- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
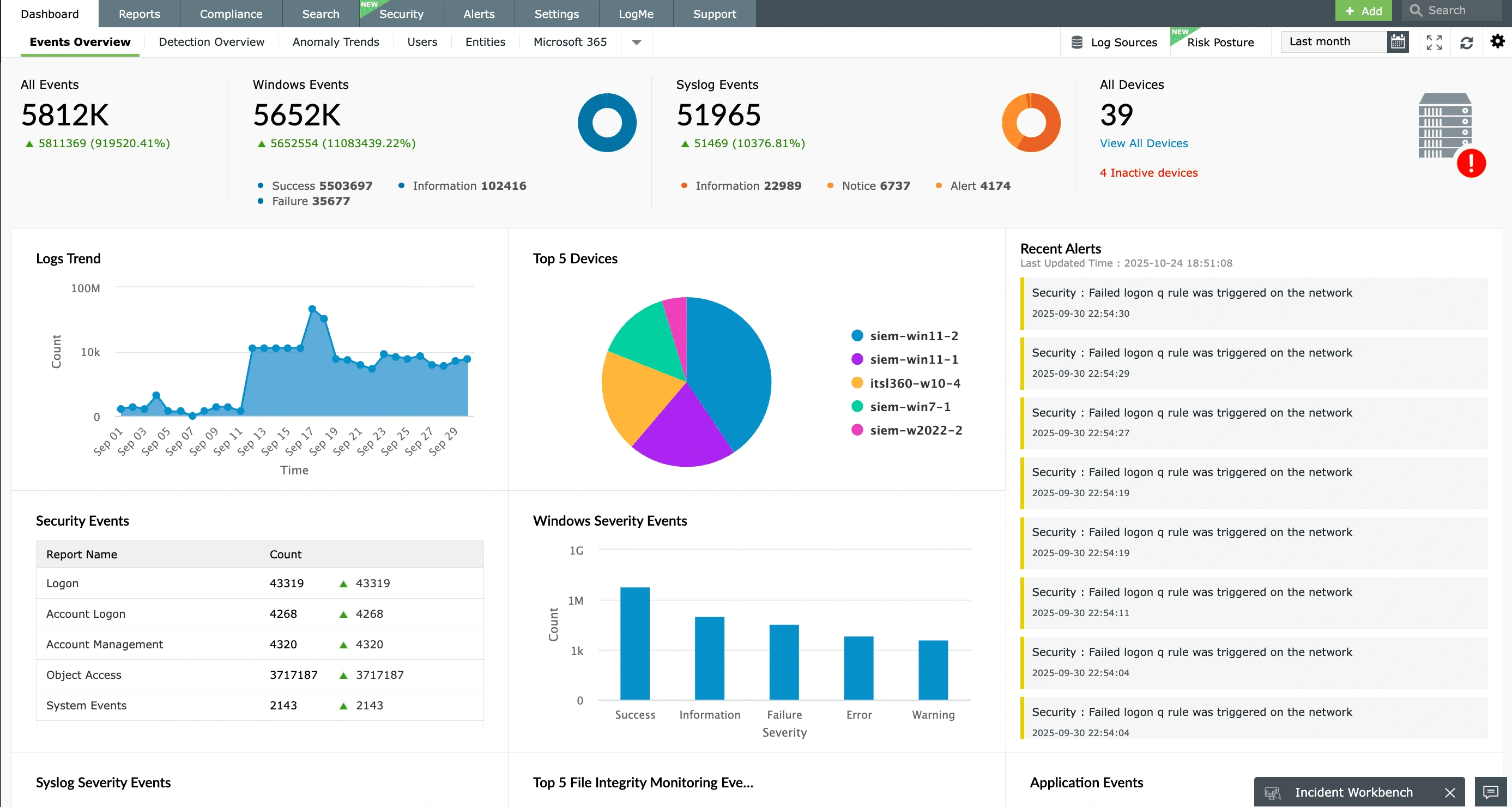
EventLog Analyzer is a comprehensive AI-powered log management software
Logging without limits, EventLog Analyzer provides complete visibility into your IT stack. It provides a cost-effective and scalable approach to centralized log management, with flexible deployment options including on-premises installation and as a cloud-based log management tool.
