Configure SAML authentication settings in OpManager for Microsoft AD FS?
Listed below are the steps to configure SAML authentication in OpManager (SP) for Microsoft AD FS (IdP) with Single Sign-On.
- Open AD FS management and click on Add Relying Party Trust.
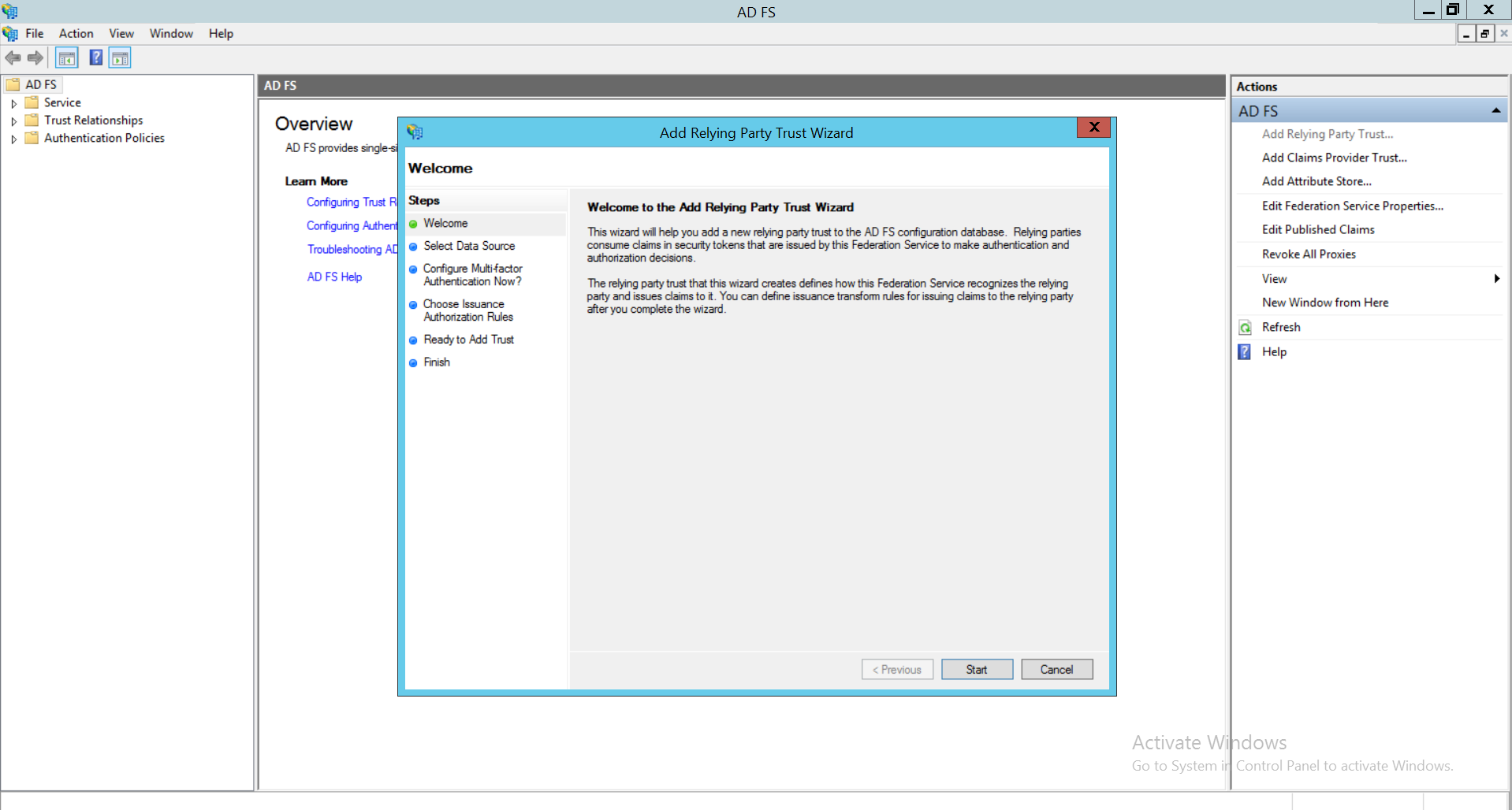
- Now, go to OpManager and navigate to Settings -> General Settings -> Authentication -> SAML . Download the Service Provider metadata and SP Certificate files from the links provided and copy the SP Entity ID and ACS URL.
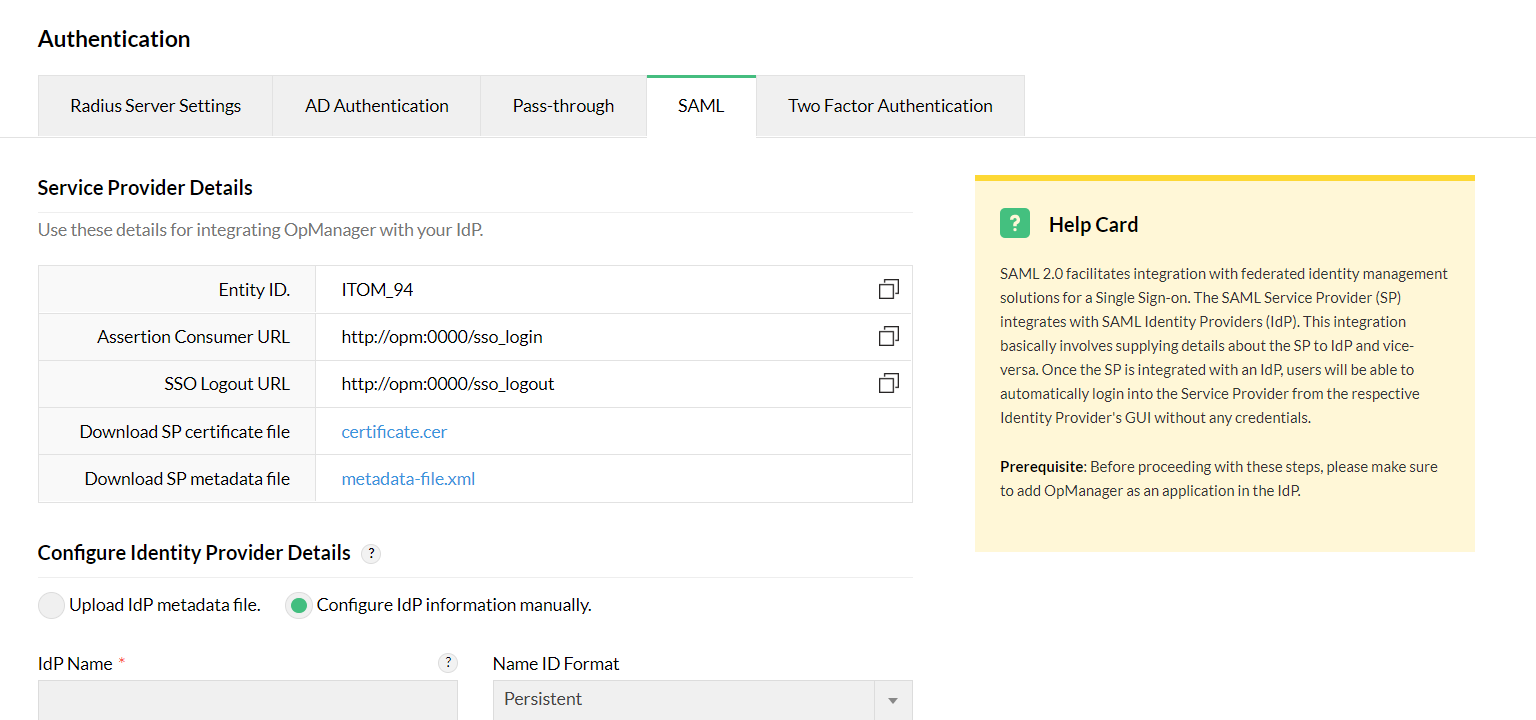
- Go back to AD FS, click Start and choose ‘Import data about the relying party from a file’. Upload the metadata file. Click on Next.
