Best practices for Windows logging
Last updated on:In this page
What is Windows logging?
Windows event logs provide valuable information, offering a detailed record of all activities within the Windows operating system, from user actions to process activities. These logs meticulously document system operations, errors, software behaviors, security incidents, and administrative changes.
By keeping thorough logs, Windows logging enables administrators to ensure that the system remains secure and operates efficiently. However, given the sheer volume of events generated, it is crucial to implement best practices to extract the maximum value from your logs, making them invaluable for troubleshooting, performing security analysis, and maintaining system health.
Windows event logging best practices
Implementing best practices for Windows event logging is essential for maintaining an efficient, secure, well-managed IT environment. Here are some key guidelines for optimizing Windows event logging:
1. Enable comprehensive Windows logging
To enable comprehensive logging, make sure that the Setup logs should document all installation and configuration activities. Use forwarded event logs to send logs from various systems to a central server. Create custom logs for specific applications to capture detailed information. For web servers, include IIS logs (for monitoring HTTPS transactions, errors, and security events) and Apache logs (for covering error logs, access logs, and custom logs).
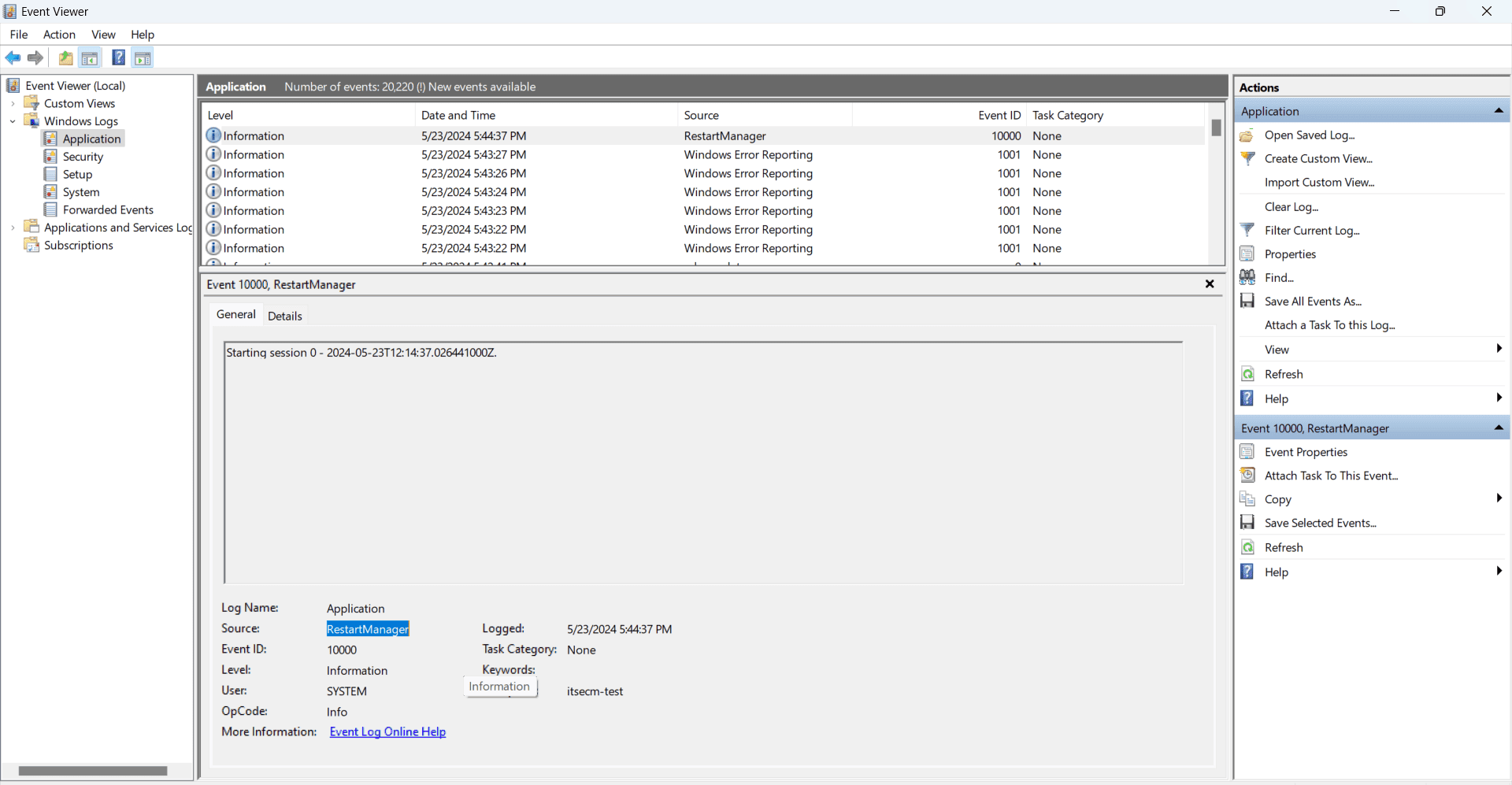
2. Configure audit policies
Ensure that you enable logs that are crucial for your environment. These typically include security, system, and application logs. Configure log settings to capture all the necessary information, such as failure audits in security logs, which can be critical for identifying unauthorized access attempts.
