COMPLIANCE > NIS2
industries in
spotlight
ensuring comprehensive coverage
hold the secret sauce of NIS2
core cybersecurity themes
potential cost of non-compliance
In today’s world of relentless and advanced cyber threats, protecting IT infrastructure is more critical than ever. As businesses become increasingly interconnected and data-driven, vulnerabilities are growing—and so is the need for a solid cybersecurity framework.
This is where the NIS2 (Network and Information Security) Directive steps in. Designed to raise the bar for cybersecurity across the EU, it addresses critical gaps and extends protection to more sectors than ever before. Building on its 2016 predecessor, the updated NIS2 Directive strengthens defenses for Europe’s critical infrastructure and sets a new standard for security.
Effective since January 2023, the directive came into force from October 18, 2024.
Endpoint Central equips you with everything necessary to maintain top-tier cyber hygiene—patching devices, encrypting data, blocking unauthorized privilege escalation, preventing data leaks, and managing USB access.
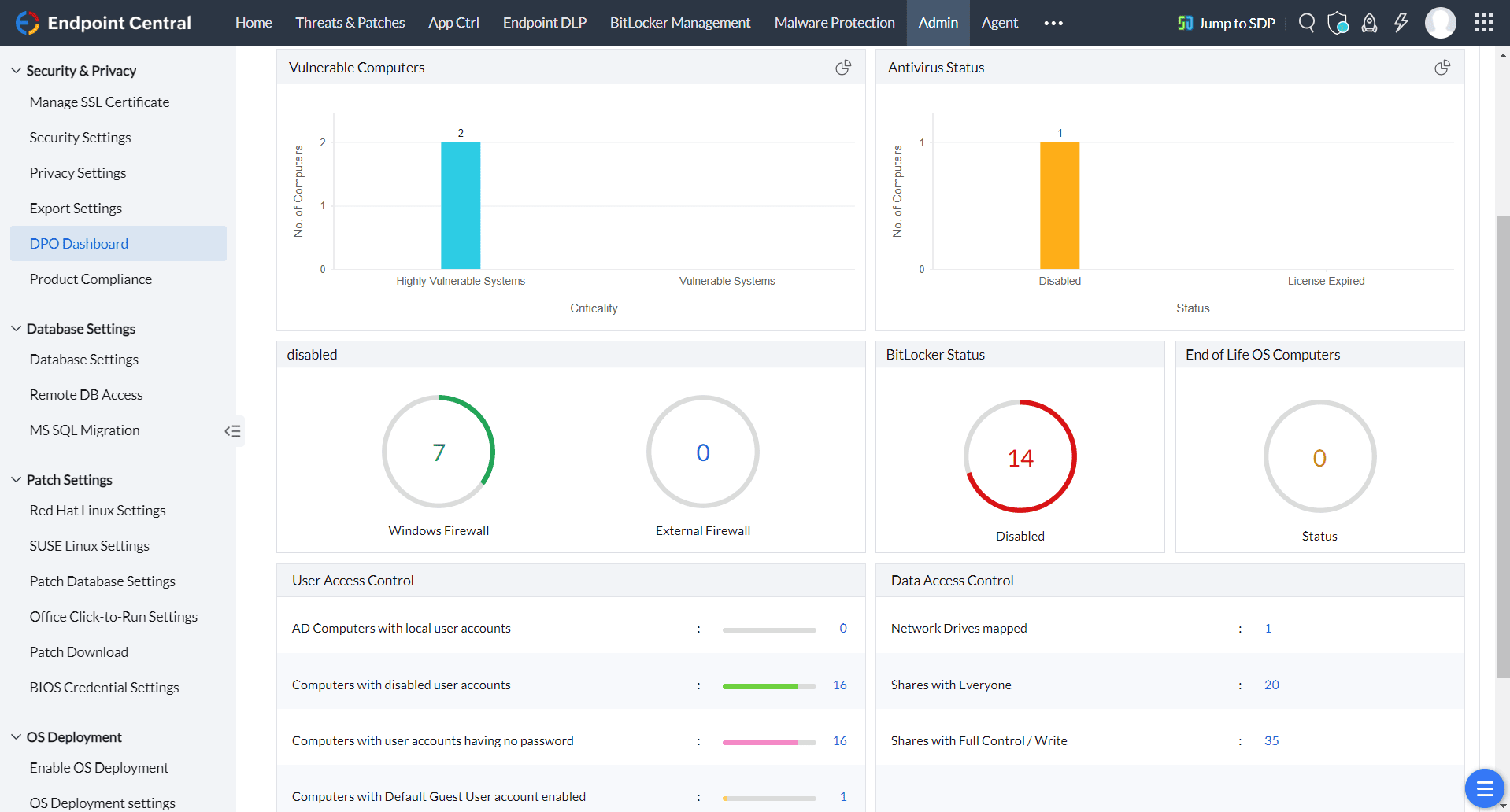
Tailored for seamless compliance, Endpoint Central delivers audit-ready reports and dynamic dashboards, offering clear, real-time insights into risks and vulnerabilities across your IT landscape.
