AWS Account Dashboard and Risks Defined in PAM360
The AWS Account dashboard within the PAM360 Cloud Entitlements tab offers a comprehensive view of your IAM users, roles, and users groups in the AWS account, including the security posture and risk status they poses in the cloud environment. After discovering an AWS account, access the dashboard to gain key insights into identity privileges, attached policies, services, and permissions. Additionally, the dashboard provides detailed statistical reports on overall risk impact, identity-specific impacts, and weekly risk assessments, and the number of identities with excessive privileges, shadow admin privileges, inactive for a longer period, and without MFA.
To explore the account dashboard features and get insights about the PAM360-defined risks, refer to the sections below.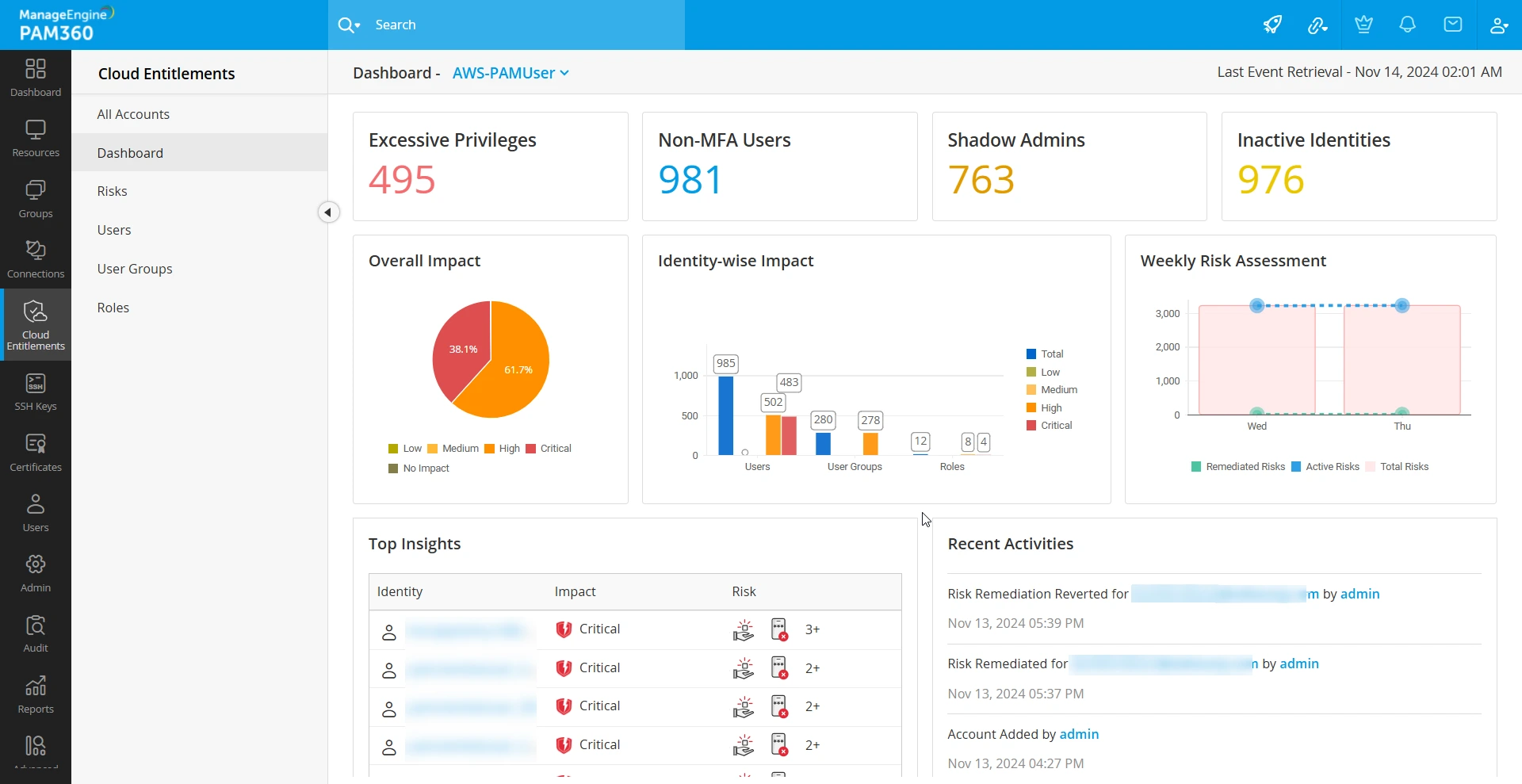
1. AWS Account Dashboard Features
The intuitive Cloud Entitlement dashboard provides the following details in your AWS account,
- Excessive Privileges - This section shows the total number of identities in your AWS account with the Excessive Privileges risk. Upon clicking the tile, you can view the list of IAM users and roles with unused permissions during the specified CloudTrail event retrieval period.
