PAM360 Plugin for Ansible
Ansible is a popular open source orchestration tool provided by Red Hat, which helps organizations automate their configuration management and similar repetitive processes. Ansible users can create instructions for a routine task in the form of a 'playbook' that is basically an automation schedule. Execution of these playbooks more often than not require user credentials and similar sensitive information like privileged passwords, API keys, and access tokens to interface with other systems, applications, and services in the environment. In most DevOps environments, such credentials are stored in plaintext within the playbooks to enable smooth task execution without service delays, which can lead to many security and management issues.
The PAM360 lookup plugin developed for secrets management in Ansible helps improve security in organizations' DevOps pipeline. The plugin once enabled in Ansible, ensures that required credentials are retrieved from PAM360's vault every time when a play is executed, instead of being embedded in plain text within the written template. Upon secure retrieval, the credentials can then be used for actions such as connecting to a remote server. The plugin also saves the user from the arduous job of having to manually update the password/SSH key in the playbooks every time there's an update. Often, there are instances when a play fails owing to an outdated credential in the template. Now with the credentials stored in PAM360, they're regularly rotated in the vault and also updated in the respective remote device, which ensures that only the latest passwords or keys are retrieved from the vault while running plays.
The following are the major two steps involved in getting set up and starting to manage secrets in Ansible with PAM360.
1. Enabling the Ansible Integration in PAM360
- Log into PAM360 and navigate to Admin >> DevSecOps >> CI/CD Platform.
- Click on the Ansible option.
- AUTH Token: Click on Generate to populate an AUTH Token automatically. This will be required later while configuring the plugin in Ansible playbooks. Once set up, all incoming connections from Ansible will be validated by PAM360 using this AUTH token.
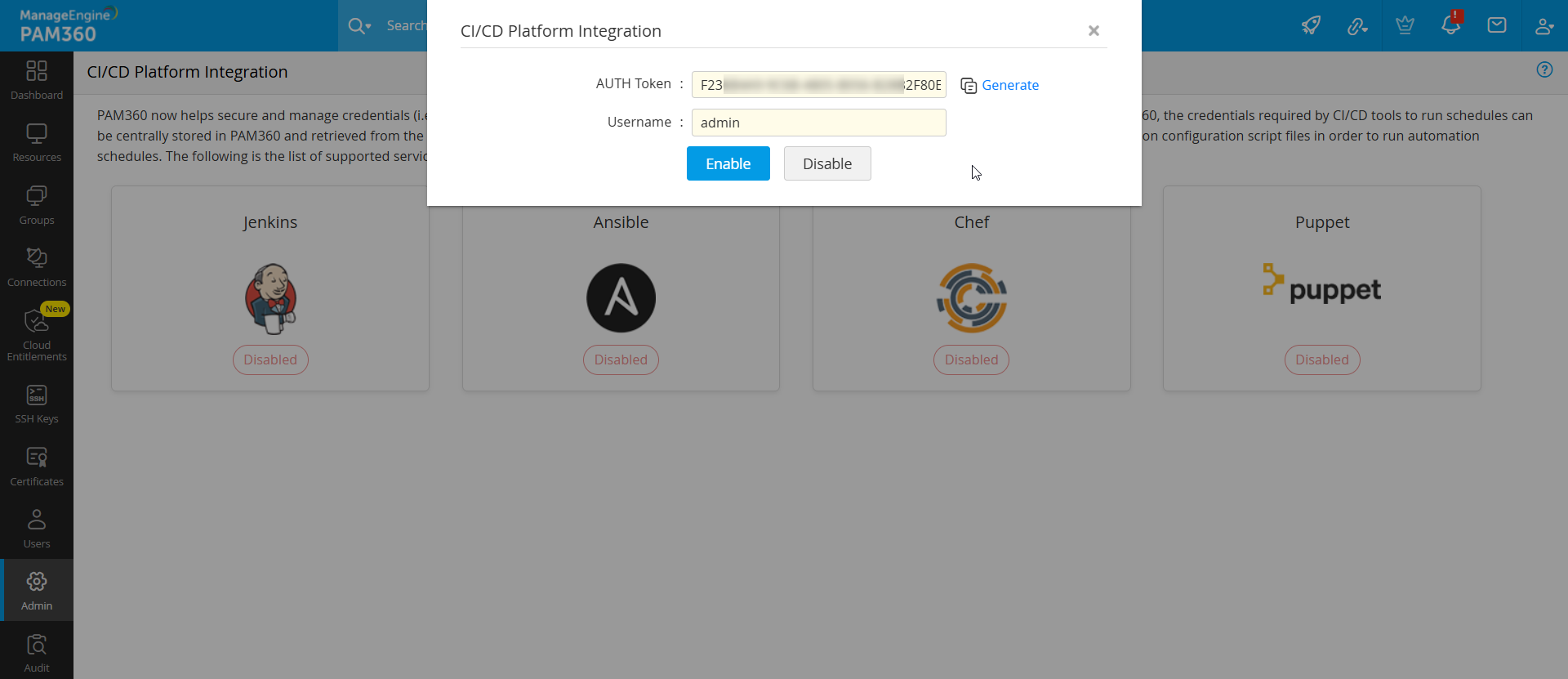
- Username: Here, enter the username of an active PAM360 user whose account will be used automatically by Ansible to securely retrieve the required passwords from PAM360's vault.
Caution
Ensure that the PAM360 user account you provide has the minimum required permissions for this workflow i.e. privilege to view/retrieve the passwords of resources to which Ansible has to connect. The passwords of resources owned by and shared to this user are the only credentials that Ansible will have access to in PAM360.
- Click Enable to enable the integration from the PAM360 interface.
2. Activating the Plugin in Ansible Playbooks
Basically, the PAM360 plugin is called a lookup plugin in Ansible's terms. As an Ansible user, you will be able to activate this custom lookup plugin by adding it to the lookup folder within the Ansible's installation directory. Once added, you can configure your playbooks to trigger the plugin whenever the play execution requires a set of credentials and the plugin will in turn connect to PAM360 to retrieve the required password or key.
Caution
PAM360's Ansible Lookup plugin works with Ansible python version 3 and above only.
Given below are detailed steps to achieve credential management workflow in Ansible using PAM360's lookup plugin.
- First, download the lookup plugin here. Extract the plugin Python script(.py) from the zip.
Caution
Ensure the SHA256 value upon downloading the file — SHA256 Checksum: 3164196bf9feba013367740ae225ffb233ba3977212718db8e5208bf39ea0a32
- Now go to Ansible's installation directory and trace the following path: ansible/lib/ansible/plugins/lookup.
- In the lookup folder, drop the plugin file and restart the Ansible service.
- Once the service is up again, open a playbook that has embedded credentials and remove the plain text credentials. In their place, add a command to invoke the PAM360 lookup plugin to connect to PAM360 and retrieve those credentials securely from the vault.
- The command should also specify the names of the resource and account that the plugin should check out from PAM360.
- The command to invoke the plugin should be configured in the playbook in the following format:
{{ lookup('pam360','RESOURCENAME', 'ACCOUNTNAME')}} - Repeat the above step for every playbook that requires privileged credentials. During this process, ensure that every resource and account names that you specify are added to PAM360's vault beforehand.
- After you have made necessary changes in the required playbooks, configure PAM360's URL and the AUTH Token generated earlier as environmental variables in Ansible.
- PAM360_URL
- PAM360_AUTHTOKEN
- You are now all set up now and ready to begin credential management in Ansible using PAM360.