Note: Please refer to the 7th point under configuring Microsoft Ad FS manually for the next steps.
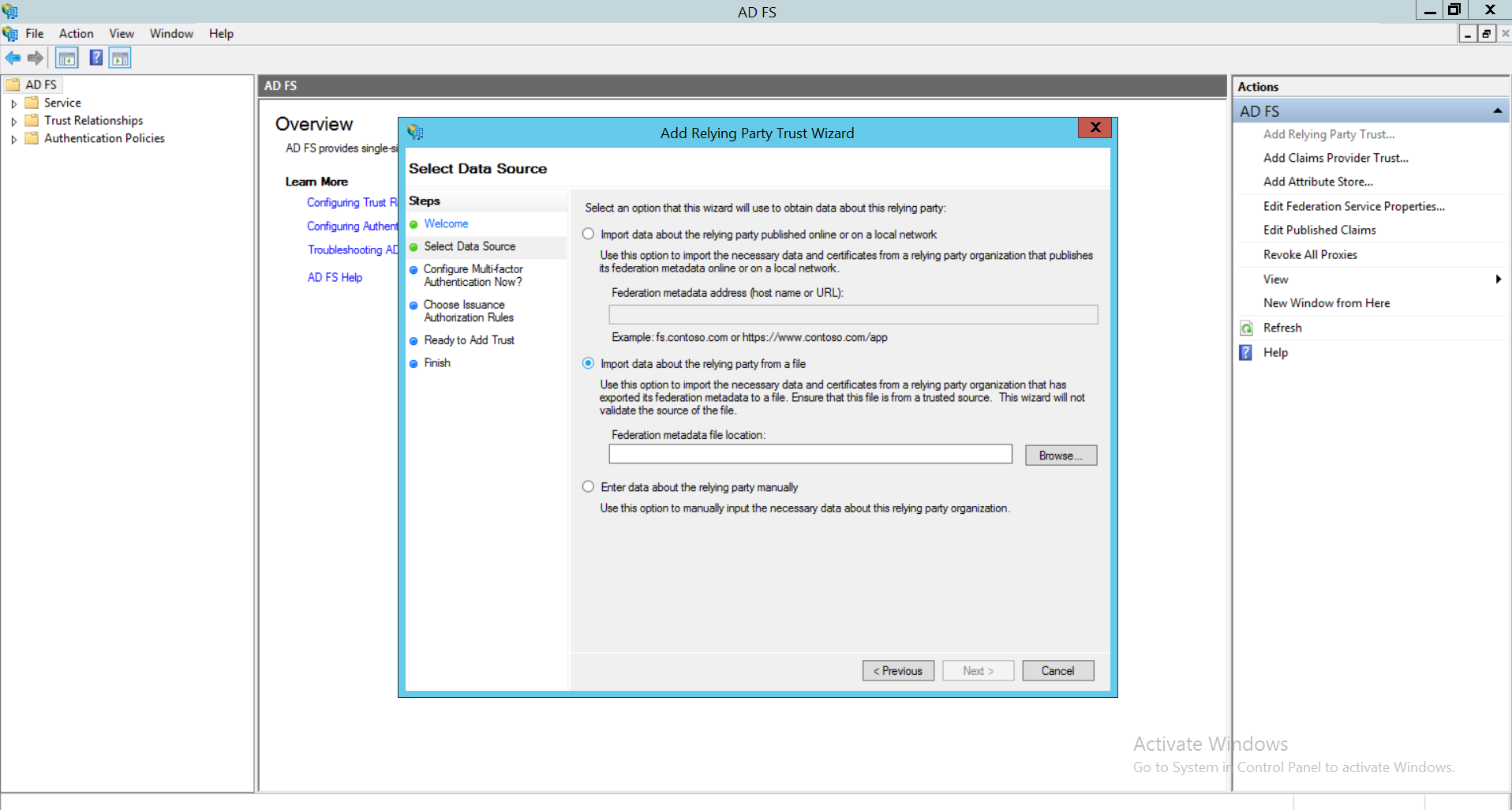
You can also configure Microsoft ADFS manually. To do so,
- Login to ADFS management and select Add Relying Party Trust.
- Click Start and choose ‘Enter data about the relying party manually’. Click on Next.
