AWS Account Discovery and Cloud Entitlements Dashboard
Managing cloud entitlements in PAM360 begins with discovering your AWS account, as it provides visibility into identities, such as IAM users, roles, and groups, along with their associated permissions and policies. This discovery enables PAM360 to assess predefined cloud account risks, including excessive privileges, shadow admin privileges, inactive identities, and missing MFA. Once an AWS account is discovered, administrators can effectively manage entitlements, remediate risks, and ensure compliance across all the discovered AWS accounts.
1. Discovering an AWS Account
Best Practice
- Before adding an AWS account in PAM360, ensure that the identity holds the necessary privileges in AWS for managing the cloud entitlements via PAM360.
- As a best practice, we recommend you to use a dedicated AWS identity for managing the cloud entitlements via PAM360.
To discover an AWS account in PAM360,
- Navigate to the Cloud Entitlements tab and click Discover Now.
- On the account discovery page, provide the following details:
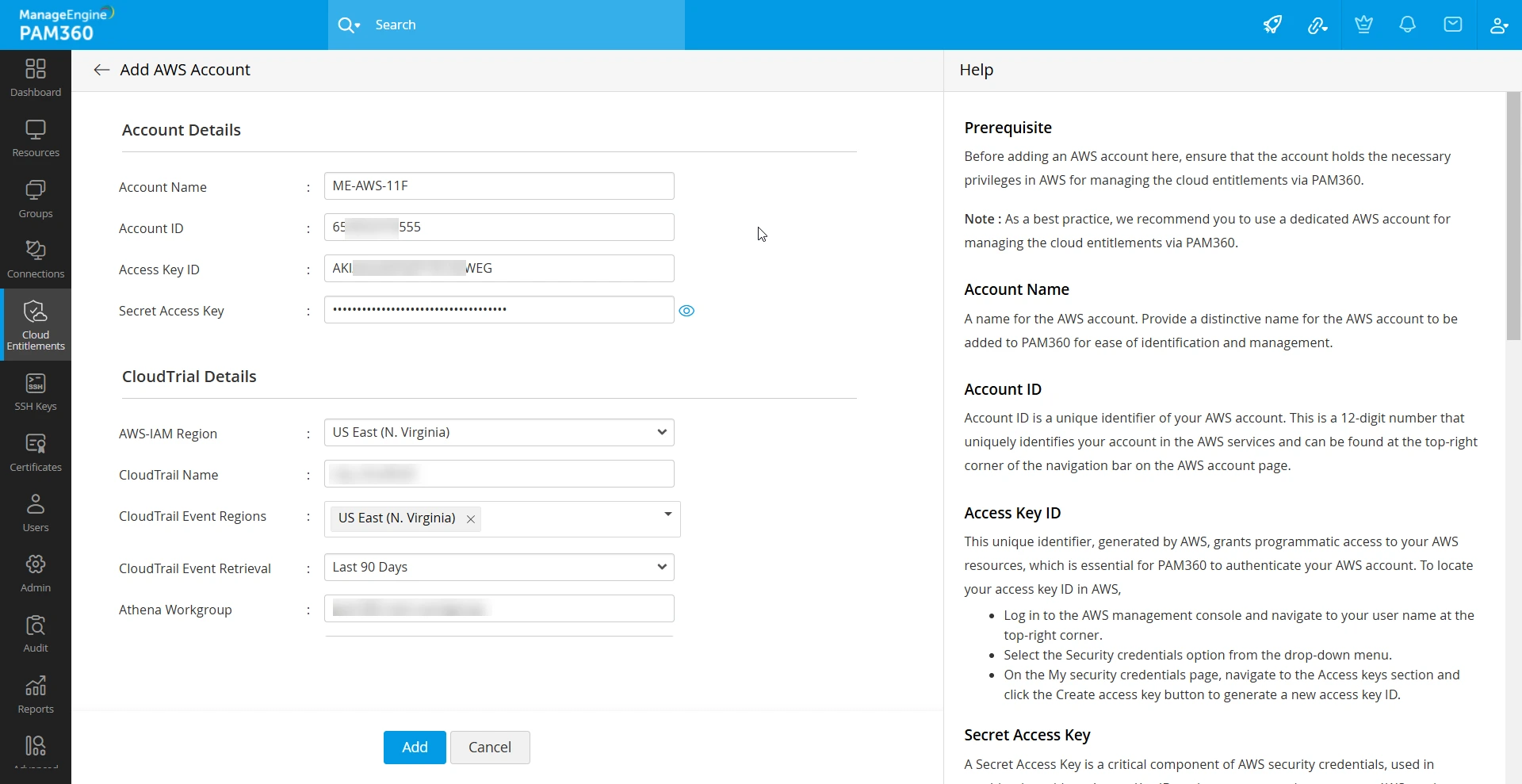
- Account Name - A name for the AWS account. Provide a distinctive name for the AWS account to be added to PAM360 for ease of identification and management.
