- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
EventLog Analyzer comes packaged with over 1,000 predefined reports. Reports are generated instantly whenever logs are collected, reducing organizations' log auditing overhead by presenting only the most important information. Event log reports help organizations analyze their network and meet various security and compliance requirements.
The helpful features available in each EventLog Analyzer report allow users to:
- View results in tabular or graphical formats.
- Drill down to the raw log contents.
- Filter and search through logs according to required criteria.
- Customize and rebrand reports to display the organization's logo and other information.
- Schedule reports to be generated automatically and sent via email.
- Export reports in PDF and CSV formats. An export status bar shows all exported reports and the progress of each exported file.
Event log reports
Windows system auditing
Audit an entire Windows network and view event logs by severity. Monitor system events and the execution of network policies.
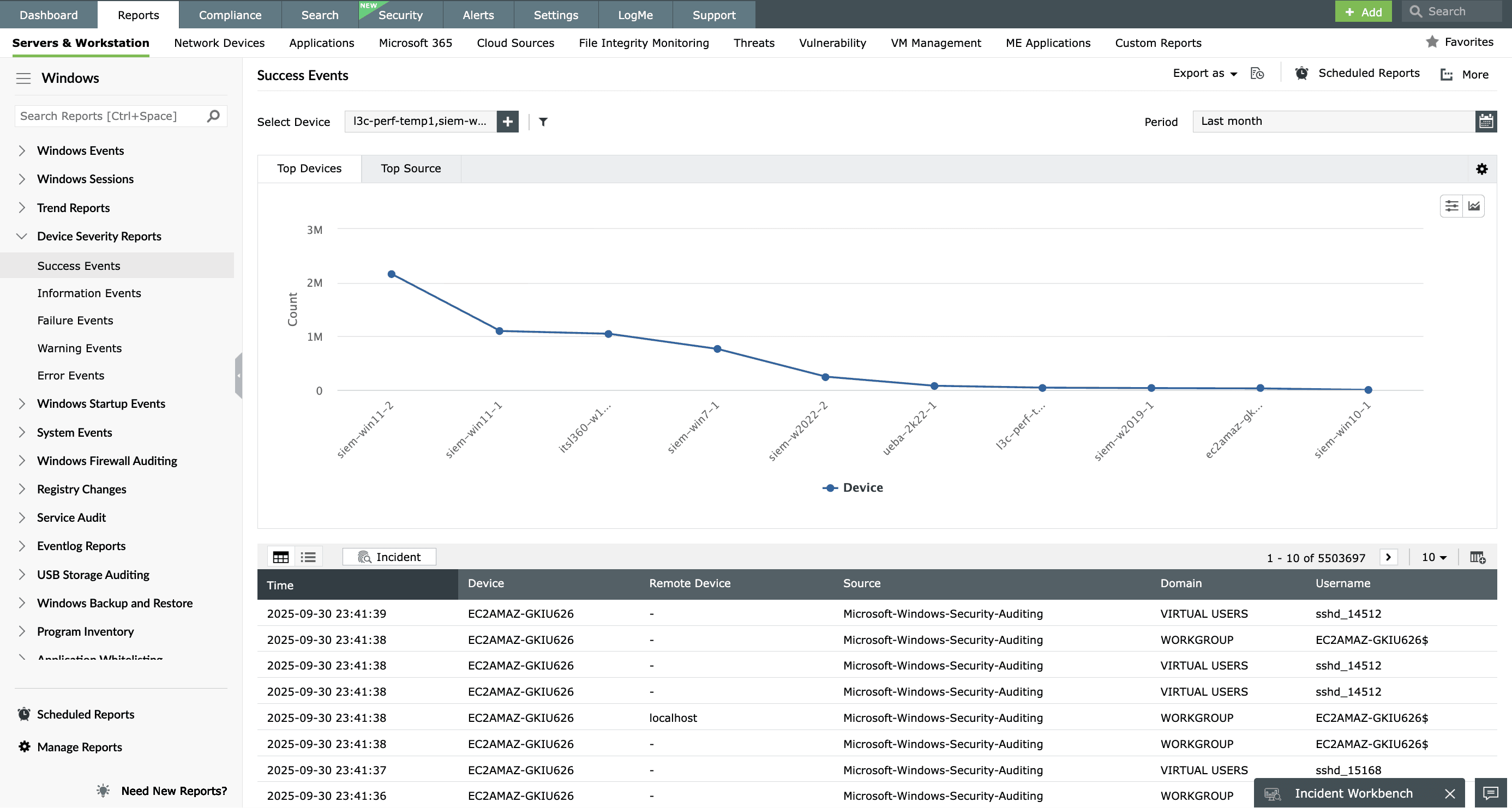
Security auditing
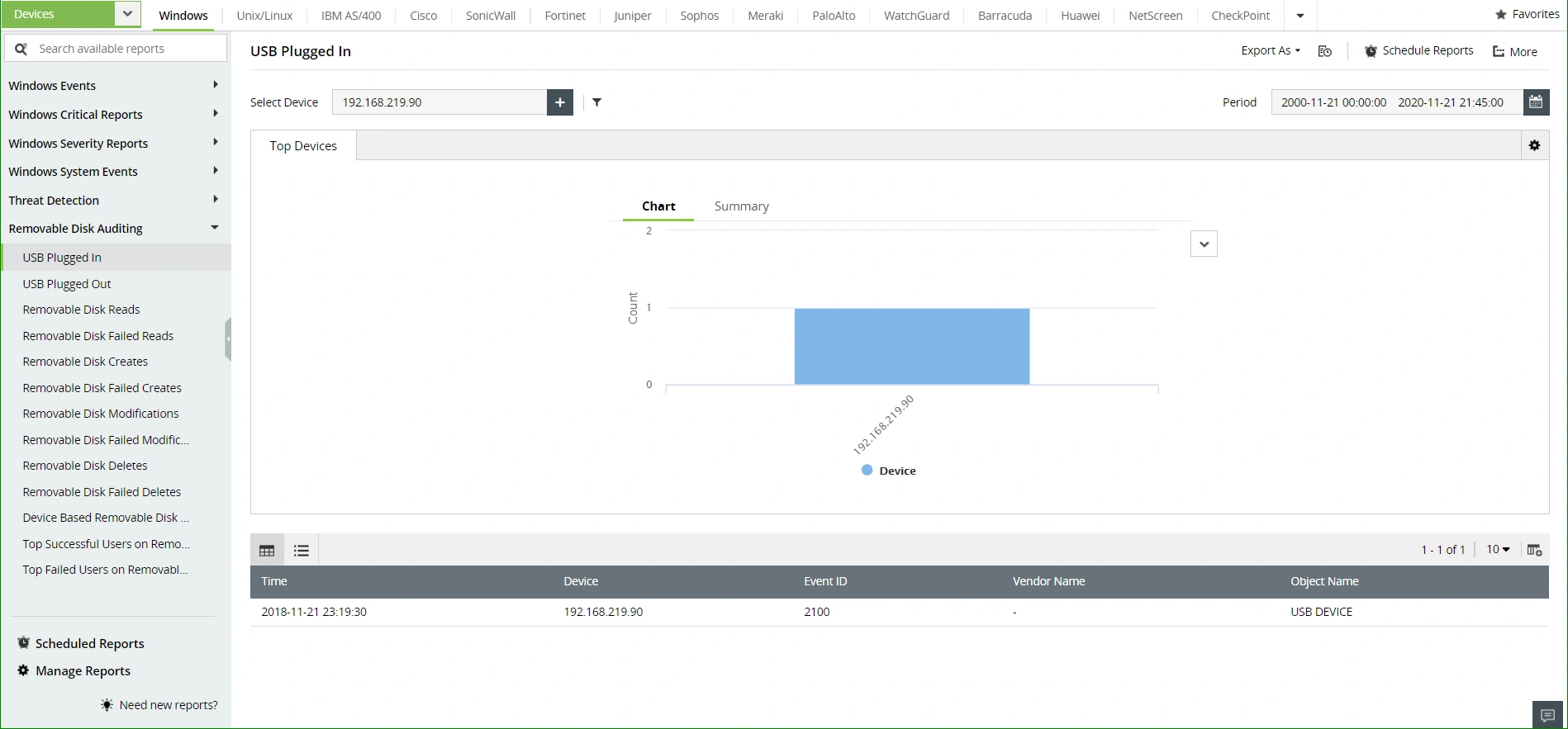
View in-depth reports on all security-related events such as network attack attempts and account lockouts. Prevent data theft by tracking usage and activity on various network endpoints such as printers, removable media, database backups, and more.