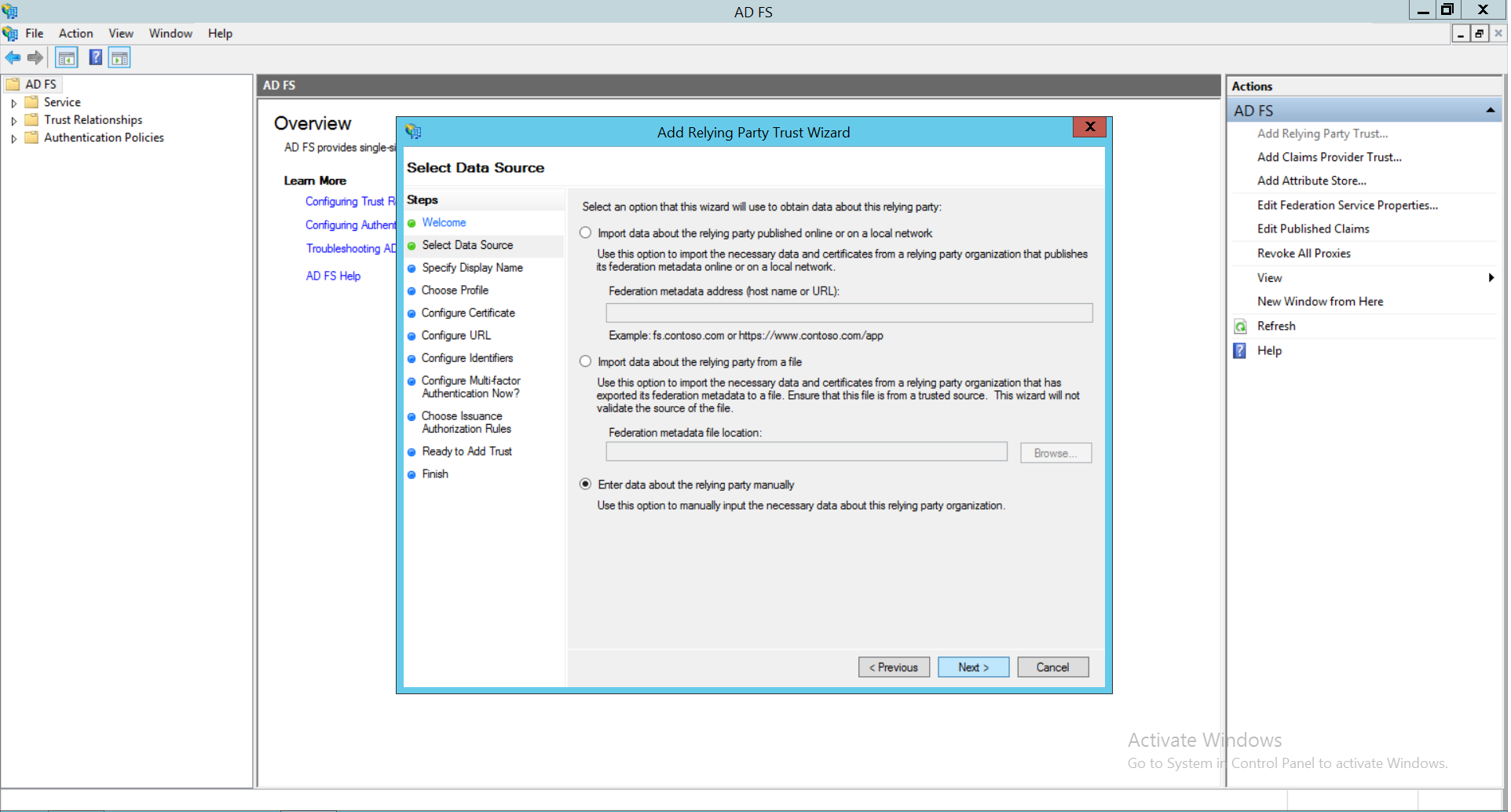
- Go to Choose Profile and select AD FS profile. Click Next.
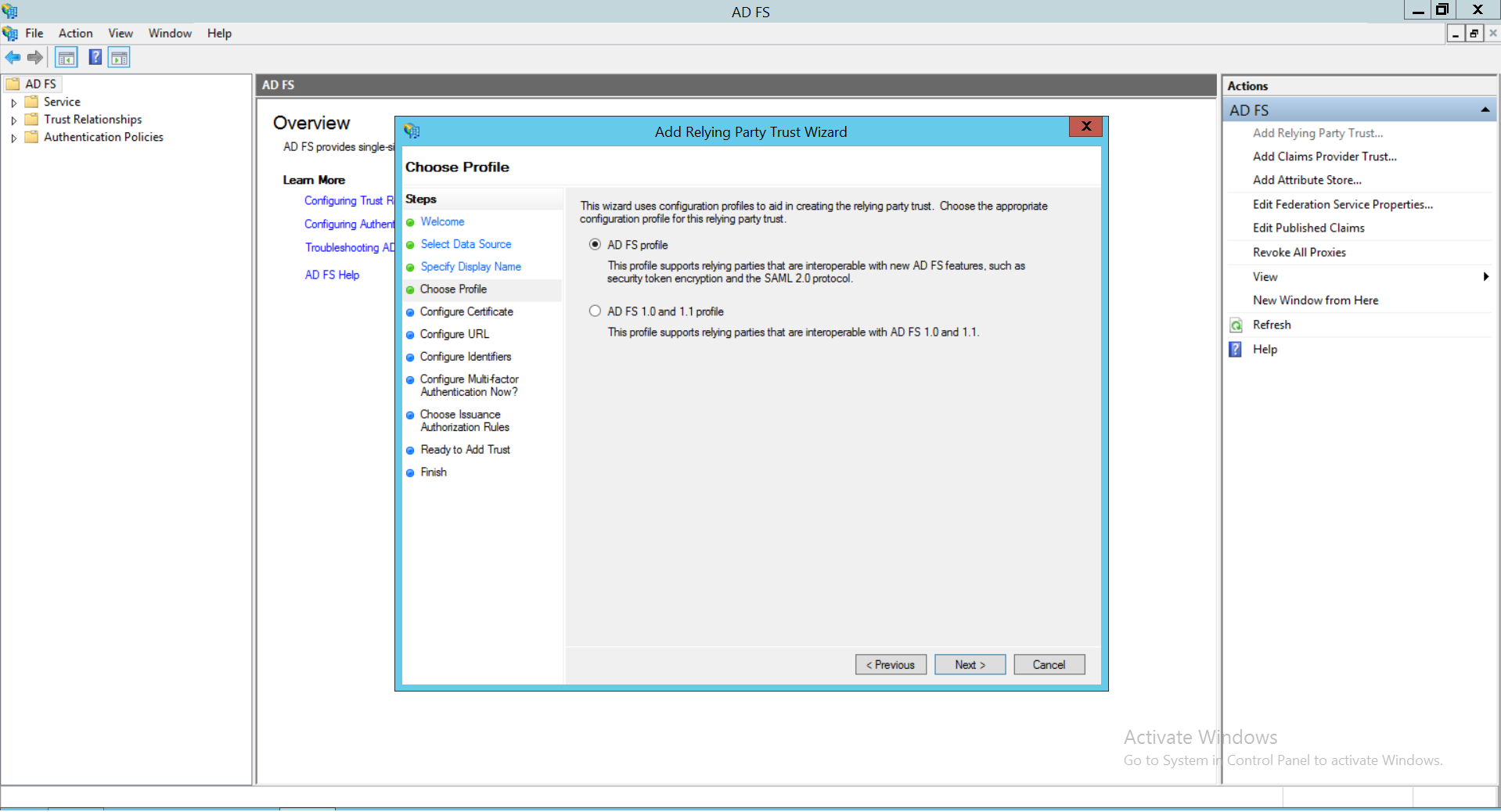
- Choose ‘Enable support for SAML 2.0 WebSSO protocol’ option and enter the service provider URL. Click on Next.
