COMPLIANCE > ISO 27001
Clauses in ISO/IEC 27001
defining security requirements.
Security controls in
ISO/IEC 27001:2022 framework.
ISO member countries
ensuring global reach.
Total ISO standards
covering various industries.
Growth in ISO/IEC 27001
certifications in a decade
The International Organization for Standardization (ISO) is a global non-governmental organization (NGO) that develops and promotes standards to ensure quality, safety, and efficiency across industries worldwide. Established in 1947, ISO currently has 160+ member countries, each represented by its national standards body (e.g., BIS from India, ANSI from the USA). These members collaborate to create internationally recognized standards that help organizations achieve consistency and excellence.
ISO/IEC 27001, jointly developed by International Organization for Standardization (ISO) and International Electro Technical Commission(IEC), provides a comprehensive framework for establishing, implementing, and managing an Information Security Management System (ISMS). This standard helps organizations safeguard their sensitive information through robust security practices.
With Endpoint Central, organizations gain detailed insights into their endpoint ecosystem through intuitive dashboards and reports. It provides extensive visibility into endpoint vulnerabilities, security misconfigurations, and overall health, ensuring a secure and compliant asset management strategy.
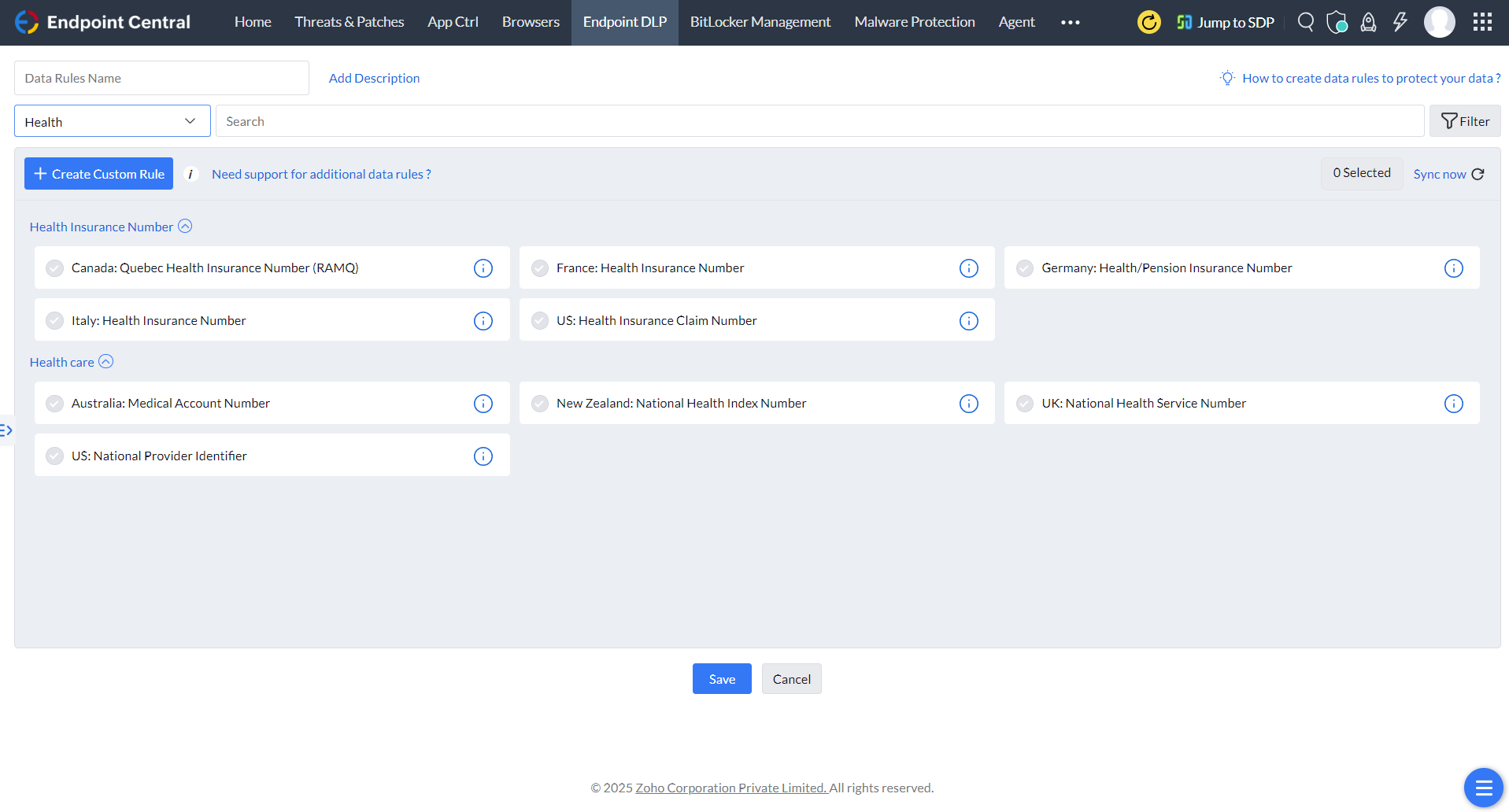
Endpoint Central's advanced data loss prevention capabilities empower organizations to classify and secure sensitive information, such as Personally Identifiable Information (PII) and Electronic Protected Health Information (ePHI). Its robust data leakage prevention features include restrictions on copying data to public clouds, clipboards, peripheral devices, and more.