Proactively secure your network with event correlation, which detects attack patterns from events occurring across your network.
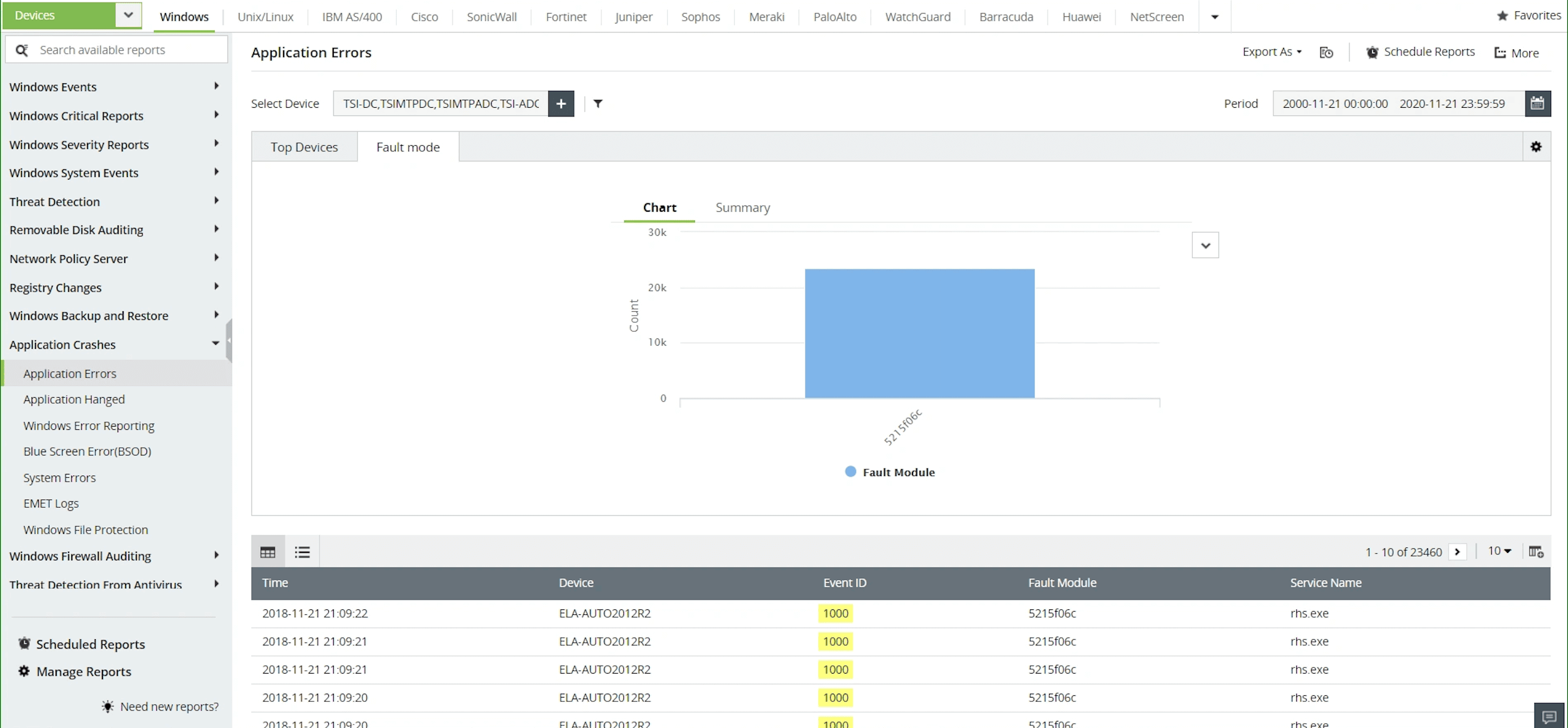
Application auditing
Identify which applications are being accessed, including all application installs, updates, and removals. View application crash reports, along with a list of what caused applications to crash.