Dive deeper into how EventLog Analyzer delivers comprehensive log management across your entire infrastructure:
- Leverage unrestricted scalability for all your log management needs
- Gain instant insights leveraging AI for log analytics
- Troubleshoot faster with centralized logging
- Enhance security analytics with real-time log data
- Simplify regulatory compliance audits
- Store your logs with secured log archival
- Respond and remediate security incidents quickly
Leverage unrestricted scalability for all your log management needs
EventLog Analyzer ensures your log management grows with you, seamlessly handling vast volumes of data from an expanding IT infrastructure. Whether it's adding more endpoints, servers, applications, or cloud sources, our solution provides the scalable architecture required to centralize, analyze, and store every log without compromise. This includes a robust cloud-based deployment option that inherently delivers the elasticity and on-demand resources necessary to scale effortlessly, adapt to your evolving needs, and ensurecomprehensive visibilityat any scale.
Gain instant insights leveraging AI for log analytics
In its cloud version, this log management solution leverages Zia Insights, for AI-driven log analysis and transforms raw log data into actionable intelligence. It automatically categorizes logs by type (for example, error, security, system events) and provides critical insights. This includes visual timelines of sequential events, proactivethreat mapping to the MITRE ATT&CK® framework, and one-click access to troubleshooting tip-fea-25s or remedial actions.
EventLog Analyzer: Simplifying log management and enhanced security operations for enterprise
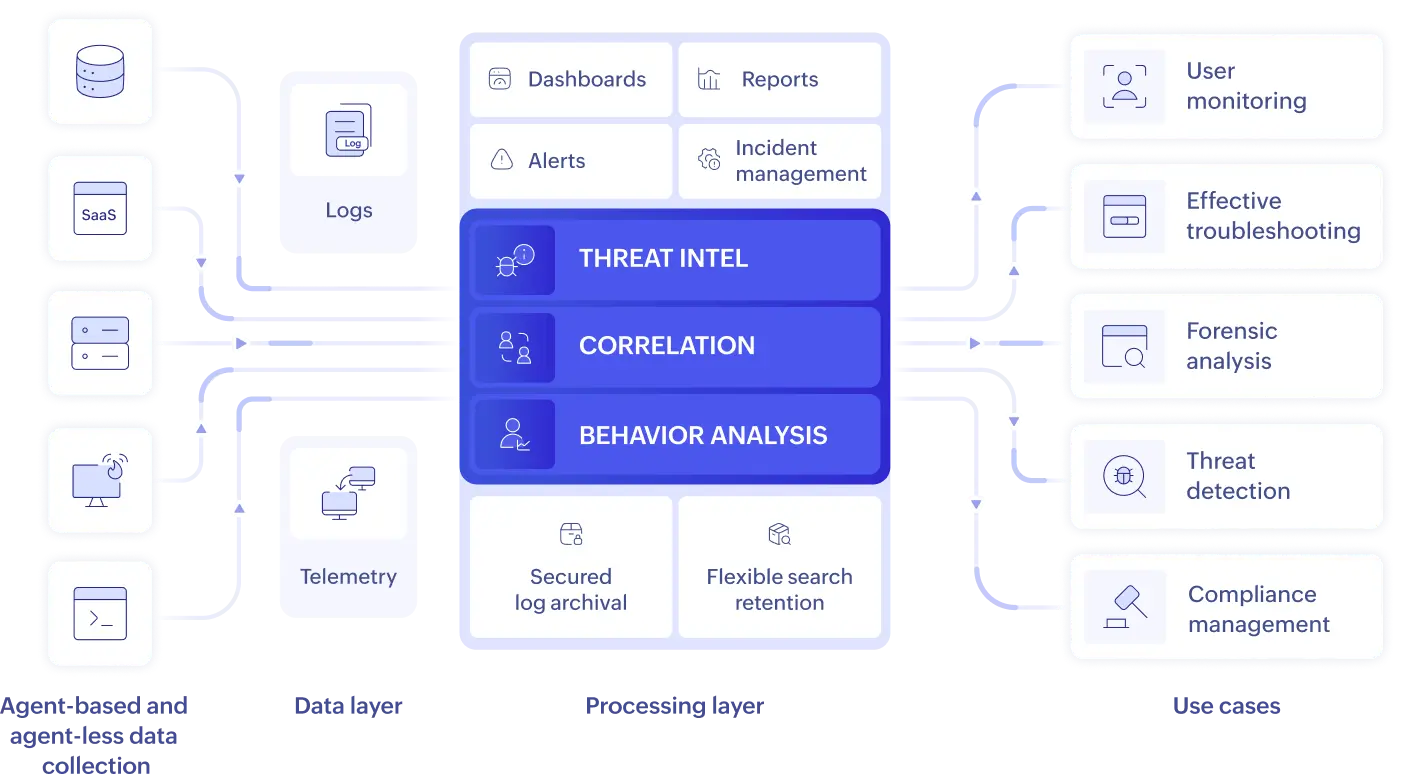
Troubleshoot faster with centralized logging
EventLog Analyzer's centralized logging capabilities are designed to dramatically cut troubleshooting time. By unifying log data from every device, application, server, and cloud source into a single console, it eliminates the need to manually sift through disparate logs. Gain immediate access to all relevant information, pinpoint root causes with precision, and resolve operational issues far more efficiently with a unified view of your entire IT environment.
