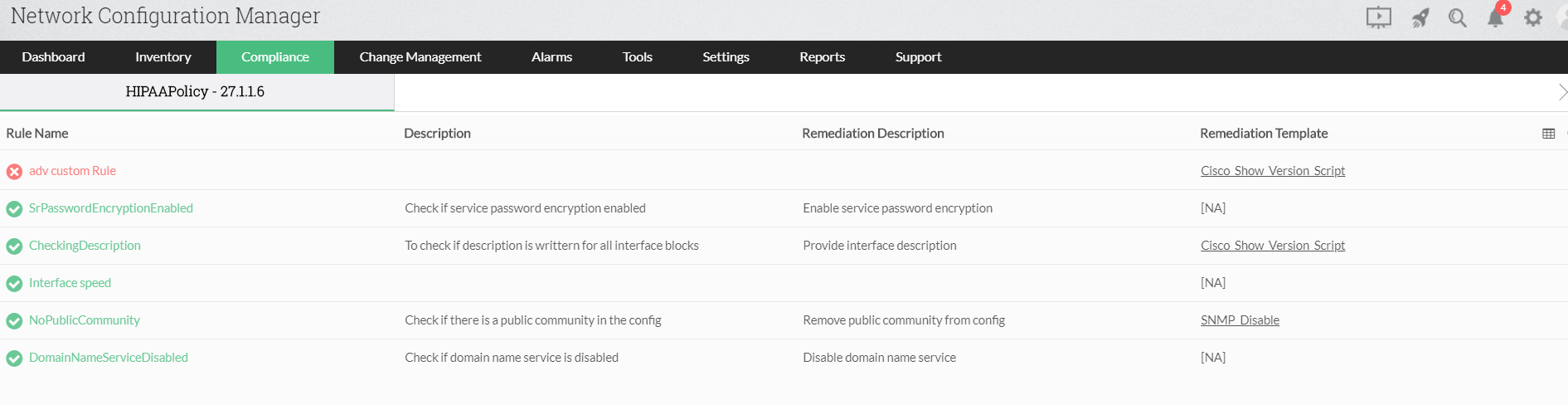
Compliance check with Network Configuration Manager
In a multi-user network environment where several changes are made to the configurations in parallel, there is a high probability of manual errors. In the process of changing a configuration, a network admin can mistakenly render the network vulnerable to attacks. Network Configuration Manager, in addition to the default compliance policies like CIS, SOX, and HIPAA, allows the user to create custom compliance policies. Custom compliance policies can be used to ensure the network matches the internal regulations of the organization. Network admins can choose to manually run compliance checks or schedule them to run whenever necessary. Compliance reports are generated after every compliance check which can be exported to CSV or PDF formats.
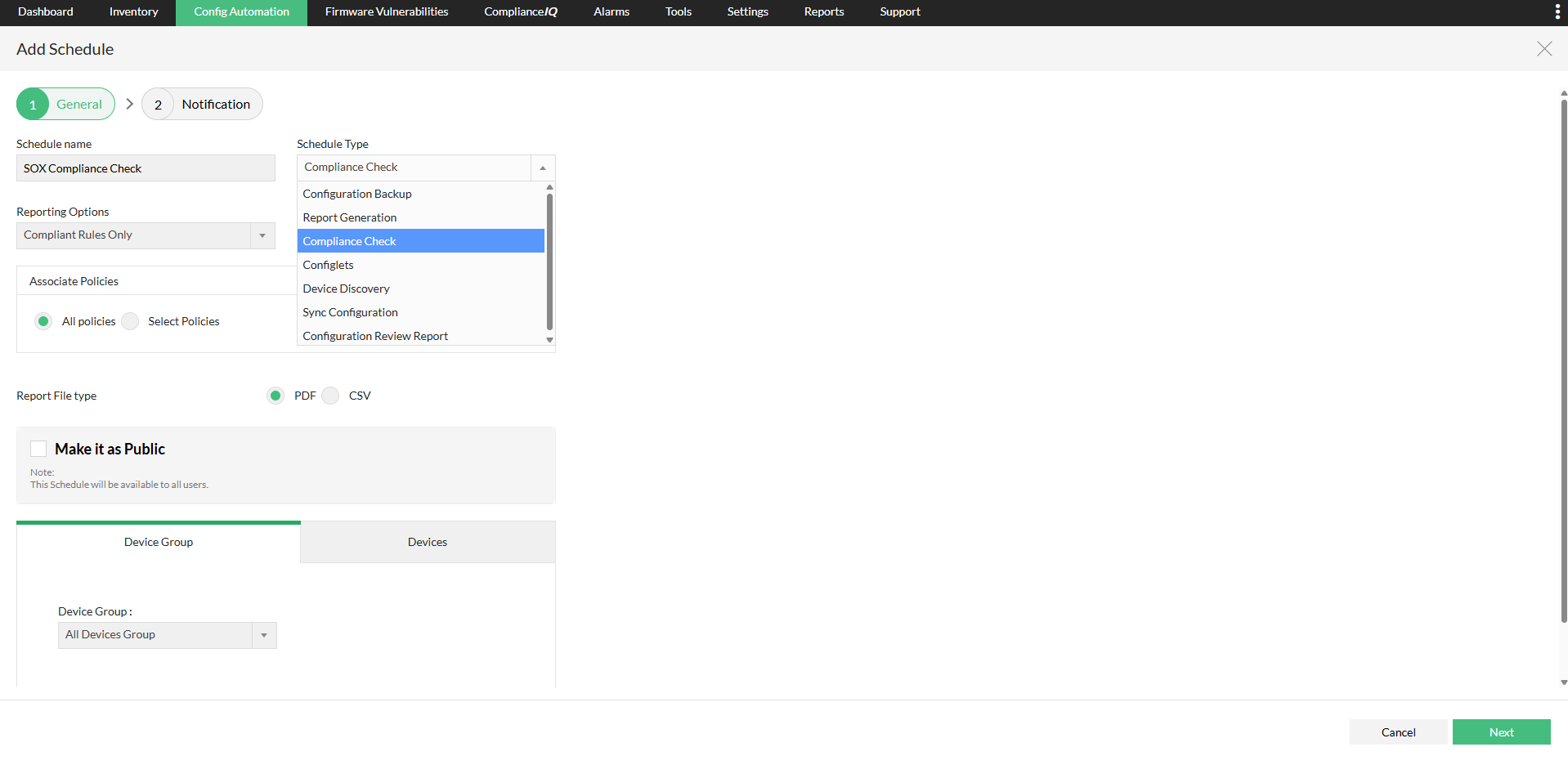
Compliance report scheduling
As configurations are frequently modified, compliance checks have to be repeatedly run to check if the changes are in accordance to the compliance standards. Every time the configurations are modified, there is a possibility that the changes applied could violate the compliance rules. If the