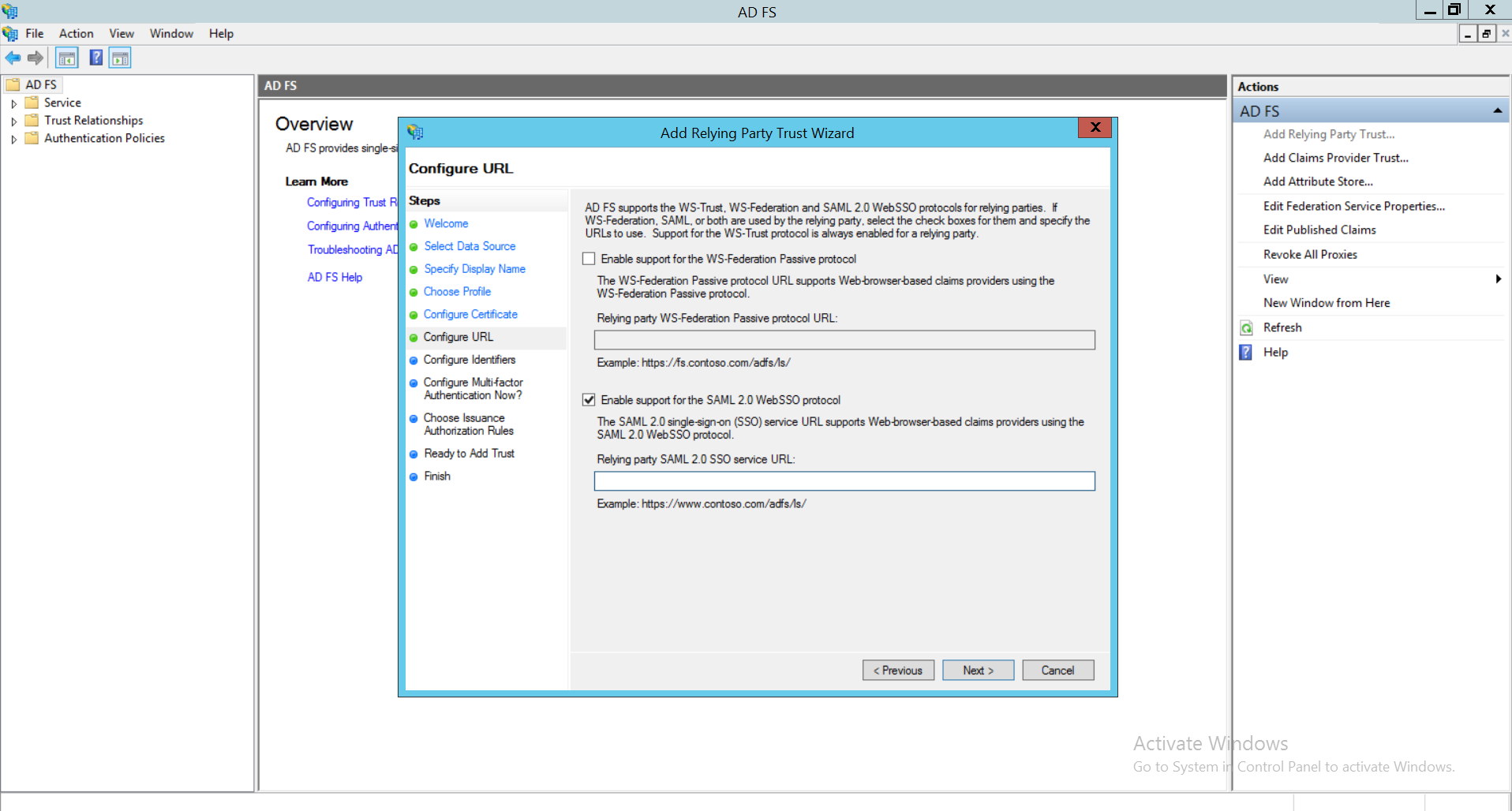
- Navigate to OpManager and copy the Entity ID. Go to Configure Identifiers in Microsoft AD FS and paste the Entity ID in relying party trust identifier.