- Account ID - Account ID is a unique identifier of your AWS account. This is a 12-digit number that uniquely identifies your account in the AWS services and can be found at the top-right corner of the navigation bar on the AWS account page.
Additional Detail
Account ID cannot be duplicated when discovering your AWS account in PAM360.
- Access Key ID - This unique identifier, generated by AWS, grants programmatic access to your AWS resources, which is essential for PAM360 to authenticate your AWS account. To locate your access key ID in AWS,
- Log in to the AWS management console and navigate to your user name at the top-right corner.
- Select the Security credentials option from the drop-down menu.
- On the My security credentials page, navigate to the Access keys section and click the Create access key button to generate a new access key ID.
- Secret Access Key - A secret access key is a critical component of AWS security credentials, used in combination with an access key ID to sign programmatic requests to AWS services. When discovering an AWS account in PAM360, specify the secret access key in the Secret Access Key field. Please note that the secret access key can only be viewed at the time of creating a new access key. For more details, click here.
- AWS-IAM Region - In this field, specify the primary geographical region where your workloads (Athena, CloudTrail Event History, and s3 bucket) are deployed. Upon account discovery, your IAM users, roles, and user groups will be fetched based on this region.
- CloudTrail Event Regions - You can select multiple regions from which to retrieve the CloudTrail event history in this field. PAM360 will analyze the data fetched from these regions and identify the risks in your AWS cloud environment.
- CloudTrail Name - Enter the CloudTrail name in the CloudTrail Name field. This allows PAM360 to audit and monitor all actions in your AWS account, enhancing security and compliance by tracking and analyzing activities and API calls. To find your CloudTrail name,
- Log in to the AWS Management Console using your AWS credentials.
- Click the Services menu in the top-left corner and select CloudTrail under Management & Governance.
- In the CloudTrail console, click Trails from the left-side pane to view the list of CloudTrail trails running in AWS.
- CloudTrail Event Retrieval - Specify the duration for retrieving CloudTrail event history (last 30, 60, or 90 days) based on your operational requirements. For instance, if you select 'Last 90 Days' from the CloudTrail Event Retrieval dropdown, PAM360 will fetch the CloudTrail event history from the AWS server for the last 90 days. This data will be fetched and updated daily to ensure the last 90 days' event history is regularly updated in PAM360.
- Athena Workgroup - Enter the Athena Workgroup name of your AWS account in this field. The workgroup will be used to run CIEM-related queries on your data in Amazon S3, enabling efficient analysis and reporting. It also ensures that PAM360’s cloud entitlement actions are organized and easily accessible for insights. To find your Athena Workgroup name,
- Log in to the AWS Management Console using your AWS credentials.
- Click the Services menu in the upper-left corner and select Analytics >> Athena.
- In the Athena console that appears, you will see a drop-down menu labeled Workgroup. It displays the name of your current workgroup.
- To view all the available workgroups, click on the Workgroups tab in the navigation pane on the left. Here, you can see a list of all the workgroups along with their details.
Best Practice
As a best practice, it is recommended to use a dedicated Athena workgroup for managing cloud entitlements in PAM360.
- Query Result Location - Enter the S3 path of your Athena query results in the Query Result Location field. This location will store the output of CIEM-related queries, making it easy to access and analyze the results. Ensure the path is accurate to retrieve and review query outcomes efficiently. To find the query result location in AWS Athena, log in to the AWS Management Console using your AWS credentials and navigate to Services >> Athena >> Settings.
Best Practice
As a best practice, it is recommended to use a dedicated query result location for managing cloud entitlements in PAM360.
- Click Add and wait for the account to be added.
Once the authentication is completed, your AWS account will appear in the Cloud Entitlements dashboard. The potential risks will be identified and displayed based on the number of days selected for CloudTrail Event Retrieval.
