Network validation
Networks, before automation, were handled or maintained manually. Because of this, admins had great management overhead and found it difficult to validate networks based on their outcome or business objective—their intent. Also, many admins did not feel the importance of network validation at that time, which led to many disastrous network mishaps.
Nowadays, networks have become more complex and near-to-impossible to handle manually. This has paved the way for network automation using network automation tools, which has greatly minimized the percentage of network mishaps worldwide.
Now, to further minimize network-related disasters, network validation has been introduced, which combined with automation provides the smoothest network process for your network infrastructure.
Network validation is the process of inspecting whether your network environment is working or functioning as per the intent required. Network validation starts from physical connectivity and includes the protocol stack. Here, each layer of network architecture is validated according to its intent.
The first step of network validation is getting to know the exact intent of the network. Once the intent is finalized, then we can proceed with the network validation for the finalized intent. There are many sources through which intent can be known:
- Intent from network configurations
- Business or enterprise intent
- Security-based intent
Disadvantages of not performing network validation in today's network world
- It will be unclear whether the network is working as intended and is healthy.
- Any unauthorized or unnecessary changes can be implemented in the network environment without proper validation.
- There will be routing problems, where unnecessary routes will exist that eventually lead to downtime.
- The network environment will be insecure and open to malicious attacks.
Benefits for enterprises when using network validation
Network validation is similar to pre-flight checks, where there are standard checks done before take-off and landing. Some of the benefits of network validation include:
- Changes in your network environment will not be pushed for publishing without an admin's consent.
- Unwanted mishaps to the network infrastructure will no longer take place since the exact network intent is known.
- There will be well-planned routing paths in your network environment.
- The security of your network infrastructure will be improved, as every step is proceeded with intent and validation.
The what, when, and how of network validation
Network validation has three The what of network validation consists of three levels which determine protection. The When of network validation also contains three levels of when a validation should be done. The how of network validation tells us about the approach of network validation. Let us know in detail about these three criteria:
- What should be the level of validation?
- When must validation be performed?
- How is validation performed?
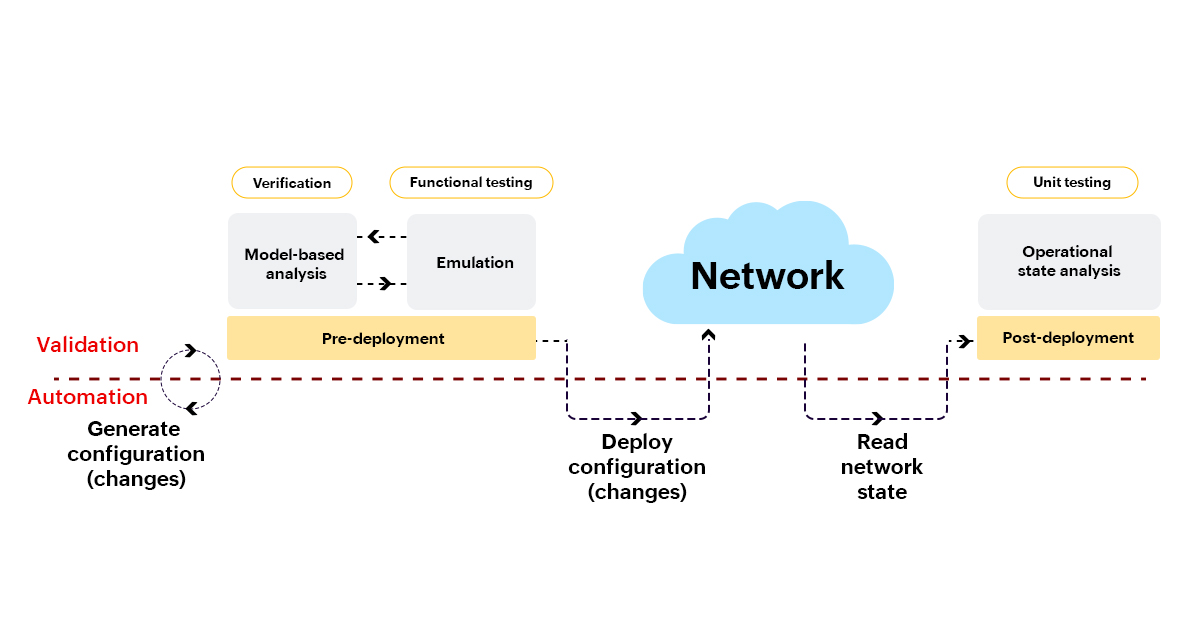
What should be the level of validation?
