
- Overview
- Configuration
Halo ITSM
Streamline IT Operations with Halo ITSM and ADManager Plus Integration
By connecting Halo ITSM to your AD by integrating ADManager Plus, organizations can achieve greater efficiency, improve security, and maintain seamless, error-free IT service management. This integration enables IT teams to automate and streamline user provisioning, access management, and security operations within Active Directory from the Halo ITSM console.
Multi-platform user provisioning
Automatically create user accounts across various platforms, including AD, Exchange, Microsoft 365, and more, when new employees are added to the HCM application.
Reduce security risks caused by inactive accounts
Automatically delete or disable user accounts, remove their licenses, and more each time a user record is deleted in the HCM application.
Follow these steps to integrate ADManager Plus and HaloITSM:
- Open ADManager Plus and go to the Automation tab and click HCM Integrations from the left-side panel.
- Under HCM Applications, click Custom HCM to add a new HCM integration.
- In the Custom HCM Integration page, add the Name and Description of the integration. You can also add a custom logo for the HaloITSM tile.
- Click Save.
- Now, the HaloITSM tile will appear under HCM Applications. Click the tile to configure API authorization methods, endpoints, and LDAP data mapping.
- Under the Authorization section, select OAuth2.0 from the Authorization Type drop-down menu. Refer to HaloITSM's authorization document here.
- Enter the following details:
- Header Prefix: Specify a prefix value for your authorization header.
- OAuth 2.0 Grant Type: The authorization code is the default grant type.
- Callback URL: The Callback URL is where you will be redirected to after authentication. This should be registered with the API provider.
- Auth URL: Specify the Authorization Endpoint URL. (https://aus-trial.haloitsm.com/authorize?tenant=<tenantname>)
- Access Token URL: Enter the OAuth server URL where the application can exchange the authorization code for an access token. (https://aus-trial.haloitsm.com/token?tenant=<tenantname>)
- Client ID and Client Secret: Enter a valid ID and its secret key.
- Scope: Specify the permissions you want for the required action.
- Click Advanced Options and choose the headers and query parameters from the Add To drop-down menu.
- In the API Endpoint Configuration section, add the following:
- Endpoint URL: Enter the Endpoint URL. (https://<host>/api/Users) Note: Click here to view HaloITSM's API references.
- Click Advanced Options to add headers and parameters.
- Method: Choose between the HTTP request methods Get and Post.
- Headers: Click and configure the respective HTTP headers.
- Parameters: Cick and configure the query parameters.
- Message type: Select None.
- You can also check the Repeat calling this Endpoint option to repeatedly call the API until you get the required response, if needed. From the drop-down menu, select the parameter and specify the increment value. You can also set a condition, which when satisfied, calls the endpoint repeatedly. This step is required only when the complete user list retrieval needs repeated calls.
- Once done, click Test & Save. A response window will display all the requested elements.
- Click Data Source - LDAP Attribute Mapping to match endpoints and to map AD LDAP attributes with the respective attributes in the HCM solution.
- Enter the Configuration Name and Description, and select the Automation Category from the drop-down menu.
- In the Select Endpoint field, choose those columns that are unique to users (employeeIdenifier, username, etc.). The values in these columns should be consistent across all the endpoints.
- In the Attribute Mapping field, select the attribute from the LDAP Attribute Name drop-down menu and map it with the respective column in the HCM solution.
- Click Save.
Steps to generate the client ID and the client secret in HaloITSM
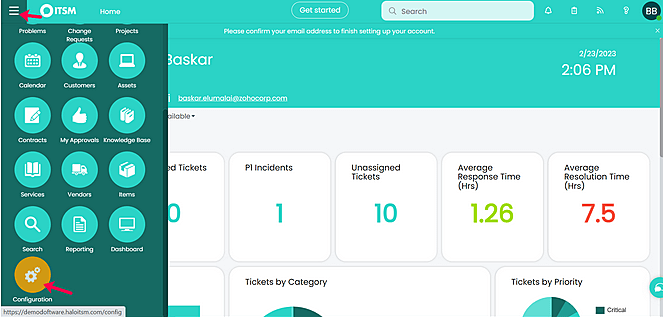
- From the home page of HaloITSM application, navigate to the menu bar in the left-hand corner and choose Configuration.