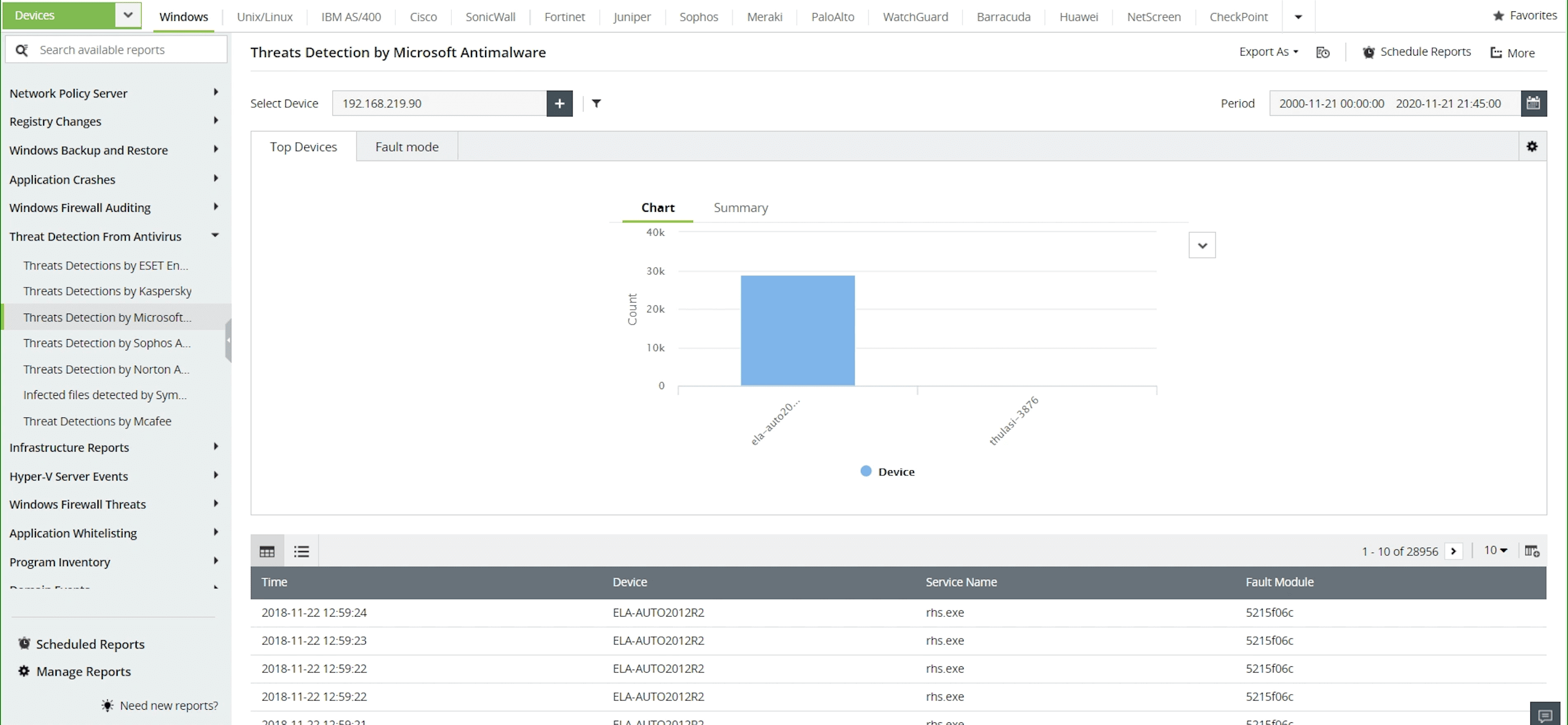
Application activity auditing
Monitor application data for several native Windows applications, such as the native backup, firewall, hypervisor, antivirus, and anti-malware applications. Audit information from various popular antivirus vendors, such as ESET, Kaspersky, Sophos, and Norton.
