In today's digital landscape, it's imperative for organizations to minimize risks associated with remote access to critical systems. Typically, in an IT environment, remote connection requests to privileged assets come from:
- Internal IT teams who need access to perform service and maintenance.
- Full-time or part-time employees who need access for business needs.
- Corporate teams operating remotely.
- Third-party vendors, contractors, consultants, and other service providers who need elevated access to networks.
While it's essential that these teams are provisioned with uninterrupted access to systems and processes to keep the business afloat, incorporating tight security and control around remote access operations is a vital aspect of preventing privilege abuse. PAM360 helps enterprises stay on top of remote connection requests to privileged systems through a straightforward web-interface approach, eliminating the need for virtual private networks (VPNs), agents, or any other ad hoc processes without compromising on security.
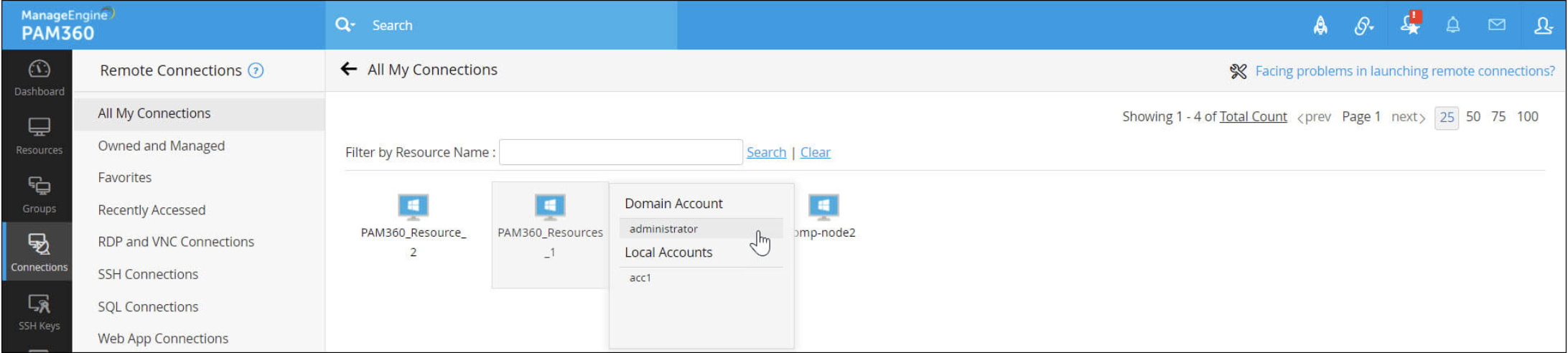
VPN-less access to remote privileged systems
With PAM360, users can launch direct terminal sessions to remote privileged systems from its browser interface. Bundled with various gateway engines, PAM360 helps users invoke and tunnel connections from web clients to target systems via emulated Remote Desktop Protocol (RDP), Virtual Network Computing (VNC), or Secure Shell (SSH) sessions without VPNs, agents, plug-ins, or helper programs installed in the endpoints. Once the resource supporting remote connection is added to PAM360, the Auto Logon gateway is enabled for all users that have access to that resource in PAM360—no complicated configurations needed.
Achieve total remote access security
IT teams are always caught between business continuity and security, trying to strike the right balance to keep processes running without leaving gaps in security. PAM360 gives you the best of both worlds with centralized control on remote access pathways. This way, users are provisioned with one-click access to remote privileged systems and are kept on the administrator's radar while accessing them. This gateway approach also eliminates the storage of access credentials to critical systems in users' local hosts.
Passwordless remote connections to SSH-based endpoints
PAM360 lets users establish passwordless connections to SSH-based remote endpoints such as Linux systems. Users can readily leverage the built-in key creation and deployment tool to generate SSH key pairs from the PAM360 web interface, associate them with existing accounts, and configure key-based authentication for those accounts instead of conventional password authentication. This mode of authentication prevents plain-text exposure of passwords to users and also ensures that the login credentials (SSH keys) are safely stored in the PAM360 database, reducing the chances of privilege misuse.
