What is kerberoasting?
Kerberoasting is a cyberattack in which an attacker exploits an inherent weakness in the Kerberos authentication protocol to ultimately gain access to an Active Directory (AD) service account.
How does a kerberoasting attack work?
To perpetrate a kerberoasting attack, the attacker must first compromise an existing user account within the AD domain. At this point, it does not matter how extensive the privileges of this account are. Once the attacker successfully takes over the user account, they proceed to carry out a kerberoasting attack by performing these five steps:
- Impersonate the user: The attacker starts by using the compromised user account to request the Kerberos ticket granting service (TGS) for a service ticket with the help of tools like Rubeus or GetUserSPNs.py.
- Obtain a service ticket: The TGS responds with a ticket that contains the password hash of the service account.
- Crack the password: The attacker then works offline using special tools like Hashcat or JohnTheRipper to crack this encrypted password hash.
- Hijack a service account: The attacker authenticates using the cracked service account credentials and gains elevated privileges as well as access to the associated services.
- Escalate privileges: The attacker then proceeds to further escalate privileges within the domain and perpetrate the more advanced Silver ticket and Golden ticket attacks.
Why are kerberoasting attacks so common?
Kerberoasting is growing popular among cybercriminals as evidenced by IBM's security analysts observing a 100% increase in kerberoasting incidents between 2022 and 2023. The following four reasons explain why kerberoasting is an attractive method for attackers to infiltrate and compromise your AD resources:
- Hard to detect: Kerberoasting does not require Domain Admin or other elevated privileges. A regular, unsuspecting domain user account could be compromised to carry out the attack, making it harder to detect using native tools.
- Inherent weakness: Although Kerberos is designed to be secure, it has an inherent weakness. The TGS does not verify the requestor's access to a service during authentication. This allows an attacker to request and obtain a service ticket for any service account and then proceed to crack the password hash and escalate privileges.
- Large attack surface: Most enterprises consist of vast Windows networks that use Kerberos to authenticate identities in AD. This makes them prime targets for kerberoasting, as a successful attack can give access to a lot of valuable resources and information.
- Remote execution: Attackers can carry out kerberoasting attacks remotely without interacting directly with the authentication server. This makes it challenging for defenders to spot and stop the attack in time.
How to protect against kerberoasting attacks
Given how common kerberoasting attacks are, it's vital for you take the right precautions to detect and mitigate them in your IT environment. Here are a few steps you can take to protect your organization from kerberoasting attacks:
- Enforce a strong password policy: A strong password policy is your first line of defense against kerberoasting. Encourage users to create long, complex passwords to reduce the risk of attackers compromising their accounts. For service accounts, use even stronger passwords that are at least 20 characters long. This makes it much harder for password-cracking tools to guess the password and break into these accounts.
- Enable strong encryption: Kerberos supports various encryption algorithms for securing password hashes during authentication. Weak algorithms, like RC4 encryption, can make it easier for attackers to decrypt a service account's password hash. To enhance security, ensure strong encryption, such as AES 256-bit, is used for service accounts.
- Don't add service accounts to privileged groups: Avoid adding service accounts to privileged groups like the Domain Admins group. While it's common to do this to prevent service downtime, it isn't safe. Administrators should limit service account access to only what is necessary. A couple of service account best practices to follow include creating separate accounts for specific tasks and always implementing the principle of least privilege.