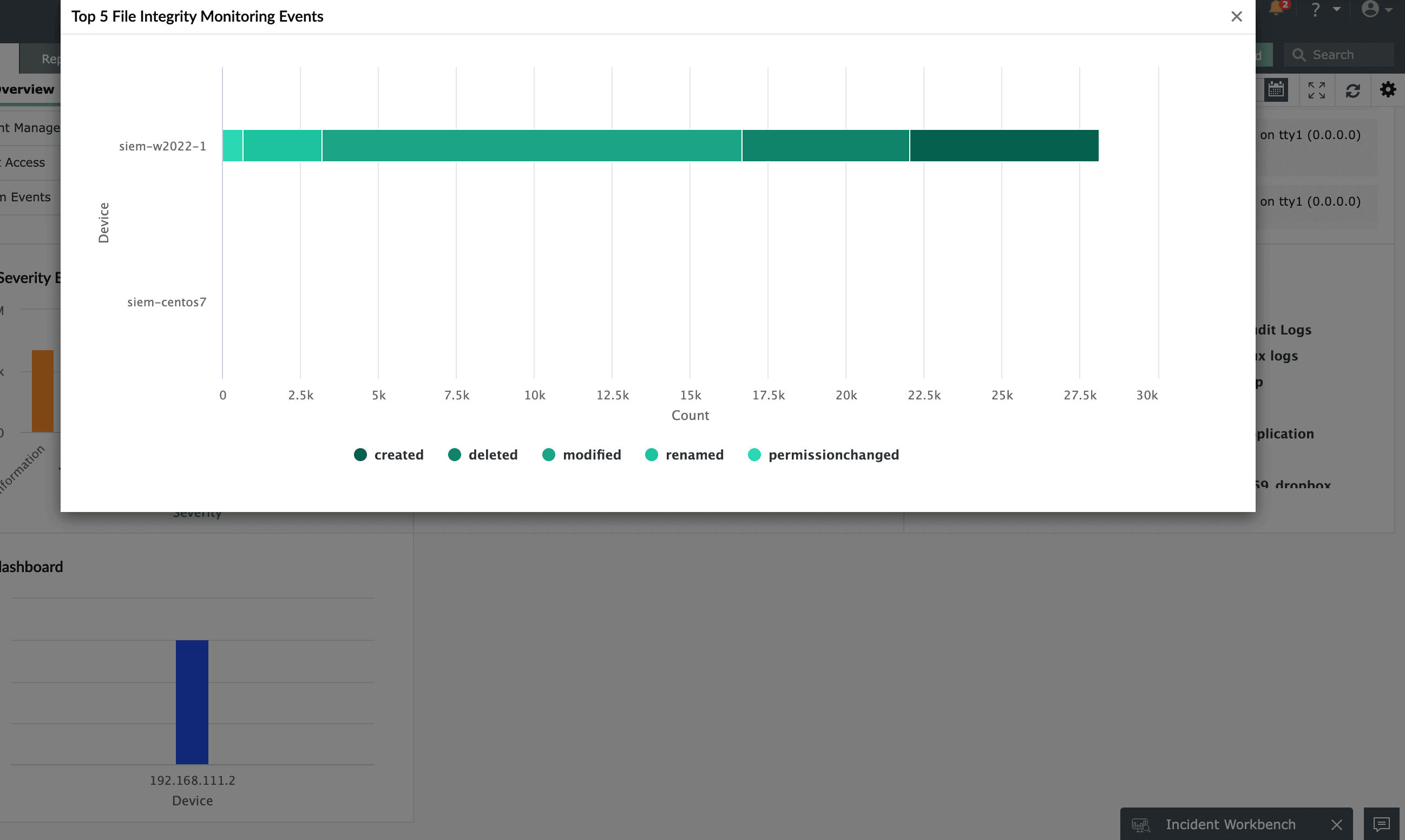
File integrity monitoring
Monitor business-critical files and folders in real time. View all critical file operations as clear, concise reports. Track file operations, including successful or failed file creation, file access or modification, removal of files and folders, as well as permission changes.
Other features
SIEM
EventLog Analyzer offers log management, file integrity monitoring, and real-time event correlation capabilities in a single console that help meeting SIEM needs, combat security attacks, and prevent data breaches.
IT Compliance Management
Comply with the stringent requirements of regulatory mandates viz., PCI DSS, FISMA, HIPAA, and more with predefined reports & alerts. Customize existing reports or build new reports to meet internal security needs.
Real-time alerting
Detect anomalies, threats, and data breach attempts with real-time email/SMS alerts. This tool comes with meticulously drafted 700+ alert criteria plus a wizard to create custom alert profiles at ease.
Real-time event log correlation
With EventLog Analyzer's real-time correlation engine, proactively mitigate security attacks. The solution has 70+ predefined rules on file integrity, user activities, malicious program installation, and more.
Log analysis
Analyze log data from sources across the network. Detect anomalies, track critical security events, and monitor user behaviors with predefined reports, intuitive dashboards, and instant alerts.
Need Features? Tell Us
If you want to see additional features implemented in EventLog Analyzer, we would love to hear. Click here to continue