- Non-MFA Users - This section indicates the total number of users without configured MFA (Multi-Factor Authentication) in the AWS account. Click the tile to get the list of IAM users on your AWS account with no MFA enabled.
- Shadow Admins - The section highlights the total number of identities in the AWS account with administrator privileges. Upon clicking the tile, you will get the list of identities with administrator privileges.
- Inactive Identities - This section lists the total number of inactive IAM users and roles in the AWS account. Click the tile to view the complete list of inactive IAM users and roles, including other risks they are associated with.
- Overall Impact - The pie chart in this section represents the total impacts in your AWS account, categorized by impact levels: Low, Medium, High, Critical, and No Impact.
Additional Detail
No Impact does not imply that your IAM user account is entirely risk-free. While there may be potential risks associated with the account, these risks do not pose a security vulnerability within the defined scope of PAM360's assessments.
- Identity-wise Impact - The bar graph in this section illustrates the impacts within Users, Roles, and User Groups.
- Weekly Risk Assessment - The bar graph in this section depicts the weekly risk assessment, including total risks, remediated risks, and active risks.
- Top Insights - This section provides information about the critical impacts and risks associated with the identities in the AWS account.
- Recent Activities - This section lists the recent activities carried out in the AWS account.
2. Risks Defined in PAM360 for Cloud Entitlements
| Risks | Description |
|---|---|
Non-MFA Users | The IAM users without configured MFA are referred to as Non-MFA Users. If their credentials are compromised, the lack of active MFA allows accidental exposure to resources and services. This can potentially result in data breaches, disrupted operations, and other malicious activities. |
Excessive Privileges | The identities (IAM users and roles) possessing unused permissions are referred to as Excessive Privileges. Holding excess permissions will increase the risk of data exposure when an unauthorized identity gains access to the account. |
Shadow Admins | The permissions that enable an identity to perform administrative operations are classified as Shadow Admins. These privileges are highly sensitive and must be tightly controlled, as they could allow identities to modify or delete critical data, disrupt services, or escalate privileges to gain even greater control. |
Inactive Users | The IAM users who have not been active are referred to as Inactive Users. This could be a security risk, as the inactive IAM user's unused permissions might result in privilege escalation or account compromise issues. |
Inactive Roles | The IAM roles that have not been active are referred to as Inactive Roles. AWS Identity and Access Management (IAM) roles are crucial for granting permissions to teams and applications using your AWS infrastructure. Over time, as requirements evolve, some roles may become obsolete and remain unused in your AWS account. If an IAM role has been inactive for the last 90 days, it could lead to unauthorized access. |
Non-Rotated Passwords | The users with non-rotated passwords in the AWS console fall under the Non-Rotated Passwords risk. Over a period, there might be a risk of the password being compromised, thus leading to unauthorized access to resources of the IAM user. Failure to adhere to password rotation policies could lead to compliance violations. |
Non-Rotataed Access Keys | The users with non-rotated access keys in the AWS console fall under the Non-Rotated Access Keys risk. The outdated access keys become more vulnerable to exploitation and might lead to unauthorized modifications in the cloud environment and service disruptions. |
Once you open your AWS account, you can view the Risks tab from the left-side pane. You can get the following information within the Risks tab:
- Active Risks - This page provides information about the risks (PAM360-defined risks) identified on your AWS account. Classified into High Risks, Medium Risks, and Low Risks, the active risks in Users, Groups, and Roles of your AWS account will be listed here. For information about the risk and remediation steps, click the Info icon on the risk tile.