A basic network validation has three levels:
- Verification
- Functional testing
- Unit testing
Verification
Verification is the starting step of network validation and it is done to ensure that all the network process scenarios in your network infrastructure are correct. Some of the important aspects that are covered during verification are whether DNS packets are reaching DNS server, which routing paths are specified, and the availability of services after failure.
Functional testing
Functional testing is used to check for network behaviors to see whether they are working as intended from end to end. This can include confirming that routers are using the correct routing protocols and path, packets are correctly reaching servers without interruption, and the network traffic is using the intended backup paths if it is blocked.
Unit testing
Unit testing is used to inspect various aspects of the devices present in the network, such as whether they have correct configurations, accurate ASN, and more. This form of validation is a simple and effective testing method where the root cause is identified immediately whenever the test process fails. However, with unit testing you will not have a clear picture of end-to-end processes.
When must validation be performed?
Network validation is performed in three stages:
- Pre-deployment
- Deployment
- Post-deployment
Pre-deployment
Pre-deployment validation is before any changes (new or modified) are pushed to your network infrastructure. Here, all the changes to be pushed are verified thoroughly before full deployment, keeping the intended network operations in mind.
Deployment
Here, the new changes are implemented after a thorough pre-deployment stage. Deployment won't occur until all the pre-deployment validations are completed.
Post-deployment
After deployment is complete, another validation check is made to confirm whether the deployment had its intended impact. This method does not fully stop errors, but it will help stabilize the production from disastrous mishaps.
How is validation performed?
There are three approaches for network validation:
- Model-based analysis
- Emulation
- Operational state analysis
Model-based analysis
Model-based analysis is an approach that depicts the behaviour of networks in a range of scenarios using particular configurations. This method is used via simulation as well as abstract mathematics. Model-based analysis is the only reliable approach to perform verifications, but it can also present slightly inaccurate verification at times.
Emulation
Emulation is a test bed for network engineers to use for safely deploying and checking configurations. This approach is useful for predicting how a network environment will behave, as long as it consists of production software similar to emulated environments.
Operational state analysis
Operational state analysis is when network engineers push changes to network configurations and check whether they work with the intended purpose, such as if newly configured router configuration has made any intended process. The main advantage of this approach is that it checks the behavior of entire networks. However, since it supports only post-hoc validation, there is a higher chance of leakage in your network.
ManageEngine Network Configuration Manager: Your all-in-one network validation software
- Validate important configurations and back them up to use during sudden downtime.
- Manage changes in real time using validation features such as change notifications, role-based access control, labelling configurations, and Diff View.
- Push changes with automation script templates (pre-deployment), execute the template (deployment), and then receive timely reports from Network Configuration Manager that help you check on network configurations (post-deployment).
- Manage compliance effortlessly, with PCI, SOX, and HIPAA provided as default. This saves your network environment from malicious threats.
- Protect your devices' firmware from outside vulnerabilities by applying download patches from the link provided. It also lists the devices that are currently vulnerable, along with the CVE ID and severity level.
Download Network Configuration Manager and handle network validation with ease.
Curious about pricing? Get a personalized price quote according to your requirements.
Want to learn more about Network Configuration Manager's features? Try scheduling a free online demo with our experts.