IT Asset Management is the process of managing an organization's IT assets throughout their lifecycle, right from provisioning, monitoring, maintenance, and upgrades to disposal. This process comprises the hardware, software, and network resources, to ensure that they are utilized optimally and cost-efficiently, and adhere to the industry-wide compliances. For streamlining IT asset management, organizations today leverage ITAM solutions to automate the workflow and manage assets better.
IT Asset Management Software is a program that manages and monitors the IT assets found in a network. With the help of IT asset management solutions, an asset can be tracked for its entire duration in the organization. You can manage LAN as well as work from home endpoints from a central location. Using IT Asset management (ITAM) software, you can manage both hardware and software assets in your network anywhere, anytime, from your laptop or mobile phone.
Similarly, an ITAM software also helps in keeping track of digital assets. With the help of asset scans available in an ITAM software, you can easily configure alerts to notify you regarding any change detected in the hardware or software inventory. Endpoint Central's IT Asset Management Software, along with its unified endpoint management functionalities is one of the best ITAM software that offers effortless management of physical and digital assets along with predefined inventory reports and email notifications to track, monitor and manage everything from a single console.
Key Features of IT Asset Management Software
Here is a complete list of IT asset tracking and management features offered by us for a comprehensive IT asset management (ITAM):
- Periodic Asset Scans
- Software License Management
- Hardware Warranty Management
- Real-Time Inventory Alerts
- Software Metering
- Certificate Management
- Geofencing
- Power Management
- USB Device Management
- Software and Hardware Inventory
- File Scanning
- Prohibit Software and Block Executables
Periodic Asset Scans
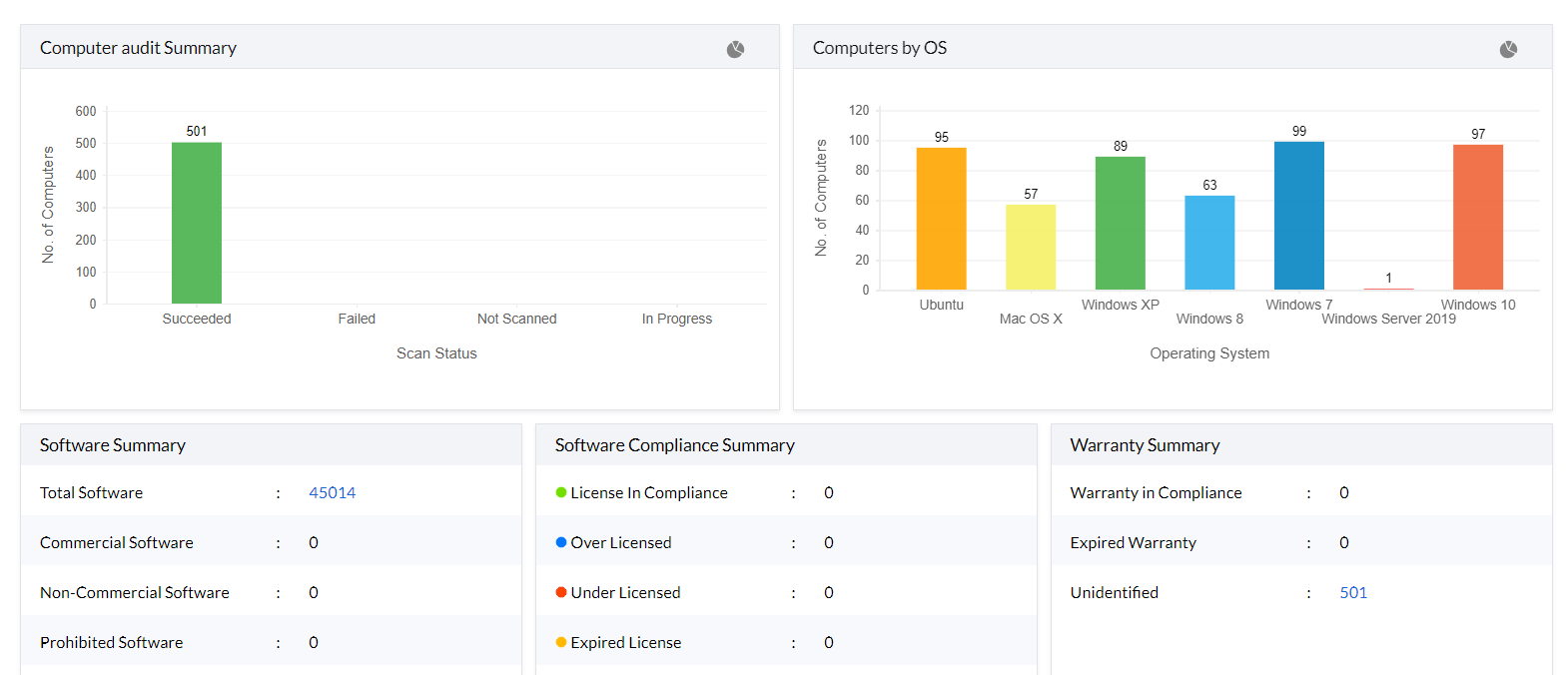