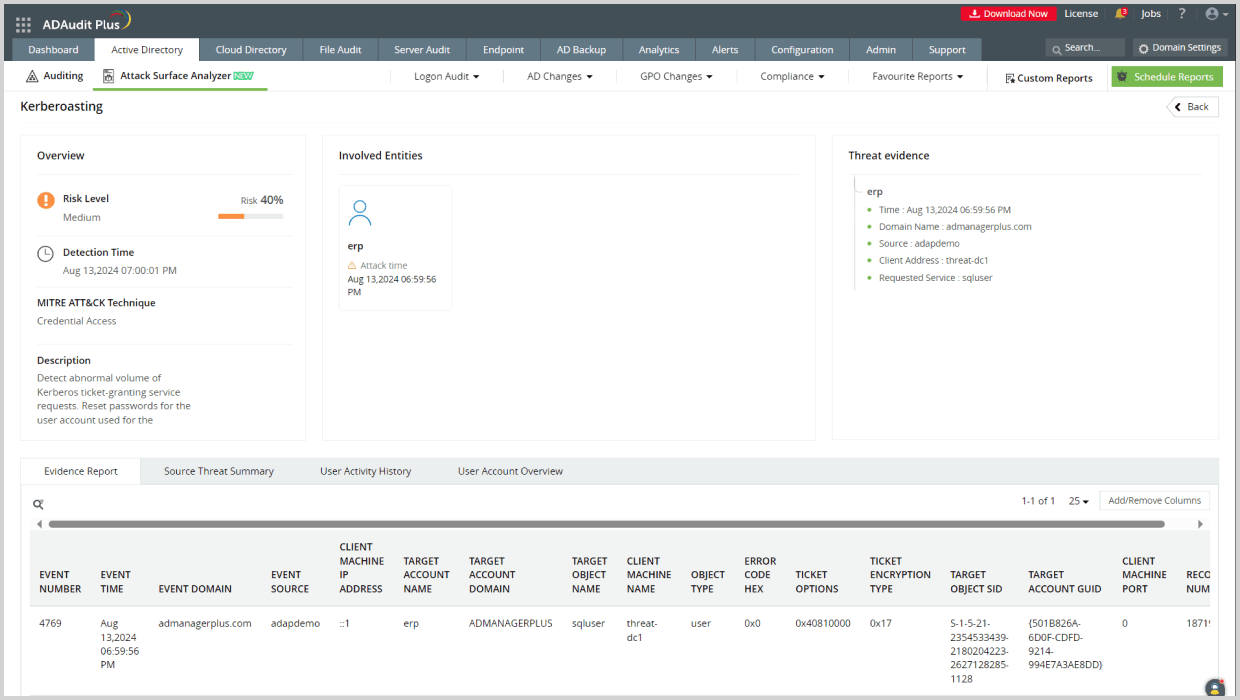
- Closely monitor Kerberos events: Monitoring your Windows environment for event ID 4769 is an effective way to detect kerberoasting attacks. This event is triggered whenever a user account requests a service ticket. If you notice a sudden spike in service ticket requests from a single user, it could signal suspicious activity. Typically, most service ticket requests are AES-encrypted and generally safe, whereas malicious requests often use RC4 encryption. Administrators can identify these by checking the Ticket Encryption Type field in the event details. If it shows 0X17, the request is RC4-encrypted and requires further investigation. Keep in mind that event ID 4769 is a noisy event, so this process can be time-consuming.
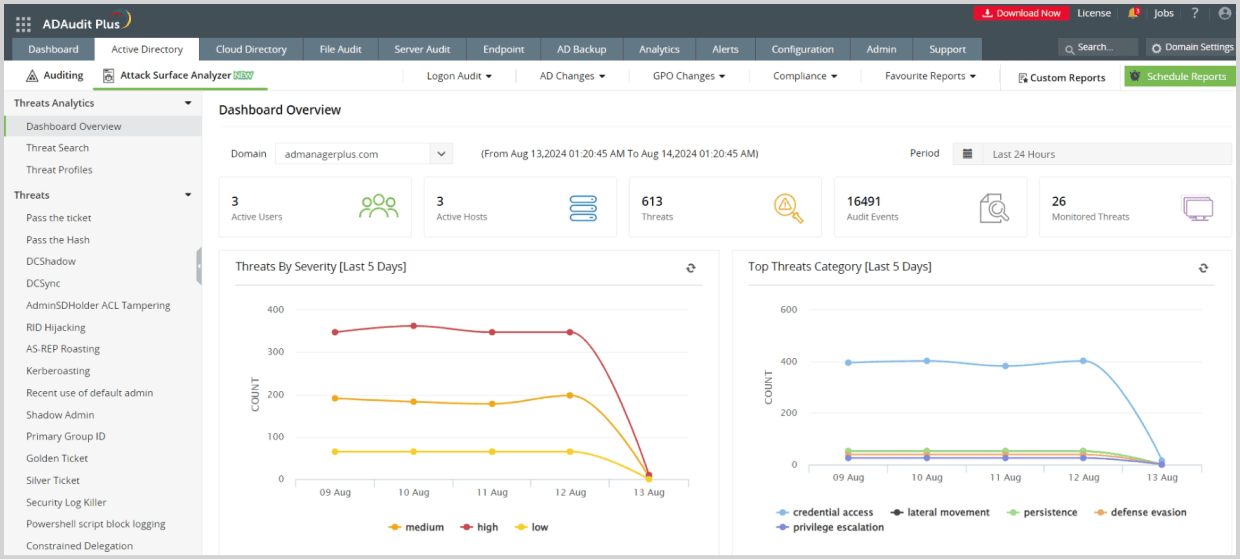
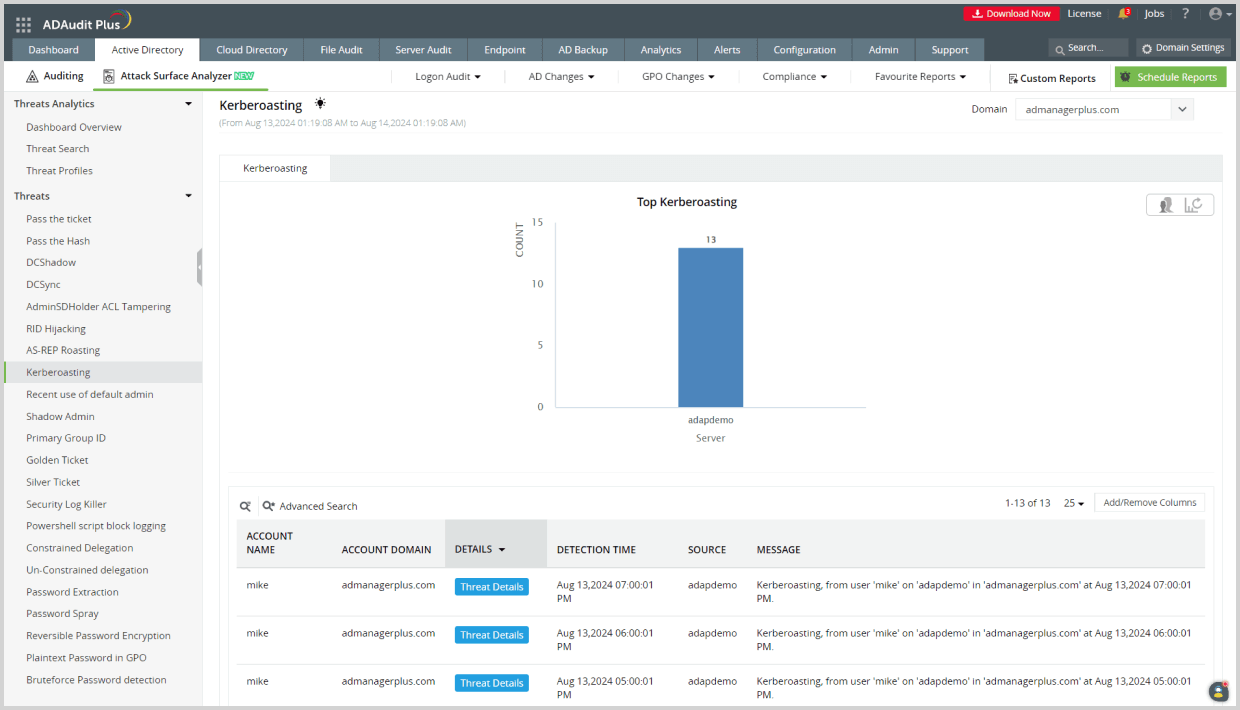
How ADAudit Plus can help you detect and mitigate kerberoasting attacks
ADAudit Plus' Attack Surface Analyzer features curated dashboards and specialized reports that help you detect and respond to kerberoasting attacks in real time. Powered by exclusive rules derived from the MITRE ATT&CK framework, the Attack Surface Analyzer delivers invaluable threat insights, enabling you to investigate potential kerberoasting attacks in just a few clicks.
Start protecting your on-premises and cloud AD resources with ADAudit Plus
Detect over 25 different AD attacks and identify potential misconfigurations within your Azure, GCP, and AWS cloud environments with the Attack Surface Analyzer.
See the Attack Surface Analyzer in actionWe're thrilled to be recognized as a Gartner Peer Insights Customers' Choice for Security Incident & Event Management (SIEM) for the fourth year in a row.