Direct Inward Dialing: +1 408 916 9892


CVEID: CVE-2022-28219
Severity: Critical
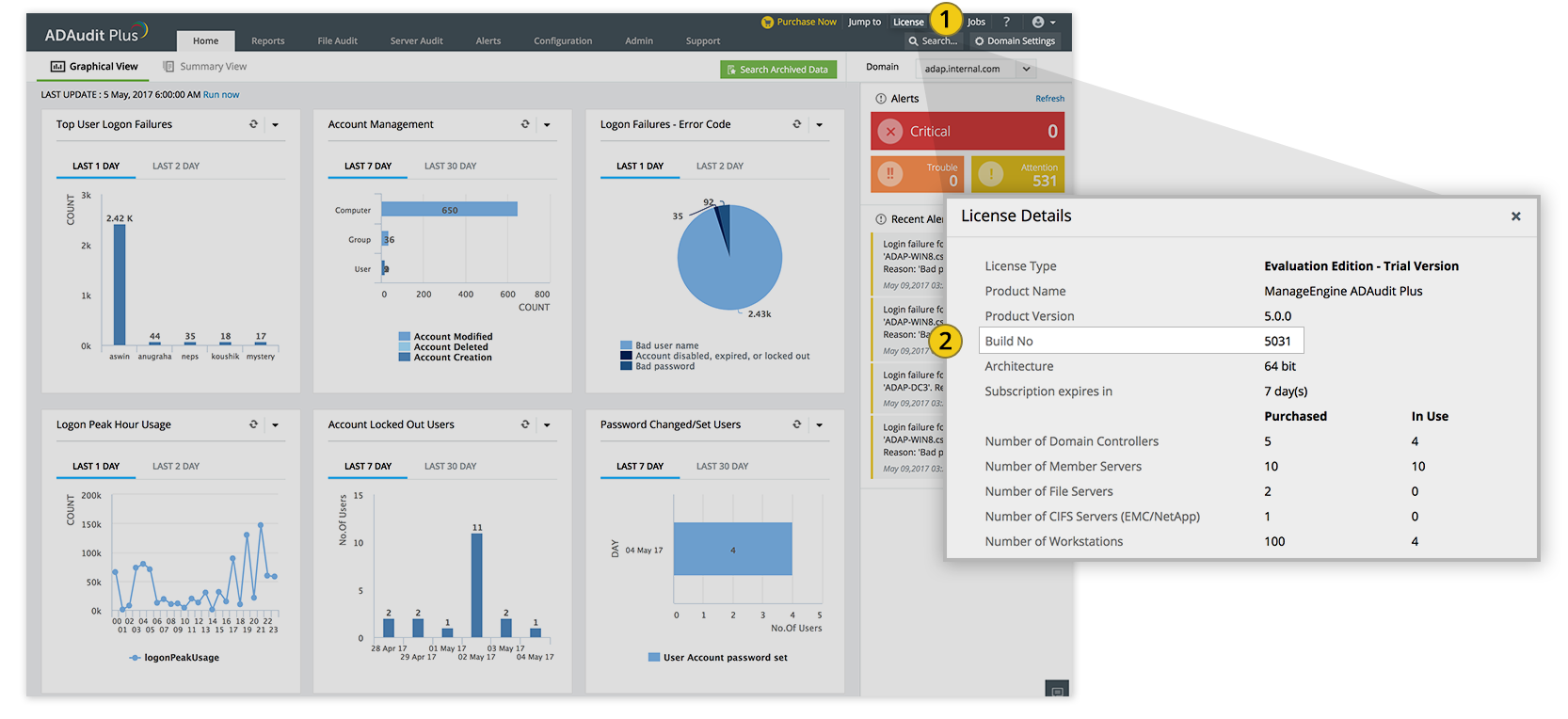
Affected Software Version(s): All ADAudit Plus builds below 7060 [How to find your build number]
Fixed Version(s): Build 7060
Fixed on: March 30, 2022
Details: ManageEngine ADAudit Plus had some vulnerable API endpoints that allowed an unauthenticated attacker to exploit XML External Entities (XXE), Java deserialization and path traversal vulnerabilities. The chain could be leveraged to perform unauthenticated remote code execution. This issue has been fixed.
Impact: An unauthenticated attacker would be able to remotely execute an arbitrary code in the ADAudit Plus server.
Steps to upgrade: Update your ADAudit Plus instance to the latest version – 7065 – using the service pack.
