COMPLIANCE > ESSENTIAL EIGHT
Key mitigation strategies in
essential eight
Maturity levels guiding
essential eight implementation.
Proportion of Govt entities achieving
essential eight maturity level 2 in 2024.
of cyber incidents reported are
from Australian public sector entities.
Cybercrime incidents reported to
ACSC in 2023-24
The Essential Eight, introduced by the Australian Cyber Security Centre (ACSC) in 2017, serves as a fundamental cybersecurity framework within the broader Strategies to Mitigate Cyber Security Incidents. While it is mandatory for Australian government agencies, the Australian Signals Directorate (ASD)—part of the Ministry of Defence—strongly advocates its adoption across all organizations. By proactively implementing the Essential Eight, businesses can significantly reduce their exposure to cyber threats. The cost of prevention is far less than the financial and reputational damage caused by a major cybersecurity breach.
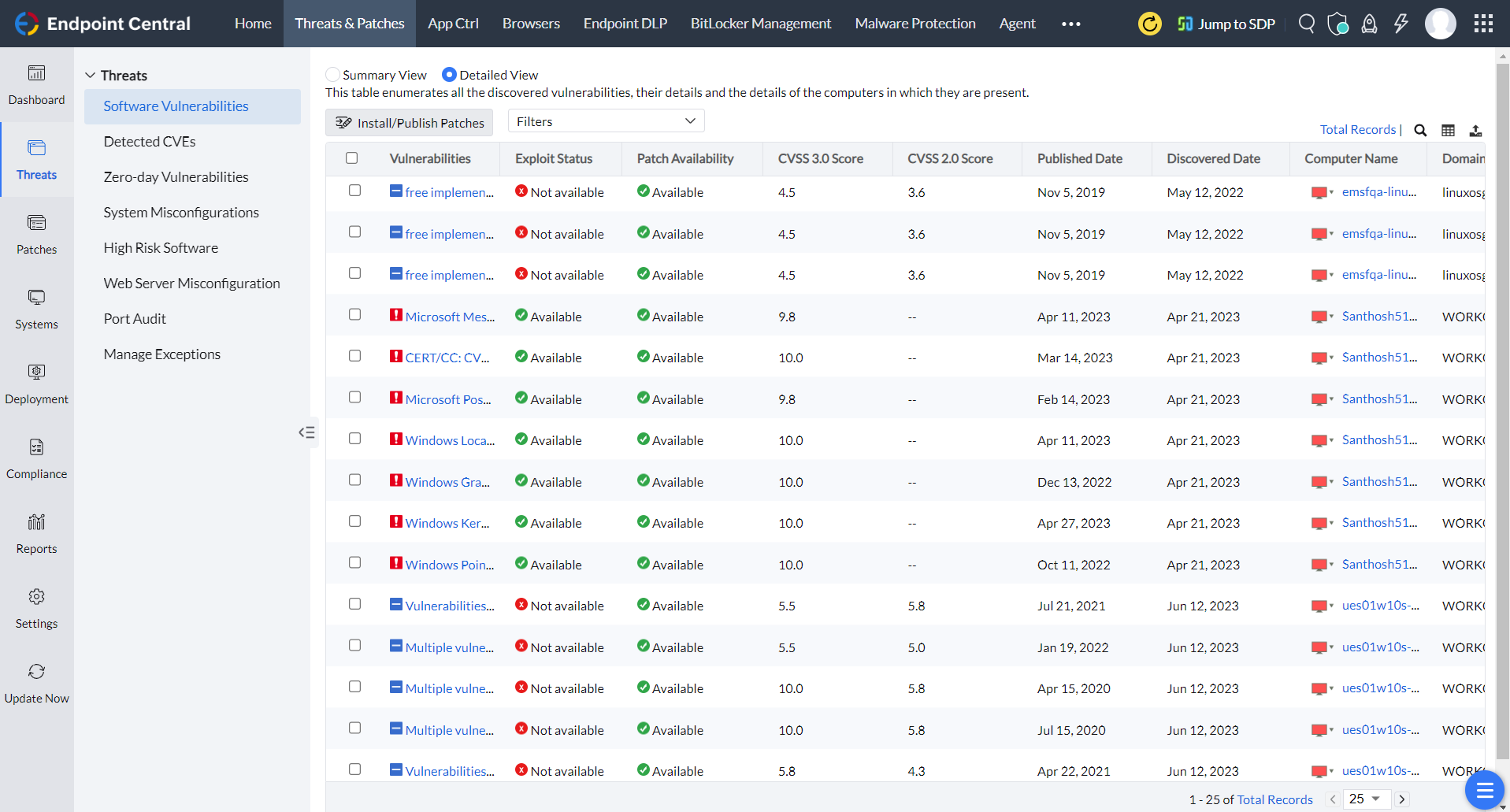
Endpoint Central ensures seamless patching and vulnerability scanning across Windows, Linux, macOS, and Windows Server environments. Beyond endpoints, it detects vulnerabilities across network devices, strengthening the organization's overall security posture. Effective patch management is pivotal for Essential Eight compliance, closing the door on known exploits before they become entry points.
Endpoint Central reduces attack surfaces by enabling application allow-listing and block-listing. It enables administrators to enforce the principle of least privilege, eliminate unnecessary local admin accounts, and provide Just-in-Time (JIT) access. This ensures that organizations strike the perfect balance between strong security and operational efficiency.
Endpoint Central's browser security capabilities allow organizations to restrict outdated browsers like Internet Explorer 11 while configuring modern browsers to mitigate browser-based threats and prevent data leaks. This enhances the organization's defense against malicious web-based attacks.
The Essential Eight Maturity Model is designed to guide organizations in implementing Essential Eight controls in a phased manner. It focuses on Techniques, Tactics, and Procedures of the cybercriminals (TTPs) to address evolving cyber threats. Each maturity level reflects the organization's cybersecurity resilience, from basic defenses to advanced protections. The latest version of the Essential Eight Maturity Model, released in November 2023, offers updated insights into evolving cybersecurity practices.
We have carefully aligned the features of Endpoint Central with the controls defined in the Essential Eight Maturity Model. By utilizing Endpoint Central, your organization can effortlessly incorporate these essential security measures into everyday workflows, ensuring a fortified cybersecurity framework. This alignment highlights how our solutions support and enhance your security efforts, reducing risks and improving resilience against potential threats.
Click here
We have comprehensively mapped the features of Endpoint Central to both the Essential Eight Maturity Model and the principles of Information Security Management (ISM). Information Security Management focuses on establishing robust security frameworks that safeguard critical assets and mitigate potential risks. By integrating Endpoint Central with these key security models, your organization can effectively apply ISM standards while implementing the Essential Eight controls. This holistic approach ensures that your cybersecurity strategies are not only aligned with industry best practices but also continuously evolve to meet emerging threats, enhancing your overall security posture.
Click here
"Endpoint Central has allowed us to move towards our goal of a centralized application to cover off IT support activities. The deployment was really simple with no real issues. We use it mainly for the integration with ServiceDesk Plus and the reports it provide for our ISO implementation"

Feel free to connect with our experts to address your specific queries and discover how Endpoint Central can assist you in meeting Essential Eight requirements.