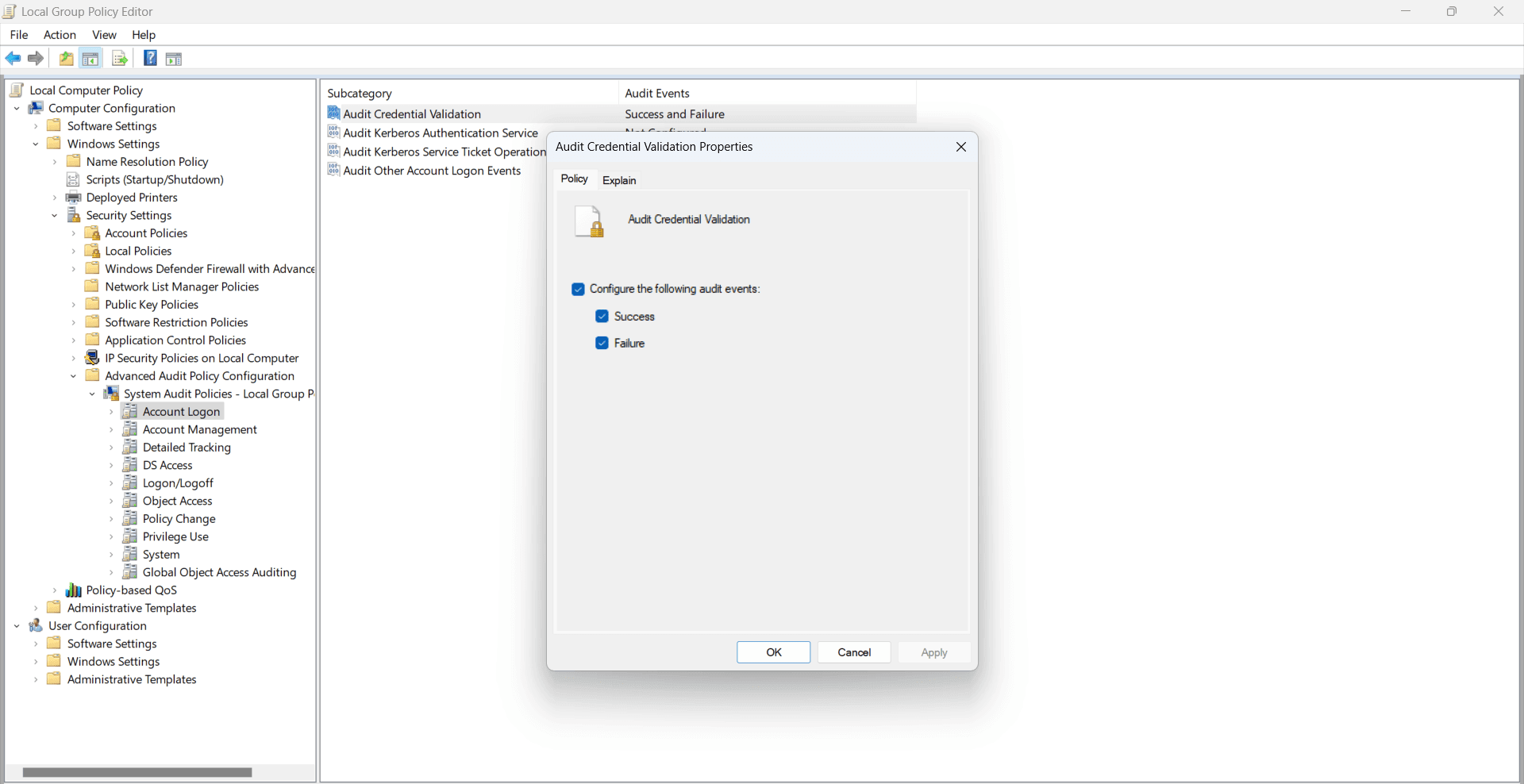
Steps to configure audit policies
To configure audit policies on a Windows machine, follow these steps:
- From the domain controller, click the Start menu, go to Windows Administrative Tools, and select Group Policy Management.
- Select your forest and domain within Group Policy Management, right-click Default Domain Policy or create a new policy, then click Edit.
- In the console tree, go to Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > System Audit Policies.
- Double-click the policy you want to change.
- In the properties window, right-click the relevant subcategory, then select Properties.
- Choose whether to log success, failure, or both by checking the appropriate boxes according to your audit requirements, then click OK.