number of times the configurations are changed every day is high, manually running compliance checks would be time-consuming. Network Configuration Manager simplifies this task with the option to schedule compliance checks and generating reports for specific devices or device groups. You can set the compliance checks to run hourly, daily, weekly, monthly or just once. While scheduling the reports, you can choose between generating the reports for all rules, compliant rules or violated rules. You can also enable the option to receive notifications after the compliance check only if there is a policy violation.
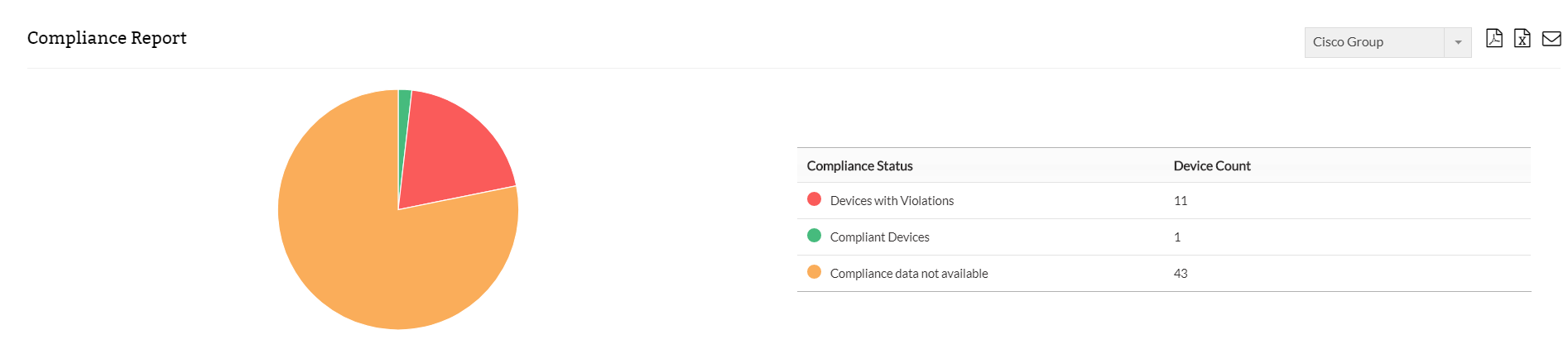
Compliance reports in Network Configuration Manager
The compliance snapshots in the reports contain a graphical summary of the compliance status of the devices/device groups in question. The detailed section in the reports show you the rules that have been violated the devices/device groups that are in violation. The admin has the option to classify violations based on their severity. Based on the organizations security policy, each rule violation can be a warning, major or critical. The reports also contain descriptions for each violation.