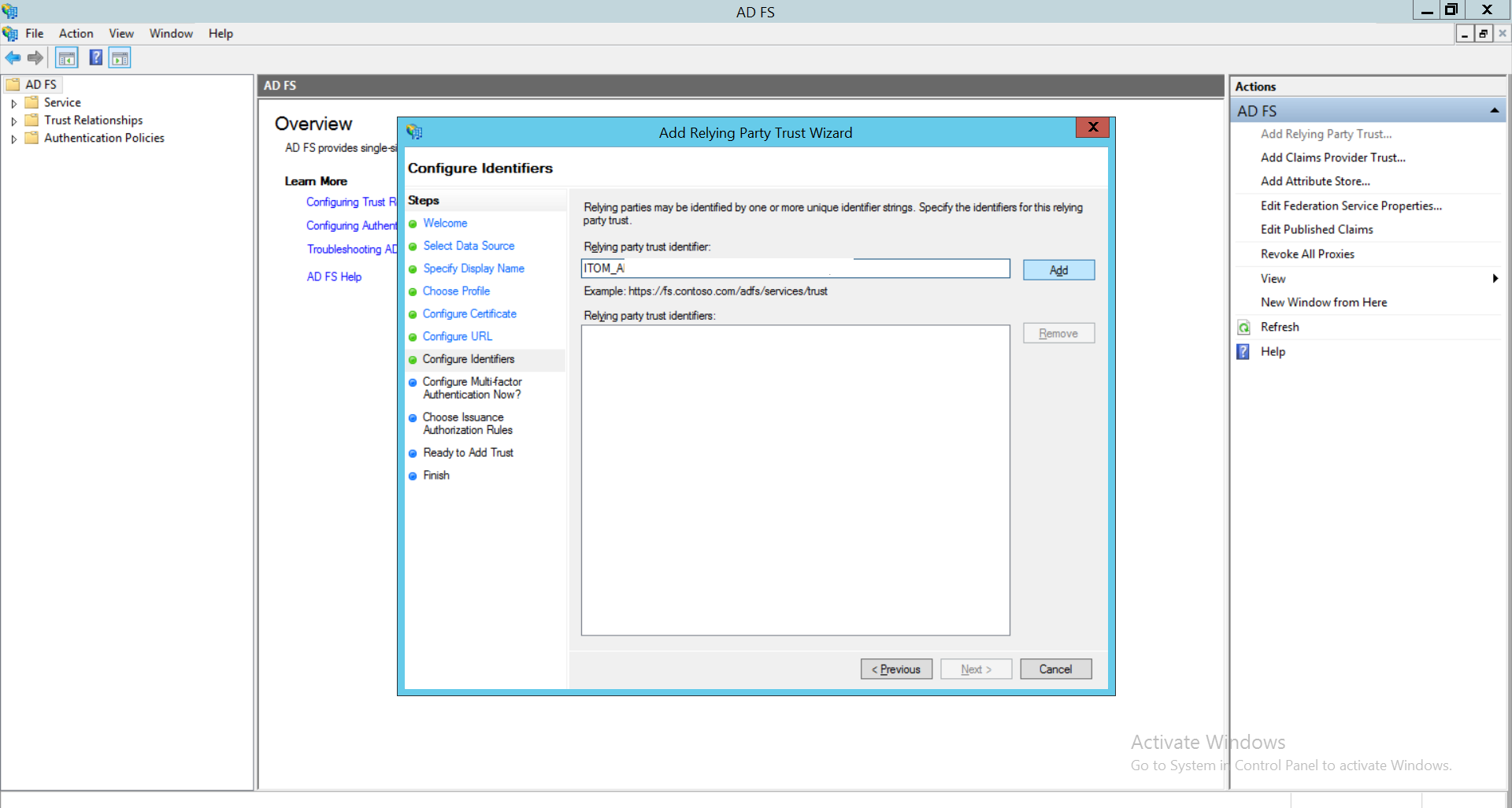
- Choose the ‘ I do not want to configure multi-factor authentication settings for this relying party trust at this time’ option.Click Next.
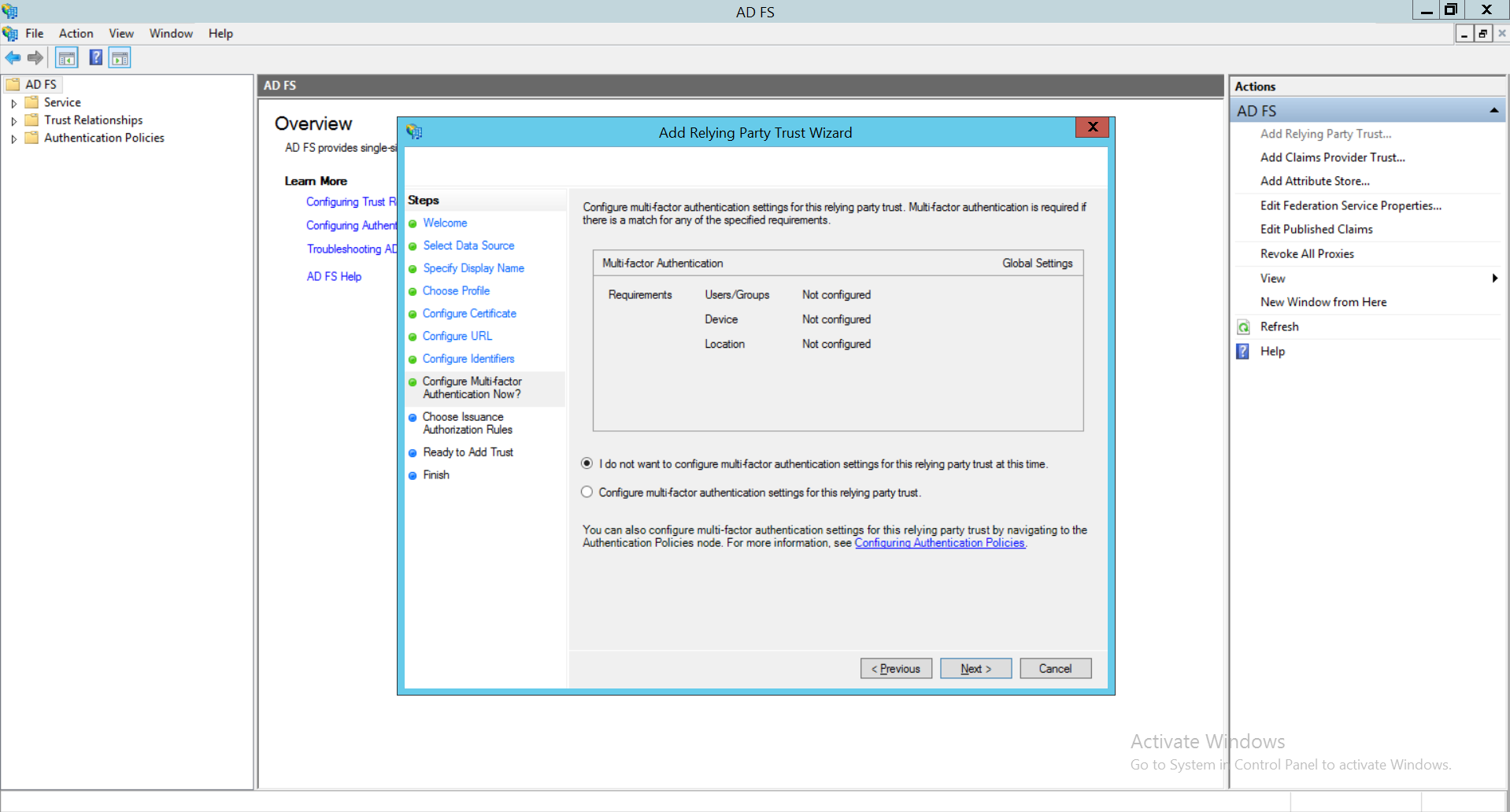
- Select ‘Permit all users to access this relying party’ option.Click Next.