Looking for the best log management tool for your organization? Start with ManageEngine EventLog Analyzer's free trial!
Are you looking to deploy a log management tool for your security and operational needs? Explore ManageEngine EventLog Analyzer, the industry leading log management tool that is easy to implement, configure yet packed with powerful log management capabilities.
Leverage the 30-day fully functional free trial with technical consultation to kick-start your journey today.
Enhance security analytics with real-time log data
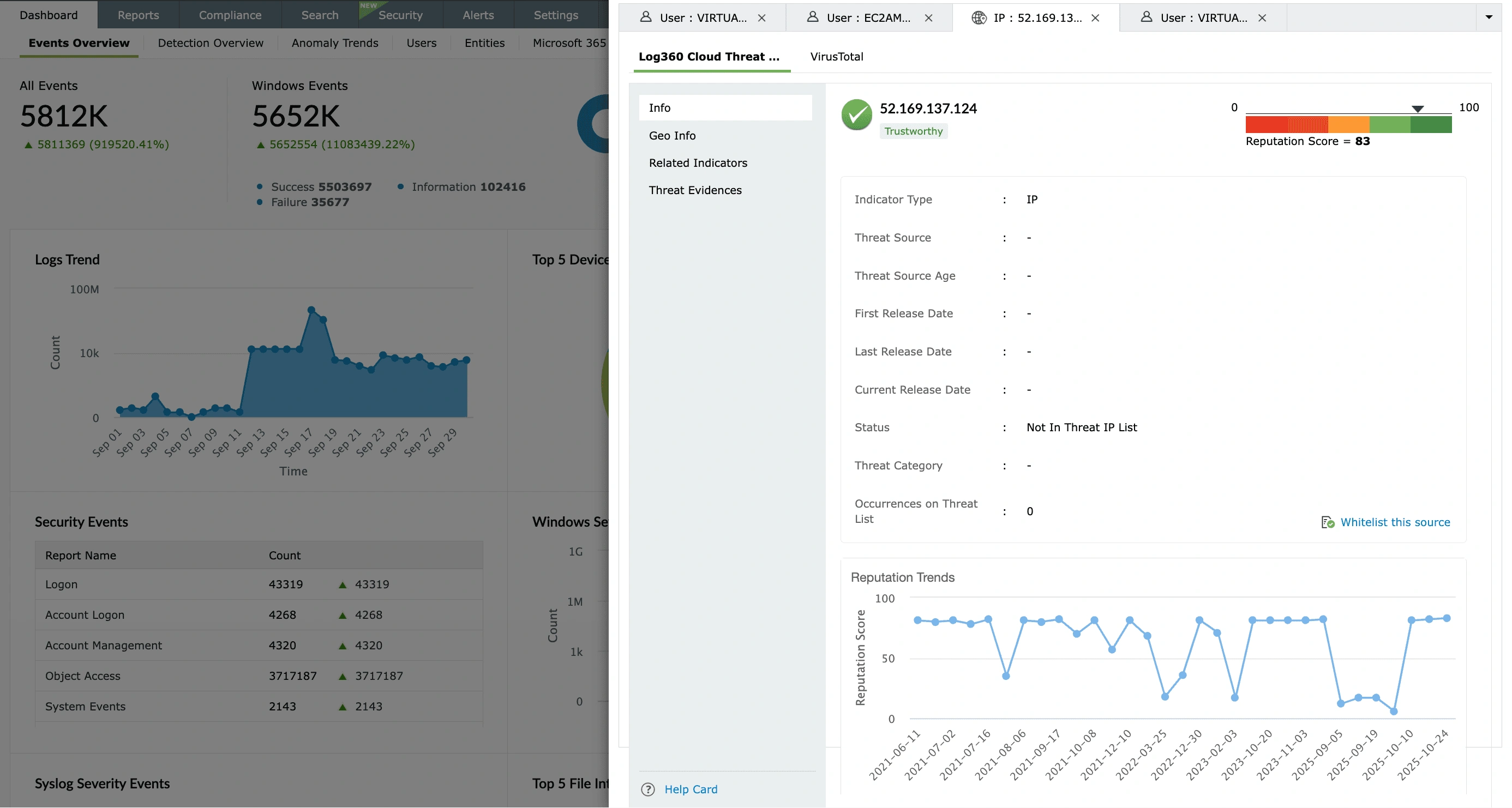
EventLog Analyzer utilizes advanced correlation to link disparate log events, proactively identifying complex threat patterns. Its ML-powered anomaly-based threat detection spots unusual behaviors often indicative of advanced persistent threats, zero-day attacks, or insider threats. This log management solution also has a unified incident workbench which brings in contextual data of users from AD, threat intelligence, or process information for effective analysis.
Simplify regulatory compliance audits
EventLog Analyzer provides robust capabilities for regulatory compliance, including monitoring privileged users, tracking access to sensitive data, and overseeing configuration changes. Its flexible log retention and querying features fulfill most IT audit requirements. Our log management solution provides prebuilt, audit-ready report templates for the PCI DSS, the GDPR, HIPAA, SOX, ISO 27001, and NIS2, and other regulations, simplifying compliance efforts. Furthermore, compliance violation alerts ensure immediate notification upon any deviation from established requirements.
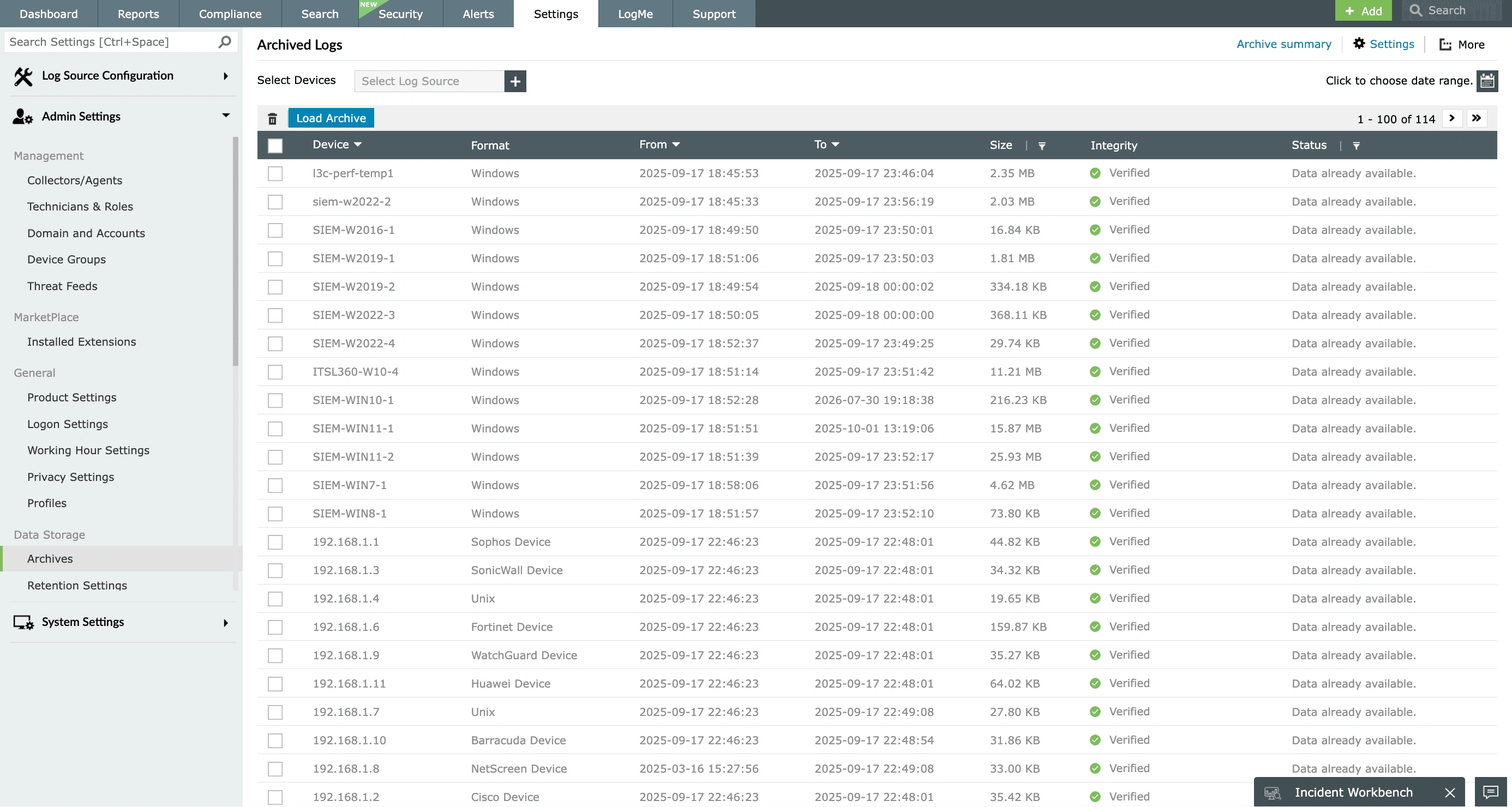