In today's fast-paced world, devices are replaced or upgraded within the blink of an eye, at an alarming frequency. It is your job as an IT Administrator to keep track of all these changes/additions using an IT asset management system and ensure that only authorized devices are connected to your network. This IT asset tracking and management software scans your network periodically to fetch software and hardware inventory details and detect any changes in your network. You can perform asset scanning in the following ways:
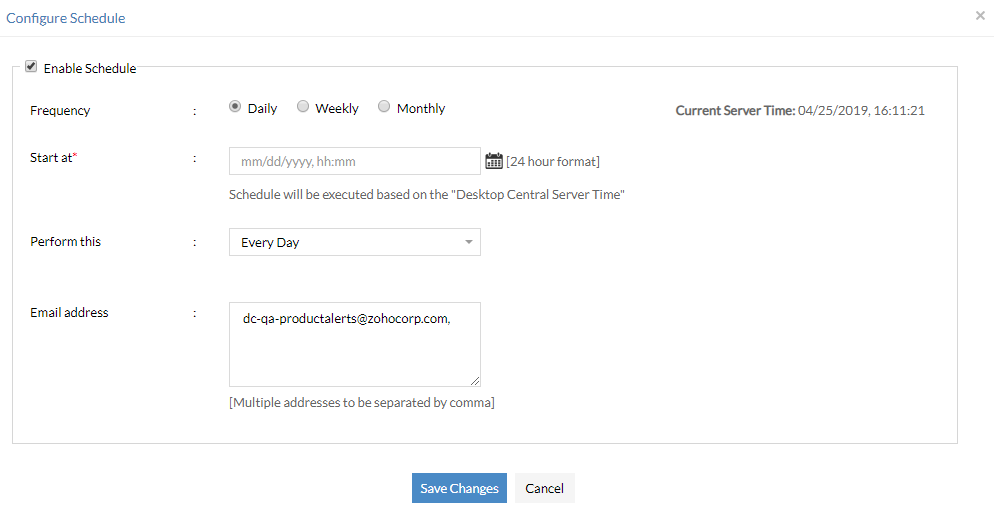
- Post-install
This scan is initiated when the agent is installed on the machine for the first time. It occurs immediately after the installation of the agent to gather all necessary details of the machine.
- Scheduled
This type of scan is scheduled in advance to run at specific intervals or times. It's a regular, automated scan that occurs based on a predefined schedule.
- Scheduled-user
Similar to a scheduled scan but these are triggered when a scan is scheduled at a pre-defined time, and a less privileged user happens to be logged into the system.
- Notify
A notify scan is triggered when a software is installed or uninstalled. It occurs as a response to changes in the system software configuration, alerting the system to perform a scan in response to such events.
- Notify-user
This scan is similar to the notify scan but focuses on user-specific software. It's triggered when user-specific software is installed or uninstalled.
- On-demand
This scan is initiated manually by the Administrator from the server. It allows for immediate, user-initiated scans when there is a need for specific system checks or troubleshooting.
- Tray-icon
A scan that is manually triggered by the user from the agent tray icon. Users can initiate this type of scan through the system tray, providing them with a convenient way to perform scans when needed.
- FS-server
This is a quick scan triggered by the server when the previously parsed differential data is only partially saved in the server. The full scan ensures that the necessary details is entirely parsed to the server.