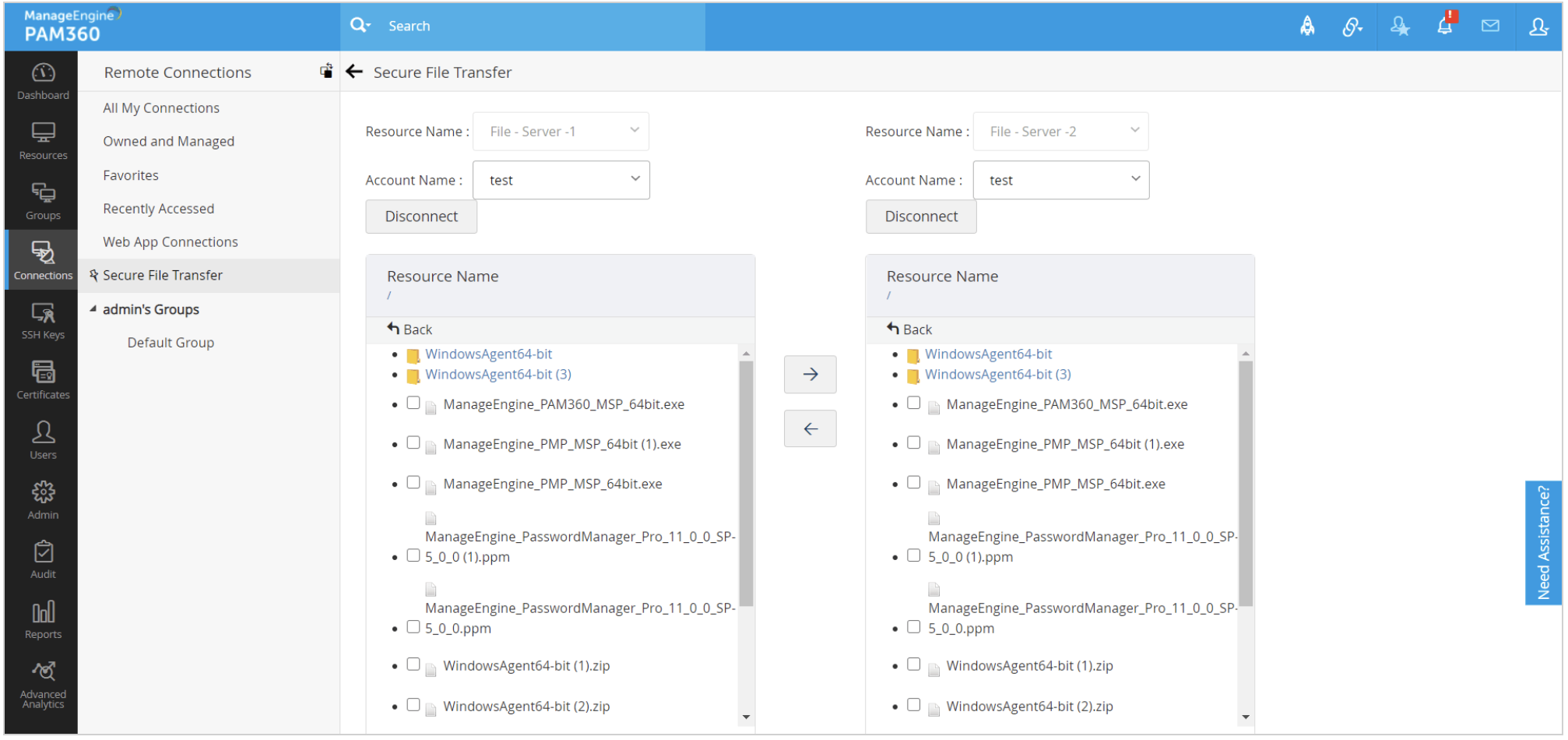
Easy, secure, reliable, and uncorrupted file transfer
IT administrators can securely transfer files during Windows RDP sessions tunnelled via PAM360. All you need to do is drag and drop the files you want to share, making it easy to move information to and from remote systems while keeping security intact.
Invoke custom connections to target systems using auto-logon helper scripts
Configure multiple remote access pathways (RDP, VNC, and so on) to target systems, and predefine what operations users can perform on those systems. With PAM360, administrators can create helper scripts for each connection. Any number of connection paths can be created and mapped to a target system.
