- Home
- Logging Guide
- Enabling logging and analyzing Windows firewall logs
Enabling logging and analyzing Windows firewall logs.
In this page
- How to generate Windows firewall log files
- Analyzing the Windows firewall logs
Windows systems have a built-in firewall. Though it doesn't log the network traffic by default, it can be configured and logs of the allowed and denied traffic can be obtained. If firewall logging is authorized, 'pfirewall.log' files will be created in the directory.
How to generate Windows firewall log files
Firewall log generation in Windows is an elementary task. The steps to enable the firewall logs are as follows.
Step1
Go to Windows Firewall with Advanced Security, right click on it and click on Properties.(OR)
Press Windows (key) + R to open the run box. Type 'wf.msc' and press Enter. The Windows Firewall with Advanced Security screen appears. On the right side of the screen, click Properties.
Step2
In the Advanced Security screen that appears, multiple tabs like Domain Profile, Private Profile, Public Profile, IPsec Settings will be visible. Click Private Profile > Logging > Customize.
Step3
A new window opens with options to choose the maximum log size, location, and whether to log only dropped packets, a successful connection or both. A dropped packet is a packet that Windows Firewall has blocked. A successful connection may refer to both an incoming connections or any connection that has been made over the Internet.
Go to Log Dropped Packets and switch it to Yes.
Only dropped packets are logged generally. A successful connection doesn't essentially serve the purpose of solving a problem.
Step4
After copying the default path for the log file, click OK. Open the destination folder in File Explorer to find a pfirewall.log file.
Step5
Copy the file to the desktop and it can be viewed.
Analyzing the Windows firewall logs
The Windows firewall log can be split into two sections, viz. the header and the body. The header provides static information describing the version of the log, and the fields available. The body provides information about the traffic that tries to bypass the firewall. Since it's a dynamic list of logs, new entries are added to the bottom. If no entries are recorded for a field, it is represented using 'hyphen (-)'.
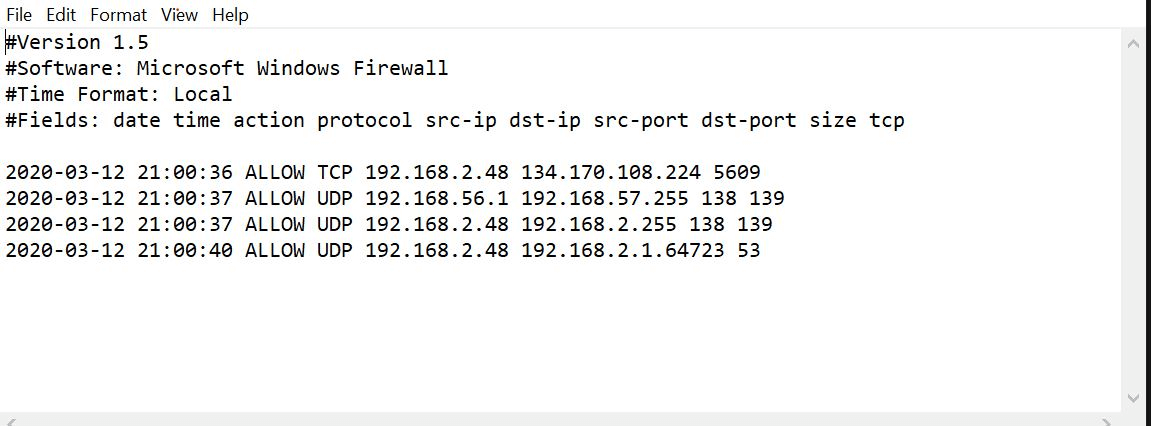
The above image is an example of how a firewall log looks. The key aspects of the above log are:
- The date and time of the connection.
- The type of connection and whether it was allowed or dropped.
- The source and destination IPs and the port that was used for the connection.
- Information on whether the packets were sent or received.