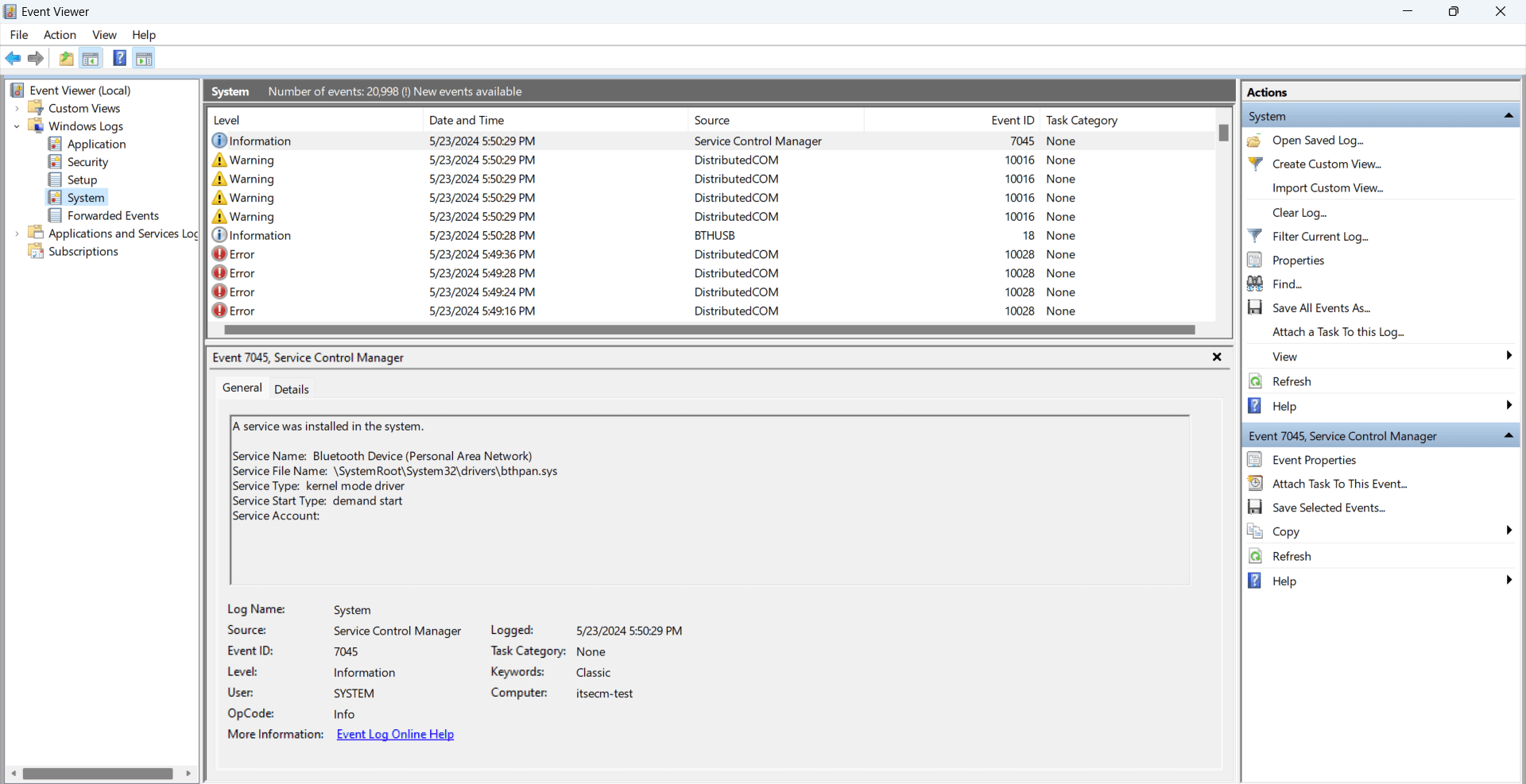
3. Retain and archive logs
Establish and enforce log retention policies that comply with the requirements of your business and regulations. Determine how long logs need to be kept based on the criticality of the information and the legal requirements.
4. Centralize logging
If your environment has multiple servers and systems, use a centralized log management solution like ManageEngine EventLog Analyzer to collect, store, and analyze logs from all sources in one place. This simplifies monitoring and analysis, making it easier to detect patterns or issues across your entire infrastructure.
5. Standardize log formats
Use structured formats like JSON or XML for log entries to ensure consistency and facilitate easier parsing and analysis. Additionally, define and use consistent templates for custom application logs to maintain uniformity and enhance the clarity and usability of log data.
6. Review and analyze logs regularly
Proactively monitor logs for any unusual activities or anomalies. Automated tools can help flag events that deviate from normal patterns, enabling quicker responses to potential issues.
7. Secure log information
Ensure logs are protected from unauthorized access and tampering. This includes setting permissions to restrict access to logs, using encryption for log data at rest and in transit, and storing logs in a secure location.
8. Configure alerts for critical events
Configure alerts for critical events that require immediate attention, such as security breaches, system failures, or critical application errors. This enables rapid responses to potential threats or issues.
9. Ensure time synchronization
Use Network Time Protocol to synchronize all systems to the same time source to maintain accurate timestamps in your logs.
10. Document and comply
Maintain thorough documentation of your logging policies, procedures, and configurations. This documentation is vital for audits and ensuring compliance with internal policies and external regulations.
By implementing these best practices, you can gain a comprehensive view of your systems' performance and health. This helps in proactively identifying and mitigating security threats, quickly resolving system issues, and reducing downtime. Leveraging tools such as Windows Event Viewer, System Monitor, PowerShell, and EventLog Analyzer can transform Windows event logs into critical assets for security monitoring, operational troubleshooting, and compliance with regulations and standards.