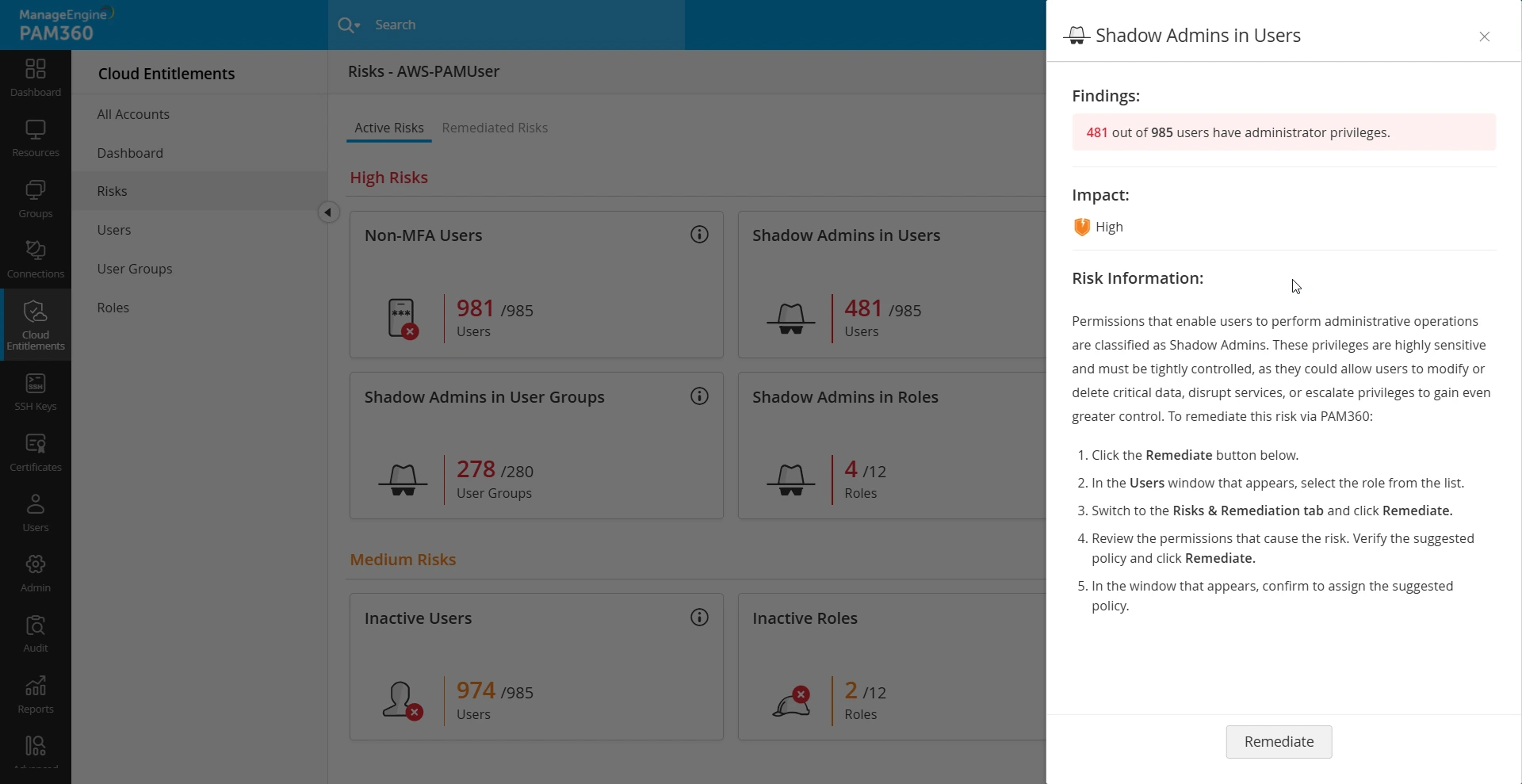
- Remediated Risks - This page displays a log of remediated and reverted risks for identities in the AWS account. It allows you to view the risks that have been remediated or reverted, along with details on who performed what with the corresponding timestamp.