Software License Management
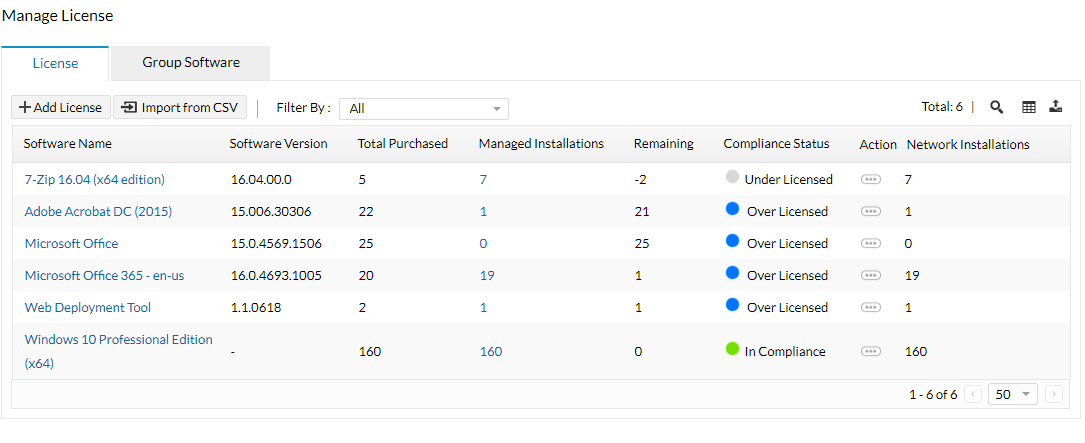
An IT asset management system ensures you're license compliant at all times and helps you steer clear of hefty non-compliance fines during a software audit. ManageEngine's IT asset tracking and management software makes this process a whole lot easier by detecting your compliance status automatically. When a software is found to be under-licensed, you can either add more licenses or uninstall the software from required number of computers using ManageEngine's Asset Management software - Endpoint Central. These functionalities are also available on the Endpoint Central mobile app
Learn more about software license compliance.
Hardware Warranty Management
Keeping track of hardware warranty with an IT asset management tool can help you save unnecessary maintenance costs. This IT Asset Management software greatly assists in computer asset management by automatically detecting warranty details for Dell, Lenovo, Toshiba and HP devices. The asset management software also has pre-configured reports for computers with about-to-expire warranty and computers for which the warranty has expired already.
Real Time Inventory Alerts
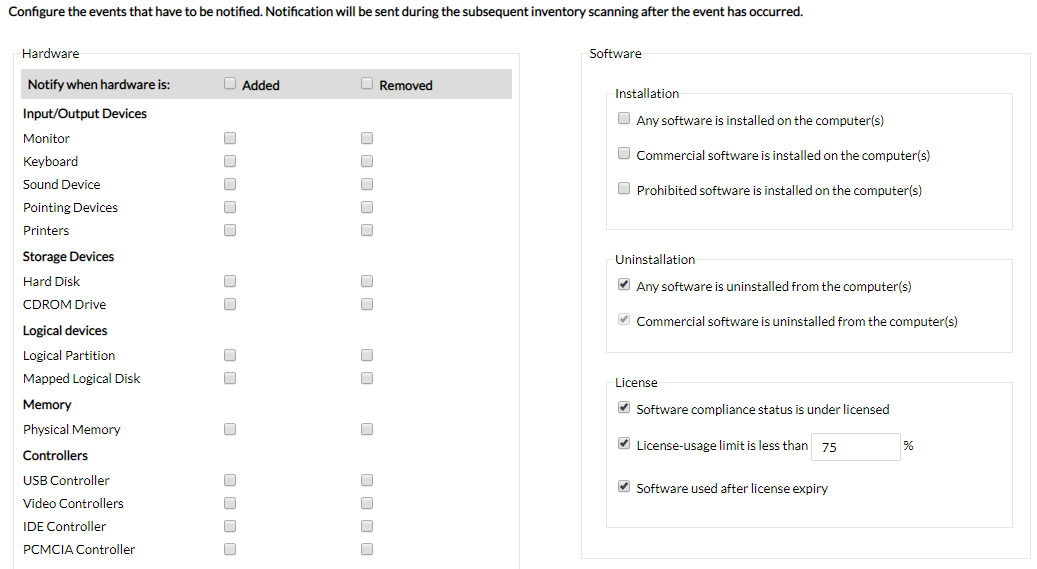
With the help of this asset tracking software you can set up real-time notifications for whenever a new software is installed, a hardware component is added/removed, software is under licensed or is being used after license expiry, commercial software is installed/uninstalled, disk space on a computer falls below a specified percentage, and more in just a few clicks.
Software Metering
You can cut down on significant expenses with an IT asset management tool by monitoring the usage of commercial software, and ensuring that you're using the licenses efficiently. With Endpoint Central, Software asset management is now easier; you can view detailed reports and determine whether the software usage justifies the cost, which helps you make informed procurement decisions.