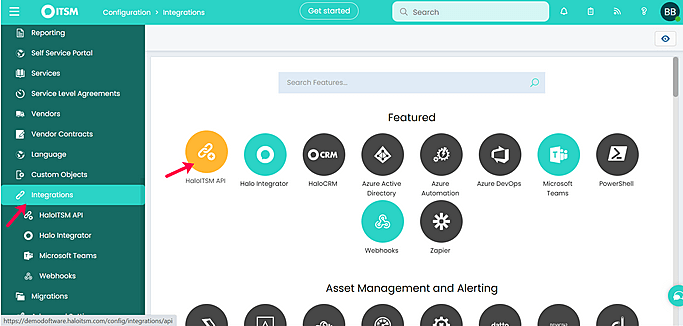
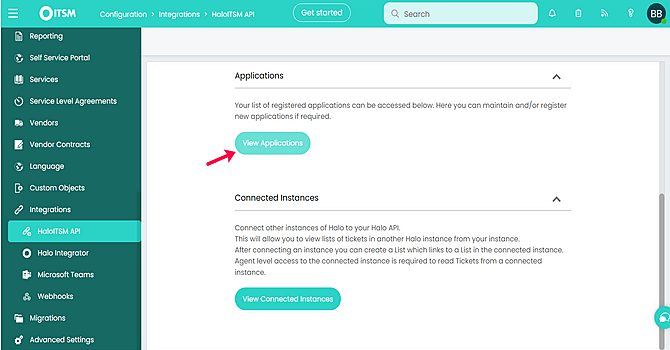
- Then, go to Integrations → HaloITSM API and choose View Applications → New.
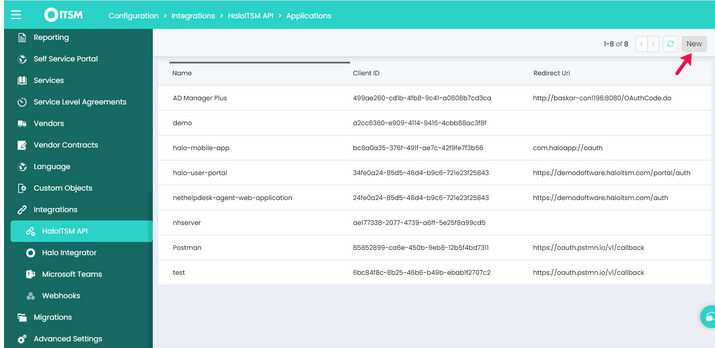
- In the Details page, select the required Authentication Method (e.g., Authorization code). You can now find the Client ID, Client Secret, Redirect URI, and other information required for authentication.
- In the Permissions page, select the required permissions. These permissions define what features this application can access. They must be specified in the scope parameter of any authentication request.
Sample Postman configuration to get access token
Required credentials:
- OAuth URL: https://aus-trial.haloitsm.com/authorize?tenant=<tenantname>
- Access Token URL: https://aus-trial.haloitsm.com/token?tenant=<tenantname>
- "response_type" - Must be "authorization_code"
- "client_id" - Must be your applications client id
- "redirect_uri" - Must be your applications redirect URI
- "scope" - Must include any application permissions that are required by your application; if unsure, set to "all”
- Navigate to Postman (postman.com).
- Fill in all the required parameters and click Get New Access Token.
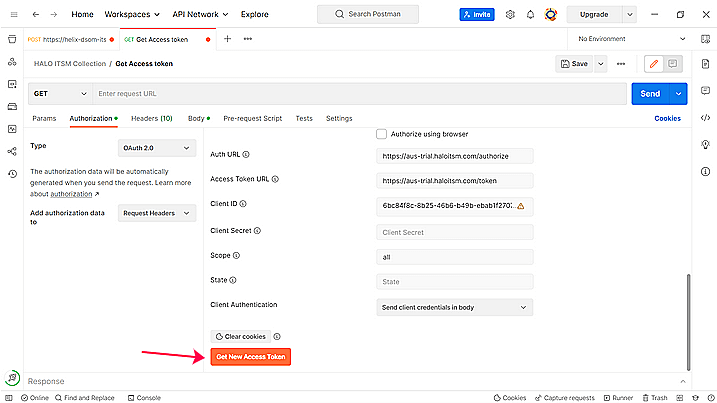
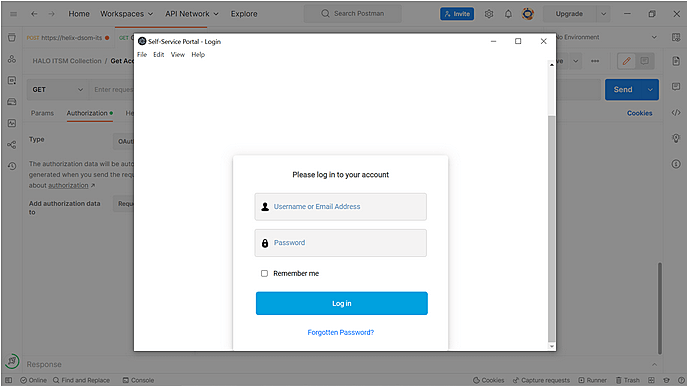
- In the HaloITSM login page that appears, enter your login credentials and authenticate yourself.