1.2 Managing the Discovered AWS Accounts
The AWS accounts discovered in PAM360 are listed as tiles in the Cloud Entitlements dashboard. Below are the operations you can perform from the dashboard on your discovered accounts: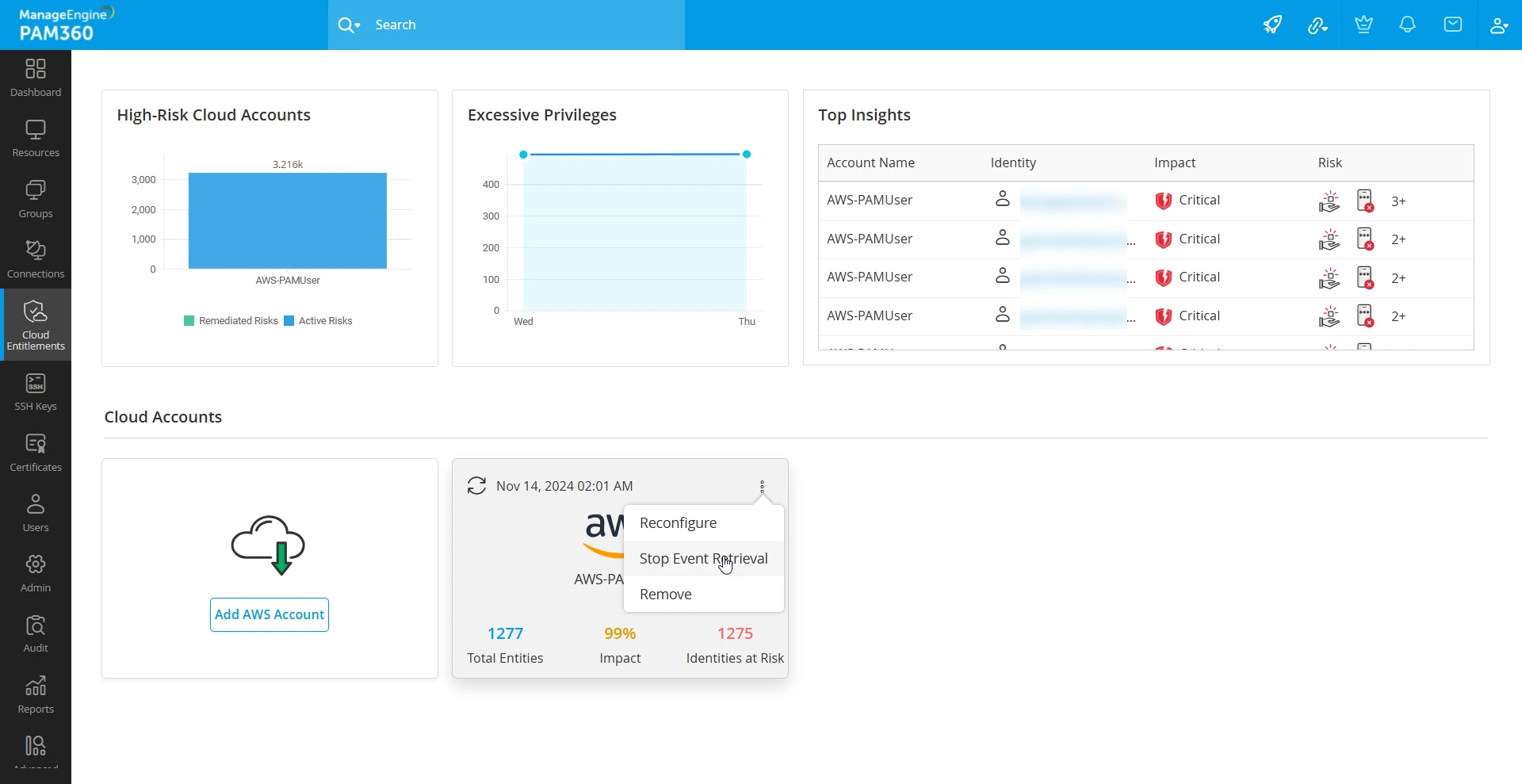
- On-Demand Data Retrieval - To retrieve the IAM users, roles, or user groups data immediately from the AWS server to PAM360, click the On-Demand Data Retrieval icon on the AWS account tile. However, this action will not fetch the details from the CloudTrail event history.
- Reconfigure Account Details - To reconfigure the account details, click the three-dot menu on the account tile and click Reconfigure. Modify the required details and click Add to add your account again into PAM360.
- Start/Stop CloudTrail Event Retrieval- To start or stop CloudTrail event retrieval on your AWS account, click the three-dot menu on the account tile and select the desired option. Stopping the CloudTrail event retrieval of the AWS account will pause the daily data retrieval from the CloudTrail event history of the AWS server until resumed. However, you can still manage the data discovered within the selected retrieval duration.
- Remove AWS Account - To remove the discovered AWS account from PAM360, click the three-dot menu on the account tile and select the Remove option. Then, confirm your action in the dialog box that appears.
2. Cloud Entitlements Dashboard - A Walkthrough
The Cloud Entitlements dashboard in PAM360 provides a comprehensive overview of your discovered AWS accounts, presenting critical insights and risk assessments.
- High-Risk Cloud Accounts - This graph highlights the total number of active risks and remediated risks in the discovered AWS accounts.
- Excessive Privileges - This graph depicts the change in the excessive privileges risk of the AWS accounts weekly based on accumulated data.
- Top Insights - This table provides information about the top 5 identities of the AWS accounts added into PAM360 with the most critical impacts and risks.
- Add AWS Account - The tile below the High-Risk Cloud Accounts section, featuring the Add AWS Account button, allows you to add new AWS accounts to PAM360.