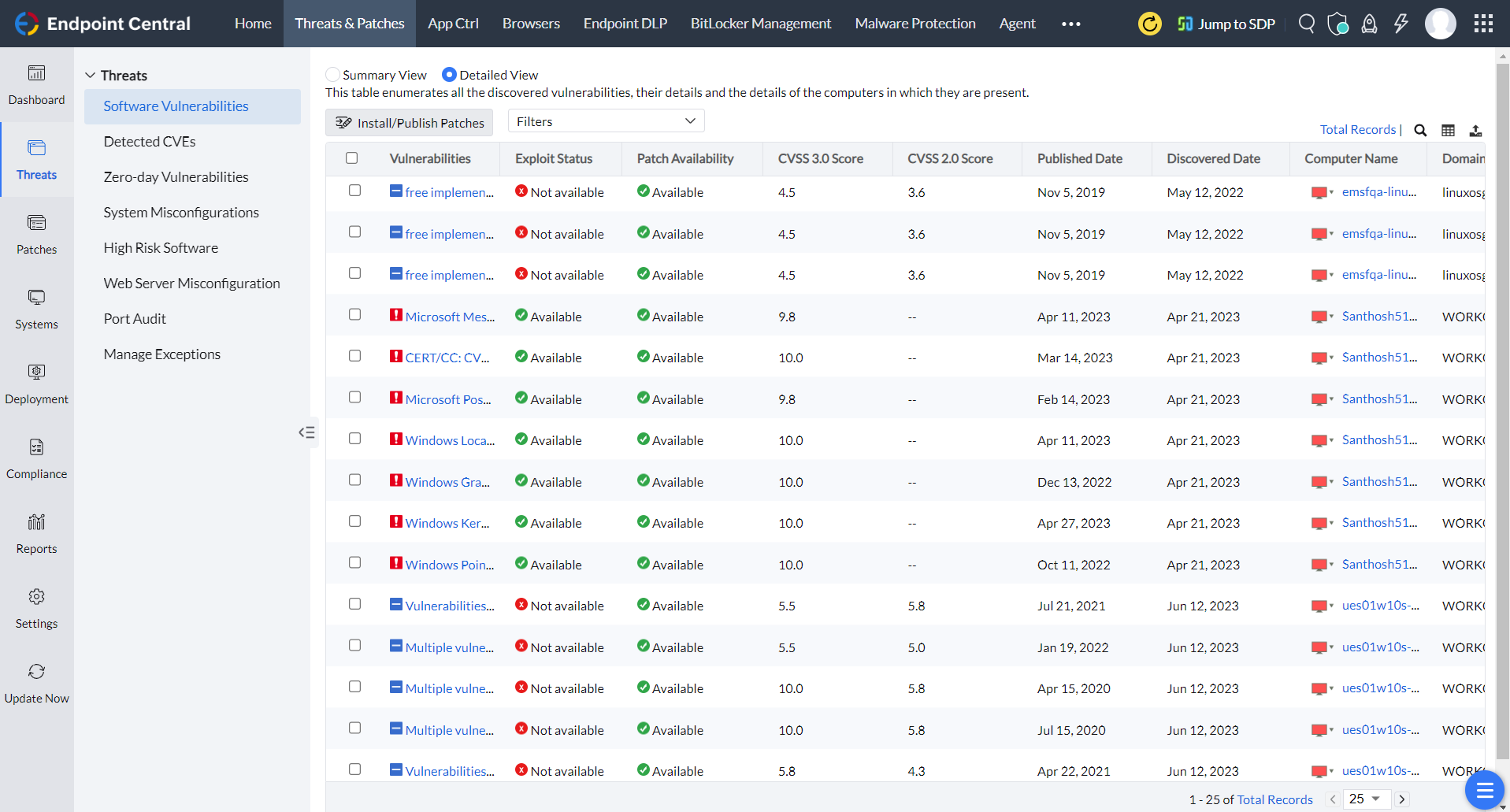
Endpoint Central's built-in vulnerability assessment tools deliver a thorough evaluation of network vulnerabilities. Additionally, its integrated remediation capabilities serve as a unified platform for IT Operations (ITOps) and Security Operations (SecOps), streamlining efforts to mitigate risks effectively.
The Information Security Management System (ISMS) is a set of policies, procedures, and controls designed to protect an organization’s information assets. It addresses various aspects of information security and is organized into the following key areas:
We have meticulously mapped the features of Endpoint Central to the information security controls outlined in Annex A of ISO/IEC 27001. By leveraging Endpoint Central, your organization can seamlessly integrate ISO 27001 practices into daily operations, ensuring robust information security management. This mapping demonstrates how our solutions align with and support your compliance efforts.
Click here
YKK Lanka became the the first manufacturing organization to obtain ISO 27001 in Sri Lanka. Endpoint Central's reports are very important for our internal and external ISO 27001 audit purposes. From 2009, for last 15 years , we are using Endpoint Central and saved a lot of IT time but never increased our overheads in IT department. [sic]

Feel free to connect with our experts to address your specific queries and discover how Endpoint Central can assist you in meeting ISO requirements.