Exploitation and Public Announcements: We are aware that a proof-of-concept exploit code is publicly available for the vulnerability described in this advisory.
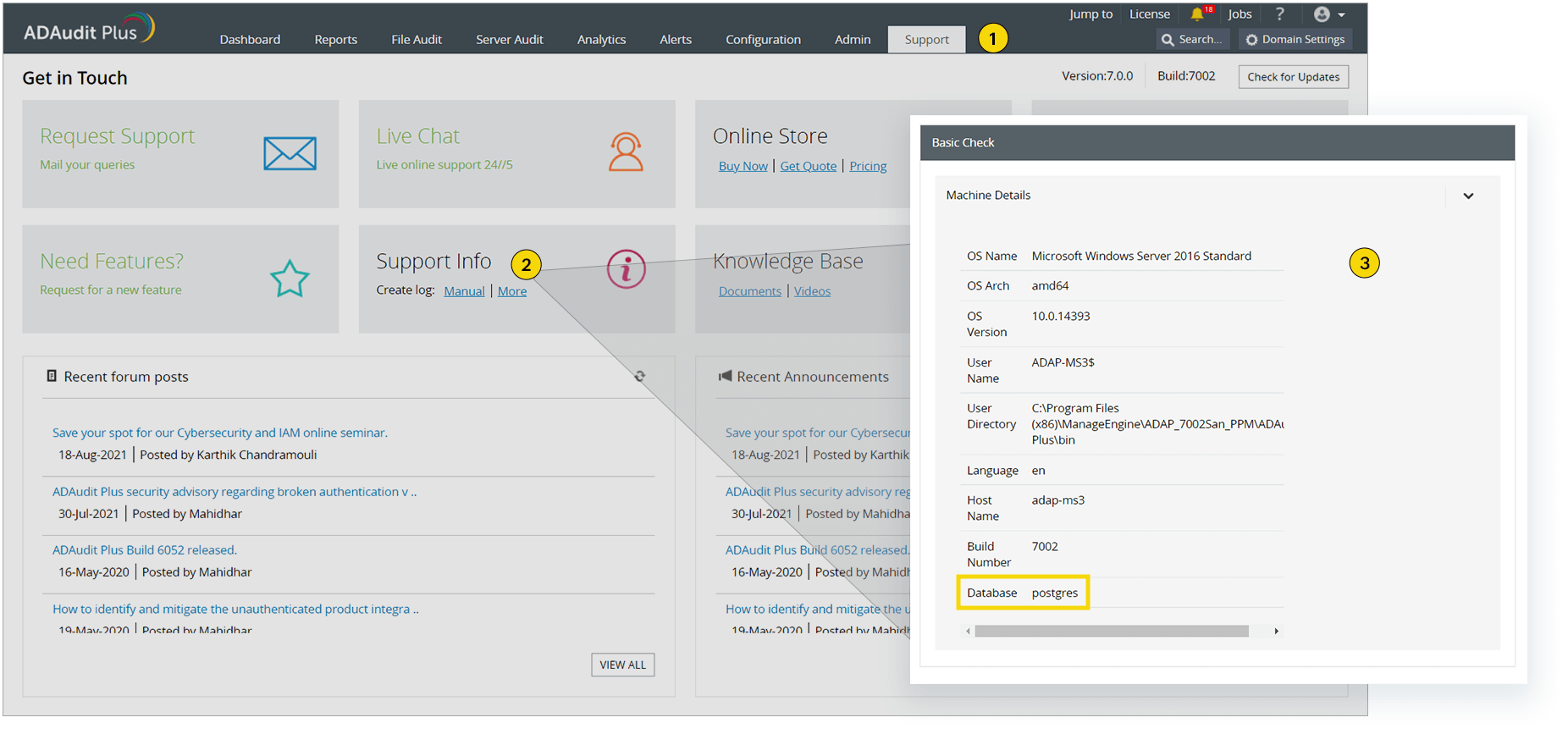
How do I check if my installation is impacted?
Please use our exploit detection tool to identify whether your installation has been impacted by this vulnerability. You can download the tool here. Once you have downloaded it, follow these steps:
Please reach out to support@adauditplus.com with logs for further assistance if your ADAudit Plus set up is impacted.
We strongly recommend that you update your ADAudit Plus installation to the latest version – 7065 – to mitigate this vulnerability.
Acknowledgments: This issue was reported by Naveen Sunkavally at Horizon3.ai.
Please contact support@adauditplus.com for more details.