Store your logs with secure log archival
EventLog Analyzer securely archives the ingested logs by adopting encryption, hashing, and time-stamping techniques to make the log archives tamper proof and ensure its integrity. The log files that are archived are easily retrievable for searching based on their time of creation, size details, and the device information. This log management tool also enables you to configure custom log archival intervals and storage locations based on your requirement. EventLog Analyzer provides chain of custody making the forensic analysis easier and meeting one of the most common requirements of IT mandates for log archival.
Respond and remediate security incidents quickly
Reduce detection and response time to security incidents or operational issues with EventLog Analyzer's automated incident response and management system. The console ensures you can set predefined workflow rules and send alerts upon security events or system failures. You can also configure this log management solution to notify relevant administrators, automatically create tickets from alerts and assign them to the right analyst based on the device, or divide up the group that generated the alert.
What our customer say
-
After implementing EventLog Analyzer, the team found that we were actually getting all the logs for the build servers, Linux and Windows alike. We were able to demonstrate a good level of compliance in all of our internal audits.
Shakil Ahmad
CISO and DPO, Samsung R&D Institute
-
It's a very user-friendly application. I evaluated other products, but none covered all the features we needed. EventLog Analyzer is a single application that meets all our requirements.
Madhu
Lead System Engineer at EvonSys
-