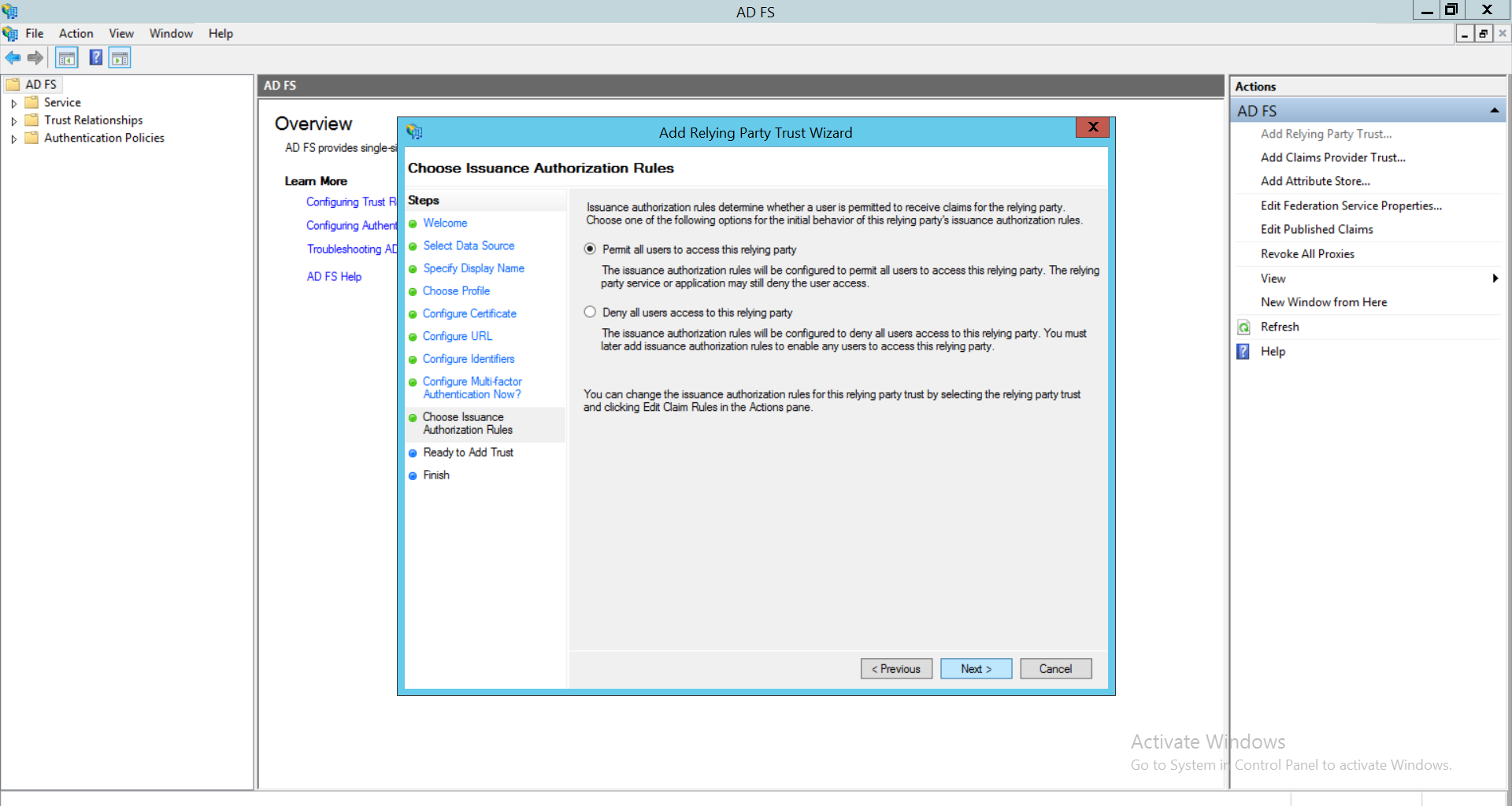
- Click on Next.
- Check the option 'Open the Edit Claim Rules dialog for this relying party trust when the wizard closes’ and select Close.
- Click on Add Rule. In the drop-down list under Claim rule template, choose Transform an Incoming Claim and click Next.