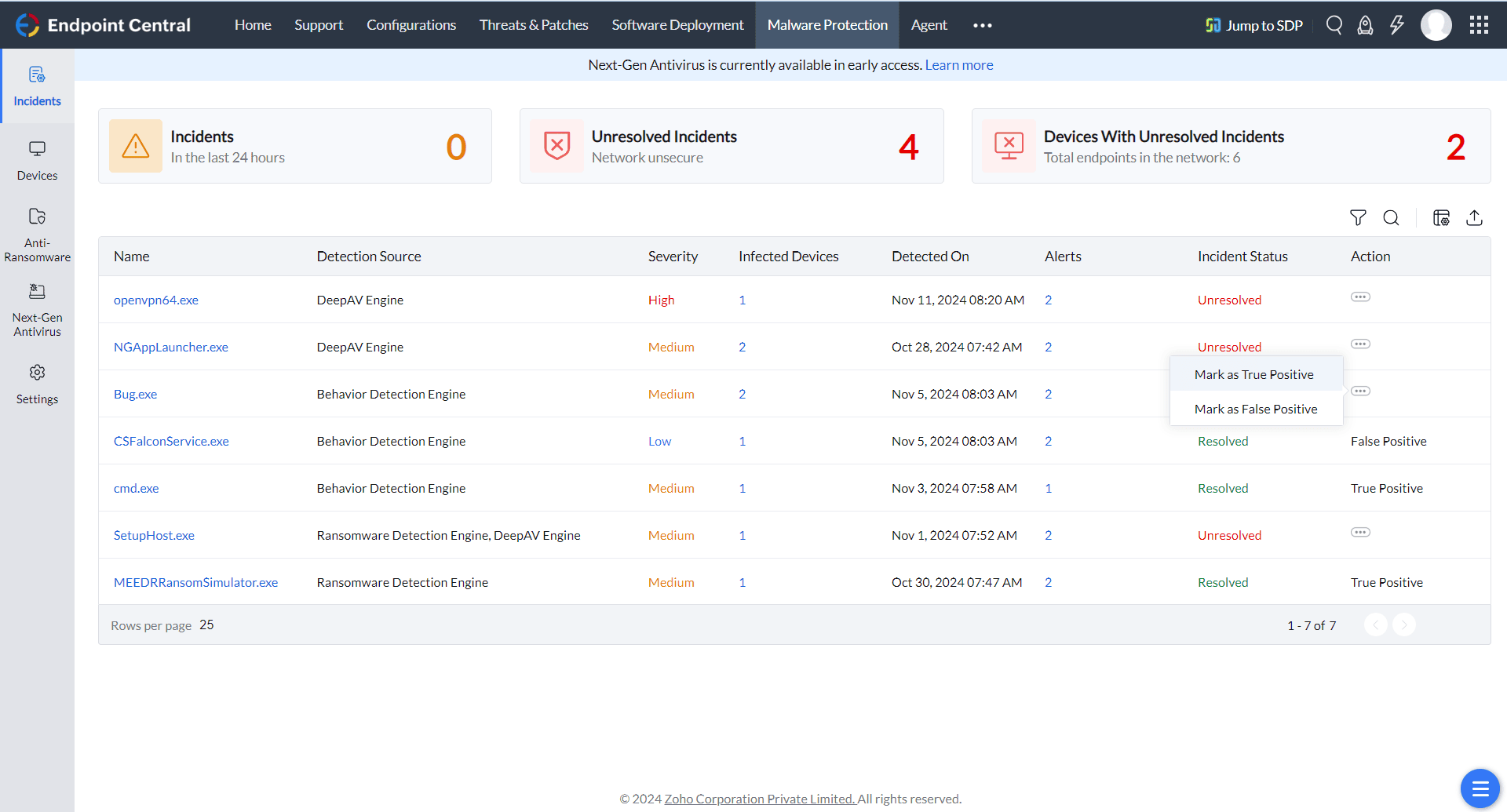
Unlock full IT visibility with advanced asset management capabilities, while its robust anti-malware features safeguard your environment. With one-click data restoration and endpoint quarantine, business disruptions are minimized, ensuring smooth operations.