Certificate Management
In addition to using passwords for security and authentication, many organizations now prefer to use digitally signed certificates for authentication before allowing users to access Exchange servers, Wi-Fi, VPNs, and other such applications. Create, distribute, and renew digitally signed certificates with Endpoint Central.
There are two types of certificates that are commonly used:
- Trust certificates
A single trust certificate is used by admins to authenticate all users in the organization. The certificate must be present on the device in order for the user to be able to authenticate their devices. This can be done by distributing the certificate using Endpoint Central.
- User-specific certificates
Certificate Authorities (CAs) are responsible for issuing certificates to organizations and create certificates for each user. When integrated with Endpoint Central, the CA authority creates and distributes these certificates.
Geofencing
A geofence is a virtual fence based on a geo-location range that ensures certain actions are performed on the device automatically when it leaves the specified range. It creates a virtual defense to protect corporate devices containing sensitive enterprise data that cannot leave a certain location/range.
Endpoint Central ensures devices leaving the geofence are automatically marked as non-compliant and thus, triggers a set of actions - from passive actions such as notifying administrators, locking the device, wiping the device data or executing preferred security commands.
Power Management
By managing and optimizing the power consumption of hardware in your network, Endpoint Central saves you money and energy.
- Create, modify, and apply power schemes based on branches/departments/job roles.
- Shutdown, hibernate or standby an idle computer to save power consumption.
- Monitor the battery levels of critical business devices.
- In older models that do not support power schemes, you can turn off the screensavers.
Read more on power management here.
USB Device Management
Pen drives, CDs, and any other portable storage devices can jeopardize your company's data or security if not monitored by your IT team. By blocking or disabling USB devices, you can limit their use based on the roles and departments. You can restrict not only by computer and user level, but also by manufacturer type, facilitating more accessibility. Enable/disable the following USB devices for users and computers:
- Mouse
- Disk drive
- CD-ROM
- Floppy disk
- Bluetooth
- Image
- Printer
- Modem
- Apple USB Devices
- Portable storage devices
Instead of disabling or enabling USB devices, you can choose to just record these activities for future auditing. Endpoint Central helps track the usage of USB devices and provides you with all the necessary information such as:
- Device name
- User name
- Device type
- Time duration
- Manufacturer and more.
Read more on USB device management here.
Software and Hardware Inventory
Staying up-to-date and informed about the assets present in your network is one of the benefits of ITAM. The IT asset management solution empowers you to make data-backed decisions about acquiring new assets, which will lead to cutting unnecessary expenses. ManageEngine's IT Asset Management (ITAM) software, Endpoint Central, offers in-depth reports related to both hardware and software asset management along with all the relevant metrics, and this information is easily accessible from your mobile phone, using mobile app.
File Scanning
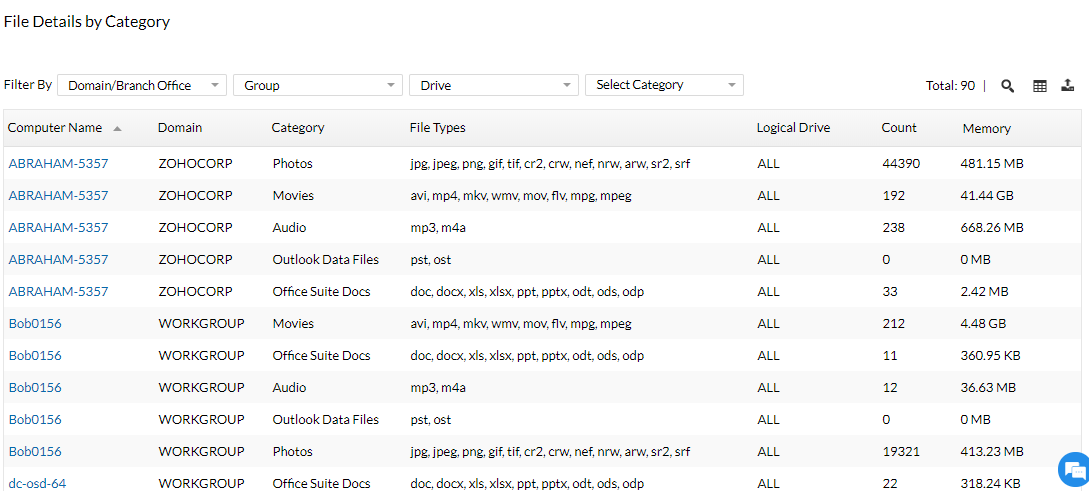
Using asset tracking software, gain visibility on the type of files present in your network by setting up rules and scheduling scans. An IT asset management software allows you to set up file scan rules(audio, video, documents, etc) and determine how much space is being occupied by these files. If required, you can notify users to delete unnecessary files on computers with low free disk space using an ITAM tool.