There's just a lot of pre-built alerts, rules, and reporting [in EventLog Analyzer] that saves a lot of time that we could have done manually. Before, we would have had to go through and research the event ID with the Windows event ID, and which alert that correlates to. And then just manually create all of that.
Brett Lechner
Sr. Network Engineer, FES
Seamless log management across all your
data sources with EventLog Analyzer
Web Servers
Routers and Switches
- Cisco
- Hewlett-Packard
Hypervisors
Vulnerability Scanners
- Nessus
- Nmap
- Nexpose
- OpenVAS
- Qualys
Endpoint Security Solutions
- ESET Antivirus
- Kaspersky Antivirus
- Microsoft Antimalware
- Sophos Antivirus
- Symantec Endpoint Protection
- FireEye
- Malwarebytes
- McAfee
- Norton Antivirus
Streamline log management of your IT stack with EventLog Analyzer
Server log management
Gain crucial insights into server performance, security events, and operational health. EventLog Analyzer provides deep visibility into server user activities and identifies abnormal behaviors, resource bottlenecks, and potential threats by analyzing server logs.
Learn moreCloud log management
Strengthen your cloud security and compliance with EventLog Analyzer's cloud log management. Ingest logs from services like AWS to detect anomalous API calls, unauthorized access, and misconfigurations while providing audit-ready trails crucial for regulatory adherence in the cloud.
Learn moreEvent log management
EventLog Analyzer provides predefined reports, dashboards, and alerts for user logons, logoffs, and failed authentication attempts. This capability extends to monitoring other vital events such as privilege escalations, system shutdowns, and security policy changes.