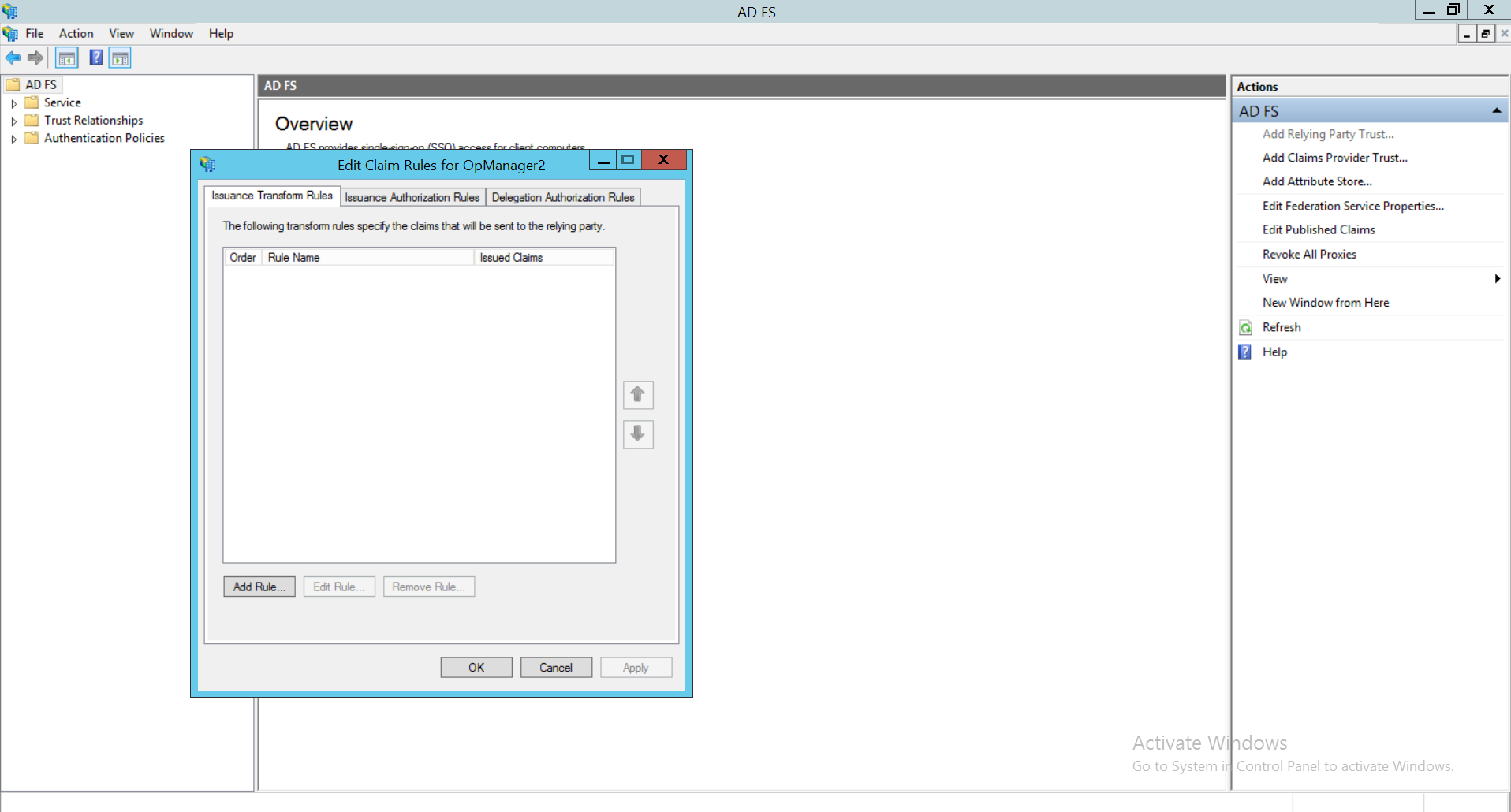
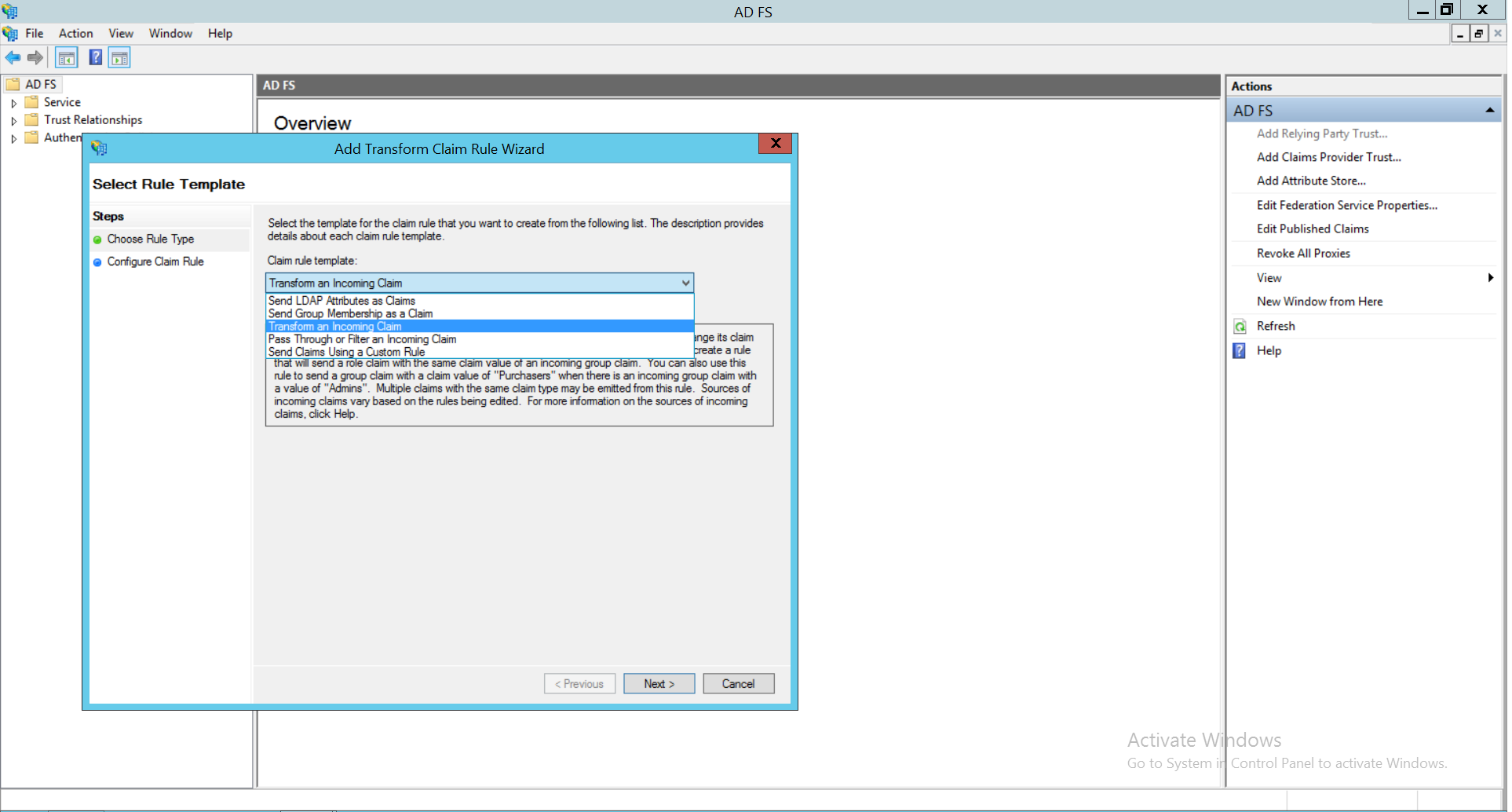
- Enter appropriate Claim rule name. Choose Windows account name as Incoming claim type. Select Name ID as Outgoing claim type. Choose Transient Identifier as Outgoing name ID format. Select Pass through all claim values. Click on Finish.