Prohibit Software and Block Executables
As a system administrator, you need to ensure that none of the computers have any prohibited software installed on them. Using this IT asset management software, you can prohibit software and create an auto uninstall policy within a few clicks. You also have the option to notify the user and request them to uninstall the software on their own with an IT asset management system. In some cases, malicious software doesn't need to be installed on the computer and can be run from an external drive. Our IT asset management solution allows you to prevent the usage of such applications by blocking these executables. This will prevent the application from being executed which will in turn prevent attacks/data breaches.
Overview of the ITAM process
The ITAM process can be easily simplified with a unified ITAM software in place. Here's an overview of the IT asset management process:
- Inventory management: The ITAM process begins with comprehensive inventory management, where all the IT assets (software, hardware, and other digital resources) across the organization are onboarded on the unified ITAM software console.
- Asset tracking: By leveraging IT asset management solutions, the process also involves continuous asset tracking to monitor the lifecycle of each asset from procurement, and licensing to disposal, ensuring accurate records of location, usage, and status.
- Configuration and lifecycle management: The IT asset management process encompasses configuration and lifecycle management, which includes planning, acquisition, deployment, maintenance, and retirement of IT assets. Additionally, the hardware and software configurations are standardized to ensure consistency, compatibility, and compliance with organizational standards and industry regulations.
- Security and compliance monitoring: Another important aspect of the endpoint asset management process is to monitor security and compliance. By leveraging a unified ITAM software, admins can monitor software licensing agreements, regulatory requirements, and internal policies via continuous monitoring and audits. Furthermore, the ITAM process also safeguards IT assets against cyber threats, thereby ensuring data privacy.
- Reporting and Analysis: The IT asset management process also involves generating reports and conducting analysis to provide insights into asset utilization, costs, risks, and performance metrics, enabling informed decision-making and continuous improvement of IT asset management practices.
IT Asset Management (ITAM) Best Practices
Because of the sheer number of assets in enterprises, IT asset management can be intimidating. Here are a few of the IT asset management best practices you can weave into your existing ITAM strategy to ensure optimum results:
- Keep redefining and evolving your strategy. IT asset management (ITAM) is not a destination, but an automated process and needs to be treated as such. Leveraging automated ITAM tools ensures that the endpoints are discovered and assessed, as soon as provisioned into the network.
- Set up real-time notifications for any hardware/software changes within your network in your IT asset management software, so that you can detect anomalies and remediate them right away.
- Before renewing the license for commercial software, analyze the usage statistics thoroughly to ensure you buy only what is required. Accurate reports from IT asset management software helps you make informed decisions with minimal effort. Furthermore, such real-time reporting also ensures that your endpoints are compliant and helps secure the IT environment.
- Enable real-time alerts for:
- When the license status is under-compliant
- When a commercial software is installed/uninstalled within your network
- When the license for a commercial software is about to expire
IT Asset Management Made Simple
IT asset management is, as stated above, performing certain operations on hardware and software assets of the organization like identifying, discovering, procuring, managing, monitoring and disposing them. All types of IT Asset Management like Hardware Asset Management, Software Asset Management and Digital Asset Management are of critical importance for the smooth functioning of any organization.
As assets play a huge role in ensuring a productive workflow of an organization, managing them by a suitable IT asset manager is of paramount importance. By monitoring and managing assets with an ITAM software to reduce the turn-around-time in replacing or repairing damaged assets, organizations can save a lot of time, manpower and money.
ManageEngine's Endpoint Central is one of the best IT asset management software that helps an IT administrator in automating many of the routine tasks and offer a comprehensive overview of the status of assets in the network. A simple IT asset management software like Endpoint Central makes your entire asset management process easier yet effective. Don't believe us? Download our ITAM software for free and see for yourself.
If you are looking for an exclusive MSP-centric solution for endpoint management, Endpoint Central MSP today!

"Endpoint Central provides me with a complete inventory of all of my hardware and software assets. This helps me to track the status of my assets, identify any potential problems, and make better decisions about IT spending."
Adnan R,
Review collected by and hosted on G2.