Learn moreApplication log management
Monitor performance and ensure security of business critical applications like web servers, databases, cloud apps, and more with EventLog Analyzer's prebuilt parser and log analytics capabilities. Effectively correlate application logs with network logs to detect threats and operational failures.
Learn moreFirewall log management
Correlate firewall logs with application and server logs for effective external threat detection. Get to know firewall rule and policy changes with predefined reports and alerts. Correlate threat intel data with firewall logs to detect unauthorized access attempts of critical resources.
Learn moreEndpoint log management
Analyze, correlate, and archive log data from Windows and Linux endpoints for user monitoring, compliance audits, and troubleshooting. Detect suspicious software installations, unauthorized remote connections, possible account compromise, or suspicious processes or service installations in endpoints. Track USB activities of endpoints with predefined reports and alerts.
Learn moreInsights and resources for log management
- What is log management?
- Logging guide for your IT stack
- Regulatory compliance hub
- Get to know EventLog Analyzer
Frequently asked questions
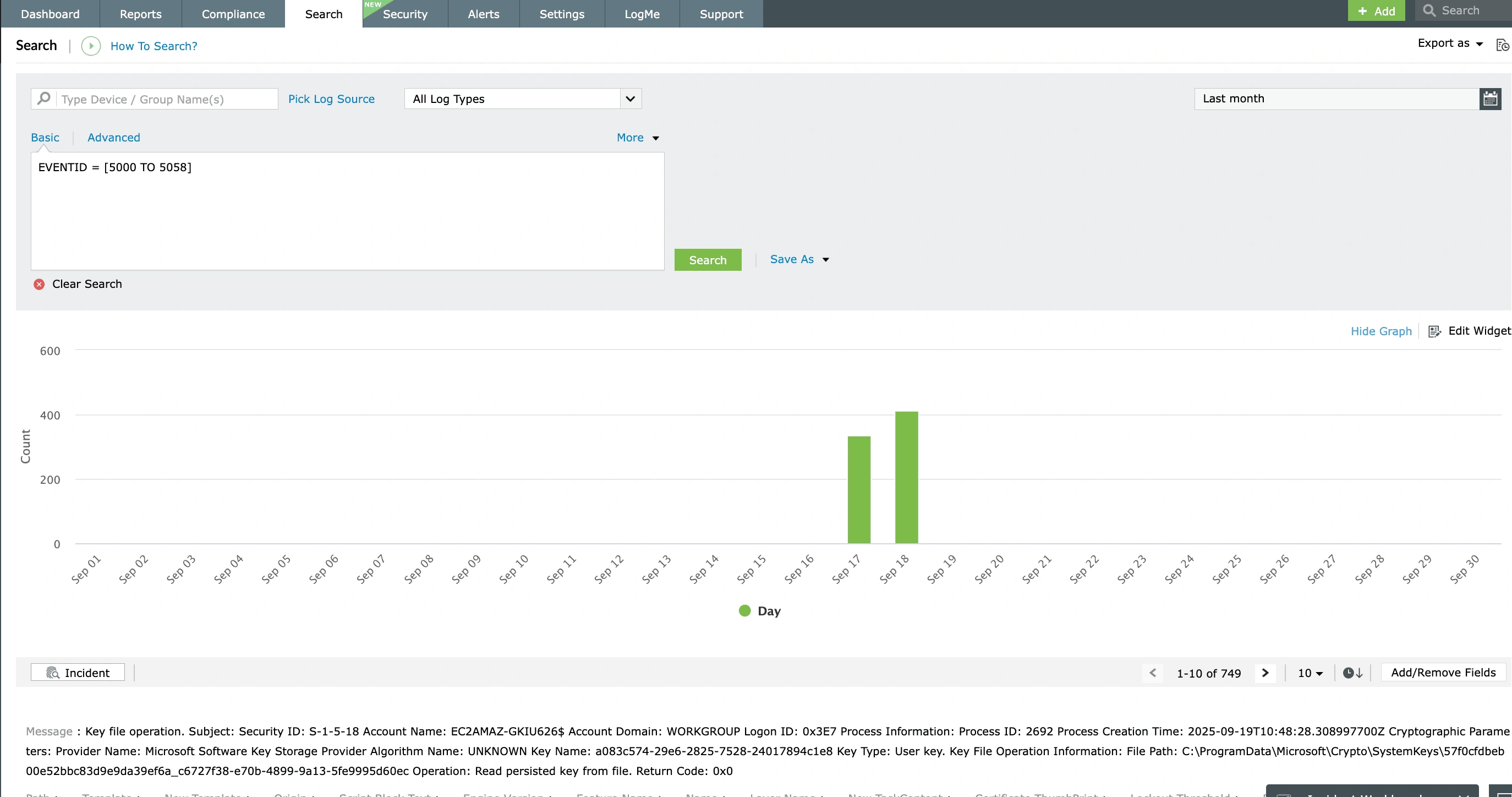
Log management is the systematic process of centrally collecting, processing, analyzing, monitoring, correlating, and storing log data generated by devices and applications throughout an enterprise network.