- Once the authentication is completed, the server should respond with Status code 200 if the credentials are valid. This response will contain the Access Token and Expiry Time as well as a Refresh Token if the offline_access is specified.
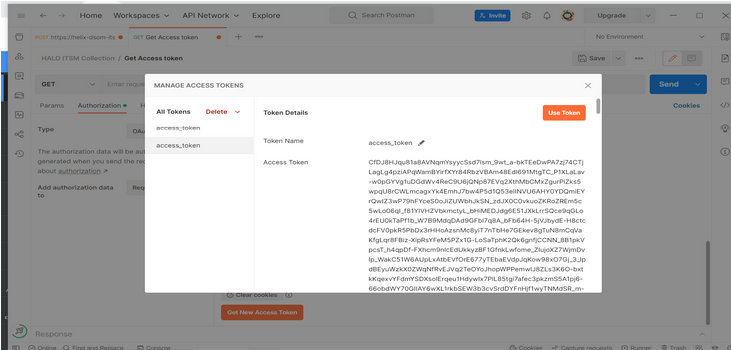
- Once you get the Access Token, you can use it in the API request. Here is an example of API integration to retrieve all the users:
- Method: GET
- API: https://<host>/api/Users
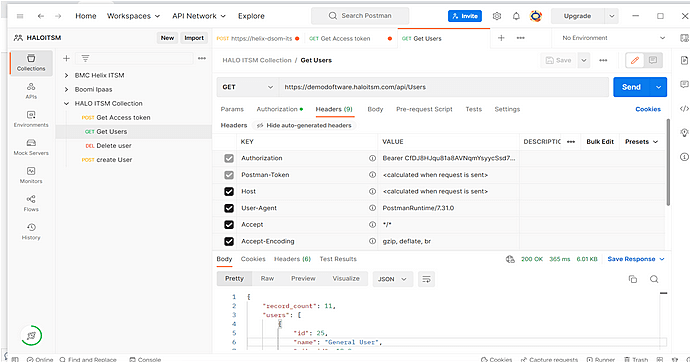
Sample response
{ "record_count": 1,
"users": [
{
"id": 26,
"name": "Baskar Balaji",
"site_id": 18.0,
"site_name": "Main",
"client_name": "DemoDoftware",
"firstname": "Baskar",
"surname": "Balaji",
"initials": "BB",
"emailaddress": "baskar.elumalai@zohocorp.com",
"phonenumber_preferred": "9092409380",
"sitephonenumber": "",
"phonenumber": "9092409380",
"telpref": 0,
"activedirectory_dn": "",
"onpremise_activedirectory_dn": "",
"login": "",
"inactive": false,
"colour": "#2bd3c6",
"isimportantcontact": false,
"neversendemails": false,
"priority_id": 0,
"linked_agent_id": 3,
"isserviceaccount": false,
"isimportantcontact2": false,
"connectwiseid": 0,
"autotaskid": -1,
"use": "user",
"client_id": 12
}
] } Actions supported:
Upon integrating HaloITSM with ADManager Plus, you can:
- Create user accounts
- Delete user accounts
- Disable user accounts
- Modify user account properties
- Remove Microsoft 365 licenses
- Add users to groups
- Remove users from groups
- Move users across groups
- Modify user attributes with templates
- Create mailboxes
- Disable mailboxes
- Delete mailboxes
- Reset passwords
- Move the Home folder
- Delete the Home folder
- Manage users' photos
- Configure auto-reply settings
- Disable Lync accounts
- Run custom scripts