NIS 2 directive classifies industries into Essential and Important entities. Small and Medium Businesses (employing 250 or less and turnover less than €50 million) automatically fall under Important entities.
The NIS2 Directive brings a unified approach to cybersecurity across the EU, setting consistent standards that all member states must follow. Simultaneously, it gives countries the freedom to build even stronger frameworks. For businesses, this means fewer headaches and a smoother path to compliance, thanks to the streamlined and harmonized requirements.
Refer article 5
If your business falls within the scope of the NIS2 Directive, Article 21 and 23 should be your primary focus—it’s essentially the backbone of the directive. This article requires EU member states to ensure that essential and important businesses implement the specified cybersecurity measures. It also encourages businesses to take an "all-hazards" approach, going beyond the listed requirements to address a wide range of potential threats.
Here is a complete overview of How Endpoint Central helps you achieve the measures mentioned in Article 21.
| Article 21 | Description |
|---|---|
|
2(a) policies on risk analysis and information system security; |
|
|
2(b) incident handling; |
|
|
2(c) business continuity, such as backup management and disaster recovery, and crisis management; |
|
|
2(d) security in network and information systems acquisition, development and maintenance, including vulnerability handling and disclosure; |
|
|
2(e) policies and procedures to assess the effectiveness of cybersecurity risk-management measures; |
|
|
2(f) basic cyber hygiene practices and cybersecurity training; |
|
|
2(g) policies and procedures regarding the use of cryptography and, where appropriate, encryption; |
|
|
2(h) human resources security, access control policies and asset management; |
|
|
(j) the use of multi-factor authentication or continuous authentication solutions, secured voice, video and text communications and secured emergency communication systems within the entity, where appropriate. |
|
Both Essential and Important entities are required to report a major incident (such as data breach) to CSIRT (Computer Security Incident Response Team) or any relevant authority within 24 hours. All entities are supposed to perform the initial incident forensics and impact assessment within 72 hours of the occurrence of the event.
Refer article 23
Failure to comply with the NIS2 directive (Article 21 and 23) is more than just a legal violation; it opens the door to crippling financial penalties and leaves your organization vulnerable to catastrophic operational disruptions. Essential entities face fines up to €10 million or 2% of global turnover, while important entities risk fines up to €7 million or 1.4% of global turnover.
But it’s not just about fines. Non-compliance puts your reputation, customer trust, and business continuity on the line. With cyberattacks targeting healthcare, energy, finance, and other critical sectors, one breach could devastate your operations and permanently damage your credibility.
Endpoint Central empowers your organization to not only meet NIS2 compliance but secure your digital future with confidence.
Refer article 34
While NIS2 is a comprehensive cybersecurity directive, many organizations in the European Union are required to comply with other significant compliances and legislations. Here is a very basic run down of NIS2, GDPR and DORA and how they complement each other
| Article 21 | NIS2 (Network and Information Security) 2 | DORA (Digital Operational Resilience Act) | GDPR (General Data Protection Regulation) |
|---|---|---|---|
|
Scope |
Extends to Essential and Important entities in the EU (Ref Article 3) |
Extends to all the financial entities in the EU |
Extends to all the organizations across the globe that deal with personal data of European citizens |
|
Purpose |
This directive is intended to raise cybersecurity standards across the EU |
As the name indicates, this is to strengthen cybersecurity resilience across the financial sector |
GDPR builds on the Right to Privacy, which is widely recognized as a fundamental right worldwide. |
|
Relation with NIS 2 |
- |
|
The cybersecurity framework of NIS 2 overlaps with GDPR requirements, helping organizations work towards GDPR compliance more effectively.
|
|
Penalties |
Essential entities can face fines up to €10 million or 2% of global turnover, while important entities risk fines up to €7 million or 1.4% of global turnover. |
The DORA Act does not explicitly specify penalties. However, regulatory authorities in the EU and its member states will have the authority to enforce and impose them. |
|
"Endpoint Central has allowed us to move towards our goal of a centralized application to cover off IT support activities. The deployment was really simple with no real issues. We use it mainly for the integration with ServiceDesk Plus and the reports it provide for our ISO implementation"

Feel free to connect with our experts to address your specific queries and discover how Endpoint Central can assist you in meeting NIS 2 requirements.