Log management tools are software systems that centralize the collection, processing, and storage of log data. These tools are crucial for effective troubleshooting, enhancing operational efficiency, and bolstering security across an organization's IT infrastructure.
ManageEngine EventLog Analyzer is one of the robust log management tools that simplifies log management, analysis, centralized logging, security auditing and IT compliance management. When considering other market options, it's helpful to understand their key focuses.
- ELK Stack (Elasticsearch, Logstash, Kibana):A highly flexible and scalable open-source choice, ideal for organizations seeking customizability and community support for their log infrastructure. However, it requires a significant significant technical expertise for setup, configuration, and ongoing maintenance. It lacks out-of-the-box advanced security features (like SIEM capabilities) compared to other commercial solutions, and often requires additional integrations and development.
- Datadog: A strong contender for cloud-centric and modern IT environments, it offers unified visibility across logs, metrics, and application performance monitoring. Its intuitive dashboards and prebuilt integrations accelerate time-to-value for cloud-native applications.However, pricing can escalate quickly with increased data ingestion and activated features across its monitoring portfolio. While comprehensive for the cloud, its on-premises log management capabilities might be less mature or require additional setup compared to dedicated log solutions.
- Graylog: A powerful open-source (with commercial offerings) log management platform known for its centralized log collection, powerful search capabilities, and ability to build custom dashboards and alerts. It offers good scalability and is often favored by organizations looking for a self-hosted solution. While open-source, the advanced features and enterprise-grade support often come with commercial licenses. It requires technical expertise for initial setup, configuration, and ongoing maintenance of the underlying infrastructure (like Elasticsearch/OpenSearch and MongoDB). Users sometimes report challenges with dashboard creation and complex queries.
- NewRelic: A leading observability platform with strong roots in application performance monitoring (APM), offering integrated log management alongside metrics, traces, and synthetic monitoring. It provides deep visibility into application health and performance, making it excellent for developers and site reliability engineers focused on software insights. While its log management capabilities are robust, its primary focus is APM, so it might not be as comprehensive or cost-optimized as dedicated log management tools for pure log aggregation at scale. Pricing can increase significantly due to accelerated data ingestion across its full observability suite, and some users report a steep learning curve for the breadth of features.
An effective log management software should automatically parse, normalize, and centrally store IT log data. It must leverage advanced analytics like correlation and ML-based anomaly detection to proactively identify operational issues and security threats, presenting actionable insights and key metrics through intuitive dashboards and reports.
ManageEngine EventLog Analyzer, available for both on-premises deployment and as a cloud-based log management solution helps enterprises to scale at their need with its flexible architecture. This log management tool excels compared to others by delivering comprehensive capabilities like universal log collection, real-time correlation, and integrated threat intelligence, making it ideal for robust security and compliance. Unlike solutions with unpredictable volume-based costs (Splunk, and other cloud tools) or complex open-source setups (ELK, Graylog), EventLog Analyzer provides transparent, device-based licensing. Its user-friendly interface further simplifies deployment and ongoing management, making advanced log analytics accessible and cost-effective for diverse IT environments. This blend of powerful features and practical usability truly sets it apart.
A log management tool primarily collects, stores, indexes, and enables searching of log data from various sources. It's foundational for troubleshooting and basic operational insights.
A security information and event management (SIEM) tool builds upon log management by adding advanced security capabilities. It correlates events across diverse sources in real time, applies security rules and threat intelligence, and generates alerts to detect, investigate, and respond to cyberthreats.