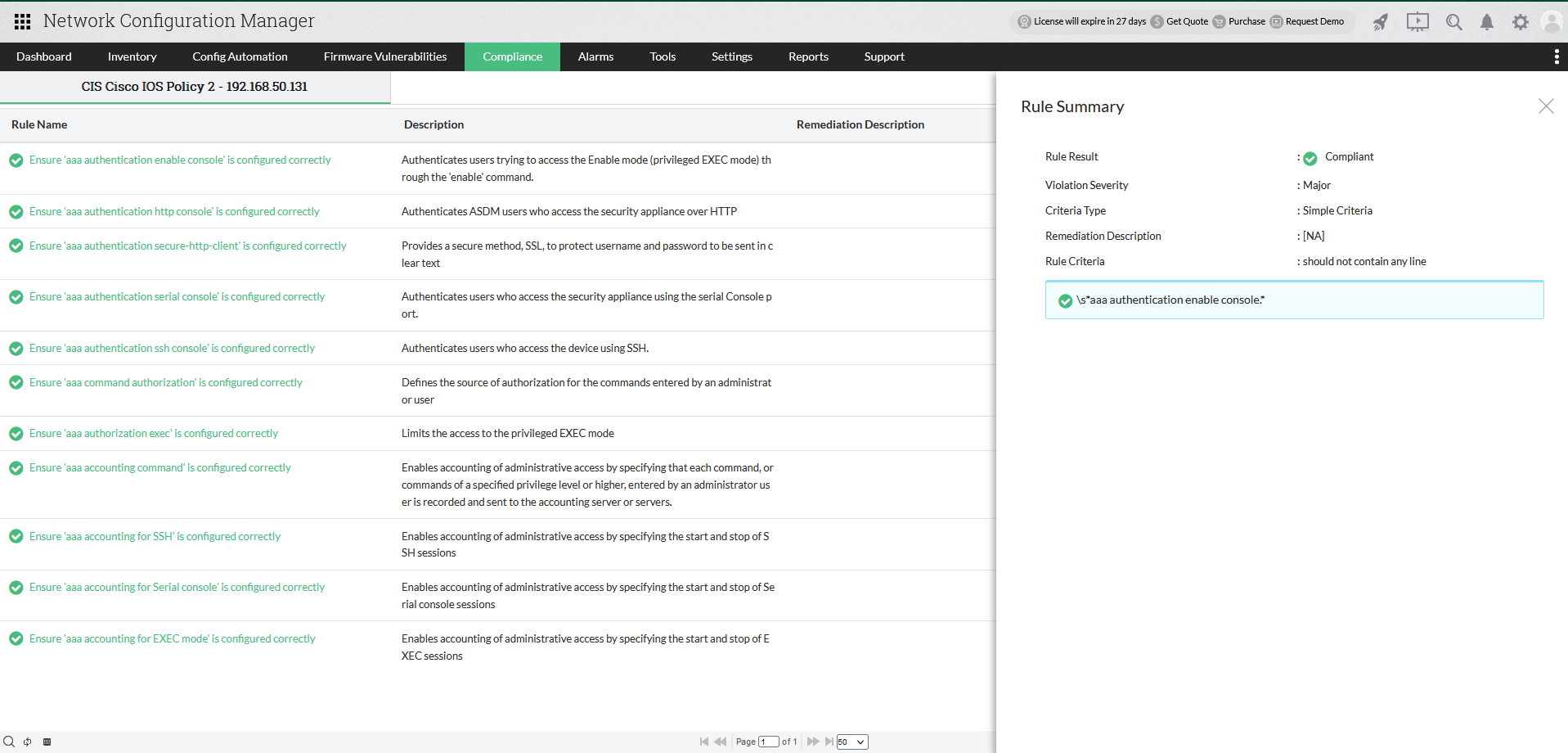
Compliance reports also show a detailed view of the compliance status of every rule under each compliance policy. The view contains the rule compliance result, violation severity, rule criteria and description of the remedial action that must be taken to fix the violation. The rule also shows the compliance status of the configuration strings that have been checked.
Fixing violations using compliance reports
Besides running compliance checks and generating reports, Network Configuration Manager helps fix rule violations. Since manually fixing these violations would be time-consuming the tool helps you achieve compliance using configlets. Each compliance rule can be associated to a configlet - executable configuration templates. On detecting compliance violations, they can be remediated by executing the rule's corresponding configlet directly from the compliance reports and achieve complete network compliance.