3. Summary of Users, User Groups, and Roles
To view the list of IAM users, roles, and user groups of the discovered AWS account in PAM360, open the account tile and explore the Users, User Groups, or Roles tabs on the left-side pane. Upon clicking an identity from the Users, User Groups, or Roles page, you will get the following details associated with the identity: Access Map, Policy Details, Risk & Remediation, and History.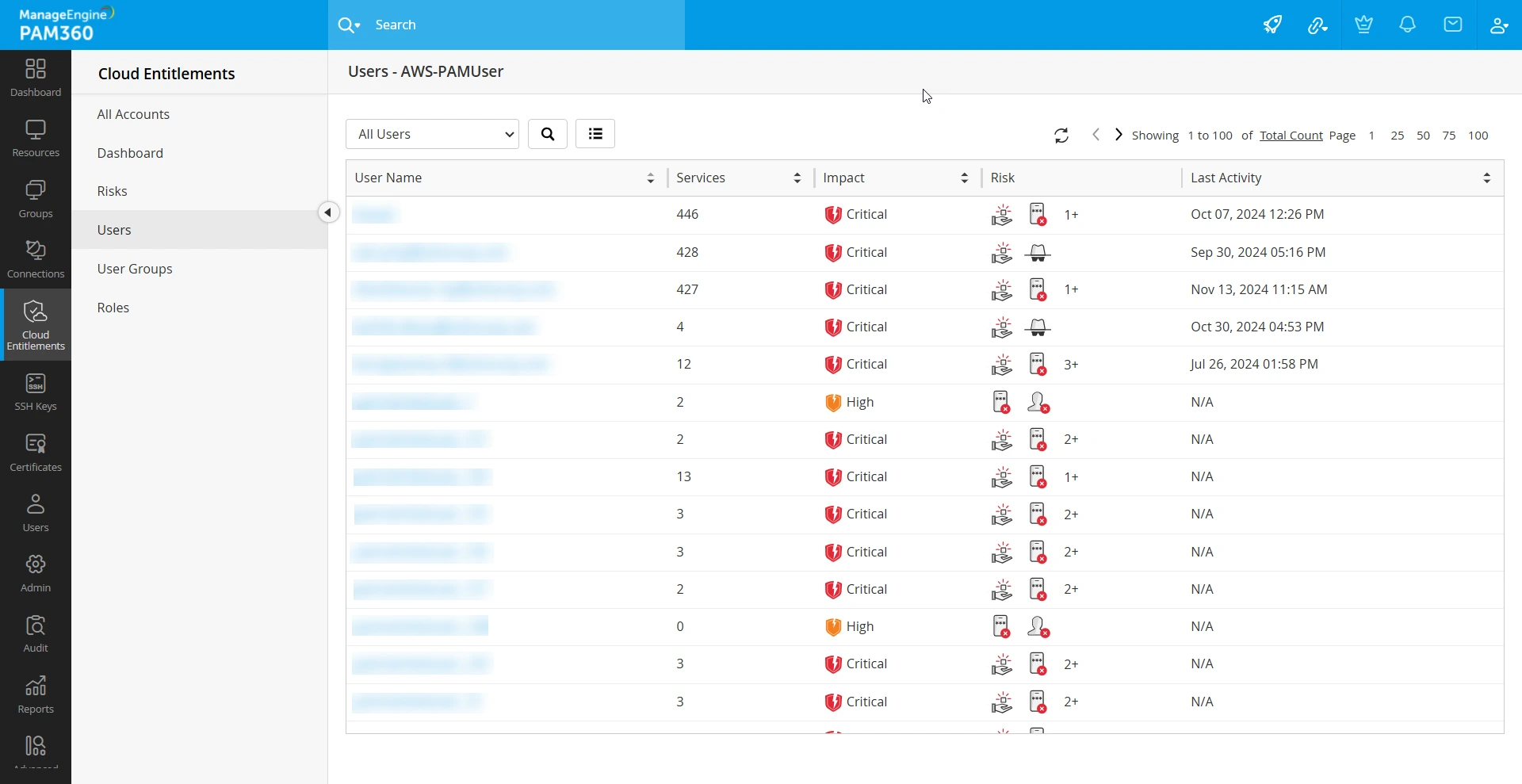
3.1 Access Map
The Access Map in PAM360 is a built-in feature designed to provide clear insights into areas with excessive permissions and standing privileges, supporting a streamlined approach to least-privilege access management. The Access Map tree offers a comprehensive view of policies, permissions, and services associated with each identity - whether user, user group, or role - within an AWS environment. To examine the permissions mapped to an identity via associated policies, simply select the desired service from the Access Map tree. This action reveals both used and unused permissions, enabling precise control and better governance over privilege assignments.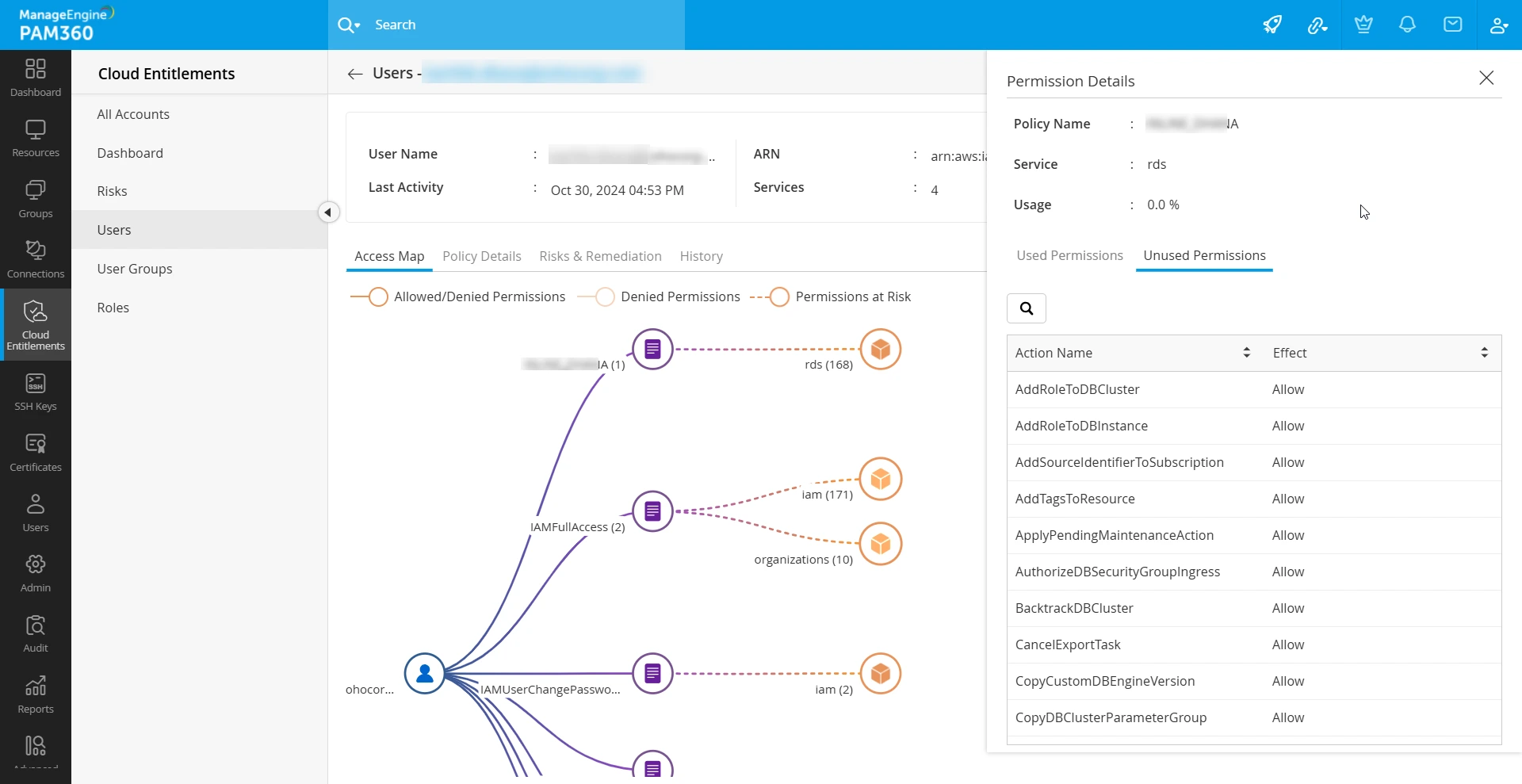
3.2 Policy Details
This section provides information about the currently attached policies and the associated IAM users or user groups of the identity.
- Policies - This section will list the policies attached to the identity (Users, User Groups, or Roles), including both IAM and PAM360 inline policy (if any).
- Users - You can get the list of IAM users attached to the identity (User Groups) from the provided table in this section.
- User Groups - This tab provides the list of user groups associated with the identity (Users).
3.3 Risks & Remediation
This section shows the list of risks associated with the identity. The Shadow Admin Privileges and Excessive Privileges risks can be remediated directly from this section using the provided Remediate button. For other risks, expand the risk ribbon to view the remediation steps. Refer to this document to learn more about remediating PAM360-defined risks in your cloud environment.
3.4 History
The information about the remediated and reverted risks of the identity are listed in the History tab. Additionally, you can get full insights about the remediated risk from this section. If you want to revert any remediation, click the Revert button on the risk ribbon and confirm your action. However, ensure to read the permissions that will be restored to the identity while reverting the risk.
By consolidating these details, you can effectively manage the users, user groups, and roles within your AWS account, addressing any associated risks and ensuring proper policy and access management.
Additional Detail
Identities from a discovered AWS account in PAM360 that have been deleted or disabled in the AWS console can no longer be managed in PAM360’s Cloud Entitlements. These unmanaged identities will still appear on the Users, User Groups, and Roles pages after the daily CloudTrail event retrieval or on-demand data retrieval. To remove these disabled or deleted identities from PAM360, click the Delete icon beside each identity and confirm your action in the pop-up dialog box.