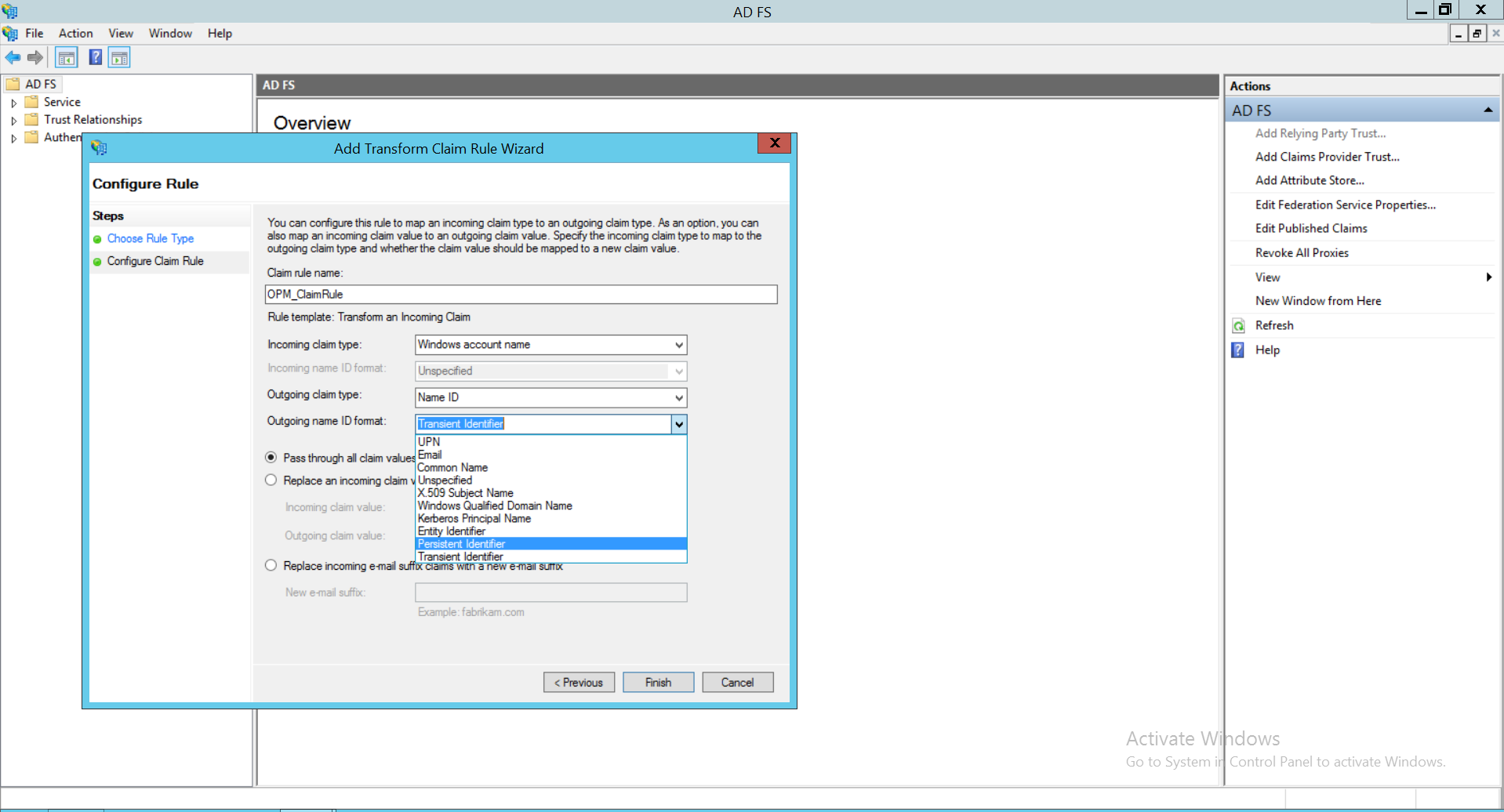
- Click on Apply and then select OK.
- The next step is to download the Federation Metadata XML file from ADFS. You can download the XML by appending: FederationMetadata/2007-06/FederationMetadata.xml to the root URL of the ADFS server. For example: If the FQDN of the ADFS server is dc.com, then the complete URL would be https://dc.com/federationmetadata/2007-06/FederationMetadata.xml
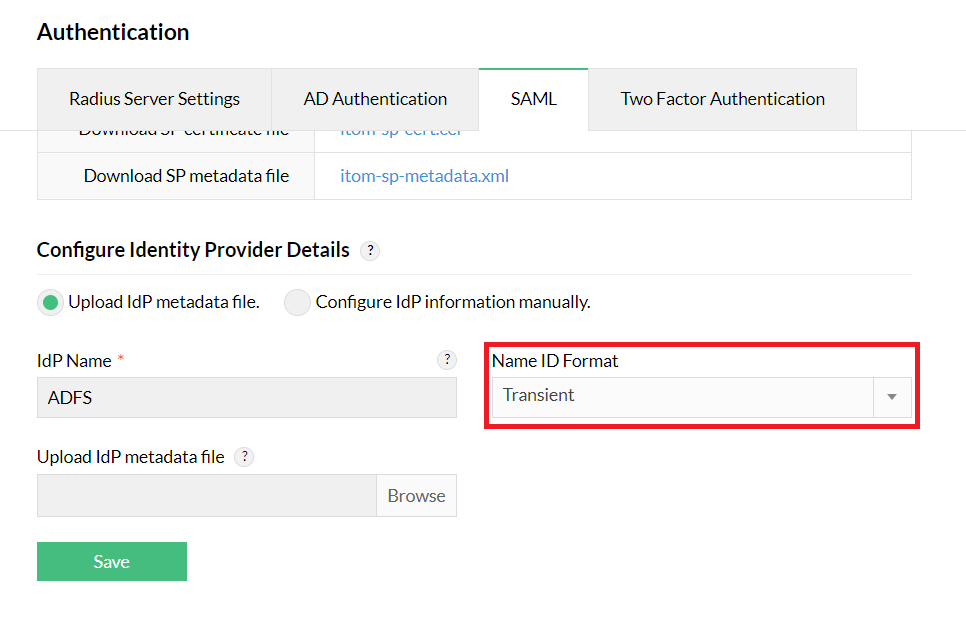
- In the OpManager web console, navigate to the Settings -> General Settings -> Authentication->SAML. Here, select the IdP as ADFS and choose the Name ID as Transient. Beside Configuration by uploading, choose Metadata and upload the Metadata XML file.
Once the configurations are done on both sides, SAML authentication via AD FS will be enabled in OpManager. In OpManager's login portal, choose to Login with AD FS and enter the necessary credentials to login.
Click here to learn more about SAML authentication in OpManager.