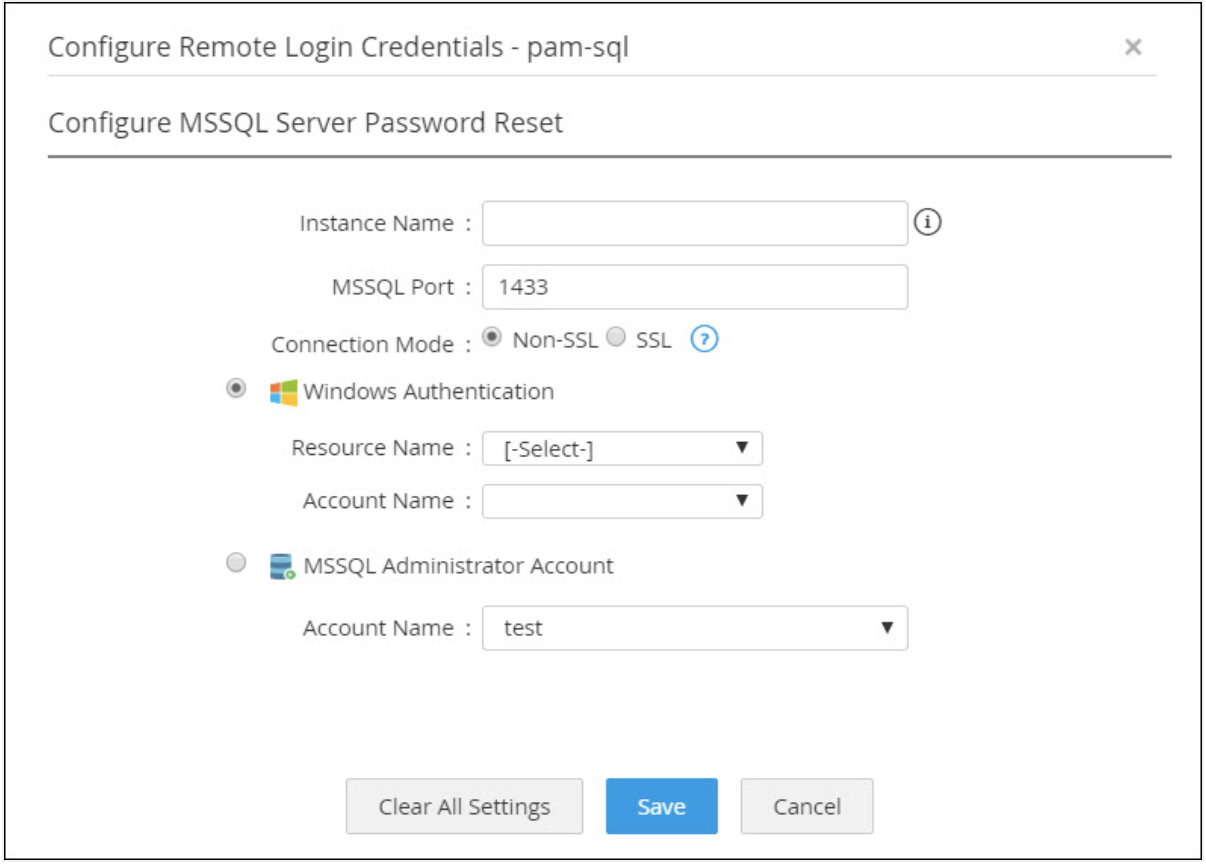
Instant, reliable access to remote datacenters
Achieve one-click access to databases in remote locations from PAM360's web client without deploying any kind of database query tools. Configure as many jump hosts as required to overcome network barriers and automate the establishment of connections to the remote server. PAM360 helps IT administrators invoke connections to databases such as MySQL, MS SQL, PostgreSQL, Sybase, and Oracle.
Leverage native browser extensions and mobile apps for smarter remote access
With PAM360, IT administrators can secure and manage their remote access on the go via native browser extensions and mobile apps. Currently, PAM360 extensions are available for Chrome and Firefox browsers, and mobile apps are available for Android and iOS platforms.